Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

The Purdue Model security monitoring is a practical blueprint for industrial security. It segments your operational technology into clear zones, creating defensible layers. This gives you the visibility to spot problems before they escalate. Forget the abstract theory. This guide provides a direct implementation strategy based on real plant-floor needs.
You’ll learn how to apply the model, where it faces modern challenges, and how to adapt it for your specific site. Build a monitoring strategy that truly protects your critical processes. Continue reading to get started.
Bringing a live plant network into the Purdue Model is never as clean as the diagrams suggest. In real environments, sensors often send data straight to the cloud, and legacy PLCs still share space with office devices. It can feel outdated at first.
“This same tool not only can tell you what’s on your network, but can also baseline normal network communication, inclusive of the industrial protocol, so you can determine if there are any deviations in the baseline and pinpoint changes from normal operations. It’s from this baseline monitoring you have a change control process, as you can start to watch for and manage changes in your process configuration.” – Tripwire Blog
But in practice, the model gives teams a way to impose structure on chaos through stronger operational technology security monitoring. We’ve walked into sites where IT and OT were fully merged.
Segmentation changes that by turning networks into visible, controllable zones.
The work usually comes down to four core steps:
• Group assets by operational function, not IP ranges
• Define and document every approved communication path
• Monitor traffic closely at each zone boundary
• Baseline what “normal” activity looks like
This approach doesn’t aim for perfection. It creates contained systems where breaches are detected early and kept from spreading.
Credits: Industrial Defender
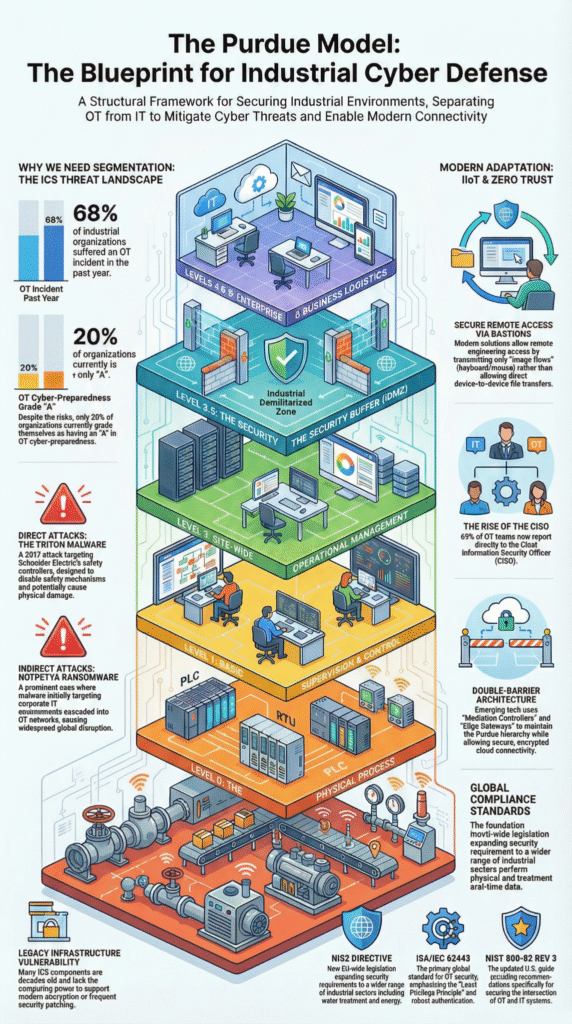
How the Model Structures Your Visibility
What do you watch on each level? Your tools and focus change from the factory floor to the office.
Levels 0-1: The Physical World
Here you find PLCs, valves, and motors. You can’t install software on these devices. Instead, you watch the data they send. Strange readings or unexpected communication are your alerts. Security relies on physical locks and network taps that listen without interrupting.
Level 2: Supervisory Control
This is where SCADA systems and HMIs live. Monitoring becomes more active. You use specialized tools to watch for unauthorized changes to configurations. You track who logs in and flag commands sent at unusual times. Attackers often target this level, so visibility must be sharp.
Level 3: Site Operations
Data historians and manufacturing systems reside here. Monitoring expands to cover entire production workflows. You send logs to your security system to look for signs of tampering. This is also where you can safely run vulnerability scans.
