Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
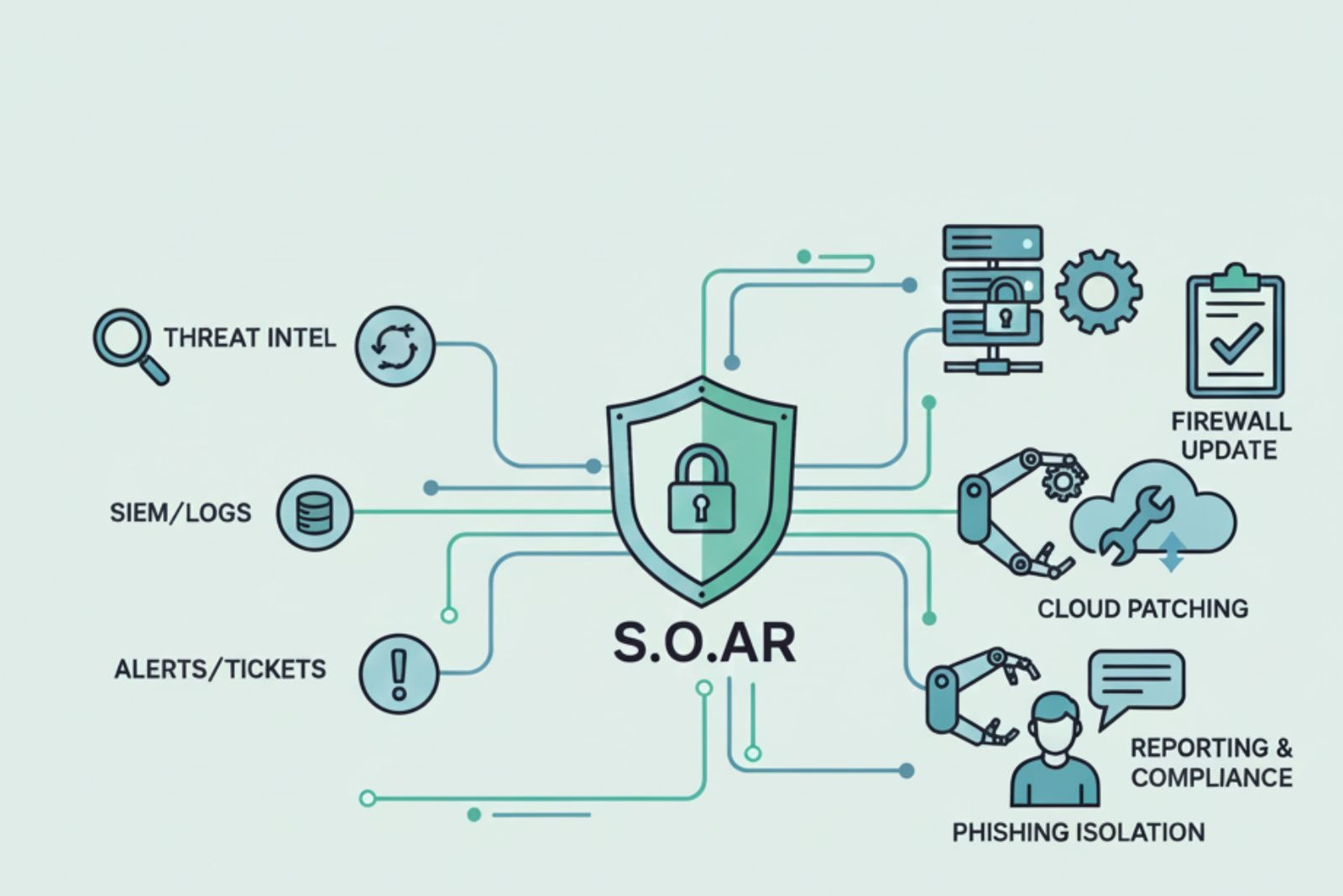
Your security team is drowning in alerts. We see it all the time. A SOAR platform is the answer. It’s software that connects your security tools, automates the routine tasks, and standardizes your response to incidents.
This isn’t just a theory. A managed SOAR platform can slash the time it takes to contain a threat by up to 90% (1).
Keep reading to understand how this automation works and why letting experts manage it is the smartest move for your business in Security Orchestration Automation Response (SOAR).
