Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Reducing attack surface vulnerabilities starts with the basics, who can get in and where they can go. Think of it like a building with too many doors, where each entrance might let the wrong people slip through.
Most organizations don’t realize they’ve left digital windows wide open until it’s too late. Smart teams cut down these entry points through access controls (the fancy term is RBAC), making sure employees can only reach what they need to do their jobs.
They’re also using encryption and those annoying but necessary two-factor login prompts that pop up on phones. There’s more to this story though, and it’s worth knowing the details. Keep reading to see how it’s done right.
Walked into a bank the other day and thought about how they control who goes where. Wish more companies treated their networks the same way. Instead, most of them run their permissions like a college party, everybody’s invited, and nobody’s checking IDs. The ones who get it right use this thing called Role-Based Access Control (RBAC). Pretty basic stuff really, just figuring out who needs what to do their job. [1]
Look, nobody likes hearing “no,” but giving everyone admin access is like handing out master keys at a hotel. The cleaning staff doesn’t need the keys to the safe, right? But you’d be amazed, or maybe not, at how many places still throw around admin rights like they’re party favors. Here’s what actually needs to get done:
Just locking the doors isn’t enough anymore. You need to know exactly who’s wandering around inside, what they’re touching, and why. A dedicated security operations center (SOC) helps monitor and respond to these activities in real time, making enforcement of access controls far more effective.

In 2023, if you’re not encrypting your sensitive stuff, you might as well write it on a billboard. Encryption isn’t perfect, nothing is, but it turns your data into gibberish that nobody can read without the right key. Your customer database probably needs bank-vault level protection. The cafeteria menu? Maybe not so much.
Any decent security setup uses TLS for data moving across networks (yeah, that little padlock in your browser), and they’ve got solid encryption on their stored files too. Throw in those access controls we just talked about, and suddenly breaking in becomes more work than it’s worth. Most hackers aren’t that motivated, they’ll just move on to somebody who left their digital front door wide open. [2]
Most IT folks would rather get a root canal than spend time cleaning up old systems. But here’s the thing, every ancient program or forgotten tool hanging around is basically an engraved invitation for trouble. Walk into any company’s network, and you’ll probably trip over abandonware from 2010 that nobody’s touched since the iPad came out.
You’d be shocked at how many places have random network services just humming along, doing absolutely nothing useful. Last week we saw a network with like 50 open ports that nobody could explain. It’s the digital equivalent of leaving every window in your house cracked open, then acting surprised when someone climbs in.
The smart money’s on breaking up networks like apartment buildings, separate units with their own locks. Sure, some companies are going nuts with micro-segmentation (probably the same ones still trying to make “blockchain” happen), but plain old network separation does the job just fine for 90% of businesses.
Walls between network sections are useless if you don’t control who walks through the doors. Firewalls do the bouncer work, but they need specific instructions, otherwise they’re about as useful as a screen door on a submarine. Some poor soul’s gotta sit down and figure out exactly what traffic needs to go where.
Ever notice how your phone’s settings somehow change themselves when you’re not looking? Networks do that too, only worse. One day everything’s locked down tight, next thing you know half your security settings have wandered off like cats in an open yard. Monthly checks aren’t fun, but they beat explaining to the boss how you got hacked.
Nobody ever got promoted for running patches, but plenty have gotten fired for skipping them. Auto-updates are great when they work, but trusting them completely is like believing your teenager actually did their homework without checking.
One missed patch on one forgotten server, and suddenly you’re explaining to the board why customer data is for sale on some forum. That’s why partnering with vulnerability management services that automate scanning and patch prioritization has become a cornerstone of proactive cybersecurity.
