Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Malware analysis reverse engineering is just the methodical study of malicious code so you can see how it behaves and how to shut it down. No drama, no myth, just structured work. You trace how the code runs, what processes it starts, which files or keys it touches, and how it talks to the network.
From there, patterns appear: how it spreads, how it hides, and how it damages systems. At MSSP Security, we handle this daily and see how it tightens real defenses.
If you want clearer visibility and stronger response, keep reading.
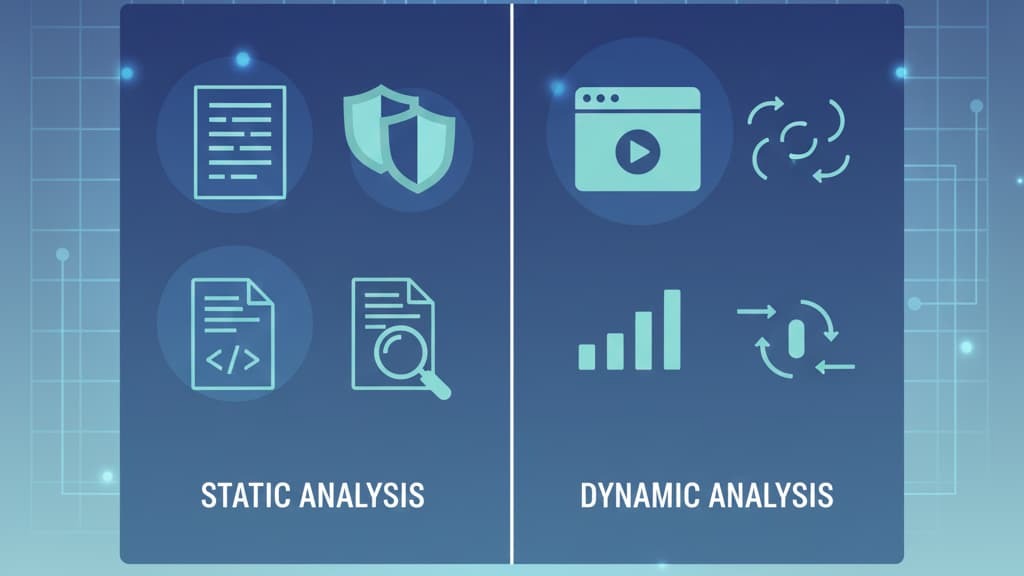
Malware analysis and reverse engineering sit at the center of how we evaluate security products for our MSSP clients.
When we break down malicious code, we’re not doing it for curiosity alone, we’re testing whether a product actually sees what matters: malware behavior, indicators, network patterns, memory activity, and payload effects that show up in real incidents.
From the outside, terms like static analysis, dynamic analysis, unpacking malware, or code obfuscation sound heavy, almost academic. Inside an engagement, they’re just different ways we prod a tool and a sample to see how deep the visibility really goes.
The goal stays simple: look into the threat without letting it touch production, then ask, “Does this platform help or get in the way?”
There’s a moment in every good case where malware starts to feel like a story. Some analysts describe it like reading a mystery novel backward, and that’s close to how our team experiences it.
When we work on an MSSP incident response review after a breach, the first question is always the same: what did the malicious code want, and did the tools our client relies on even notice the plot?
Reverse engineering tools such as disassemblers and debuggers give us a way to test that, line by line if needed. We see which products surface hidden variants, map malware families correctly, or expose C2 communication patterns instead of just saying “suspicious activity detected.”
Our job is to separate marketing claims from what actually works, so MSSPs can choose and audit products that stand up to real malware, not just test scripts.
Credits: Motasem Hamdan
Malware analysis is the practice of studying malicious code to understand what it’s trying to do and how it does it. For our team, it’s one of the key ways we test whether a product can actually support an MSSP during a live intrusion, especially when dealing with complex incidents that require malware incident response workflows.
When we pull apart a sample, we’re looking for more than just a label, we’re checking if a platform can surface exploited weaknesses, trace intrusion damage, and support real incident response and forensic analysis.
From what we’ve seen in our own reviews, malware analysis really does expose the intent behind an attack. During one product audit, a tool completely missed a hidden encryption routine in a ransomware sample, while another flagged it and mapped the behavior clearly. In another engagement, memory dump analysis revealed a rootkit that only one EDR even hinted at.
