Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Identity Access Management (IAM) support matters because identity is now the main path attackers use to get in. Cloud services, remote work, and vendor access have stretched credentials beyond old network borders, often faster than internal teams can keep up.
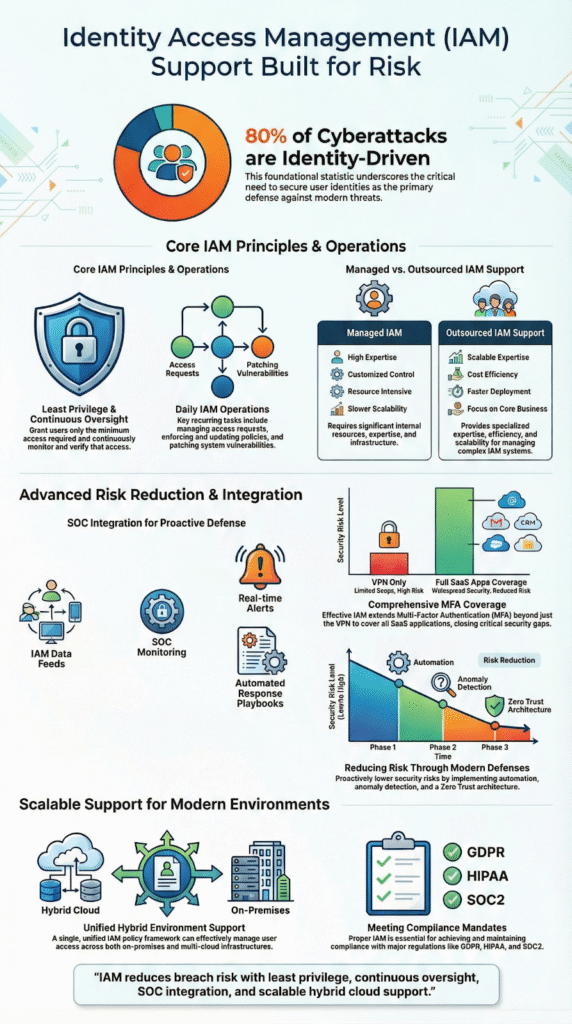
In fact, approximately 80% of all cyberattacks are identity-driven, exploiting compromised credentials as the primary route into systems [1]. When it works well, organizations see fewer access-driven incidents, cleaner audits, and access that matches how the business actually runs. Keep reading to see how effective IAM support works day to day.
We’ve seen many MSSPs burn out their teams trying to “own” every IAM platform by themselves. Tickets pile up, policies drift, and no one has time to step back and ask, “Is this still the right model?”
That’s where managed IAM support services come in.
For MSSPs, these services keep identity platforms healthy and consistent so the SOC is not fighting access chaos on top of real threats.
Managed IAM support services usually cover:
When complexity grows, multiple clouds, legacy on-prem apps, remote users, this kind of managed support keeps identity from turning into a long list of exceptions.
At MSSP Security, we help MSSPs review and compare managed IAM offerings, test how they behave under real pressure, and audit whether they actually enforce least privilege, not just promise it in a slide deck.
Some MSSPs decide they don’t want to run identity operations at all. They want to design, oversee, and own the client relationship, but let someone else handle daily identity execution.
We’ve seen this work well when:
Outsourced IAM usually includes:
We’ve helped MSSPs audit outsourced IAM providers and learned something pretty clear: the best setup is when governance stays with the MSSP and its client, while daily execution is handled externally under tight rules and transparent reporting.
Identity gets much stronger when IAM and the SOC stop acting like separate worlds.
We’ve watched this shift happen first-hand. When integrating iam with mssp soc, strong setups usually include:
As identity-centric security research notes, “Zero Trust Architecture shifts the security paradigm by assuming that no user, device, or system can be trusted by default, requires continuous verification and the enforcement of least privilege access for all entities” [2].
Credential misuse keeps showing up as a top breach vector in major reports. In our work, the MSSPs that do best are the ones that treat identity events as first-class SOC signals, not an afterthought.
The accounts that scare us most are not regular users. They’re the ones that can touch domain controllers, core databases, payment systems, privileged accounts.
From what we’ve seen across many MSSPs, effective PAM focuses on:
We regularly help MSSPs review PAM platforms and validate if the monitoring is real or just basic logging. The goal is simple: limit the blast radius if a privileged account is ever compromised, and make sure there’s a clear trail when something goes wrong.
Identity governance administration (IGA) support is what keeps those questions answered and documented over time.
