Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Vulnerability management isn’t rocket science, it’s a steady rhythm of finding weak spots and fixing them before trouble hits. MSSPs take on this daily grind across dozens of client networks, running scans and patching systems around the clock.
They’re handling everything from basic server updates to emergency fixes when critical bugs pop up (those nasty CVE-10 scores that make security folks sweat).
With the right tools and some smart automation, they’re keeping hundreds of systems locked down tight. Want to see exactly how they pull this off? Let’s break it down.
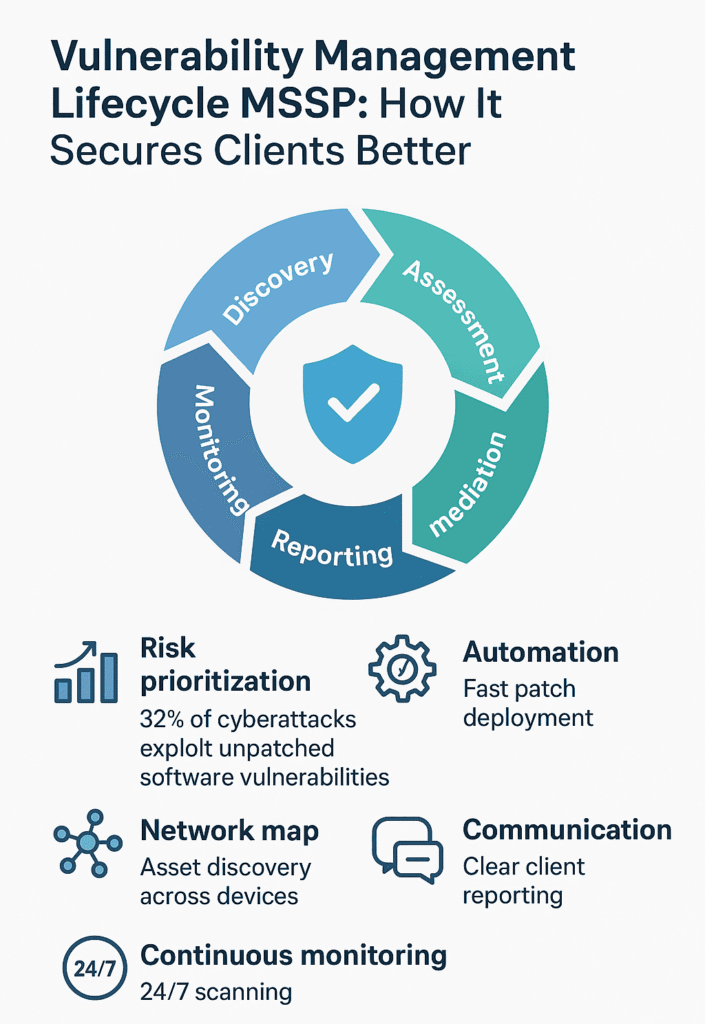
The security world’s got this thing backwards, they think vulnerability management is just about checking boxes. Truth is, for any decent MSSP, it’s more like watching a busy intersection 24/7.
You’ve got to keep your eyes peeled, watching every corner of client networks (which can stretch across thousands of endpoints) and catch problems before they turn ugly.
Think of it like this: you can’t protect what you don’t see. That’s why MSSPs spend so much time mapping out every server, cloud instance, and random laptop hanging around client networks. Miss one device, and you might as well leave the front door open.
Another IBM finding: in organizations that had AI-related breaches, 97% reported lacking proper AI access controls. This suggests that new technology layers add complexity and risk, especially when visibility or governance is lax (1).
Here’s what keeps the wheels turning:
This mirrors the importance of a continuous vulnerability assessment that MSSPs provide to catch risks before they spread.
First things first, you need a rock solid inventory. Every single thing connected to the network gets cataloged: servers sitting in basements, cloud stuff floating around somewhere, Bob’s work laptop he takes home every night. Miss something here, and you’re already behind.
Not all problems are created equal. Some vulnerabilities could let attackers walk right in through the front door, others are more like leaving a window cracked on the 20th floor. You’ve got to sort through the noise and figure out what actually matters (and what’ll keep the compliance folks happy).
According to a 2025 paper “The Hidden Dangers of Outdated Software”, 32% of cyberattacks exploit unpatched software vulnerabilities (2).
This is where the rubber meets the road. Working with clients to actually fix stuff, whether that’s pushing out patches or changing how things work. These days, automation’s doing a lot of the heavy lifting, which means fewer 3 AM patch sessions.
Just because you fixed something doesn’t mean it stayed fixed. Trust but verify, that’s the name of the game. Plus, when the auditors come knocking (and they always do), you’ve got proof everything’s squared away.
Nobody likes surprises in security. Good reporting tells the story of what’s happening in plain language, not just throwing around fancy charts. When clients understand what’s what, they make better decisions.
