Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Securing network perimeter firewall starts with recognizing it as the critical barrier between your systems and outside threats. A strong defense isn’t built on a single rule or device, it relies on layered practices such as strict access control, continuous monitoring, segmentation, and timely patching.
Each layer reduces exposure and closes gaps attackers look to exploit. Without this discipline, organizations risk costly breaches and long-term reputational damage.
The perimeter may be the first line of defense, but it must also be the most resilient. Keep reading as we break down the essential layers behind an effective firewall strategy.
We wouldn’t leave our front door with just a flimsy lock these days, and the same logic applies to networks. A perimeter firewall isn’t just another tool, it’s the bouncer at the door of our digital nightclub, checking IDs and keeping the chaos out. And make no mistake, there’s plenty of chaos trying to get in.
The reality is sobering. Companies are losing millions with every major breach, and by 2025, global cybercrime damages could hit $10.5 trillion annually. That’s not just a number, it’s a warning. Behind every statistic is a business that thought their defenses were “good enough,” until they weren’t.
Whether it’s a small shop running lean or a global corporation with sprawling infrastructure, the stakes are the same. A firewall sits at the edge, first in line to stop attackers, but if it’s not configured properly, it’s like putting up a fence that only looks strong from far away. One gap, one misstep, and everything can collapse.
We’ve seen this play out too many times. The tech teams already know the risks, the executives are starting to realize what’s at stake, and the attackers? They’re counting on someone, somewhere, leaving that digital door unlocked.

The first rule we follow is simple yet powerful: deny everything by default. That means blocking all inbound and outbound traffic unless explicitly allowed. It’s tempting to open ports just to get things working quickly, but this approach slams the door shut on unnecessary access points.
Adopting a “default deny” stance forces you to carefully consider every connection, so no surprises sneak in unnoticed.
Granting users and systems just enough access to do their job is a principle that we’ve found saves headaches down the line. Overly broad firewall rules invite trouble by letting in more than necessary.
We once encountered a case where a service had open outbound access to the internet unnecessarily. Tightening those rules stopped a potential data leak before it started.
Splitting the network into zones with different trust levels adds another layer of defense. Think internal network, external, and a demilitarized zone (DMZ). This division controls traffic tightly, so attackers can’t easily roam if they breach one segment.
In our experience, segmentation buys time,critical time that can prevent an attacker from reaching critical data. [1]
Stateful inspection tracks the status of active connections, ensuring only legitimate sessions pass through. Deep Packet Inspection (DPI) digs into the data payload itself, scanning for malicious content or anomalies.
We once noticed a spike in suspicious traffic flagged by DPI, which led to identifying a malware attempt disguised as normal communication.
The firewall is only as good as its management. If unauthorized users get control, they can disable protections or create backdoors.
We’ve seen firewall misconfigurations caused by stolen credentials. Securing management access prevents such risky situations.
Firewalls generate a ton of data. Without consistent firewall monitoring, suspicious activity can slip past unnoticed.
Our team schedules monthly firewall audits. These reviews often reveal outdated rules or new vulnerabilities that need patching.
Layering is essential. Adding Intrusion Detection and Prevention Systems (IDS/IPS) and application-layer filtering enhances the firewall’s capabilities.
Incorporating these layers makes the network perimeter firewall much harder to bypass. [2]
NAT hides internal IP addresses by translating them to public addresses. This makes it more difficult for attackers to map your network.
NAT is a simple yet effective tactic we use to keep the internal network’s layout under wraps.
Firewalls, like all software, have vulnerabilities that updates patch.
We’ve had firewalls running outdated firmware that opened doors for exploits. Prompt updates are non-negotiable.