The sheer volume of security data is overwhelming. Alerts pour in from every corner of your network. It’s too much for any human team to handle effectively. A managed SOAR platform acts like a central command center. It takes in all that telemetry, makes sense of it, and then takes action.
We’ve watched teams transform from reactive to proactive. Instead of chasing every single alert, analysts start focusing on the complex, real threats. The platform handles the noise. This leads to a reported 80% increase in proactive security responses (2).
The biggest advantage might be the workload reduction. Security professionals are in short supply. Burning them out on repetitive tasks is a huge risk. A managed SOAR automates these tasks.
Choosing to outsource your SOAR management is a strategic decision. It’s not just about buying software. It’s about buying expertise. Implementing and tuning a SOAR platform is complex. The playbooks, the workflows, the integrations. They all need constant attention.
When you outsource to a provider like MSSP Security, you get a team that lives and breathes this technology. We handle the ongoing maintenance. We update the playbooks as new threats emerge. We ensure the integrations with your SIEM and EDR tools are running smoothly. This is our full-time job.
This model offers significant cost savings. You avoid the high cost of hiring and training specialized SOAR engineers. You gain access to a scalable platform that grows with your business. It levels the playing field against much larger adversaries.
The primary goal of any security team is to stop breaches fast. The metric for this is Mean Time to Respond (MTTR). A long MTTR means a hacker has more time to move through your network. A short MTTR means you’ve shut them down quickly.
SOAR is built to reduce MTTR. It does this through speed and consistency. Imagine a phishing email is detected. A manual process might look like this. An analyst gets an alert, investigates it, determines it’s malicious, and then manually quarantines it. This could take an hour or more.
With SOAR, the process is automated. The alert triggers a pre-built playbook. The playbook automatically quarantines the email across the entire organization. It also blocks the sender’s URL and IP address..
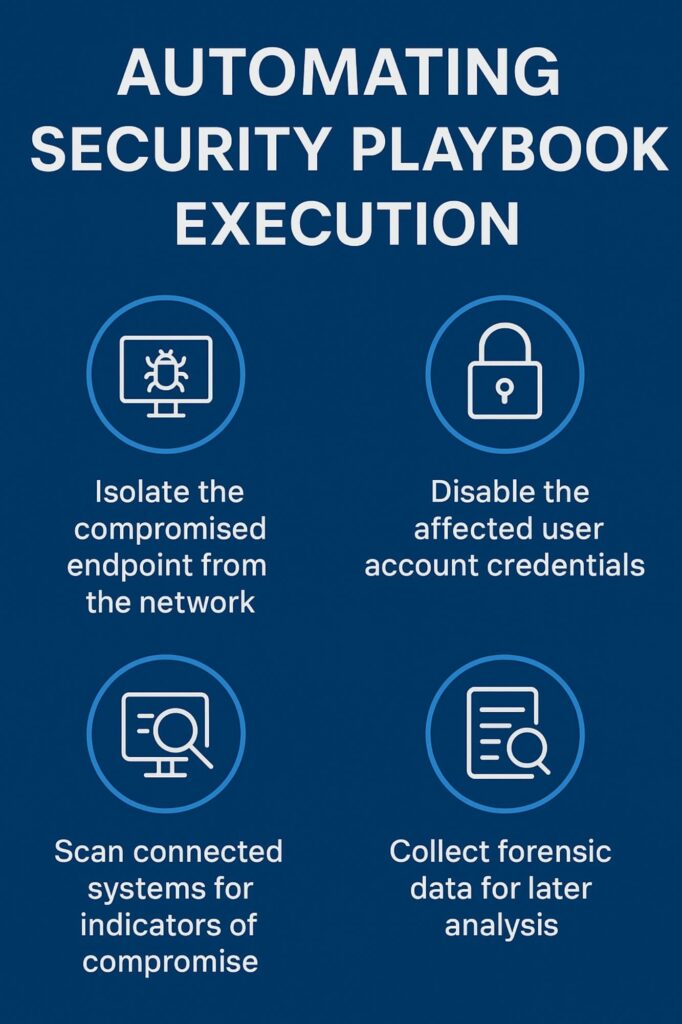
Playbooks are the brains of the SOAR platform for advanced specialized services. They are step-by-step instructions for how to handle a specific type of security incident. Think of them as digital checklists that never get tired or make a mistake. A playbook for a ransomware alert, for instance, would have a very specific sequence.
