Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

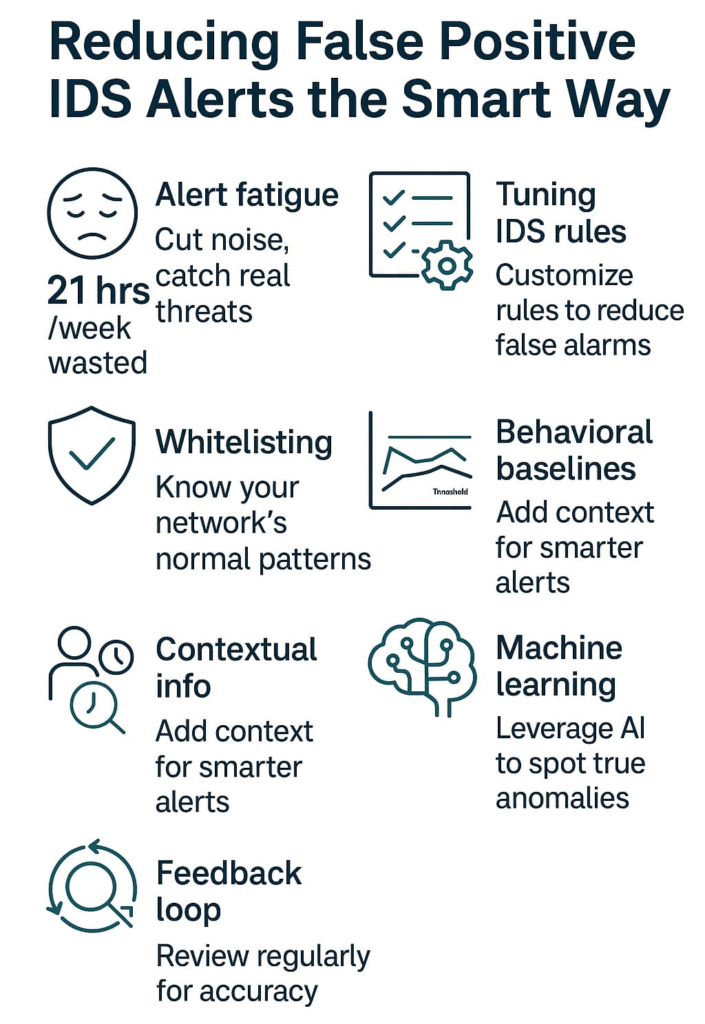
Reducing False positive IDS alerts drain security teams’ time and focus. The average SOC wastes 21 hours per week chasing down these non-threats (based on SANS data). Poorly tuned rules flag normal stuff like backup jobs and patch updates, masking the real dangers lurking in network traffic.
When Bob in accounting triggers another “malware detected” alert just by running his monthly Excel macros, the whole team rolls their eyes. But these alerts hide actual attacks in plain sight, and that’s dangerous.
Better tuning cuts through the noise – customizing rules, whitelisting known-good behaviors, and setting smart thresholds that catch the bad guys without crying wolf at shadows.
Want to actually fix your IDS headaches? Turn the page.
A senior analyst at one of our client MSSPs summed it up perfectly: “Some days I’m drowning in 3,000+ alerts, and 95% are junk.” They’re not alone. False positives drain resources and crush morale across the industry.
Real-world example: one provider’s team spent 6 hours investigating “suspicious” traffic that turned out to be a new backup system. Meanwhile, actual threats hide in the noise.
The math isn’t pretty. When teams waste 4-5 hours daily on false alarms, that’s 20-25 hours weekly down the drain. Our assessments show most MSSPs could cut alert volume by 40-60% through proper tuning and tools.
One of the most straightforward yet powerful ways to reduce false positives is to customize your IDS rules. Out-of-the-box signatures are often broad or outdated and don’t reflect your network’s unique behavior.
We recommend reviewing your alert rules regularly and tailoring them to exclude known safe traffic. For instance, if your IDS flags legitimate SSH traffic as suspicious, adjust the rule to exclude trusted IP ranges or specific ports. This simple step cuts down on unnecessary alerts immediately.
Don’t hesitate to disable signatures that no longer apply or cause excessive noise. We’ve seen environments where removing a handful of overzealous signatures reduced alert volume by over 30%.
This process aligns closely with best practices in intrusion detection system management to ensure rules fit your network’s behavior.
Credit: RapidAML
We’ve learned that whitelisting trusted IPs, apps, or user actions is a smart way to cut down on false alarms from normal activities. For instance, internal monitoring tools or maintenance servers often create traffic that might look suspicious to an IDS at first glance.
