Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Getting a penetration testing coordination approved is just the first step. If you simply hand over the keys and wait, you risk an outage or a useless report. The real work happens before the hackers start. Success depends entirely on aligning your team’s daily operations with the tester’s plan.
Without this coordination, you’ll likely miss critical flaws or disrupt business. Based on managing hundreds of tests, we’ve built the framework that turns a compliance exercise into actual security. Find out where your process has a gap.

We’ve watched it fail firsthand. A client hires a firm, provides an IP range, and disengages. Then a production line stops because a scanner flooded a legacy controller. The financial hit is instant, and trust in the security process evaporates. This isn’t a tools failure. It’s a coordination failure.
“Coordinate your testing schedule with IT and choose off-peak times to minimize impact… let people know the test is coming and get proper approvals… and collaborate with third-party service providers on controlled systems.” – Interscale
In our work, we see three tensions that proper coordination must resolve:
| Area | Hands-Off Penetration Testing | Coordinated Penetration Testing |
| Operational impact | High risk of outages and system disruption | Testing aligned with production schedules |
| Asset awareness | Testers lack system context | Assets classified by business criticality |
| Safety controls | No real-time stop procedures | Clear emergency halt protocols |
| Findings quality | Many false priorities | Risks tied to real-world impact |
| Business trust | Low after disruptions | High due to controlled execution |
Managing these tensions isn’t optional. It’s what separates a valuable test from a chaotic one.
Credits: Loi Liang Yang
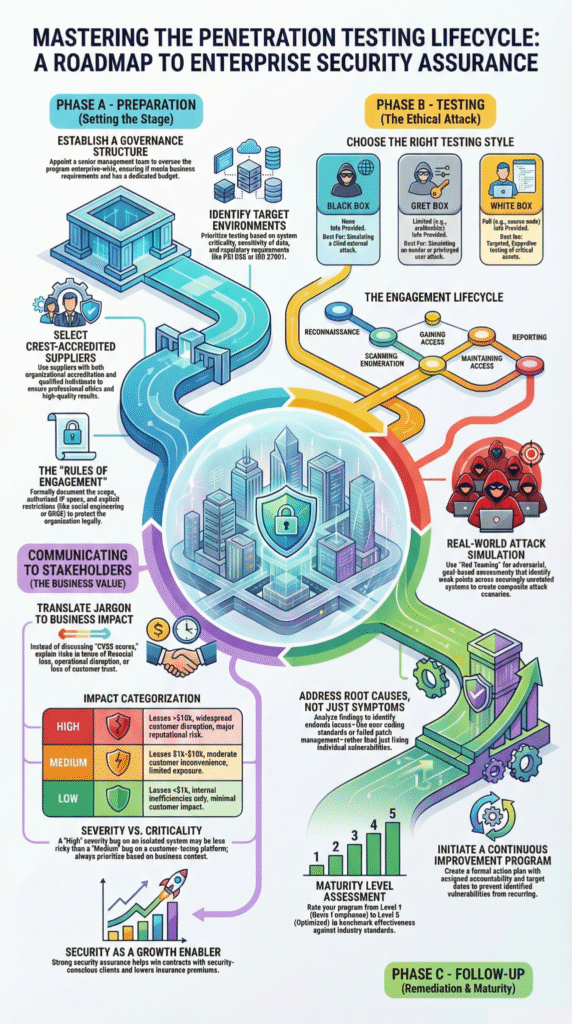
This phase is where success is decided. It moves the project from a vague “we need a test” to a concrete, safe engagement. Think of it as mission planning.
“Engage key stakeholders early, establish consensus on objectives and acceptable risk, appoint internal liaisons to coordinate testing activities, and define communication protocols for real-time updates and incident handling.” – Romexsoft
First, you must define the target. Scoping isn’t just listing IP addresses. It’s building a living asset register that classifies systems: Is this a public web server, a database with sensitive data, or a Level 1 controller on the factory floor? The scope dictates the methodology.
An application test follows OWASP guides, while an OT network assessment uses frameworks like NIST SP 800-82. Next, draft the Rules of Engagement. This document is your treaty. It must state:
For scheduling, you need more than security calendars aligned, many teams fix this fast through
outsourced pen test scheduling management that removes operational bottlenecks.
Once the plan is set, the test starts. Coordination doesn’t stop, it changes, this is where simulating real world attacks safely becomes the difference between useful insight and operational risk. Now it’s an active partnership.
The initial reconnaissance should use your network diagrams and asset lists. This isn’t cutting corners. It’s working smart. It lets testers use their tools, like a vulnerability scanner, more precisely. They spend less time mapping what you already know and more time finding what you don’t.
