Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Cybersecurity teams need reliable early warning systems, and that’s exactly what threat intelligence service details delivers. These services act as digital lookouts, scanning both obvious and hidden corners of the internet to spot potential attacks before they hit home.
They track everything from basic malware patterns to sophisticated criminal operations, helping teams prepare their defenses ahead of time. While some companies just want the raw data, others need the full package – analysis, context, and specific recommendations. Want to know which approach fits your situation? Let’s break it down.
Most people never see the internet’s back alleys – places where hackers trade stolen company data like baseball cards. These dark web markets and forums buzz with activity 24/7, selling everything from employee passwords to internal documents, sometimes for less than the price of lunch.
Dark web monitoring teams crawl through these shadowy spaces, searching for signs that your company’s secrets are up for sale. They spot things like:
But it’s not just about finding stolen stuff. These watchers also keep ears open in hacker chat rooms, catching whispers about upcoming attacks or new malware making the rounds. Sometimes they’ll spot criminals planning their next move against specific companies or industries.
Smart companies use these services as an early alert system. When monitors spot company data for sale, teams can change passwords, lock down systems, or warn employees before criminals have a chance to use what they stole.
It’s way cheaper to fix a small leak than clean up after a flood – most companies spend around $4.35 million dealing with major breaches that could’ve been stopped early. [1]

Managed threat intelligence means outsourcing the gathering, analysis, and delivery of threat data to experts who maintain a constant watch on the cyber landscape. Instead of sifting through mountains of raw data ourselves, we receive refined intelligence tailored to our environment, technology stack, and threat profile.
This service doesn’t just dump information, it contextualizes threats, highlights what matters, and delivers it in a way that security teams can act on immediately. For organizations without large in-house intelligence teams, managed threat intelligence providers become an extension of the security operations center, feeding in real-time alerts and risk assessments.
From our firsthand experience, this approach drastically reduces the time from threat detection to response. Instead of reactive firefighting, managed intelligence lets us anticipate attacks and prepare defenses, turning the tables on attackers.
Credit: Rajneesh Gupta
Curated feeds are like a custom-tailored suit for threat data. Instead of generic information, these feeds are filtered and focused on what’s relevant to your industry, geography, or technology environment. Here’s why that matters:
In our operations, curated feeds have been a game changer. By focusing on specific ransomware variants hitting hospitals or financial fraud schemes targeting banking networks, we’ve sharpened detection and cut down incident response times by up to 40%. The intelligence isn’t just faster, it’s smarter.
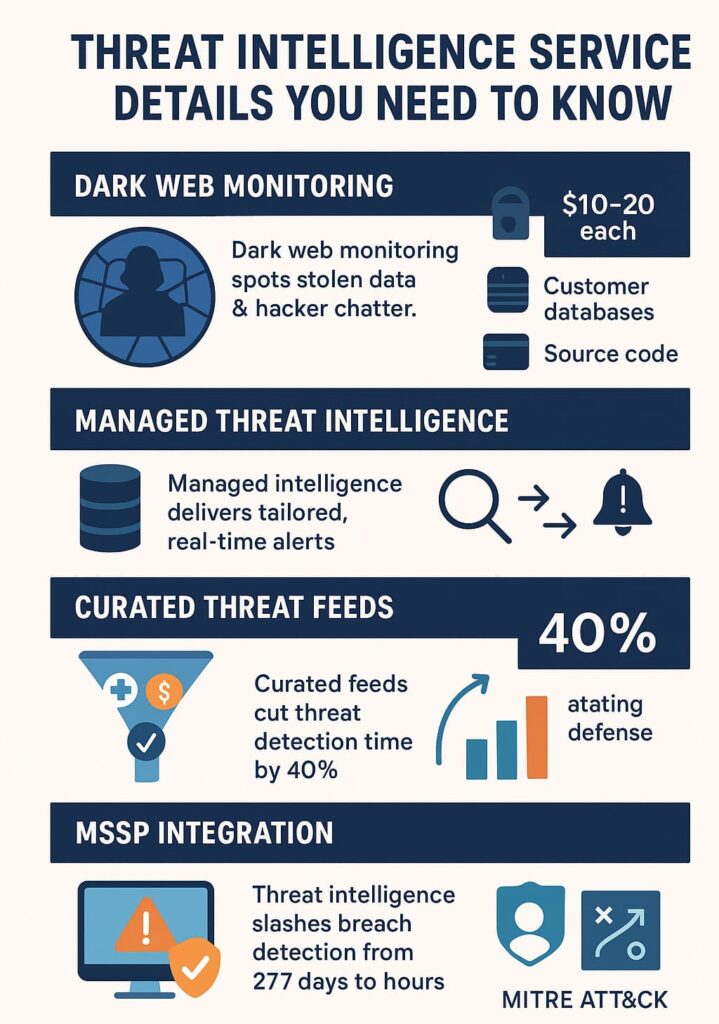
Managed Security Service Providers (MSSPs) integrate actionable threat intelligence directly into their security workflows, empowering clients with focused alerts, prioritized risk insights, and clear mitigation advice. What does this look like day-to-day?
