Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Incident response forensic analysis is the part that turns a messy breach into something you can actually understand and defend. When an attack hits, most teams don’t have the people, tools, or time to trace what the intruder did, what systems were touched, or what evidence still exists.
At MSSP Security, we keep seeing that the real picture appears only after someone methodically works through logs, endpoints, and network data. That’s when guesses turn into facts, and panic starts to drop. This guide breaks down that process in plain terms.
Keep reading if you want cleaner, faster decisions
We notice the same pattern again and again: most teams grab the fire hose and jump straight into containment as soon as an incident hits.
The visible part of the breach gets attention, but the earlier activity, the first point of access, and the full depth of the intrusion often stay in the dark. That blind spot is usually where reinfections and “mysterious” follow‑up alerts come from.
What closes that gap is incident response forensic analysis. Instead of treating forensics as a separate, niche task, we see the strongest teams weave evidence collection, examination, and interpretation into every phase of their incident response playbook.
Done right, it’s not just about looking at artifacts, it’s about turning those artifacts into a clear story the whole team can act on.
Industry guidance frames forensic analysis as work that “identifies attack vectors, attributes threats, and supports remediation.” In practice, many MSSPs and their customers stall on this because the tooling is heavy and specialized.
Memory imaging, file carving, artifact reconstruction, those aren’t point‑and‑click features, and they don’t always fit neatly into an existing product stack. That’s exactly where our consulting work usually begins.
From our side, working with MSSPs to select and audit products, we’ve watched what happens when teams lean only on alerts and dashboards. They see symptoms: a blocked connection, a quarantined file, a login from an odd location. Mature teams often steady their approach with a touch of digital forensics to see what the alerts might hide.
Once DFIR workflows and tools are built into their stack, they start to see the source: how the attacker got in, which controls failed quietly, which products add real signal versus noise.
In several ransomware and credential‑theft reviews we’ve led, that shift, from alert-driven guessing to evidence-backed answers, is what finally let those providers design response services they could stand behind. [1]
Credits: EC-Council
We keep noticing that the mature teams don’t treat forensic analysis as something “extra” they bolt on at the end. They build it into the whole incident response process. Most of them map to frameworks like NIST or SANS, so the phases are familiar: Preparation, Identification, Containment, Eradication/Analysis, Recovery, and Lessons Learned.
The difference we see in our reviews is simple, when forensics is woven into each phase, every step becomes sharper and more defensible.
From our side, working with MSSPs on product selection and audits, a complete forensic-driven incident response usually plays out in a consistent pattern:
When we walk MSSPs through this flow during product audits, the breach stops looking like random chaos and starts reading like a traceable story, who came in, how they moved, what failed, and which tools actually pulled their weight.
Preparation sets the tone for everything that follows. Teams with clear playbooks move faster and avoid missing evidence. At MSSP Security, we advise clients to prepare three essentials: tools, playbooks, and people.
First, the tools. Teams need forensic imaging tools like FTK Imager, live response tools like Velociraptor, and analysis platforms like Autopsy or EnCase. Second, the playbooks.
These outline when to image a system, what logs to save, and how to protect the chain of custody. Third, trained personnel. Even a quick RAM capture requires someone who knows what to preserve.
This preparation sounds basic, but it decides whether evidence survives an incident.
This stage is where teams separate noise from real danger. Logs, EDR alerts, and unusual activity point to possible breaches. Strong forensic habits allow teams to see early signals that others miss.
Identification usually starts with triage:
Forensic clues often appear here. Browser artifacts, PowerShell logs, or event logs hint at attacker movement. As one industry source notes, forensic triage helps responders “determine scope and severity early.” In our experience, early triage often prevents a small compromise from becoming a full incident.
Containment must be fast, but never reckless. If teams shut systems down too early, they lose volatile evidence such as RAM contents and active network connections. This data often reveals malware behavior, command execution, or credential theft tools.
During containment, forensic teams typically:
Our team has handled incidents where a simple RAM snapshot revealed an attacker’s remote shell still running. Without that snapshot, the root cause would remain hidden. Containment with forensic discipline helps stop the threat and preserve the story behind it.
This is the heart of incident response forensic analysis. This phase uncovers how the attacker got in, what they touched, and what they tried to hide. Forensic imaging creates a bit-for-bit copy of affected systems. Memory analysis tools like Volatility reveal in-memory malware, injected processes, and credentials in use.
