Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

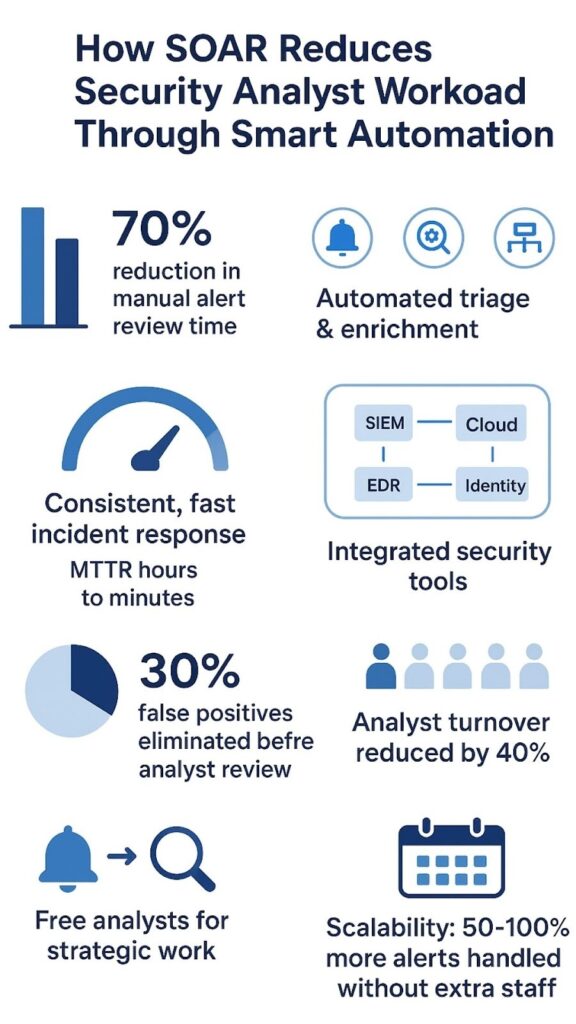
You can reduce security analyst workload significantly with SOAR by automating the repetitive tasks that consume most of their day. We’ve seen teams handling 10,000 daily alerts cut manual review time by 70 percent through automated triage and enrichment. SOAR platforms integrate your existing security tools, then execute predefined playbooks that handle everything from phishing analysis to endpoint containment without human intervention.
This shifts analysts from firefighting to strategic work while maintaining consistent response quality across all shifts. Keep reading to understand how this transformation works in practice and what it means for your team’s effectiveness.
The steady drumbeat of security alerts wears people down in a quiet, specific way. It’s not only how many alerts land in the queue, it’s how similar they feel. Most analysts fall into the same routine:
Those steps repeat, again and again, all day. We watched one SOC team spend close to forty minutes working a single phishing alert that looked almost identical to the last ten. Same pattern. Same checks. Same outcome. That’s the point where automation stops looking like a nice upgrade and starts looking like the only sane option.
SOAR shifts this pattern in a very direct way. It becomes the central nervous system of the SOC, tying together tools that usually act like strangers. Instead of one analyst hopping between:
SOAR playbooks do the legwork in the background, in a few seconds. The platform learns what “normal” looks like in your environment, then applies the same logic to every incident, whether someone just started their shift at 2 PM or is dragging through the night at 2 AM.
The work doesn’t become less serious, but it does become less punishing. This is the power of security orchestration to unify diverse tools into a seamless defense system, reducing the chaos analysts face daily.
Alert triage becomes a background process rather than a primary activity. When an alert fires from your SIEM or EDR, SOAR doesn’t just pass it along to a human queue. It immediately begins enriching the data, checking IP addresses against threat feeds, correlating with other events from the past hour, assessing the criticality of the affected asset.
What reaches the analyst isn’t a raw alert but a partially investigated incident with context already attached. This enrichment step alone can eliminate 30 percent of false positives before a human even looks at them [1].
Containment actions that used to require manual approval now happen automatically for well-understood threats. If a known malware signature triggers on an endpoint, SOAR can isolate that device from the network, block command and control IPs at the firewall, and disable compromised user accounts, all within the same workflow.
The system follows the same playbook every time, ensuring consistent response regardless of which analyst is on shift or how tired they might be. We’ve implemented these automated containment workflows for MSSP clients, and the reduction in manual endpoint management has been dramatic.
The orchestration layer ensures all your security tools work together rather than in isolation. Many organizations have solid point solutions that generate valuable alerts, but the friction between systems creates manual work.
SOAR acts as the glue, using APIs and connectors to make your SIEM talk to your endpoint protection, your cloud security platform share data with your identity management system. This integration turns a collection of tools into a coordinated defense system where automation handles the routine coordination tasks.
You really see the strain lift when you watch the day-to-day work change, not just the metrics on a slide. Some use cases make that shift almost impossible to ignore.
Phishing is where the manual grind shows up the loudest. Without automation, every suspicious email pulls an analyst into the same routine:
In a medium-sized organization, fifty of these a day is normal, which quietly eats hours of focused time. Most of those cases look nearly identical by the end of the week.
