Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Monitoring Privileged Access Management (PAM) means watching admin and service accounts do inside systems. These powerful accounts are often abused, and we’ve seen small issues turn into big breaches because of them. Real-time monitoring shows the exact commands and system moves that basic logs miss.
Effective programs record and scrutinize this high-risk activity, fundamentally changing incident outcomes by making stealthy abuse nearly impossible. This visibility is non-negotiable in modern defense. Keep reading to understand where most programs succeed or fail.

Monitoring Privileged Access Management (PAM) means tracking, recording, and analyzing activity by accounts with elevated rights. That includes:
Monitoring is what turns those policies into something you can test, prove, and enforce. This is where Identity Access Management (IAM) support becomes critical. Because access decisions without post-access visibility leave blind spots attackers can exploit.
In actual deployments, monitoring usually covers:
Those actions are logged, correlated, and stored for investigation. Given that 74% of breaches involve privileged credential abuse. According to the report, “the misuse of privileged credentials is a common attack vector in data breaches” [1].
Common monitoring capabilities we see in most mature PAM tools include:
In practice, monitoring is what separates theoretical control from real operational security.
Credits: Jigar Rajput
Privileged misuse amplifies every incident. Once attackers gain elevated access, they can:
Industry analysis shows that when privileged abuse is involved, breach costs go up by more than 30%. It’s not just more expensive; it’s harder to clean up and takes longer to understand.
Traditional Identity and Access Management (IAM) tells you:
PAM monitoring, on the other hand, tells you:
That difference becomes critical during investigations. Especially when PAM telemetry is correlated by integrating IAM with an MSSP SOC.
The main risk scenarios PAM monitoring helps control include:
By finding problems faster and stopping them early, PAM monitoring limits how much harm can happen. This reduces the overall risk to the organization.
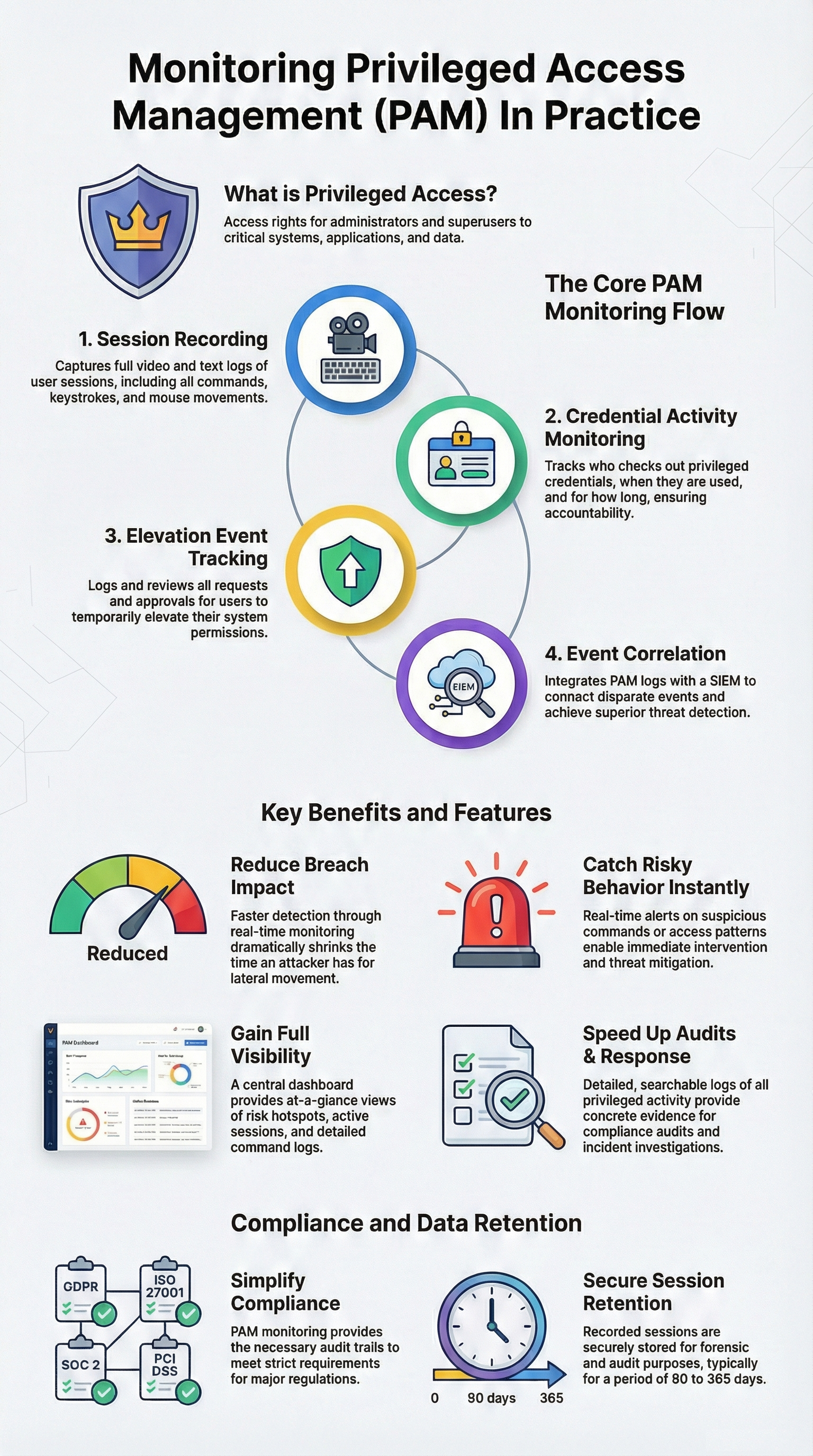
| Monitored Activity Type | What Is Observed | Why It Matters |
| Privileged Sessions | Commands, screen activity, keystrokes | Reveals misuse that standard logs never show |
| Credential Activity | Password checkout, injection, rotation | Detects stolen or abused credentials early |
| Elevation Events | Access requests, approvals, time limits | Confirms least privilege and accountability |
| Event Correlation | PAM logs sent to SIEM | Connects privileged actions to broader attacks |
In the environments we review for MSSPs, strong PAM monitoring usually centers on these four activity type:
When done well, almost no privileged action happens without some form of accountability attached to it.