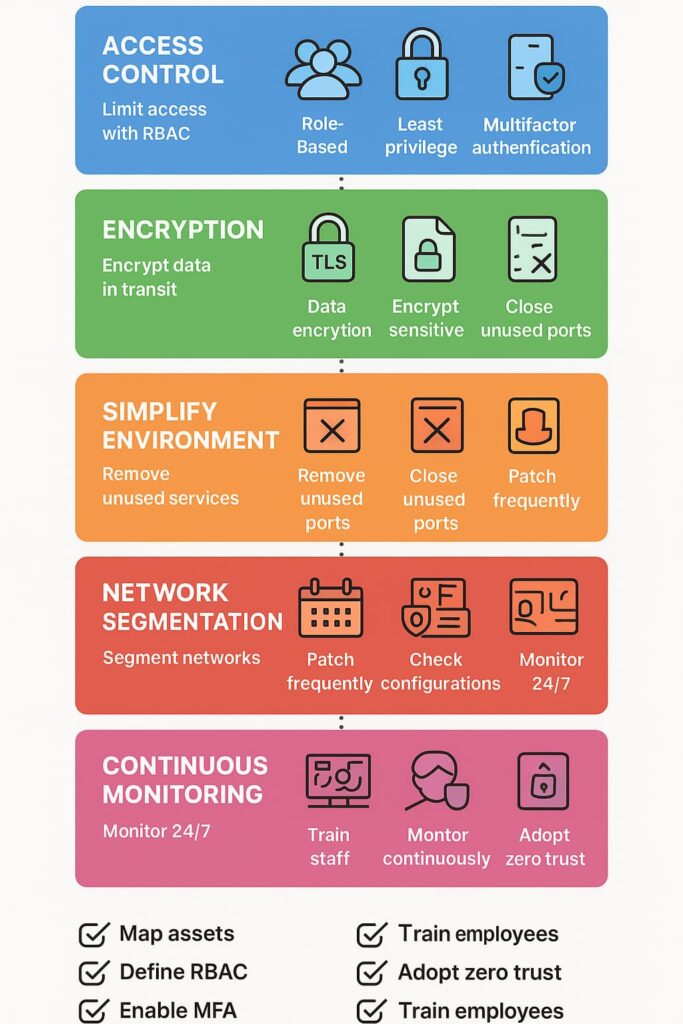
Threats evolve constantly. That’s why continuous monitoring is crucial. Tracking assets actively helps detect new or changing devices on the network and anticipate activity from advanced persistent threat groups that target sensitive data over extended periods. Anomalous activities get flagged early, giving us a chance to respond before damage occurs.
Ongoing risk assessments allow updating mitigation strategies as new vulnerabilities emerge. This proactive approach means security controls stay relevant and effective instead of becoming outdated.
Our human element is often the weakest link. We prioritize employee training to educate about cybersecurity risks, phishing, and social engineering tactics. Encouraging secure practices and reporting suspicious activity builds a security-conscious culture.
Increasing awareness helps reduce insider threats and accidental exposures. It’s a simple but powerful layer of defense that complements technical controls.
Credits: Andrew Hoffman
Zero trust means never assuming any user or device is trustworthy by default. We continuously verify every access request, authenticating and authorizing users and devices rigorously. This approach enforces strict control, assuming breaches can happen anytime.
By minimizing implicit trust and applying comprehensive access restrictions, zero trust architecture significantly reduces the attack surface. It’s a mindset shift but one that aligns well with modern threat landscapes.
We’ve seen how applying access controls, encrypting data, simplifying environments, segmenting networks, managing patches, monitoring continuously, training people, and adopting zero trust collectively shrink attack surface risks. Here’s a quick checklist to apply:
Poor network segmentation can make it easier for attackers to move laterally once they gain access to one system. Without clear firewall rules or network micro-segmentation, a single compromised endpoint security control can lead to widespread damage.
Using role-based access control, endpoint hardening, and network traffic filtering helps minimize attack surface and stop lateral movement before it spreads across the network.
Granting broad permissions creates more cybersecurity attack vectors. By applying the least privilege principle with privileged access management and account lifecycle management, organizations can limit damage from insider threats and compromised accounts.
Identity and access management combined with secure authentication methods like multi-factor authentication greatly reduce the external attack surface and help with exploit prevention across sensitive systems.
Unpatched software creates open attack surface attack paths for hackers. Patch management, patch automation, and automated vulnerability scanning should be part of continuous monitoring and security audits.
Pairing software hardening with secure configuration and logging and monitoring helps with software vulnerability mitigation. This process forms a strong defense in depth strategy and improves overall security posture while minimizing cyber risk.
Cloud services expand the external attack surface through APIs, remote access points, and shared resources. Cloud security practices like API security, encrypted communication, and secure remote access reduce exposure.
Threat modeling and threat surface mapping tools identify weak spots. Using automated security tools and threat intelligence for anomaly detection improves operational security and prevents misconfigurations in third-party risk management scenarios.
Even strong cybersecurity controls can fail if employees fall for phishing or social engineering attacks. Security awareness training teaches safe cyber hygiene, secure authentication methods, and proper use of application whitelisting.
Insider threat mitigation becomes easier when employees understand risks. Combined with intrusion detection systems, security incident response, and malware prevention, trained users help reduce attack surface vulnerabilities from human error.
Reducing attack surface vulnerabilities isn’t a one-time task, it’s an ongoing process. Combining access controls, network segmentation, simplified environments, and continuous monitoring builds a stronger defense. Adding employee training and Zero Trust practices closes even more gaps.
For MSSPs ready to streamline operations and reduce tool sprawl, our expert consulting services provide vendor-neutral guidance, stack optimization, and PoC support, helping you align your tech stack with business goals and stay ahead of evolving threats.