With SOAR in place, that workflow turns into an automated pipeline. The platform can:
Analysts only handle the edge cases, the 10% that don’t fit the usual patterns or need human judgment. The rest never clutters their queue. This kind of automation-driven security automation pipeline sharply cuts down repetitive manual tasks, allowing analysts to focus on strategic investigations.
EDR alerts have their own familiar pattern. A single flagged event usually means an analyst has to:
With SOAR, that investigation can be kicked off automatically as soon as the EDR raises a flag. For clear-cut threats, like known ransomware behavior or repeat-bad indicators, the system can:
That kind of automated response matters most at 3 AM, when the on-call analyst might be junior or juggling multiple alerts. The quality of the response stops depending on who happens to be awake.
Account-based alerts are messy by nature. A login from another country could be a stolen password, or just someone on a trip, or someone using a new VPN exit point. Manually, an analyst might have to:
SOAR can line up that context on its own and act based on risk:
The result is a quieter, more focused queue: fewer knee-jerk lockouts for normal travel, and faster attention on the logins that really look like compromise.
| Incident Type | Manual Effort Required | Automated Actions | Analyst Workload Reduction |
| Phishing Emails | Header checks, URL analysis, user contact | Automated analysis, TI checks, quarantine, notification | Analysts only handle ambiguous cases |
| EDR Alerts | Process tree review, hash lookup, network correlation | Automated evidence gathering, endpoint isolation | Automated handling of clear-cut threats |
| User Account Investigations | Log review, behavior correlation | Automated risk scoring, step-up auth trigger | Fewer unnecessary escalations |

You can usually tell when automation is working before you even check the dashboards, people stop looking so drained, and the queue stops feeling like a losing battle. The numbers just confirm what the team already feels.
When SOAR gets fully wired into daily operations, some patterns show up again and again:
One organization we worked with took phishing investigations from about 35 minutes per email down to roughly 90 seconds using full automation. Same checks, same logic, just no manual shuffling between tools. The real gain wasn’t only speed, it was consistency.
A phishing alert at:
gets the same sequence of steps, the same evidence collection, the same documentation. No shortcuts because someone is tired, busy, or new.
As the low-complexity work drains away, the analyst role itself shifts in a meaningful way. Instead of spending hours on:
Analysts start spending more of their day on:
That shift has real effects. We’ve seen:
People move from “button-click operators” to actual security practitioners who understand patterns, tradeoffs, and long-term risk. The work becomes harder in a good way, not just heavier.
Most organizations grow their digital footprint faster than their security budget. More endpoints, more SaaS apps, more cloud services, usually followed by more alerts. Without automation, that path looks very linear: more alerts → more analysts.
With SOAR in place, that curve starts to break. Automated playbooks quietly pick up the extra load:
In practice, we’ve watched teams:
The outcome isn’t just “doing more with less.” It’s making sure that when the really hard incidents arrive, there’s actually enough human attention left to deal with them properly.
| Metric | Before SOAR | After SOAR | Improvement |
| Mean Time to Respond (MTTR) | Hours | Minutes | Significant reduction |
| Phishing Investigation Time | 35 minutes | 90 seconds | 90 percent faster |
| Analyst Alert Capacity | Baseline | 50 to 100 percent higher | Increased capacity |
| Response Consistency | Variable by shift | Uniform across shifts | Higher reliability |
The turning point with SOAR usually isn’t a flashy feature, it’s that first week when the alert queue feels lighter and nobody quite believes it yet. That doesn’t happen by accident, it comes from being very deliberate about where you start and how you wire it in.
The fastest wins come from the incidents that happen all the time and behave the same way. Good first candidates usually include:
These follow stable patterns and don’t need deep debate every time. For these kinds of cases, SOAR can own the full response lifecycle:
By focusing on these patterns first, most teams feel real workload reduction within the first week, fewer repetitive tickets, fewer “copy-paste” investigations, more time for the unusual cases.
There’s a strong temptation to connect every tool in the stack on day one. That usually creates a lot of connectors and not much real value. Early on, depth beats breadth.
Start by making sure SOAR is tightly integrated with:
With deep integration, playbooks can:
Once that foundation feels stable, then it makes sense to fold in:
That staged approach keeps the team from getting overwhelmed and makes each new integration actually matter.
Not every decision belongs to automation, and that’s healthy. Some actions can hurt the business if they’re wrong, even if they’re technically “secure.” Those should keep a human in the approval chain [2].
A balanced model usually looks like this:
In those high-impact cases, SOAR still does most of the heavy lifting:
The analyst doesn’t start from zero, they review a complete, pre-built picture and make a judgment call. Workload drops, but control stays in human hands where it matters most.
Credits : Security First Corp
You can almost see the job title changing, even if the badge doesn’t. Once automation is in place, analysts stop living inside queues and start living inside investigations.
Instead of opening each alert cold and rebuilding the story from raw logs, analysts now sit one level higher. By the time they touch a case, SOAR has usually:
The analyst’s work shifts toward:
The job becomes less about “click these five buttons in order” and more about reading a situation, asking better questions, and spotting what the playbook missed. The work feels more like analysis and less like assembly line labor.