This means organizations, especially those without dedicated intelligence teams, can make informed security decisions without drowning in data. Our collaboration with MSSPs has shown that integrating threat intelligence with security operations centers (SOCs) creates a seamless defense fabric, automating alert triage and enabling quick, confident responses.
Cyber threats don’t hit all industries equally. For example, healthcare organizations face persistent ransomware targeting patient data, while financial institutions must be vigilant against sophisticated fraud schemes. Industry-specific threat feeds zero in on these unique risks.
By subscribing to feeds designed for your sector, your security team receives intelligence that’s both relevant and actionable. This focus helps avoid the overwhelm from generic threat data and directs attention where it’s most needed. In practice, it means quicker detection of sector-relevant malware strains, phishing campaigns, or emerging attack techniques.
From experience, combining industry-specific feeds with other intelligence sources ensures a layered defense that’s both broad and deep. [2]

One of the most sobering statistics in cybersecurity is the average time to detect a breach, 277 days, according to a recent study. That’s nearly nine months of attackers roaming freely inside networks, collecting data, and causing damage.
Threat intelligence services play a vital role in slashing this detection window. By providing continuous, real-time insights and integrating with security tools, these services help identify suspicious activity early, sometimes within minutes or hours.
The faster detection means quicker containment, less damage, and a shorter recovery period. Our firsthand experience confirms this, organizations leveraging threat intelligence consistently respond faster and suffer fewer losses.
Tactics, Techniques, and Procedures (TTPs) are the playbook of threat actors. They describe how attackers gain initial access, move laterally, escalate privileges, and achieve their objectives.
Knowing TTPs is like understanding your adversary’s moves before they make them. It enables defenders to anticipate attacks, recognize patterns, and deploy targeted countermeasures.
We often rely on frameworks like MITRE ATT&CK to map TTPs, helping us translate intelligence into actionable defenses. This understanding supports everything from detection rule creation to incident response planning.
A threat intelligence service helps teams understand and respond to risks in the cyber threat landscape. It gathers cyber threat intelligence from sources like dark web monitoring service tools, vulnerability intelligence, and cyber attack indicators.
By analyzing this data, organizations get early threat warning and improve intrusion detection before serious damage occurs.
A dark web monitoring service searches hidden forums and dark net markets for stolen credentials or company data. This dark web threat detection gives actionable threat intelligence so teams can react fast. It’s part of a broader threat intelligence lifecycle that tracks hacker forum monitoring and cyber fraud detection to protect sensitive assets.
Managed threat intelligence means experts handle the whole process, collecting, analyzing, and reporting threats. Curated threat intelligence feeds focus on specific risks like ransomware trends or phishing threat intelligence.
Both use real-time threat intelligence and threat feed integration to cut threat detection time and deliver intelligence-driven security for faster response and stronger defenses.
MSSP threat intelligence providers support smaller teams by offering continuous monitoring, automated threat feeds, and SOC automation. They filter cyber threat indicators and operational threat intelligence into clear alerts.
This reduces noise, improves security event correlation, and helps businesses act fast on threat assessment reports without needing large in-house cybersecurity analytics tools.
Threat intelligence services, from dark web monitoring to managed intelligence and curated industry feeds, are vital components of today’s cybersecurity strategy. They deliver timely, relevant, and actionable insights that help organizations detect threats faster, understand attacker behavior, and strengthen defenses according to unique risk profiles.
Our experience shows that intelligence-driven security is more than a trend, it’s a proven approach that saves time, resources, and safeguards reputation. To stay ahead of evolving threats, organizations should assess their current intelligence capabilities and integrate tailored feeds or managed services. Ready to take your security posture to the next level?