Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
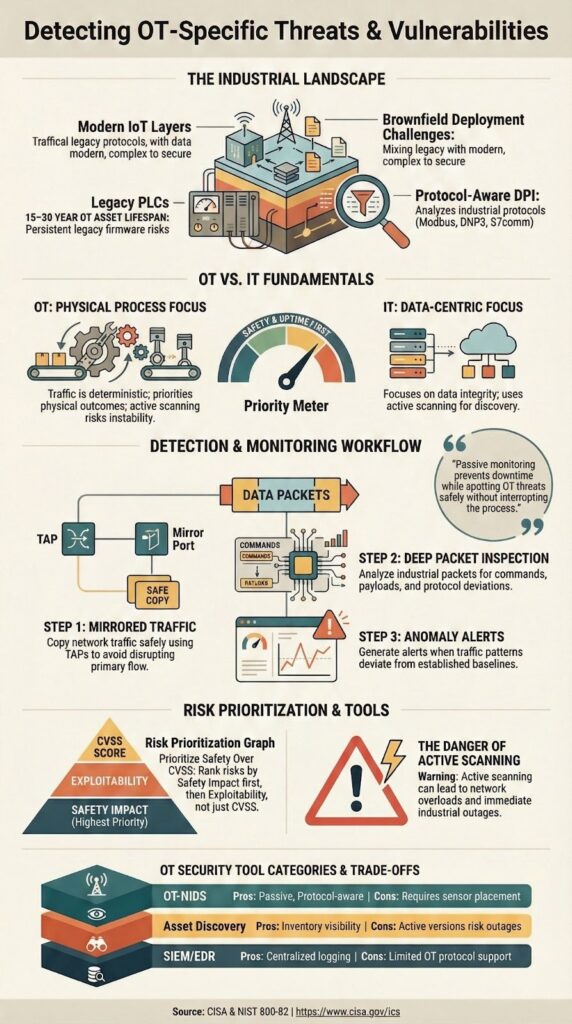
Detecting OT-specific threats and vulnerabilities requires passive, protocol-aware monitoring. Industrial systems prioritize safety and uptime, making disruptive active scanning or frequent patching impossible.
Since incidents like Stuxnet in 2010, it’s been clear that OT attacks aim for physical damage, not just data theft. We’ve seen firsthand how legacy controllers, flat networks, and limited visibility create critical blind spots across manufacturing, energy, and utilities.
This guide explains how organizations can detect OT security threats, assess ICS vulnerabilities, and reduce risk without ever breaking production. Keep reading to see how disciplined, realistic detection actually functions in live industrial environments.
OT-specific threats are different because they target the physical world. An attack isn’t about stealing data; it’s about making a turbine overspeed, a valve stick open, or a production line halt. When a SCADA system fails, the consequences are immediate and tangible.
In our work with MSSPs, we see how this reality changes everything. This fundamental difference in objective is supported by recent academic findings:
“Traditional IT cyber resilience targets data confidentiality, user accessibility and scalability… However, due to their unique design, nature, and functionality, conventional security mechanisms are often not applicable to the OT domain.” – Aalborg University [1]
The key differences that shape OT threat detection are:
This is why effective OT security relies on passive anomaly detection, not the active scanning and frequent updates common in IT. It’s about watching for the subtle deviation in a command sequence that could precede a major operational failure.

Passive network monitoring detects OT threats by listening, not touching. It works by analyzing a copy of the network traffic from a SPAN port or tap, so it never sends a single packet to the fragile controllers.
This form of OT security monitoring allows teams to detect behavioral deviations without interfering with deterministic control traffic. This makes it the only safe starting point in a live production environment.
Because OT traffic is so predictable, a PLC might poll a sensor every second for years, it’s perfect for baselining. Once you know what “normal” looks like, even a tiny deviation in timing or an unexpected command stands out clearly.
In our product evaluations for MSSPs, we look for tools that excel at:
Beyond threat detection, it also passively discovers every device on the network and provides the clean, enriched data needed for OT SIEM integration, all with zero operational risk.
The most commonly exploited OT vulnerabilities aren’t new or sophisticated. They’re the persistent, foundational weaknesses built into industrial environments.
Organizations that rely on advanced specialized services are better positioned to identify legacy exposure paths that remain invisible to traditional IT-focused assessments. Attackers repeatedly target unpatched firmware, insecure protocols, and poor network segmentation.
In our assessments for MSSPs, we see the same patterns. Data shows OT-specific vulnerabilities often remain exploitable for years because the devices simply can’t be patched without taking a production line down. Legacy firmware on PLCs and RTUs is the most common issue.
