Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Watching hackers is like tracking animals in the wild – they leave signs everywhere they go. These signs, or TTPs, tell us their favorite ways to break in, mess around, and steal stuff. Security teams who pay attention to these clues catch the bad guys way before they can do real damage.
It’s not rocket science – it’s just good old detective work applied to computers. Stick around to learn the tricks to understanding threat actor TTPS that’ll help you spot these digital trespassers before they wreck your network.
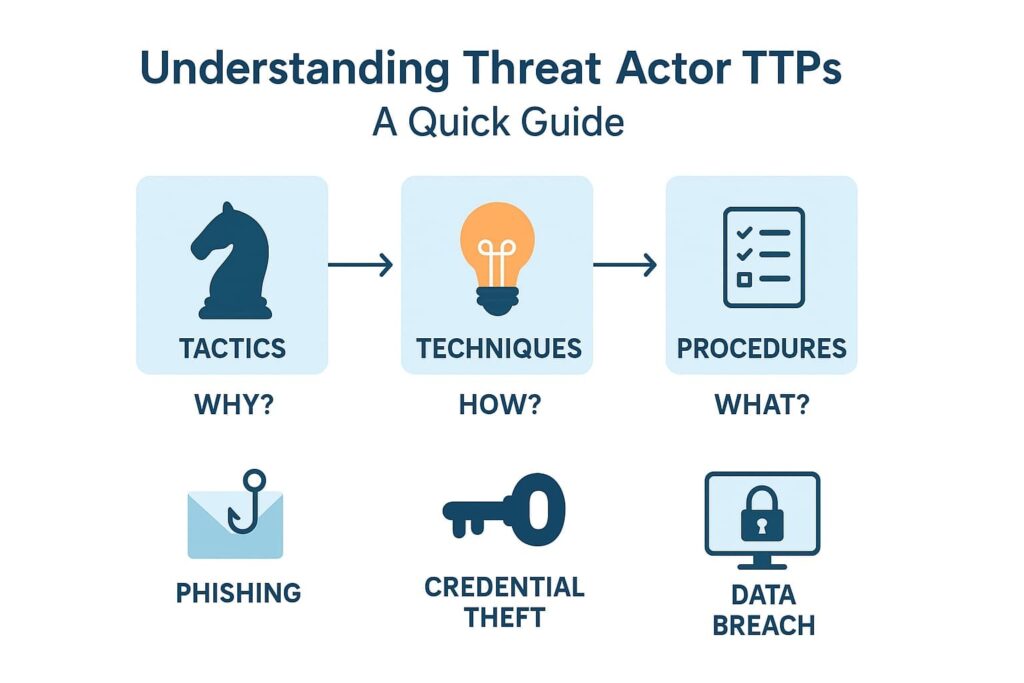
Most security folks toss around the term TTPs without really getting into the meat of it. Through our years helping MSSPs pick the right tools, we’ve learned that TTPs are really just the recipe book that shows how attackers cook up trouble.
Security teams spot tactics first – they’re the big-picture goals driving an attack. After auditing hundreds of incidents, we’ve narrowed down the main reasons attackers strike:
Take last month’s case: our client faced an attacker who deliberately hit their payment system during Black Friday. Classic disruption tactic.
The nitty-gritty methods attackers use make up their techniques. These aren’t just theoretical – we see them in action daily:
Here’s the kicker – attackers mix and match these techniques. When helping MSSPs track data theft, we often catch bad guys using both sneaky command channels and encrypted messages to avoid getting caught. [1]
Down in the trenches, procedures show exactly how attackers pull off their tricks. Our incident response team watches these digital fingerprints daily – they’re like a criminal’s step-by-step cookbook.
Through years of helping MSSPs catch bad guys, we’ve documented the most common moves:
Each crook has their own style. Last week, we caught one group using custom Python scripts for their attacks, while another stuck to off-the-shelf hacking tools. These little details help MSSPs figure out who’s behind each attack – sort of like catching bank robbers by their methods.
Credit: CBT nuggets
We’ve worked alongside many organizations that struggled with endless alerts and slow incident response. Shifting focus to TTPs changed the game. Here’s why:
When you understand attacker patterns, you can spot anomalies early. Instead of chasing alerts blindly, you’re hunting behaviors that match known adversary playbooks, allowing you to anticipate attacks before impact.