When IGA is missing, we usually see:
Strong IGA support for MSSPs and their clients usually includes:
We help MSSPs compare IGA tools and check whether they fit into the existing tech stack, reporting needs, and client size. The better the IGA support, the easier it is to say “yes” or “no” to access with a straight face and clean record.
Most MSSPs already know they need multi factor authentication. The real gap is in multi factor authentication (mfa) management, actually enforcing it, tuning it, and making it workable for users.
Effective MFA management usually covers:
At MSSP Security, we often help MSSPs evaluate MFA and access control tools, not just for security strength but for how they impact user friction. The goal is high adoption and strong enforcement, not angry users bypassing controls.
Picking an IAM support provider doesn’t just affect this quarter. It shapes how identity, risk, and compliance will feel for years.
We’ve helped MSSPs evaluate providers and have learned that slideware looks similar, but real capability does not. When choosing iam support provider options, we usually walk MSSPs through questions like:
We position MSSP Security as a first stop for many MSSPs who want an honest, experience-based view of the tools and providers they’re considering. Our focus is on matching real needs with real capabilities, not chasing the newest buzzword.
User access review support turns that idea into a regular, repeatable process.
In our work, effective access reviews look like this:
We’ve watched MSSPs move from “yearly panic before audit” to smooth, quarterly or continuous reviews. When done well, these reviews:
Access reviews are one of the lowest-cost ways to cut identity risk. They don’t require new hardware or huge change, they require discipline, good tooling, and clear ownership.
Securing identities cloud on prem means unifying how access is granted, used, and monitored across very different systems.
Common focus areas for MSSPs and their clients include:
When we help MSSPs audit or select tools here, we’re usually looking at questions like:
A simple hybrid IAM comparison often looks like this:
| Capability | Cloud IAM Security | On Premises IAM |
| Visibility | High, API-driven | Moderate, directory-based |
| Scalability | Elastic | Hardware-bound |
| Compliance | Shared responsibility | Full organizational control |
| Risk Exposure | Misconfiguration | Legacy privilege sprawl |
This is why hybrid IAM support demands real experience. At MSSP Security, we work with MSSPs to review and test tools that can handle both sides without turning operations into chaos.
Identity isn’t a “set it and forget it” control. It’s a moving target.
Reducing identity related risks means treating IAM as a continuous practice, watching behavior, tightening access, and responding fast when something feels off.
From our time in the field with MSSPs, strong programs usually rely on:
MSSP Security often steps in as the quiet partner in the background, helping MSSPs select, test, and audit the IAM, MFA, PAM, and IGA tools that fit their clients’ risk and growth plans.
When IAM support is done right, you get fewer surprises, smoother audits, and a security posture that actually keeps up with how people work. That’s where identity stops being just a problem to manage and starts becoming a way to run the business with more confidence.
For MSSPs that need deeper validation, design review, or pressure testing beyond day-to-day operations, this work often extends into advanced & specialized services, covering complex IAM integrations, high-risk environments, and situations where standard managed support is not enough.
Identity Access Management (IAM) support handles who can access systems and data every day. This includes setting up new users, removing access when people leave, and changing access when roles change. Teams manage MFA, role based access control, and user access reviews. They also handle audits and reports to reduce identity risk without slowing work.
Companies use managed IAM services or outsourced IAM when access grows too complex. This often happens with cloud use, remote work, or many vendors and contractors. Outsourced IAM helps control access, apply least privilege, and keep reviews on track. It lets internal teams focus on business while IAM experts manage daily identity tasks.
IAM support connects identity activity to SOC monitoring. SOC IAM integration helps track privileged access, session activity, and unusual behavior. These signals support identity threat detection and faster incident response. When identity data reaches the SOC early, teams can stop misuse faster and reduce the chance of a larger security incident.
IAM support keeps access clean and easy to review. Identity governance support manages access checks, separation of duties, and approval workflows. IAM reporting helps meet GDPR, HIPAA, PCI DSS, and SOC2 needs. Strong IAM auditing reduces audit stress and prevents last-minute access fixes before compliance reviews start.
IAM provider selection should focus on real experience, not tools alone. Teams should look for support with hybrid IAM, cloud identity security, and on premises IAM. The provider should handle IAM automation, MFA management, and growth over time. Clear reporting, simple processes, and identity risk reduction matter most.
Identity Access Management (IAM) support now drives both security and business outcomes. It helps organizations grow safely, meet compliance needs, and stay resilient as identity replaces the network perimeter. Managed and outsourced IAM bring clearer access control, faster decisions, and lower identity risk across cloud and on-prem environments.
Work with us to build IAM support that scales with your business, backed by deep MSSP consulting experience, practical stack optimization, and clear guidance that turns identity strategy into daily operations.