That’s the gap our clients care about: what an engine claims to detect versus what it actually shows under pressure.
The question we hear most from MSSP leaders is why this level of analysis matters when they already have alerts and dashboards. For us, the answer comes back to speed and clarity. When an attack lands, the fastest containment comes from understanding the code’s behavior, not just its name.
That’s where static code review, malware forensics, and malware log analysis prove themselves. They don’t just solve today’s case, they feed into forensic readiness planning, so the next time something slips through, the MSSP and its tools are better prepared instead of starting from zero. [1]
There are three main types: static, dynamic, and hybrid.
As reports often mention, “runtime analysis reveals what static analysis cannot.” We’ve seen malware sandbox evasion too, where threats try to hide activity if they detect virtual environments.
Reverse engineering malware means tearing it apart piece by piece. Analysts disassemble or decompile malicious code to study logic, algorithms, encryption, and communication routines. Reverse engineering tools like IDA Pro, Ghidra, and Radare2 help map binary analysis, malware strings extraction, and binary reversing.
Many guides say reverse engineering “exposes what malware tries hardest to hide.” That has been true in every case we’ve handled. Through malware debugging techniques, API hooking, or malware unpacking tools, hidden behavior surfaces. Malicious code often includes encryption analysis challenges or decryption techniques that require careful examination.
For highly sophisticated threats, rootkits, fileless malware, or stealthy C2 communication, reverse engineering is the only way to truly understand them. This work helps create malware detection rules, malware signature creation, and defensive patches.
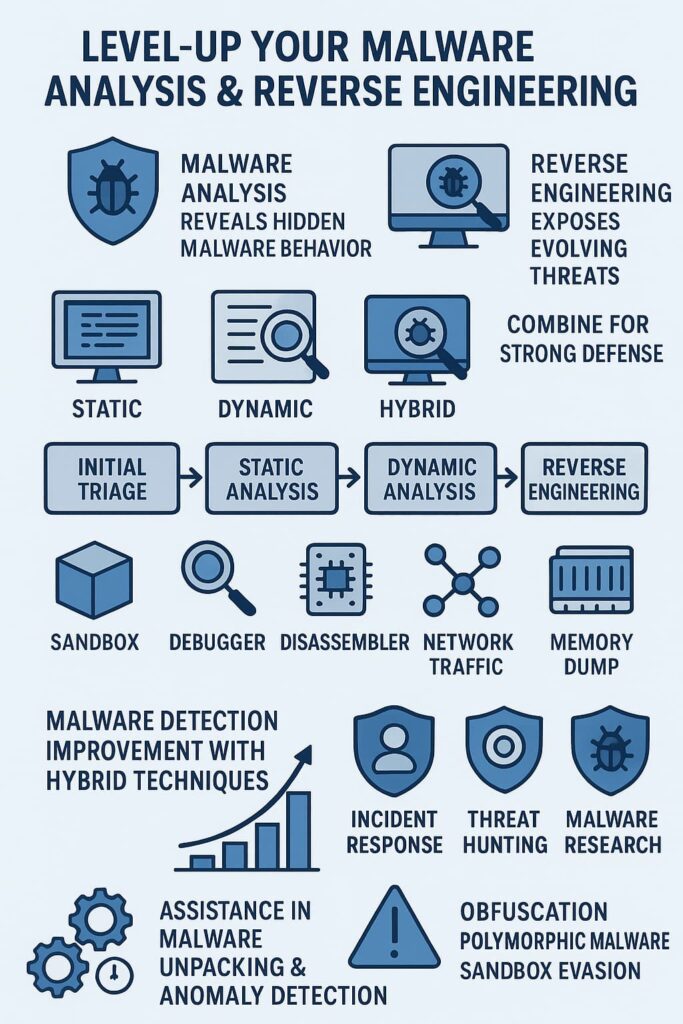
Analysts follow four main steps:
Step 1: Initial Triage
This includes file name checks, hashing, metadata review, and isolating the sample. Malware triage helps determine whether it’s ransomware, a trojan, or a malicious payload dropper. Many teams use malware sandbox tools here.
Step 2: Static Analysis
Strings, headers, sections, and resource checks reveal clues. Malware indicators become visible. Sometimes, we see hints of malware injection or malware evasion techniques.