Knowing the “how” and “what” behind attacks enables your team to craft targeted detection rules and response plans. This focus on behavior patterns plays a major role in reducing threat detection time, resulting in faster containment, less damage, and a smoother recovery process.
Profiling threat actors through their TTPs helps predict their next moves and motivations. This kind of insight is central to building stronger threat intelligence service that arms your defenses and informs strategic decisions, from patch management to user training.
In practice, integrating TTP awareness into daily operations is vital. Here are some proven ways:
We regularly use TTP-based indicators to proactively search for hidden threats lurking in networks. By combining this approach with industry-specific threat feeds, threat hunting becomes more effective and precise, helping analysts focus on relevant attacker patterns.
Understanding which TTPs exploit certain vulnerabilities helps prioritize patching efforts. This reduces your attack surface by focusing on weaknesses attackers are most likely to target. [2]
Deploying intrusion detection and prevention systems tuned to known TTPs improves your ability to block attacks. Enforcing strict access controls and application whitelisting also closes doors that attackers use frequently.
Educating users about common TTPs, like phishing and social engineering tactics, builds a human firewall. A security-aware workforce is one less easy target for attackers.
Seeing TTPs in action clarifies their value.
| Tactic | Technique | Procedure |
| Data Encryption & Extortion | Malware Deployment (Ransomware) | Phishing email with malicious attachment sent, user executes ransomware, files encrypted, ransom demanded |
The attacker’s goal (tactic) is to encrypt data for extortion. They use malware deployment (technique) via phishing (procedure) to initiate the attack.
| Tactic | Technique | Procedure |
| Data Exfiltration | Credential Theft | Spear-phishing email targets employees, fake login page captures credentials, attacker accesses and steals data |
This shows how attackers combine social engineering with credential theft to steal sensitive information.
Many organizations rely on established frameworks to structure their understanding of TTPs.
This is a comprehensive, evolving knowledge base that categorizes tactics, techniques, and procedures based on real-world observations. It empowers security teams to identify specific adversary behaviors and tailor defenses accordingly.
The Cyber Kill Chain breaks down the stages of an attack from reconnaissance to final objectives, helping defenders map out and interrupt attacker progress.
Open Web Application Security Project (OWASP) and Cyber Threat Alliance offer valuable threat intelligence and best practices aligned with TTP concepts.
Leveraging the right tools is crucial for operationalizing TTP knowledge.
From our experience, integrating these tools with MSSP Security services can enhance detection and response capabilities while freeing up internal resources.
The cloud adds unique challenges. Attackers exploit misconfigured storage, overly permissive identity policies, and vulnerable APIs. Applying TTP knowledge here means focusing on cloud-specific attack vectors and adjusting defenses to ephemeral and multi-cloud architectures.
Threat actor TTPs, or tactics, techniques, and procedures, describe how attackers plan and carry out cyber attack methods. They include everything from reconnaissance techniques to privilege escalation methods.
Understanding these attacker methodologies helps improve threat intelligence, threat hunting, and incident response, making it easier to predict and stop future attacks.
Threat actor tactics constantly change as cyber adversaries learn from detection engineering and update their attack procedures. New cyber threat techniques like zero-day exploitation and social engineering tactics appear often.
Studying the cyber attack lifecycle through frameworks such as the MITRE ATT&CK framework helps analysts track adversary behavior and adapt cyber defense strategies effectively.
The cyber kill chain outlines each attack stage, from initial access tactics to data exfiltration tactics. Threat actor TTPs map directly to these steps, showing how cyber threat actors move through the system using persistence techniques or lateral movement tactics.
Understanding this attack timeline helps teams improve intrusion detection and incident mitigation.
Threat actor profiling combines threat intelligence and threat modeling to identify adversary behavior and attack motivations. By studying specific cyber threat actor groups and their attack vectors, security teams can predict likely breach tactics and apply the right security controls.
This proactive approach supports stronger SOC operations and better cyber risk management.
We’ve learned that TTPs are more than just jargon, they’re the lens through which we understand and anticipate cyber threats. By dissecting the why, how, and what of attacker behavior, security teams can design smarter defenses, respond faster, and minimize risks.
For organizations looking to elevate their cybersecurity strategy, partnering with an MSSP Security provider can be the first step. With expert support focused on TTP detection and response, you can stay ahead in this relentless battle.
Want to bring deeper TTP insights into your security operations? We’re here to help.