Typical forensic work includes:
This is where we see the deepest insights. It’s also where teams with no forensic experience feel overwhelmed. Our experience across thousands of cases shows that a methodical forensic workflow exposes the real attack path every time.
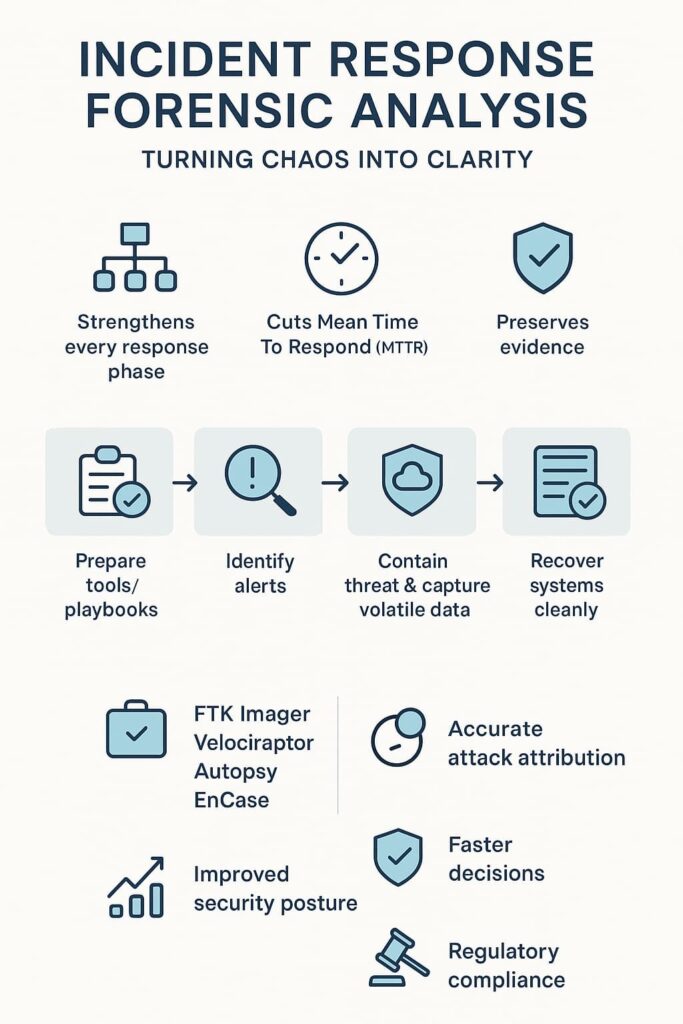
alt text: Infographic on incident response forensic analysis, highlighting tools and steps for effective incident management.
Recovery isn’t just about getting systems back online. It’s about making sure they’re clean. Teams use forensic findings to validate patched systems, rebuild infected machines, and restore trusted configurations.
Typical recovery work includes:
We’ve seen organizations skip forensic recovery and get reinfected days later. A forensics-informed recovery cycle breaks that pattern.
This phase turns an incident into long-lasting improvement. Forensic reporting explains what happened, when it started, how it spread, and what weaknesses made it possible. Reports include timelines, hashes, visuals, and legal-ready documentation for compliance needs such as GDPR or PCI.
Lessons learned help teams:
When we walk clients through this phase, most realize their biggest issue wasn’t the malware, but the lack of forensic readiness.
Incident response forensic analysis combines multiple techniques to see the full picture. Tools vary, but the goals stay the same: capture evidence, decode artifacts, and reconstruct events.
Common forensic techniques include:
Useful tools include forensic duplicators, EDR triage utilities, and platforms like Autopsy, EnCase, and Velociraptor. These tools support the chain of custody and preserve evidence integrity, which remains essential when incidents involve legal or regulatory consequences.
