Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Your security team is drowning in alerts. Every ping is a potential crisis, but most are just noise. This is the reality for businesses in Fullerton and across Orange County, where the volume of threats outpaces the capacity of human analysts. The solution isn’t just more staff; it’s smarter processes.
Security Orchestration, Automation, and Response (SOAR) implementation consulting provides the blueprint to turn that chaos into a coordinated, automated defense. It connects your disparate security tools, automates repetitive tasks, and ensures your team focuses on genuine threats.
We’ve seen it cut response times by more than half. Keep reading to understand how a structured SOAR engagement can secure your operations and give your team their focus back.
It usually starts quietly. One alert pings on the screen. Then ten more. By the end of the day, your Security Operations Center (SOC) is drowning in thousands of notifications.
The real issue isn’t only the volume, it’s the lack of connection between them. Your firewall logs sit in one place, endpoint protection data in another, email security alerts in yet another. None of them talk to each other in a meaningful way. So each alert feels isolated, stripped of context.
When that happens:
That’s how alert fatigue sets in. The mind just stops reacting to the constant stream, and dangerous signals get missed. For a mid-sized tech firm in Fullerton, this isn’t some abstract security theory. It’s a steady, daily drag on people, time, and attention, while risk quietly grows in the background [1].
A strong security program shouldn’t chase “more data” as its main goal. It should chase clarity, knowing what matters, when it matters, and why.
SOAR implementation steps into this mess and works like a central nervous system for all your security tools. Instead of treating alerts as scattered messages, it pulls them into one coordinated response system.
Here’s what it actually does:
From there, SOAR uses predefined logic and playbooks to:
This kind of setup doesn’t push humans out of the loop. It does the opposite. It frees your analysts from repetitive triage work, so they can:
SOAR doesn’t replace your team’s judgment. It gives them room to actually use it.
So, what does a SOAR consultant do? They don’t just install software. They begin with a deep assessment of your current security posture. This gap analysis looks at your tools, your processes, and your team’s skills. They identify where manual tasks are creating bottlenecks.
For instance, a simple phishing email might require an analyst to manually check five different databases. A consultant designs a playbook that automates those five checks in seconds, leveraging the power of security orchestration automation to streamline workflows and reduce human error.
The process is typically phased. It’s a journey from assessment to optimization.
This structured approach ensures the solution fits your business, not the other way around. The consultant’s role is to be a guide, translating complex security needs into an efficient, automated reality.
| Phase | What It Includes | Outcome for Your Team |
| Security Posture Assessment | Review of tools, processes, policies and skills | Clear view of gaps and priorities |
| Playbook Development | Design of automated workflows for common incidents | Faster and consistent response actions |
| Integration and Deployment | Connecting SOAR to SIEM, EDR, cloud and email tools | Unified workflow that reduces manual work |
| Training and Knowledge Transfer | Hands on sessions and documentation | Team can operate and modify SOAR confidently |
| Ongoing Optimization | Continuous tuning against new threats | Stronger automation accuracy over time |

You can almost feel the difference when a security team moves from reacting to actually staying ahead. That shift is where a solid SOAR platform proves its worth, not in theory, but in minutes saved and mistakes avoided. For most Fullerton businesses, the impact shows up in two main areas: time and accuracy.
Faster Response When It Matters Most One of the clearest numbers to watch is Mean Time to Respond (MTTR). That’s how long it takes your team to go from alert to action. With SOAR, a big chunk of the early work gets automated, such as data enrichment and initial triage.
This is exactly where a managed SOAR platform can deliver consistent and measurable improvements in efficiency and response times. For most Fullerton businesses, the impact shows up in two main areas: time and accuracy.
One of the clearest numbers to watch is Mean Time to Respond (MTTR). That’s how long it takes your team to go from alert to action.
With SOAR, a big chunk of the early work gets automated, such as:
When those steps run on their own, MTTR can drop by 50% or more. That’s not a small quality-of-life gain, that’s the difference between:
For a hospital, clinic, or bank in Orange County, that speed can protect patient records, transaction data, and even daily operations.