By marking these as trusted, you can stop alerts on harmless activity. Still, it’s important to be careful, too much whitelisting can hide real threats. That’s why we regularly review and update our whitelists to keep them accurate, secure, and free from blind spots that attackers could take advantage of.
Whitelisting is a key part of configuring IDS/IPS rules and alerts, helping reduce noise while maintaining coverage of real threats.
We’ve learned that understanding what’s “normal” on your network is one of the most important steps in reducing false alerts. When you know how your users and systems usually behave, it’s much easier to notice when something truly unusual happens. This way, you can focus on real problems instead of wasting time on harmless changes or daily patterns.
For example, if most users transfer around 1GB of data a day, it makes sense to set your alert level at 5GB instead of 1.5GB. That small change can stop your system from flagging normal activity as suspicious.
In our experience, building and updating behavior baselines helps us detect strange traffic without drowning in false positives. It takes time and careful observation to get the balance right, but it pays off. Once your baseline is solid, your IDS becomes much smarter, focusing on true threats instead of background noise, and that’s where real security begins. [1]
We’ve found that alerts by themselves don’t always tell the whole story. When an IDS shows something strange, adding more details, like who the user is, what time it happened, and how important the system is, helps tell whether it’s really a problem or just normal activity.
For example, if a login alert pops up, checking the user’s usual login times or how sensitive the system is can help decide if it needs a closer look. In our experience, connecting IDS data with other security tools, such as SIEMs, gives a clearer picture and helps teams focus on the most important threats.
This contextual approach is vital in 24/7 intrusion monitoring analysis, where real-time insights and audit trails support faster, smarter responses.
Machine learning (ML) models are game-changers for reducing IDS false positives. They continuously learn network behavior and adapt to new patterns, cutting out unnecessary noise.
We’ve implemented ML-driven anomaly detection that can:
By reducing reliance on static rules and leveraging adaptive intelligence, ML makes detection systems far more resilient, helping security teams focus on real threats, not repetitive noise.
.
We’ve learned that reducing false positives isn’t something you fix once and forget. It’s an ongoing process that requires regular checkups and fine-tuning. By reviewing alerts and identifying which ones are false, you can keep your IDS sharp and up to date with how your network changes over time.
Our team holds regular review sessions to go through alert logs, study patterns in false positives, and adjust detection rules where needed. This steady feedback loop helps the system stay aligned with real user behavior and the latest threat trends.
Over time, this process not only reduces noise but also builds a stronger, more accurate IDS. When everyone contributes to reviewing and refining the alerts, the result is a cleaner, more reliable detection system that stays effective as your environment evolves. [2]
| Strategy | Description |
| Tuning IDS Rules and Signatures | Customize and refine detection rules to match normal network behavior. |
| Leveraging Whitelisting | Exclude trusted IPs and applications from alerting to reduce noise. |
| Behavioral Analysis & Baselines | Establish normal activity baselines and flag only true deviations. |
| Contextual Information Use | Correlate alerts with user, time, and asset data for better prioritization. |
| Machine Learning Implementation | Use adaptive models to dynamically distinguish real threats from benign anomalies. |
| Regular Review & Feedback | Continuously analyze alert patterns and tune rules accordingly to maintain accuracy. |
False positives in an intrusion detection system often happen when normal network activity looks like a threat. Poor IDS tuning, old signatures, or missing whitelist management can cause this. Regular rule customization and better anomaly detection help reduce these mistakes.
IDS tuning means adjusting detection rules so the system understands what’s normal for your network. It includes baseline profiling, IDS rule customization, and anomaly thresholding. This keeps the IDS from flooding analysts with false alarm noise while improving detection accuracy.
Machine learning IDS systems can learn from past alerts. They analyze patterns, use behavioral analysis IDS methods, and apply IDS dataset training. Over time, the IDS adapts to real traffic, lowering false alarms while spotting new attacks more effectively.
IDS alert correlation links related events from different sources. When alerts are analyzed together, the IDS can tell real attacks from harmless events. Using IDS alert prioritization and security event correlation makes it easier to manage alert fatigue and focus on true threats.
Reducing false positive IDS alerts is a continuous process, not a one-time fix. Combining IDS tuning, behavioral baselining, and machine learning delivers the strongest results. Regular feedback and contextual awareness keep detection accurate and efficient. By cutting the noise, teams can focus on real threats, respond faster, and strengthen security posture.
Get expert guidance tailored for your IDS and MSSP operations , our consultants help streamline workflows, reduce tool sprawl, and enhance visibility. With 15+ years of experience and over 48K projects completed, we’ll help you optimize tools, improve integration, and boost overall security effectiveness.