The benefits reach far beyond solving a single breach. Incident response forensic analysis helps teams:
Clients often tell us that the biggest benefit is confidence. Instead of guessing, they know exactly what happened. Instead of reacting blindly, they act with purpose. [2]
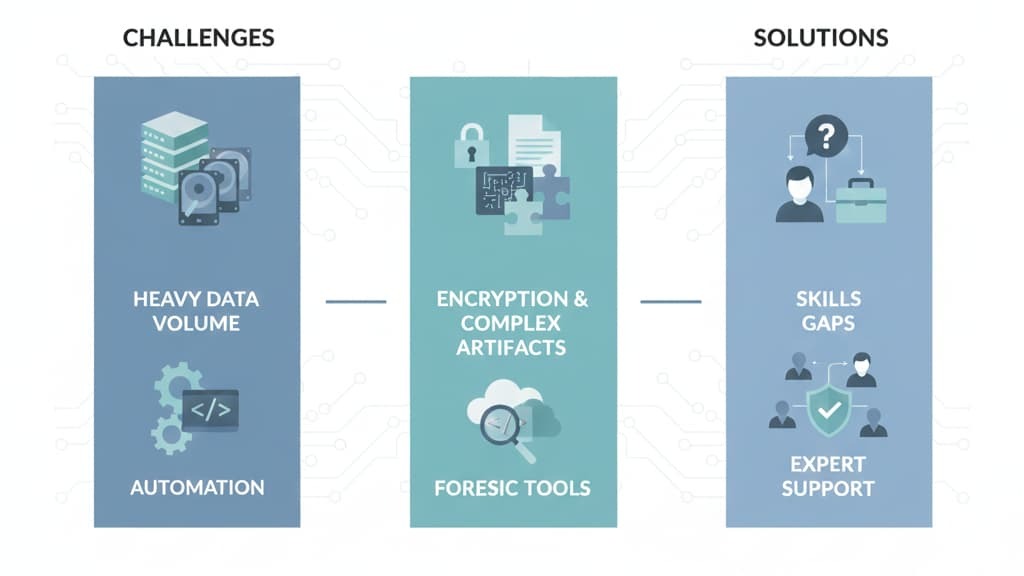
Even strong teams face challenges with forensic analysis. Data volume grows every year. Encryption complicates examination. Skills gaps make advanced techniques hard. Tools can be expensive and complex.
To address these, teams can:
At MSSP Security, we handle these challenges daily. We guide teams through high-volume evidence, encrypted containers, and complex multi-endpoint investigations. The goal is always the same: clear answers without overwhelm.
Incident response forensic analysis works best when integrated with SOC operations, MSSPs, and proactive threat hunting. SOC alerts reveal symptoms. Incident response forensic analysis uncovers causes. MSSPs like ours bridge the gap by giving teams both visibility and deep investigation capacity.
Many organizations use forensic readiness as part of their long-term security planning. This includes storing the right logs, enabling the right artifacts, and pre-staging tools for faster triage.
We’ve seen organizations go from reactive to resilient simply by adding a forensic lens to their incident response program.
Good IR work starts with simple steps. Many teams use incident response forensic analysis to understand what happened and why. Basics like DFIR forensic analysis, digital forensics in IR, and forensic evidence collection IR help you move fast. You learn how to keep chain of custody IR clean and how memory forensics incident response fits into the bigger picture.
Start with tools that match the job. Some people use Volatility framework IR for RAM analysis DFIR or FTK Imager incident for disk imaging IR. Others add Autopsy tool DFIR or Magnet AXIOM DFIR for artifact analysis DFIR.
Choose tools that help with timeline reconstruction forensics, IOC extraction forensics, or even network forensics IR when the case needs it.
Teams use forensic incident response to piece events together. They check logs with log analysis DFIR, SIEM forensics IR, or event log forensics IR. They build a super timeline IR or look at malware forensics IR when needed. This work supports root cause analysis IR and ties into TTP mapping IR with MITRE ATT&CK forensics to show how the attacker moved.
Cloud and mobile work need extra steps. Cloud cases may use AWS forensics incident, Azure IR forensics, or GCP forensic response. Mobile work often uses mobile forensics IR or iOS Android forensics IR.
These cases still use the DFIR lifecycle forensics flow but add checks like packet capture analysis IR, proxy forensics IR, or registry forensics IR depending on the device.
Incident response forensic analysis gives organizations the clarity they need when incidents strike. It strengthens every phase of response, cuts confusion, and reveals the true root cause behind attacks. With the right tools, preparation, and support from an experienced partner like MSSP Security, teams respond faster and preserve evidence without stress.
When forensic investigation becomes part of daily security practice, companies gain control, even in moments that used to feel chaotic. Ready to streamline your operations and elevate your security stack? Join us here.