Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

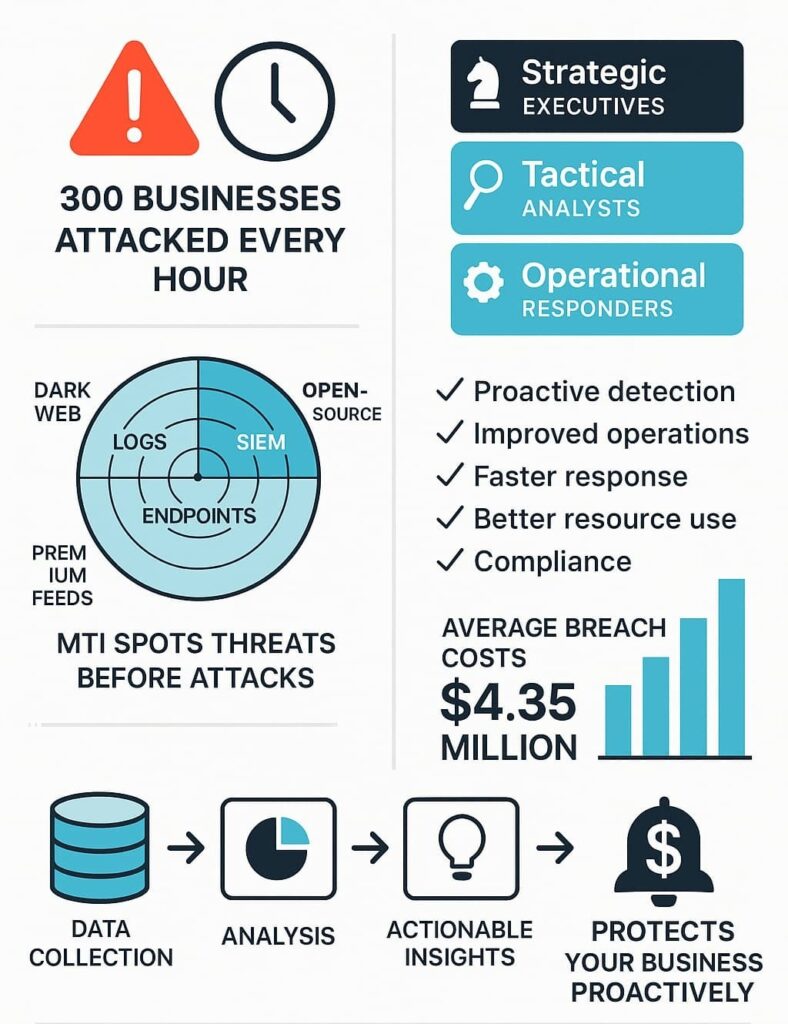
Every hour, roughly 300 businesses fall victim to cyber attacks. Most find out months later, when their data’s already gone. It’s frustrating – the old “detect and respond” method just isn’t cutting it anymore, especially when hackers are working overtime. But some companies are getting smarter about this.
They’re using managed threat intelligence (MTI), a security approach that doesn’t wait for attacks to happen. By watching patterns and analyzing real threats, MTI helps spot the warning signs before criminals can strike.
Curious to know what is Managed Threat Intelligence and how it can protect your business? Let’s break down what makes MTI different.
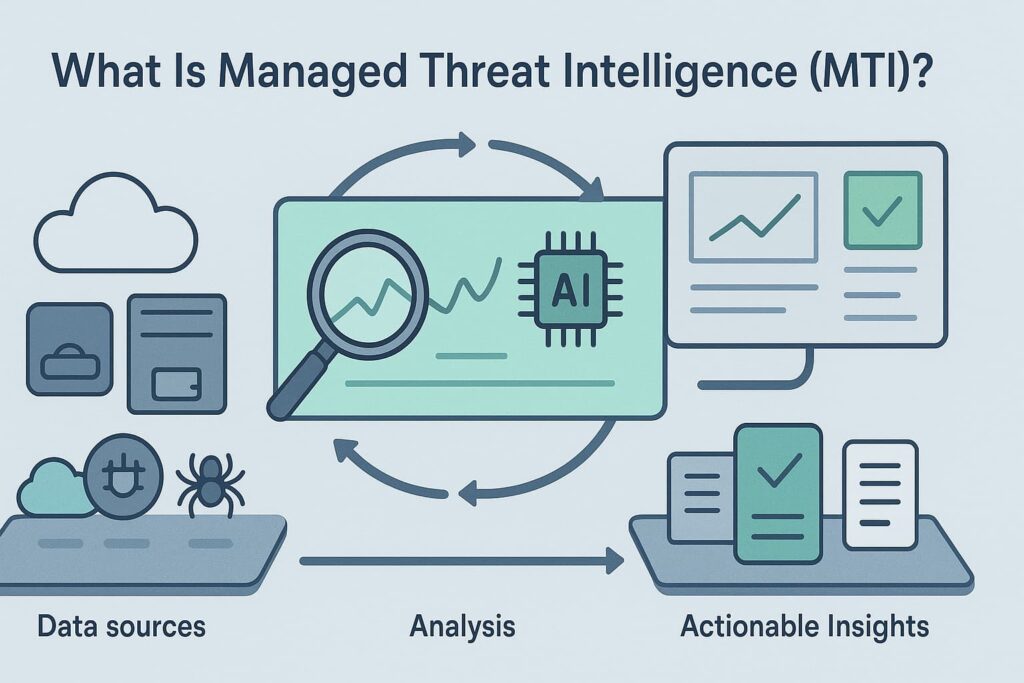
At its core, managed threat intelligence acts like a radar system for cyber threats – but way more sophisticated. We’ve seen countless organizations struggle with basic threat feeds that dump endless alerts without context. MTI fixes that headache by combining smart automation with seasoned analysts who know which threats actually matter.
