Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Choosing an OT security monitoring provider in California means prioritizing safety, uptime, and regulatory alignment over traditional IT-style threat detection. In our experience with manufacturing plants and utilities across the state, the wrong choice can increase downtime risk instead of reducing it.
California’s utilities, food processors, and water districts operate under strict oversight from bodies like the California Public Utilities Commission, making OT security a board-level issue.
This guide explains what actually matters when selecting a provider and why local, OT-first expertise changes outcomes. Keep reading to avoid the common mistakes we see during RFPs and pilot deployments.
OT security monitoring is fundamentally different because its primary goal is to keep physical processes safe and running. In IT, a security scan might be an annoyance; in OT, it can stop a production line or a water treatment process. Because of this, providers must move away from “active” IT methods that can crash legacy PLCs.
As industrial environments converge with digital networks, the criteria for a provider must shift from traditional data protection to the safety of the physical environment itself.
“Vulnerability Management [in OT]: Leverage both active query and passive monitoring for safe assessment of OT devices. … The potential consequences of such cyber attacks are not just financial but can also disrupt critical infrastructure and even cause injury or death.” – IBM Consulting [1]
Effective OT monitoring focuses on a few key traits:
This focus on uptime, safety, and passive observation is the baseline for evaluating any provider. It’s why an IT-centric security model will struggle and potentially cause harm in an industrial setting.

OT security providers in California need to support a mix of state and federal standards. While the California Public Utilities Commission (CPUC) sets the tone for local energy and water sectors, federal guidance provides the technical roadmap.
NIST SP 800-82 is the authoritative framework for securing Industrial Control Systems (ICS). When evaluating an MSSP, look for a “compliance-by-design” approach where their monitoring directly supports these high-level executive and board concerns.
“Boards may not always distinguish between IT and OT attacks, but they do care about safety and uptime. … Unlike IT, where systems are regularly updated and replaced, OT systems often operate for decades. … [A provider must address] OT-specific risks rather than simply connecting OT systems to IT.” – Forbes Technology Council [2]
In our work evaluating providers for MSSPs, the strong ones show compliance through their product’s design, not just a checklist. They can clearly explain how their monitoring directly supports:
This practical alignment is what separates a provider that helps you pass an audit from one that actually helps you manage risk.
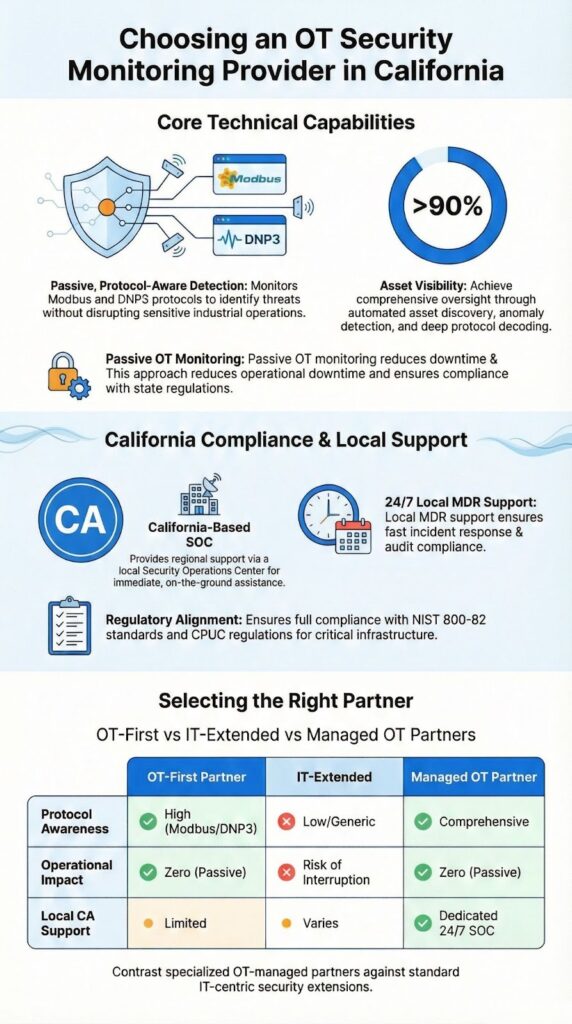
An OT monitoring provider needs a few core technical capabilities built for industrial reality. Operational technology OT security monitoring ensures passive asset discovery, behavioral anomaly detection, and deep ICS protocol support without installing agents on PLCs, HMIs, or other controllers.
Protocol awareness is absolutely essential. If it can’t tell the difference between a normal “read” request and an unauthorized “write” command, the alerts it generates will be useless to your engineers.