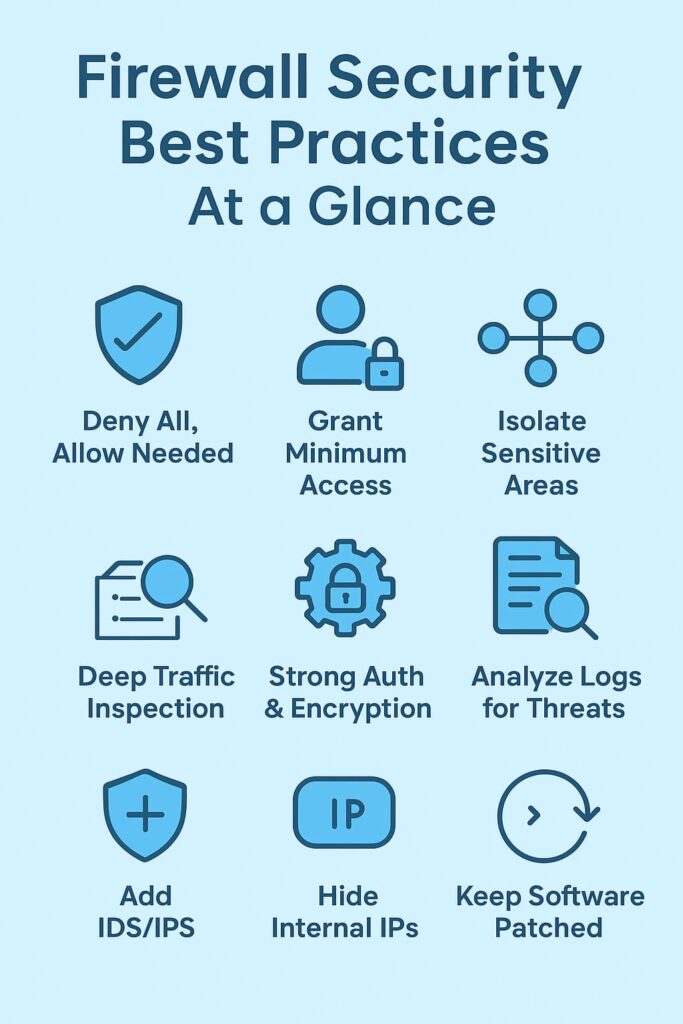
Start with a “deny all” policy and only allow traffic that’s absolutely necessary. This approach minimizes the attack surface and ensures only approved connections are permitted.
Apply the principle of least privilege by granting users and applications only the minimum access they need. This limits the potential damage if an account or system is compromised.
Divide your network into zones, isolating sensitive areas from less critical ones. Segmentation reduces the risk of attackers moving laterally once inside the network.
Go beyond simple packet filtering by inspecting both traffic and payloads through stateful or deep packet inspection (DPI). This enables detection of sophisticated threats that basic firewalls might miss.
Protect administrative access to your firewall with strong authentication, encrypted connections, and limited management interfaces. Doing so prevents unauthorized changes to security settings.
Consistently log firewall activity and monitor it for anomalies. Regular analysis of these logs helps identify suspicious behavior before it escalates into a breach.
Strengthen your defense with added tools such as Intrusion Detection/Prevention Systems (IDS/IPS). These layers provide extra protection against complex and evolving attacks.
Use NAT to mask internal IP addresses from external view. By hiding your network’s structure, NAT makes it harder for attackers to map and target internal systems.
Keep your firewall software patched and up to date. Regular updates close known vulnerabilities and protect against newly discovered threats.