It might start by isolating the infected endpoint from the network. This prevents the ransomware from spreading. Then, it could disable the user’s account to block further access. Next, it might scan the network for other signs of infection.
Selecting the right SOAR provider is one of the most important decisions you’ll make. The market has many options, and they are not all the same. You need to find a partner, not just a vendor. The provider must understand your business and your specific security challenges.
Look for a platform that is scalable. It should work whether you’re fully in the cloud, on-premises, or a mix of both. For small and mid-sized enterprises, a cloud-based solution often makes the most sense. It’s faster to implement and easier to manage. The provider should also have a strong focus on integrations.
Your SOAR platform is only as good as its connections. It needs to talk seamlessly with your existing security tools. This means your SIEM system, your EDR on endpoints, your firewalls, and even your ticketing system like ServiceNow. An API-first approach is essential for building these connections without a huge development headache.
Integration is where SOAR proves its value. Your SIEM system is a great alerting tool. It collects logs from everywhere and correlates events to find potential threats. But it often stops at alerting.
It says, “Here’s a problem.” Your EDR tool is excellent at protecting endpoints. It can see malicious activity on a laptop or server. But it might not see the bigger picture across the network.
Alert fatigue is a real and dangerous problem in security operations centers. Analysts are bombarded with thousands of alerts every day. The vast majority of these are false positives or low-priority events. But they all need to be looked at, just in case. This constant triage is exhausting and leads to burnout.
Worse, it can cause analysts to miss a real, serious threat buried in the noise. SOAR addresses this directly. It acts as a force multiplier for your team. The platform can be tuned to automatically handle the low-level alerts. It can classify them, close false positives, and only escalate the truly important incidents to a human analyst.
Implementing a SOAR platform is a significant project. It’s not something you just turn on. It requires careful planning and configuration. This is where expert consulting becomes invaluable. For businesses in Fullerton and Orange County, working with a local consultant like MSSP Security provides a distinct advantage.
We offer hands-on SOAR implementation consulting. We start by understanding your unique environment. What tools do you have? What are your biggest pain points? We then design a SOAR strategy that fits your specific needs. Our team handles the technical integration, building the connections between your systems.
Out-of-the-box playbooks are a great starting point. But every organization is different. Your business processes, your risk tolerance, your compliance requirements. They are unique. That’s why the ability to customize SOAR workflows is so important.
A good SOAR platform allows for easy customization. Modern platforms often feature no-code or low-code editors. This means your security team can drag and drop to modify a workflow without needing to be a programmer. For example, you might have a specific approval process for blocking a critical business IP address.
The SOAR workflow can be customized to send an alert to a manager for approval before taking action. This balance of automation and human oversight is key. Customization ensures the SOAR platform works for you, not the other way around. It aligns automation with your actual business rules.
The benefits of implementing a SOAR platform touch every aspect of security operations. The most obvious is efficiency. Tasks that used to take hours now take seconds. This efficiency leads to faster threat containment, which directly reduces business risk. A contained threat cannot become a full-blown data breach.
Another major benefit is standardization. Before SOAR, two analysts might handle the same type of incident in two different ways. With SOAR, every incident is handled according to the approved playbook. This consistency improves your security outcomes and makes auditing a breeze.
SOAR also provides unparalleled visibility. It brings data from all your different tools into a single, unified dashboard. For the first time, you can see your entire security posture from one screen. This helps leadership make better decisions about where to invest security resources. It turns security from a cost center into a strategic advantage.
Source: Google Security Operation
You’ve invested in a SOAR platform. How do you know it’s working? You need to measure it. The return on investment (ROI) for SOAR is significant, but you have to track the right metrics. The most important metric is Mean Time to Respond (MTTR). You should track this before and after SOAR implementation.
Another key metric is the number of alerts handled automatically. Aim for a high percentage, like 80% or more. This shows the platform is effectively reducing the workload on your team. You can also measure cost savings. Calculate the time saved by analysts and translate that into dollars.
How many hours of manual work did SOAR automate? This demonstrates a direct financial return. Finally, track metrics like dwell time.