Once the repetitive response work is off their plate, analysts finally get time for the work most SOCs say they want to do but rarely reach: hunting and improving.
That time gets used for:
When that shift happens, the SOC stops feeling like a pure cost sink that only reacts to bad days. It starts to act more like a risk management function that actively lowers the chance and impact of those bad days.
A quieter alert queue doesn’t make analysts idle, it makes them sharper. When they’re not buried under repetitive triage, there’s finally room to deepen skills and cross-train in a structured way.
Common patterns that emerge:
This kind of growth helps both sides. Analysts build careers that feel like they’re moving forward, not just sideways from one incident to the next. The organization ends up with a more resilient team, better prepared for the rare, high-impact attacks that automation alone can’t solve.
You can usually tell when a SOC is ready for SOAR not by the tools they own, but by how often someone sighs before opening yet another alert. Turning that around takes more than just buying a platform, it takes planning that starts from the actual work your analysts are doing.
The first step is simple, but it takes honesty. You map out the work that actually exhausts your team. Not the rare, heroic incidents, but the daily grind. Look for:
Those become your first automation targets. Phishing, low-risk malware detections, repeat vulnerability alerts, these are usually at the top of the list. When you design playbooks around them, the impact shows up fast, because you’re cutting straight into the work that eats most of the day. This approach aligns with best practices in outsourced security automation orchestration, where focusing on common patterns first accelerates workload reduction and improves SOC efficiency.
Picking a SOAR platform matters too, but not in a shiny-demo way. The key is:
If a SOAR tool demands that you replace half your stack, it’s probably working against you, not with you.
The quality of your playbooks depends heavily on who writes them. If they’re designed only by vendors or architects far from the queue, they’ll look clean on paper and feel wrong in practice.
Analysts should help decide:
You can structure that collaboration around a few simple questions for each playbook:
When analysts see their own logic reflected in the playbooks, two things happen: the automation works better, and they trust it more.
There’s a quiet fear in a lot of SOCs that “automation” is just a polite word for cutting people. That fear can stall projects before they really start. The reality, when SOAR is done right, looks different.
Automation is best at:
Analysts are best at:
Good SOAR design leans into that split. The platform sets the stage by doing the data gathering and first-level reasoning, and analysts make the calls where context and nuance matter.
There’s a tempting fantasy where every alert is fully automated and no one ever has to touch a queue again. That’s not how healthy SOCs work. The real goal is something more balanced: automation where it’s reliable, humans where it’s necessary.
A practical model looks like this:
In that setup, SOAR becomes the force multiplier: it clears the noise, builds the context, and gives your analysts the space to work on the threats that actually matter. The SOC shifts from being a burnout machine into something closer to what it was always supposed to be, a focused, strategic security function that can keep up as your organization grows.
SOAR automation helps you handle alert triage automation, incident response automation, automated incident enrichment, and automated evidence collection. You improve security analyst productivity and reduce alert fatigue. You use SOAR playbooks to guide rule based incident handling and playbook driven response. You cut repetitive task reduction and support SOC workload reduction. You make SOC efficiency improvement easier through clear security process standardization.
You use incident correlation automation, contextual alert enrichment, SOC alert deduplication, automated phishing triage, and alert routing automation. SIEM and SOAR integration and EDR and SOAR integration help event normalization and correlation. You cut mean time to respond with MTTD reduction with SOAR. You keep queues clean with auto closing false positives and clear incident prioritization automation.
You use real time response automation, automated containment actions, automated IOC blocking, user account lockout automation, and endpoint isolation automation. SOC process orchestration and security orchestration workflows control tools in one flow. You follow standardized incident handling with security runbook automation. You use knowledge driven playbooks and adaptive playbooks for safer response action orchestration.
SOAR supports analyst burnout reduction through Level 1 task automation and Tier 1 analyst offloading. You use workflow orchestration in SOC and a task orchestration engine to share work across tools. Role based task assignment and auto escalation of incidents keep work balanced. You support SOC scalability with SOAR and SOC resource optimization through a hybrid human machine SOC.
You use cross tool integration and orchestration of security tools for better security operations automation. You guide actions with a security automation framework and a security event workflow engine. Case management in SOAR and playbook lifecycle management help continuous playbook improvement. You use closed loop incident response, compliance driven automation, and policy based response actions for stable automation led SOC transformation.
SOAR shifts your security team from reacting to planning. It handles repeatable tasks. You get faster responses. Your analysts focus on investigations and threat hunting. You reduce fatigue. You create consistent protection.
Start with phishing workflows. Grow to other high volume incidents. You build a system that scales with your team. Humans and automation work together. Your analysts deliver more value.
We offer consulting that helps you choose the right tools. You reduce overlap. You improve visibility. You integrate your stack with clear steps. You get support from needs analysis to PoC. You receive recommendations that match your goals. Our team has delivered more than 48,000 projects over 15 years.
You can explore our service and join here