Real-time PAM monitoring sits on the second side of that line. Instead of only collecting logs for later review, real-time monitoring:
Over time, the system builds baselines for what “normal” admin behavior looks like:
When behavior strays from those baselines, alerts fire. In some setups, high-risk patterns can automatically:
Organizations that use real-time monitoring often find problems much faster. In some cases, they cut the time it takes to spot suspicious activity by more than half. These tools also work closely with intrusion detection systems and automated response tools. Key real-time functions usually include:
From our work with MSSPs, we see that real-time monitoring often finds problems early. Basic logs usually show issues only after damage is done. Real-time monitoring helps teams spot risky actions right away, before they turn into bigger incidents.
When auditors come in, they rarely want to read policy documents first. They want proof. This approach aligns with NIST guidance, which stresses continuous monitoring and auditability for privileged access. Its reduce compromise risk and improve response accuracy [2].
PAM monitoring creates that proof in a structured, repeatable way. It generates:
This monitoring also helps organizations follow rules that require clear control over who can access systems, such as:
Instead of scrambling for screenshots and partial logs during an audit, teams can:
Outputs that help most during audits usually include:
This level of evidence doesn’t just make audits smoother; it reduces the chance that a finding or fine will come from missing or incomplete data.
From our experience working with MSSPs, PAM monitoring shows whether a security program real. Organizations that use this type of monitoring can collect audit evidence much faster. In some cases, teams cut the time spent gathering proof by 40% or more.
When we help MSSPs select or audit PAM products, we look for tools that:
We’ve watched MSSPs use strong PAM monitoring to:
Organizations focused on long-term security. PAM monitoring makes powerful access easier to see and control. What was once hidden becomes clear and trackable. Together works with clear rules, least privilege, multi-factor authentication, and regular access reviews. PAM monitoring becomes a core part of security, not just an extra task
Monitoring Privileged Access Management (PAM) tracks how powerful accounts are used across systems. It watches admins, superusers, and service accounts. Teams review session recordings, keystroke logs, and screen activity to see what happened. PAM monitoring also keeps audit trails and session playback. Real-time alerts help teams spot risky actions quickly and review them later without guessing.
PAM monitoring looks for strange behavior, not just logins. It flags unusual commands, unexpected access paths, and fast privilege changes. Behavioral analytics help show when actions do not match normal use. Real-time alerts let teams act fast. Session controls can stop unsafe actions right away. This helps catch insider misuse early and limits how much damage ransomware can cause.
Just-in-time access limits how long powerful access is active. Users only get higher access when they need it. Monitoring Privileged Access Management (PAM) supports least privilege and removes standing access. PAM monitoring checks that access ends on time. This reduces forgotten accounts and lowers the risk of long-term misuse.
PAM monitoring keeps clear records of privileged access. Audit trails show who accessed systems, when, and why. Logs from account discovery and credential use support reviews. These records help meet GDPR, SOX, and security framework needs. Teams can show proof quickly without manual tracking or missing data.
Continuous PAM monitoring is most important in mixed environments. Cloud systems, on-premises systems, and hybrid setups all add risk. Monitoring PAM helps track service accounts, apps, and root access everywhere. With IAM and SIEM integration, teams keep visibility across servers, endpoints, and DevOps tools.
Monitoring privileged access management (PAM) helps teams see how powerful accounts are used every day. Actions that were once hidden become clear and easier to control. With real-time monitoring, organizations can reduce damage and build trust across systems. We’ve seen security improve when teams use clear rules and hold people accountable.
As systems grow more complex, PAM monitoring becomes a basic need, not a nice extra. The next step is using it fully across the environment. Start strengthening privileged access monitoring today.