Speed helps, but consistency is what builds trust in the process. Manual workflows, especially under stress, leave room for:
SOAR uses automated playbooks so every incident follows a set, documented path. That means:
This structure supports compliance with frameworks and regulations such as:
You’re not just saying you follow a process, you can actually show it.
There’s also a human side here. When analysts spend most of the day clearing false positives or repeating the same checks, their skills stall out. SOAR helps shift their focus toward:
So the return on investment isn’t only about avoiding breaches or cutting losses. You end up with:
For a Fullerton business trying to stay secure without burning out its staff, that might be the most valuable change of all.
| Benefit Area | Manual Process Impact | With SOAR Implementation |
| Response Time (MTTR) | Hours spent on enrichment and triage | Reduction of 50 percent or more |
| Analyst Workload | Repeated manual checks and validation | Automated triage frees analysts for threat hunting |
| Consistency | Error prone steps under pressure | Standardized responses using automated playbooks |
| Compliance | Hard to maintain repeatable evidence | Playbooks enforce best practice and documentation |
You can usually tell pretty quickly whether a security consultant is there to help you, or just to sell you a product. That difference matters a lot when you’re picking a partner for SOAR implementation.
The truth is, not every consulting service works the same way. Some are tied closely to one vendor, while others stay more independent. That’s where you want to be careful.
When you’re evaluating a SOAR consulting partner, a few traits stand out as non-negotiable:
This kind of structure keeps the project grounded and measurable.
For businesses in Fullerton and the broader Orange County area, there’s a strong case for working with a regional consultant instead of someone completely remote.
A local or regional partner usually:
That proximity helps when your team needs:
Over time, the right consultant starts to function like an extension of your internal security team. They’re not just focused on turning the tool on, they’re watching how well it’s actually used.
That includes:
The goal isn’t to have SOAR sitting on a slide deck or as another unused tool. The real win is when your people use it well, and your security operations feel sharper, calmer, and more under control because of it.
You can almost feel the tension when a new automation tool gets announced. Some people lean in with curiosity, others lean back with worry. That mix of reactions is normal, especially in a SOC where work already feels intense. A common fear is simple: “Is this going to replace me?”
With SOAR, the reality is more layered than that. It doesn’t erase the need for skilled analysts, it shifts where their time and attention go. The key is to have strong outsourced security automation consulting that aligns people and technology, helping your team use automated processes without losing their critical judgment or control over security operations.
A common fear is simple: “Is this going to replace me?” With SOAR, the reality is more layered than that. It doesn’t erase the need for skilled analysts, it shifts where their time and attention go.
SOAR is best at the work humans usually dislike but still have to do, such as:
When those tasks are automated, your analysts can put their energy into:
We’ve seen SOC teams move from:
That kind of shift doesn’t happen by accident, though. It needs clear communication and good change management. People need to hear, directly and honestly, that:
When the message is right, SOAR feels less like a threat and more like a strong extra pair of hands.
Credits : IBM Technology
Good consulting in this space isn’t just wiring up tools and walking away. It should focus heavily on aligning human talent with the new technology.
That usually includes:
The deployments that work best are the ones where analysts feel:
When technology and talent grow together, the SOC starts to feel different. Less reactive, more steady. Automation handles the noise, your people handle the judgment. And that balance is where security operations become both efficient and resilient [2].