The high-risk vulnerability categories we consistently find are:
We’ve seen firsthand how a single misconfigured jump server can breach the Purdue Model, letting an attacker move from the corporate email system directly into the control network. These segmentation failures are a primary reason ransomware and targeted attacks can cause such widespread operational damage.
Active scanning is risky in OT because it can directly crash the equipment. A standard IT vulnerability scan sends unexpected packets and connection requests that can overload a PLC or RTU, causing it to stop responding.
This is why many operations favor managed OT security monitoring approaches that emphasize passive detection over intrusive validation techniques. We’ve seen this happen during product evaluations, a scanner that works fine in an office can halt a production line because it misinterprets the industrial protocol.
There are limited, controlled scenarios where active methods might be used. A vendor’s own diagnostic tool, running a specific protocol query during a planned maintenance window, is one example. But for routine security assessments, passive methods are the only safe choice.
Safer alternatives include:
These approaches provide the necessary security coverage while preserving the stability and trust of the operational environment. In OT, the first rule is to do no harm.

Detecting OT threats requires a combination of specialized tools. No single solution covers everything, especially given the limited logging and host visibility in these environments. The most effective approach uses layers of detection that work together.
Modern research from the European Conference on Cyber Warfare and Security emphasizes that a siloed approach to these tools often misses the most sophisticated attacks:
“All threats are not found by monitoring data separately from IT or OT sources but we identified hidden threats by monitoring and comparing IT and OT data. This research focuses on… combining data from IT and OT sensors and logs to enhance SOC’s situational awareness.” – ECCWS [2]
The core tools typically include:
Here’s a quick comparison of their roles:
| Tool Type | Primary Strength | Key Limitation |
| OT-NIDS | Protocol visibility & anomaly detection | Limited insight into the host itself |
| Asset Discovery | Accurate, live OT inventory | Depends on update frequency and network coverage |
| SIEM/EDR | IT-OT event correlation | Sparse, non-standard OT logs |
Supporting these are capabilities like OT-specific threat intelligence, safe vulnerability assessment, and passive monitoring.
Credits: e2e-assure
OT teams need to prioritize threats based on what could actually happen on the plant floor. A standard IT vulnerability score (CVSS) is almost useless here because it doesn’t consider physical safety or production impact. A critical score for an office server is not the same as a medium score for a PLC controlling a high-pressure valve.
The priority should be driven by the asset’s role in the process, not just the number of flaws it has.
From our consulting work, practical prioritization focuses on a few key factors:
By combining data from anomaly detection with OT-specific threat intelligence, teams can cut through the noise. The goal is to focus on the handful of vulnerabilities that could be exploited in a way that leads to a real-world safety incident or a costly shutdown, and address those first.
OT security threats are difficult to detect because industrial control systems rely on predictable, deterministic communication.
Attacks such as PLC exploits, zero-day ICS attacks, and advanced malware often imitate normal operational behavior. Limited logging, air-gapped OT networks, and legacy ICS flaws reduce visibility, allowing threats to persist without triggering alerts until operational disruption occurs.
OT anomaly detection works by passively observing network traffic rather than actively scanning devices. It establishes a baseline of normal behavior for protocols such as Modbus, DNP3, and OPC UA. When deviations occur, the system flags potential threats without sending disruptive packets, helping maintain safety, uptime, and process reliability.
Legacy ICS vulnerabilities remain risky because many devices cannot be patched or upgraded safely.
These systems often lack encryption, authentication, and secure firmware update mechanisms. Attackers exploit known ICS vulnerabilities and OT-specific CVEs, which increases exposure to ransomware, sabotage, and persistent threats targeting critical infrastructure operations.
OT asset discovery identifies all connected industrial devices, including PLCs, HMIs, RTUs, and edge systems.
Accurate inventories reveal hidden assets, outdated firmware, and insecure communication paths. This visibility enables effective OT vulnerability management, asset criticality ranking, and targeted remediation, reducing blind spots caused by shadow IT and OT network complexity.
Protocol-based attacks bypass IT security tools because industrial protocols use structures that standard tools do not inspect deeply. Attacks against Modbus, S7comm, EtherNet/IP, or Profinet exploit protocol logic rather than malware signatures. Without OT-aware deep packet inspection and behavioral analysis, these threats can operate undetected within normal process traffic.
Detecting OT threats means respecting physical risk and uptime, not copying IT tools. Passive visibility, disciplined baselining, and risk-based prioritization work where active scans fail. This approach builds control without causing disruption.
Need a practical detection strategy?
Start your OT risk assessment with MSSP Security
We offer vendor-neutral consulting to help MSSPs select the right tools, reduce sprawl, and build a resilient OT security program aligned with your operational goals.