A “war room” setup is non-negotiable. Having your point of contact on standby means a tester can ask, “This service looks odd, can I probe it?” and get an answer fast. A real attacker wouldn’t ask. Your ethical hacker has to. Your immediate response, “That’s the legacy batch server, be gentle”, prevents an outage and keeps the test on track.
It’s also where many teams discover gaps in compliance penetration testing requirements before auditors do. Testers check if the controls mandated by your SOC 2 or ISO 27001 framework actually work. Is the segmentation you documented real? Coordination lets them verify this without hammering every system.
The report arrives. It’s 80 pages long, filled with terms like SQL injection and CVSS scores. This is the moment where many programs falter. The technical team feels overwhelmed, leadership sees a giant cost, and nothing gets fixed. Interpreting penetration test results properly is what turns a dense report into clear remediation priorities.
A critical vulnerability on an isolated, non-Internet-facing test server is technically severe but poses low immediate risk. A medium-severity flaw on your public customer portal is a five-alarm fire. Without that context, teams waste months patching the wrong issues, prioritizing pen test findings for remediation keeps effort focused on real business risk. You must ask:
This is where a structured risk management tool helps. Don’t just work down the list from Critical to Low. Triage based on exploitability and impact, creating a remediation roadmap with clear owners (application owner, system owner) and deadlines.
The role of the coordinator is to shepherd this process, ensuring the security team doesn’t get bogged down in low-priority items while critical gaps remain open.
A penetration test is just a snapshot. Your threat landscape is a movie. The real value of a coordinated test isn’t just fixing last month’s flaws. It’s building a stronger system for next month’s threats.
The findings should directly feed your security program. Update your policies. Train your developers on the coding mistakes that created the flaws. Most importantly, use the insights for internal practice. Many mature programs level up by coordinating red team blue team exercises to continuously pressure-test detection and response.
When the next external assessment comes around, your process is sharper. You have better asset lists, more aware staff, and a clearer picture of what truly matters. This maturation is the goal, turning a point-in-time expense into a continuous driver of stronger security.
You know you need a test. The question is how to run it.
When vendor quality varies wildly, choosing a penetration testing vendor carefully prevents wasted budget and weak test coverage. This demands significant time from a security team already juggling daily alerts and projects.
Or, you can remove the chaos entirely by using managed penetration testing coordination that handles scoping, execution, and follow-through as one controlled process. A partner that doesn’t just sell a test, but manages the entire lifecycle.
From the initial scoping call to the final remediation review, they handle the complex orchestration. This turns a disruptive, one-off project into an integrated part of your security operations.
For many of the MSSPs we advise, this managed approach is the difference between a PDF that gathers dust and a process that genuinely reduces risk for their clients. It’s what lets them focus on their core service, while ensuring their own security validation is thorough and safe.
Penetration testing coordination aligns your security team, application owner, and system owner before any penetration test begins. It defines testing windows, a clear point of contact, and pre-testing groundwork like asset inventory and network diagrams.
This prevents online attacks from disrupting Internet-facing applications, cloud services, or network infrastructure while still exposing real security vulnerabilities across your attack surface.
Strong preparation includes asset inventory, data flows mapping, data classification, and security policies documentation. A readiness checklist should cover active ports, API endpoints, storage buckets, system credentials, and physical assets.
This groundwork helps ethical hackers use penetration testing methodologies effectively while ensuring vulnerability scanning and port scanner tools focus on high-risk attack surfaces.
Vulnerability scanning only identifies potential cybersecurity weaknesses using automated tools and a vulnerability database. Coordinated penetration testing goes further by simulating attack patterns like SQL injection, brute force attacks, malformed data exploitation, and ethical hacking scenarios.
It follows structured frameworks such as the Penetration Testing Execution Standard and OWASP Web Security Testing Guide for real-world security assessment.
Clear coordination connects penetration testing reports directly to remediation steps and remediation actions. Findings are mapped to business impact, compliance frameworks, and security strategy priorities.
Security experts can quickly assign fixes to the right application owner or system owner, improving cybersecurity defenses, strengthening security posture, and supporting ongoing security health checks across the threat landscape.
A penetration test is only as good as the context you provide. The technical findings are just data. The real value comes from the structured conversation between the people who know how to break things and the people who know how to keep the business running.
Without it, you get noise and disruption. With it, you get a clear, actionable roadmap that ties security spending directly to business risk. The goal is a more resilient organization.
Your next step: Let’s simplify this process. Our team provides vendor-neutral consulting for MSSPs, from product selection and auditing to stack optimization. We help you cut through the noise, choose the right tools, and build a resilient tech stack. Schedule your free consultation to get started.