The job’s never done. While you’re fixing today’s problems, tomorrow’s are already showing up. That’s why the best MSSPs keep their scanning tools running 24/7 and stay plugged into the latest threat intel. Because in this game, standing still means falling behind.

Credit: pexels.com (Photo by panumas nikhomkhai)
Cybersecurity’s got this trio of terms that keep tripping people up, probably because they sound kind of the same. Here’s what’s what.
Vulnerability: There’s always that one weak spot in a system, like that back door nobody remembers to check. It’s just sitting there, waiting for some hacker to find it (and they usually do). Companies spend millions each year trying to spot these holes before someone else does.
Patch Management: When developers find these weak spots, they’ve got to fix them, that’s where patches come in. Think of it like this: there’s a leak in your roof, you patch it up.
Same thing with software, except these patches roll out pretty much every week (sometimes daily for big companies). It’s a never ending game of catchup.
Threat Management: This one’s about the whole security setup. It’s watching the cameras, checking the locks, and knowing what to do when something looks off. Sometimes it means pulling all-nighters when systems start acting weird, or shutting things down fast if there’s an attack.
Think of vulnerability assessment like taking a photo of your house’s security weak spots right now. One moment, one picture. That’s what it is.
That’s more like being the security guard who walks the perimeter 24/7, spots issues, fixes them, and keeps checking to make sure new problems don’t pop up.
Patch management’s just one piece of the puzzle, it’s downloading and installing those pesky software updates (you know, the ones everyone loves to postpone). Vulnerability management’s the whole security playbook: patches, sure, but also tweaking settings, adding security tools, the works.
Most clients get these mixed up at first, which can lead to some awkward conversations about what they’re actually getting. Better to sort it out on day one.

Credit: pexels.com (Photo by Christina Morillo)
Managing security across different client setups is like juggling while riding a unicycle. Every client’s got their own mix of old and new tech, and some of it’s in the cloud, some isn’t.
The bigger challenge with managed vulnerability management is keeping consistency across all those environments while prioritizing fixes. There’s never enough time or people to fix everything, so we’ve got to pick our battles.
Plus, there’s always some regulation breathing down our necks, demanding proof we’re doing things right.
When you nail it right from the start, it’s like a switch flips. Those endless weeks of playing catch up? Gone. What used to drag on forever now wraps up before lunch. That’s not just time saved, that’s money in the bank. And yeah, everyone’s a bit safer too.
It’s really just common sense when you think about it. Get ahead of problems while they’re still manageable. Before they grow teeth and start biting back.
Like that dripping faucet in the break room, fix it now, it’s a five-minute job. Wait a month? Now you’re looking at water damage and maybe even mold. Same deal with pretty much everything else at work.
When the problems stay small, the whole place runs like a well-oiled machine. Everyone gets their stuff done faster. The budget stays healthy. And nobody’s walking around worried about what might break next.
Nobody said watching for system weak spots would be easy, it’s not. The whole process needs someone paying attention around the clock, mixing automated tools with people who actually understand what they’re looking at. And let’s face it, having clients who give a damn helps too.
The math isn’t complicated. Keep your eyes on the networks, deal with the scary stuff first (using real data, not just gut feelings), and maybe, just maybe, you’ll catch problems before they turn into disasters.
Those follow-up checks after patching? They’re like double-checking the front door’s locks. Feels redundant until the one time it wasn’t.
Paperwork’s boring, sure. But good documentation means everyone sleeps better at night, especially when the auditors come knocking with their clipboards and questions.
Here’s the thing about managing security for multiple companies: there’s no magic button, no silver bullet. It’s grunt work. Sometimes it’s a real pain in the neck. But when systems run smooth as silk and the emergency calls drop off, that’s when you know you didn’t waste your time.
Think of the whole find-and-fix cycle like insurance, nobody likes paying for it, nobody gets excited about it, but everybody’s thankful it exists when things go sideways. Simple as that.
Ready to streamline your MSSP operations and build a stack that works for you? With 15+ years of experience and 48K+ projects delivered, we’ll help you cut tool sprawl, sharpen visibility, and align your services with business goals.
The vulnerability management lifecycle is a step-by-step process that MSSP vulnerability management teams follow to find, assess, fix, and track weaknesses. It usually involves asset discovery vulnerability checks, vulnerability scanning, and continuous vulnerability monitoring.
The vulnerability lifecycle stages often begin with vulnerability discovery MSSP services and vulnerability assessment MSSP reviews, then move into vulnerability risk assessment, vulnerability prioritization techniques, and vulnerability remediation.
A solid vulnerability management framework provides structure for the vulnerability lifecycle in cybersecurity. It outlines vulnerability control processes, vulnerability lifecycle security controls, and vulnerability management best practices.
Teams often rely on vulnerability lifecycle management tools such as vulnerability tracking software, vulnerability management dashboard solutions, and vulnerability lifecycle reporting dashboards. These track vulnerability management metrics and vulnerability lifecycle management KPIs.