Threat detection must be behavioral, not just based on known malware signatures. OT attacks often use legitimate commands in malicious ways. The platform needs to learn what normal traffic looks like for each machine and flag deviations, like a sensor reporting data at the wrong interval, that could indicate a safety or availability risk.
The core capabilities to verify are:
The real value isn’t just in the tool generating an alert, but in how it integrates into an OT Security Operations Center for a clear, timely response.

Leading OT security providers differ significantly in their protocol expertise, managed service maturity, and local support for California. When helping MSSPs evaluate options, we see buyers typically focus on a handful of OT-first platforms, judging them more on capability and service fit than brand name.
The key differences often come down to a few points:
Organizations often compare providers across a few key areas during an RFP. The table below reflects common evaluation criteria:
| Capability Area | OT-First Platform | IT-Extended Platform | Managed OT Partner |
| Protocol Depth | Native ICS decoding | Limited adapters | Native + curated intelligence |
| Asset Discovery | Passive only | Hybrid (active & passive) | Passive only |
| MDR Availability | Optional add-on | Limited or none | 24/7 OT-focused MDR |
| California Presence | Varies by vendor | National coverage | Regional focus & engineers |
At MSSP Security, we position ourselves as that managed OT partner offering advanced specialized services. Our team delivers local engineering support, OT-aware monitoring, and vendor-neutral guidance while protecting industrial operations in California without disruptive technology changes.
Local presence and MDR support are critical in California, especially for securing industrial control systems (ICS). On-site engineers, OT-aware MDR coverage, and immediate response help contain incidents, communicate with regulators, and maintain uptime for utilities, manufacturing, and water treatment facilities.
We’ve been part of response efforts where having an engineer on-site within hours, not days, made a tangible difference in containment and recovery. Being able to coordinate from a hub in the state matters during a grid or water system disruption.
A 24/7 OT-focused MDR service also reduces the operational burden on your team. Many facilities run with lean staff. Having alerts triaged by security engineers who understand the difference between a nuisance and a real process safety risk is invaluable.
Local MDR support typically improves a few key areas:
The California Public Utilities Commission explicitly emphasizes preparedness and coordination in its guidance, which reinforces why regional expertise and support are so valuable for any organization under its oversight.
Credits: CRN Spotlight: Illuminating the IT Channel
For OT-IT convergence, integration isn’t just about sending data to a SIEM. It’s about sharing the right context so your IT security team understands what’s happening on the factory floor. Industry surveys indicate about 60% of organizations are working on some form of convergence, but the risk is losing that crucial industrial meaning when data hits IT systems.
Alerts from the OT network should enrich the enterprise SIEM, but they shouldn’t trigger automated IT responses that could accidentally shut down a process.
From our deployments and product evaluations, integration works best when the provider supports a few key requirements:
Ultimately, convergence is less about the tools and more about the workflow. Providers that truly understand both the OT and IT worlds can build integrations that reduce friction and prevent alert fatigue, turning raw data into actionable intelligence.
You should choose an OT security monitoring California provider with proven experience in industrial and utility environments.
The provider must support real-time OT monitoring, passive OT asset discovery, and OT network detection response. They should understand California regulatory requirements and protect industrial control systems without disrupting production or safety operations.
Operational technology cybersecurity providers CA should deliver deep packet inspection for ICS, accurate anomaly detection for SCADA systems, and continuous threat detection in industrial environments.
They must support legacy OT protocols such as Modbus, DNP3, IEC 61850, and Profibus. Strong asset visibility, OT vulnerability management, and OT SIEM integration are also required.
Compliance knowledge is essential when securing OT environments in California. Providers must support NIST 800-82 compliance CA, CPUC regulations for OT security, and NERC CIP monitoring for the utility sector. They should also perform OT risk assessments and compliance auditing for industrial control systems to meet regulatory and operational requirements.
OT monitoring services should always include 24/7 managed detection and response. This includes access to an OT security operations center, defined OT incident response services, and OT forensics tools.
Continuous coverage enables faster containment of ransomware, supports supply chain OT security, and minimizes downtime across critical infrastructure environments.
You should evaluate cost by reviewing OT security ROI metrics and total cost of ownership for OT solutions in California. Providers must explain how OT segmentation strategies, zero trust OT architecture, and high availability OT security reduce operational risk. Clear pricing models help both SMB and enterprise environments justify long-term OT cybersecurity investments.
Choosing an OT security provider in California requires trust and deep technical knowledge. Look for passive monitoring, regulatory alignment, and experienced OT responders. At MSSP Security, we know security must integrate with operations, not disrupt them. The right provider joins the engineering team, offering clear support.
Our vendor-neutral consulting helps MSSPs streamline operations. We assist with product selection, auditing, and optimizing your tech stack to build resilient, effective security.