This is how long a threat is in your environment before it’s found. SOAR should reduce this time significantly. By measuring these KPIs, you can build a strong business case for your SOAR investment and show continuous improvement.
A managed SOAR platform is a security tool that helps your team handle alerts faster. It connects your security systems and uses automation to complete simple tasks on its own. This includes blocking attacks, quarantining files, and gathering data.
A managed SOAR also has experts who watch over it and make sure it works correctly. It helps your team focus on real threats instead of small tasks. This makes your security stronger and more organized every day.
SOAR cuts chaos by taking over the routine work that slows teams down. Alerts come in from many tools, and SOAR sorts them automatically. It knows which alerts are harmless and which ones need attention.
It can respond right away by blocking bad files or isolating devices. This keeps analysts from being overwhelmed. With fewer tasks to handle, your team can think clearly, act faster, and spend more time on the problems that matter most for your business.
SOAR helps teams work faster because it removes the slow steps in incident response. Normally, a person must look at every alert, check details, and choose what to do. SOAR completes these steps in seconds.
When an alert appears, SOAR triggers a playbook that follows a ready-made plan. It carries out actions instantly and the same way each time. This shortens the time needed to handle threats and gives analysts more freedom to solve bigger, more complex issues.
A security playbook is a step-by-step plan that tells SOAR how to respond to a specific threat. It works like a digital checklist that never forgets a step. For example, a phishing playbook may quarantine emails, block websites, and notify your team.
Because the playbook follows the same steps every time, your responses become faster and more accurate. Playbooks keep your security process steady and dependable, even when large amounts of alerts arrive at once and overwhelm your team.
Companies outsource SOAR management to save time, money, and effort. Setting up SOAR takes skill and daily attention. It needs updates, new playbooks, and correct system connections. Not all teams have time or staff for this.
When a company outsources SOAR, experts manage everything for them. They keep the system running well and updated for new threats. This frees the business to focus on growth instead of daily security tasks and reduces the cost of hiring specialized staff.
SOAR reduces alert fatigue by handling simple and low-risk alerts automatically. Analysts often face hundreds of alerts every day, and many do not need a human response. SOAR identifies these alerts and closes them on its own.
Only true threats are sent to your team. This means fewer tickets, fewer stressful tasks, and less risk of missing something important. With SOAR, analysts can spend their time on real investigations instead of sorting large numbers of basic or false alerts.
Integration with SIEM and EDR is important because SOAR needs full and accurate information to act quickly. The SIEM gathers logs and finds threats across the network. The EDR watches what happens on devices.
When both connect to SOAR, the platform can see the complete picture. It uses this data to pick the best response instantly. These strong connections help SOAR work faster, reduce mistakes, and give your team a strong and unified defense against advanced security attacks.
SOAR shortens response time by acting the moment an alert appears. Instead of waiting for an analyst to read the alert and choose actions, SOAR follows a playbook right away. It can isolate a device, block an IP, or remove a file in under a minute.
These quick actions stop attackers from spreading or stealing data. Faster responses help reduce damage, save money, and keep your business safe during incidents. This speed is one of SOAR’s biggest advantages.
Businesses can expect faster response times, fewer manual tasks, and stronger protection. SOAR automates common steps, which cuts down the time needed to handle each incident.
Teams also report less burnout and clearer workflows. Because SOAR follows the same steps every time, the company gains better consistency and easier audits. Overall, SOAR helps businesses stay safer with much less effort and confusion.
You measure SOAR’s success by watching key numbers. The most important is MTTR, which shows how long it takes to respond to threats. After using SOAR, this number should drop a lot. You can also track how many alerts SOAR handles automatically.
A higher number means your team is saving time. Other useful metrics include reduced analyst workload and shorter threat dwell time. These numbers help show how well SOAR improves your security program’s speed, strength, and daily performance.
Security Orchestration, Automation, and Response is no longer a luxury for large enterprises. The threat landscape is too aggressive, and analyst burnout is too real.
A managed SOAR platform provides a clear path out of the chaos. It automates the repetitive, accelerates the response, and empowers your team.
The goal is to move from a constant state of reaction to a position of controlled strength. The data shows it’s possible to cut your security workload dramatically while improving your defense.
The first step is to evaluate your current alert volume and response times with MSSP Security. See the gap between where you are and where you could be. Then, the value of automation becomes undeniable.