Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

The OWASP Top 10 isn’t a checklist. It’s a blueprint for building a website that…

Outsourced web application security is when you bring in outside experts to handle the testing…
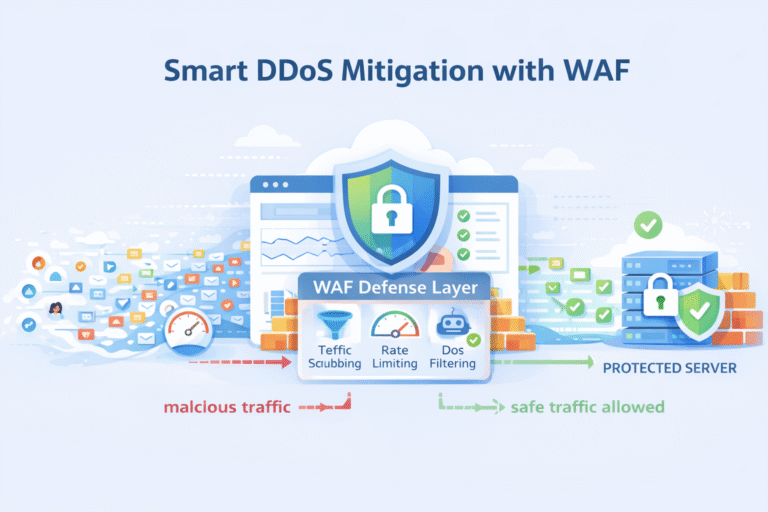
DDoS Protection Mitigation WAF solutions work together by spotting abnormal traffic, blocking malicious requests, and…
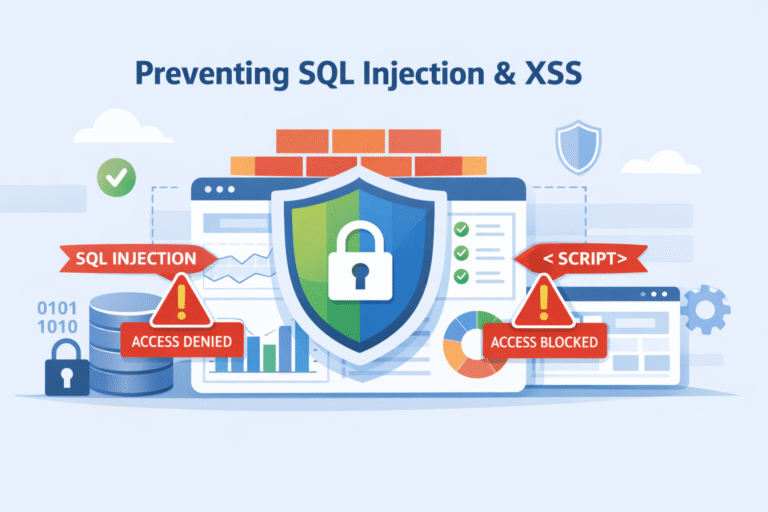
SQL injection and XSS attacks persist because developers still let untrusted input reach executable code.…