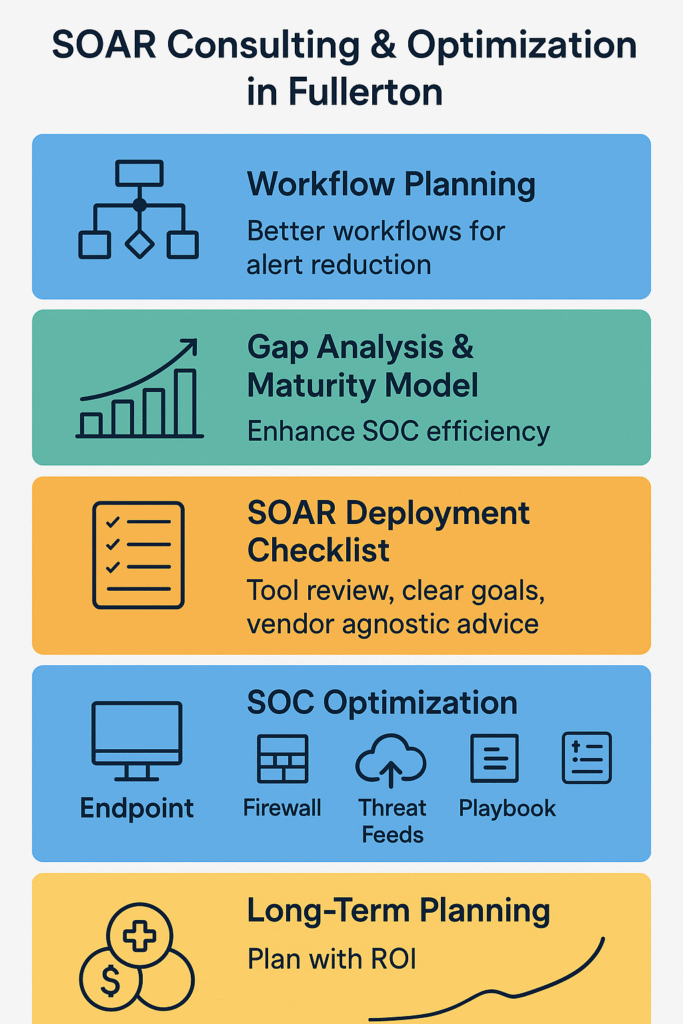
SOAR implementation consulting services in Fullerton help you plan better workflows. You get support with security orchestration automation response, incident response automation, threat detection integration, and SIEM SOAR connector setup. Consultants use gap analysis cybersecurity and the SOAR maturity model to find weak spots. This helps reduce alert fatigue and improve mean time to response reduction for your team.
You should look at your current tools and goals. A cybersecurity SOAR deployment needs clear requirements planning security and good resource management SOAR steps. You can review SOAR vendor selection options and get vendor agnostic advice. Many teams in Fullerton use playbook assessment services and SOAR playbook development to build strong plans before they go live.
Fullerton SOC optimization helps you use automated incident response in a practical way. You can add endpoint integration SOAR, firewall orchestration tools, and threat intelligence feeds. Teams also use phishing response automation and ransomware playbook design to cover common attacks. This work improves SOC efficiency consulting efforts and supports NIST compliance SOAR activities across your environment.
You need people who understand custom API integrations, workflow automation consulting, and performance tuning SOAR tasks. Many teams add SOAR training programs and SOC team upskilling to help staff grow. Southern California SOAR consultants also support stress testing playbooks and continuous playbook maintenance. These steps help with human capital alignment and talent alignment cybersecurity work.
Orange County SOAR experts guide teams through strategic security planning. They help with organizational security alignment and business process management. They support phased rollout strategy plans and ROI SOAR calculation. Many mid-sized business SOAR projects include healthcare incident response needs, finance SOAR solutions, and LA area security operations. These steps give leaders better decision support cybersecurity data.
Your team moves forward when you accept that manual security operations no longer scale. SOAR helps you shift from reacting to shaping your defense. You cut noise. You regain control. You focus on real risks. Start by reviewing your gaps. Set clear automation goals. Work with specialists who design solutions that match your environment.
You get guidance that covers needs analysis, vendor selection, PoC support, and integration planning. You improve visibility. You reduce tool sprawl. You strengthen your service quality with support backed by 15 years of experience and more than 48,000 completed projects.
Take your next step and join the experts at MSSP Security.