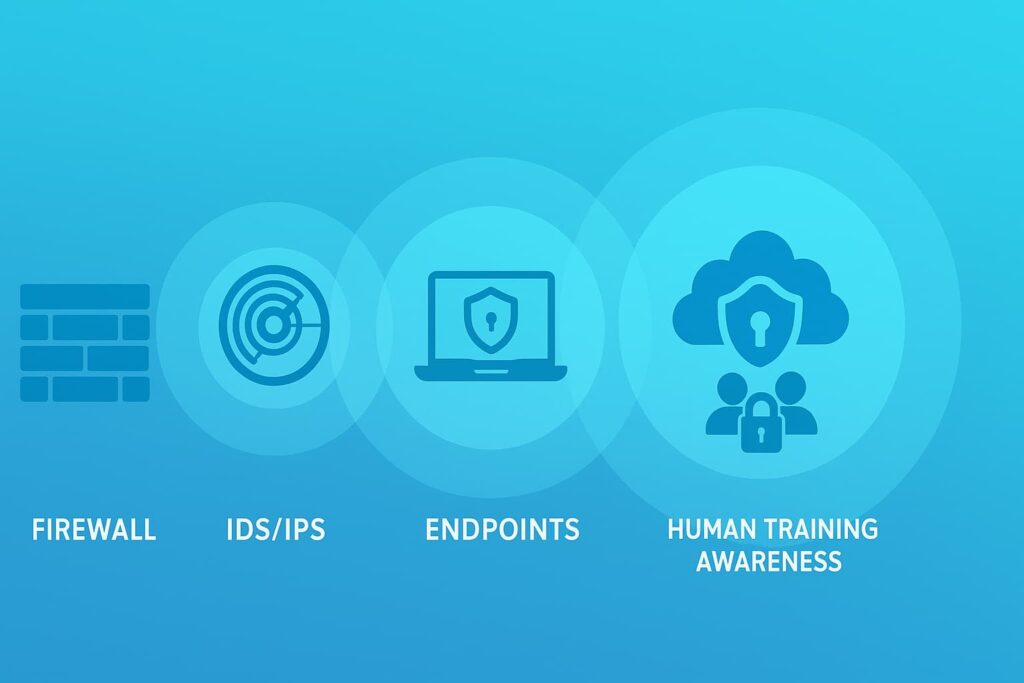
The perimeter firewall is a crucial pillar but not the entire fortress. We’ve learned the hard way that relying solely on the firewall leaves gaps elsewhere.
Endpoint protection, intrusion detection systems, and ongoing user awareness training all plug holes attackers might exploit. Regular security audits and penetration tests uncover weaknesses before attackers do.
By weaving together these elements with a strong perimeter firewall, organizations create a resilient defense that adapts to evolving threats.
A network perimeter firewall filters traffic at the edge, acting as the first barrier. Strong firewall security depends on clear firewall rules, proper perimeter firewall configuration, and continuous monitoring.
Using stateful inspection, packet filtering, and access control, it reduces risks from both internal and external threats. Regular firewall updates, firewall audits, and consistent firewall policy reviews strengthen compliance and ensure the firewall security posture stays effective against new attacks.
Firewall security layers combine multiple defenses, such as intrusion prevention system, malware filtering, firewall content filtering, and firewall anomaly detection. Features like next generation firewall, deep packet inspection, firewall application control, and firewall user identification support stronger threat detection.
Logging, monitoring, firewall analytics, and firewall alerts connect these layers, enabling faster response. By reducing the firewall attack surface and applying zero trust with network segmentation, the overall firewall security posture becomes more resilient.
Effective perimeter firewall configuration requires balancing firewall performance with firewall security. Clear firewall rules, firewall role-based access, firewall authentication, and firewall policy keep control tight.
Packet filtering, firewall deep packet inspection, and firewall traffic control help manage flows without slowing systems. Encryption, VPN support, NAT, and DMZ design secure data while hiding internal structures.
Regular firewall troubleshooting, firewall incident response, firewall backup, and firewall change management keep operations smooth while reducing risks.
Firewall management extends beyond setup, it includes logging, monitoring, firewall incident management, and firewall analytics. Firewall audits ensure compliance, while anomaly detection, security orchestration, and automation improve speed in addressing threats.
Firewall alerts trigger firewall incident response, supported by firewall backup and data loss prevention measures. Features like firewall traffic control, firewall user identification, and firewall change management keep defenses adaptive. Together, these practices strengthen firewall security posture while minimizing disruption.
Securing network perimeter firewall requires more than basic setup, it’s about building a layered defense with strict policies, access controls, traffic inspection, and constant monitoring. When these elements work together, the perimeter transforms from a static barrier into an active guardian against intrusions.
To strengthen your defenses, start with these core practices and adapt as threats evolve. Cyber risks won’t pause, and neither should your strategy. Stay proactive, stay secure, and safeguard your network with MSSP Security.