The real magic happens when human expertise meets machine speed. Having audited over 200 security products for MSSPs last year, our team knows that generic threat data isn’t enough. Some providers brag about collecting terabytes of threat data, but what matters is picking out the relevant pieces. Every organization faces different risks – a hospital’s threats look nothing like a bank’s.
Our decade in the trenches taught us that effective MTI needs both breadth and focus. The service constantly gathers intel from across the cyber landscape, then filters it through expert analysis to deliver insights MSSPs can actually use. With cybercrime getting more expensive (average breach now costs $4.35 million) and creative, MTI has become as essential as firewalls and antivirus. [1]
After testing hundreds of security tools, we’ve found that solid MTI needs data from everywhere – inside and outside your clients’ networks. Here’s what a robust collection system should grab:
From Inside the Network:
From the Outside World:
Our audits show that MSSPs need both streams of data to catch everything. When you mix internal oddities with external threat info, patterns start jumping out. Some of our clients spotted attacks 2-3 weeks before they hit, just by connecting these dots. That’s the kind of edge good MTI gives you. [2]
Raw data is noisy and overwhelming. The magic happens when MTI providers filter, normalize, and correlate this data to identify meaningful patterns, trends, and threats. This phase often leverages machine learning and human expertise to pinpoint the most relevant risks.
The end goal is to produce intelligence your security team can act upon immediately. This might include tailored reports for executives, real-time alerts for SOC analysts, or integration with security tools like SIEMs and firewalls to automate defensive measures.
Credit: Adam Goss
This is the bird’s-eye view for executives and board members. It focuses on long-term cyber risk trends, business impact assessments, and strategic planning. For example, a strategic report might analyze ransomware trends in your industry and suggest investment priorities to mitigate risk.
Technical teams, security analysts, network engineers, rely on tactical intelligence. This level dives into attacker tactics, techniques, and procedures (TTPs), vulnerability assessments, and threat hunting guides. Imagine receiving detailed analyses of a phishing campaign targeting a specific vulnerability in your software stack.
Operational intelligence supports hands-on defenders like threat hunters and incident responders. It includes real-time attack indicators, threat actor intentions, and specific campaign details often pulled from deep and dark web sources. For example, a sudden alert on stolen credentials circulating on underground forums can trigger immediate containment efforts.
alt text: Infographic explaining what is managed threat intelligence and its benefits for businesses in cybersecurity.
With MTI, you don’t have to wait for an alert. Instead, you anticipate the attacker’s moves, identify risks early, and mitigate them before they materialize. This reduces dwell time and limits damage.
MTI streamlines workflows by automating detection rules and enriching alerts with context. This leads to fewer false positives and helps your analysts focus on what truly matters.
Rapid, informed decisions are critical during a breach. MTI equips response teams with the data and insights needed to investigate and contain incidents faster and more effectively.
By understanding the actual cyber risks your organization faces, you can prioritize security investments wisely and optimize existing tools for maximum impact.
Continuous monitoring and detailed reporting help you meet regulatory requirements and demonstrate due diligence in protecting sensitive data.

Selecting the right MTI provider is vital. Based on our experience, here’s what you should look for:
Having worked closely with many organizations, we know firsthand that MTI is more than a luxury, it’s a necessity. Integrating managed threat intelligence transformed our approach from reactive firefighting to strategic cyber defense.
The key is choosing a partner who not only delivers quality data but also understands how to make that data work for your operations. It’s about turning information into action.
For teams struggling with alert fatigue and skill shortages, MTI offers a way to extend capabilities without overburdening staff. For leadership, it provides a clear picture of cyber risks and helps justify security investments.
Managed threat intelligence combines cyber threat intelligence, data analysis, and expert insight to help organizations understand and respond to risks.
It uses real-time threat intelligence, threat actor analysis, and threat intelligence feeds to spot potential attacks early. By turning cyber threat data into actionable insights, teams can make smarter, faster cybersecurity decisions.
It works through a full threat intelligence lifecycle, collection, processing, and dissemination of information about threats. Managed threat intelligence services monitor the cyber threat landscape, track threat actor tactics, techniques and procedures (TTP), and use threat intelligence automation for faster detection.
The result is intelligence-driven security that supports early threat detection and rapid response.
Managed threat intelligence benefits include improved threat detection, faster incident response intelligence, and better cyber risk management. It helps reduce false alerts, improve visibility, and streamline cybersecurity intelligence workflows.
With continuous threat intelligence sharing and enrichment, teams can focus on strategic threat intelligence and operational decisions that strengthen overall cyber defense intelligence.
Regular cyber threat intelligence is often handled in-house, while managed threat intelligence is run by external threat intelligence experts. These services offer continuous monitoring, dark web monitoring, and threat intelligence integration with SIEM tools.
They provide advanced threat intelligence, predictive threat intelligence, and customized reports tailored to specific industries or attack surface monitoring needs.
Managed threat intelligence empowers organizations to shift from reactive defense to proactive, intelligence-driven cybersecurity. It transforms overwhelming data into actionable insights, helping teams anticipate threats and strengthen response capabilities.
The right service, aligned with clear objectives and strong integration, fortifies defenses and safeguards critical assets. Partner with MSSP Security for expert consulting tailored for MSSPs.
With 15+ years of experience and 48K+ projects completed, we help streamline operations, reduce tool sprawl, and enhance visibility, offering vendor-neutral selection, auditing, and actionable recommendations to build a secure, efficient, and goal-aligned cybersecurity infrastructure.