Step 3: Dynamic Analysis
This phase monitors system behavior during execution: registry changes, network malware detection, and memory interactions. Some threats attempt anti-debugging tricks or sandbox evasion.
Step 4: Reverse Engineering
Disassemblers expose hidden logic. Analysts uncover encryption routines or C2 communication channels. The final goal: create detection signatures, strengthen defenses, and guide incident response forensic analysis for rapid incident containment forensics.
This structured flow remains consistent across outsourced digital forensics investigation teams and managed DFIR retainer service providers.
Organizations rely on these practices for critical reasons:
Incident Response
When malware hits, responders must contain it fast. Effective handling aligns closely with broader digital-forensics-incident-response-dfir operations, where malware analysis exposes what the threat is doing and supports rapid decision-making.
Threat Hunting
Threat hunters search for malicious code that hides inside networks. Malware behavior analysis and memory analysis help trace suspicious activity. We often use threat intelligence hits to connect malware infrastructure analysis patterns.
Threat Alerts and Triage
Security teams often drown in alerts. Malware classification and payload extraction help prioritize the dangerous ones. Malware behavior profiling simplifies things for defenders.
Malware Research
Researchers study malware variants and polymorphic malware to understand new attack tactics. This leads to stronger detection systems and improved vulnerability assessment.
These use cases directly support benefits MSSP DFIR support teams deliver, calmer workflows, faster containment, and cleaner evidence preservation handling forensics readiness planning.
Modern malware is messy. Obfuscation techniques grow stronger. Packed malware hides logic. Encryption layers block analysis. Polymorphic and metamorphic malware constantly change shape. Fileless malware leaves almost nothing behind. Some malware families deploy anti-debugging tricks to detect reverse engineering tools and shut down.
As one expert said, “you are not just chasing code, you are chasing someone who does not want you to find them.” We’ve watched malware detect virtual machines, block debuggers, and alter behavior when monitored.
This makes memory dump analysis, rootkit detection, and forensic analysis malware work more important than ever. Even with strong tools, complexity continues rising. [2]

Automation helps reduce manual work. Tools like malware sandbox automation speed up sample processing. AI models support malware detection, malware classification, and anomaly spotting. Many analysts rely on machine learning to review network traffic analysis or detect malware evasion techniques.
Reports say that “automation accelerates reverse engineering without replacing the human mind.” And that’s true. We use it daily at MSSP Security, AI flags suspicious system calls, while automation handles repetitive unpacking malware tasks.
Automated malware analysis platforms examine patterns at scale. Predictive systems may detect C2 communication anomalies or memory injection patterns before a threat fully executes. Automation helps incident response forensic analysis and post-incident remediation reporting become faster and more accurate.
Still, human expertise remains key, especially for deep reverse engineering process challenges.
Beginners can start small by learning malware analysis basics like static analysis and dynamic analysis. Checking simple malicious code samples helps them see malware behavior.
They can practice with a malware sandbox to watch malware execution in a safe way. Using a debugger or disassembler later helps them follow the reverse engineering process at their own pace.
A file may need malware forensics when it shows strange malware indicators, odd memory analysis results, or fails normal malware detection checks. Packed malware, polymorphic malware, or metamorphic malware often hide inside layers.
In these cases, unpacking malware or using a malware unpacker can reveal the malicious payload for closer malware behavior analysis.
Analysts often check network traffic analysis by watching packet inspection and C2 communication in a closed space. They track command and control patterns and network malware detection signals.
Runtime analysis or system calls tracing helps show what the malware tries to send out. This keeps threat hunting focused while keeping the system safe from malware injection.
Some analysts use reverse engineering tools to handle binary analysis or binary reversing. They look at code obfuscation, malware strings extraction, and encryption analysis to find clues.
A disassembler helps show how malware variants work, while cryptographic analysis and decryption techniques help reveal malware behavior that hides behind complex malware evasion techniques
Malware analysis and reverse engineering help defenders understand hidden malicious behavior and stay ahead of evolving threats. Using static, dynamic, and hybrid methods builds stronger defenses and improves response speed.
With automation, skilled analysts, and a solid workflow, organizations can manage threats more confidently. At MSSP Security, these practices guide our daily operations to keep systems protected.
Strengthen your capabilities with us.