Level 3.5: The Security Gatehouse
This isn’t an operations level, it’s a security checkpoint that defines how teams approach choosing OT security monitoring controls between IT and OT.
Levels 4-5: The Business Network
This is standard office IT, email, databases, business software. The tools are familiar, but the goal changes. You’re now protecting the doorway to your factory systems. A hacked user account isn’t just an IT problem, it could be the first step in an attack on your plant. Good monitoring here gives you early warning.
Across many OT environments we’ve audited, segmentation is treated as optional because it feels complex or risky for legacy systems. In practice, every major incident we’ve investigated traced back to flat networks. Without clear zones, detecting threats becomes guesswork. With segmentation, abnormal traffic finally has somewhere obvious to surface.
“With distinctly segmented environments, it’s easier for both IT and OT teams to see where to monitor and secure any traffic and communications… This is where east-west traffic, the traffic between devices on the same network segment, comes in handy. The Purdue Model is far from dead.” – EmberOT Blog
On one plant floor, we discovered a legacy PLC sharing a network with an engineering workstation. No controls. When malware hit that laptop earlier, it had a direct path to the controller. After restructuring zones and monitored conduits, only a single HMI could communicate with it, and every violation generated alerts.
| Security Area | Flat OT Network | Segmented Purdue-Based Network |
| Threat visibility | Hard to detect abnormal activity | Clear alerts at zone boundaries |
| Lateral movement | Attackers move freely | Movement blocked and logged |
| Incident containment | Breach spreads quickly | Breach isolated to one zone |
| Legacy system protection | Directly exposed | Shielded behind conduits |
| Response speed | Slow and reactive | Fast and targeted |
The benefits scale quickly. East-west segmentation limits lateral movement, while north-south boundaries stop IT breaches from reaching operations, key to protecting critical infrastructure security across industrial environments.
We’ve seen this approach simplify IEC 62443 audits and drastically reduce attack surfaces. More importantly, it turns chaotic OT networks into systems teams can actually defend.
The Purdue Model isn’t perfect. It was made for older, isolated systems. Today’s smart devices and cloud connections break the rules. A sensor might send data straight to the internet, skipping your security gateways. This mix of office and factory tech makes the old, strict levels hard to follow.
All these new devices create a blind spot. They’re often added for convenience, not security. They don’t show up on your usual network maps. To handle this, you need to move from big security zones to tiny ones. You must control each device individually, not just whole sections of the network.
There’s also a big patching problem. You can update an office computer easily. Updating a factory machine might mean shutting down production for a year. Your security tools have to make up for this. They must block attacks targeting old, un-patchable machines and watch for signs someone is trying to hack them.
These challenges don’t mean the model is useless. It’s still the best starting point. Use it to build your main security areas. Then, add modern tools to protect the new, connected devices. The model is your solid foundation. Your smart, flexible monitoring is what makes it work today.

Start by knowing what you have. You need a list of every machine and device on your factory floor. This isn’t a computer scan, you have to walk around and write them down. Note what each device is and what it talks to.
Next, group your devices. Put machines that do the same job together. Then, decide who needs to talk to whom. Write down these allowed conversations in detail. Block everything else.
Now, put up your security tools. Put firewalls between your groups of devices. Install security software where you can. Make sure your strongest protection is at the main gateway between the factory and office networks. All these tools should send their logs to one central security system. This system connects the dots to show you attacks.
Finally, keep watching and improving. Set up alerts for strange activity. Run safe security checks. Practice your response to attacks. When you add new devices, update your groups and rules. This cycle of listing, grouping, protecting, and watching turns a plan into real security. It’s hard work, but it’s what keeps a factory safe.
The Purdue Model breaks industrial networks into clear levels, from Level 0 devices like sensors up to Level 5 enterprise systems. This structure helps teams monitor traffic between zones instead of guessing what normal activity looks like.
With proper network segmentation and access control, unusual behavior becomes easier to detect before it spreads across operational technology environments.
In control systems, many legacy systems were never built with security in mind. Network segmentation limits how far attackers can move if they gain access.
By separating Level 1 programmable logic controllers, Level 2 operator systems, and Level 3 operational servers, organizations reduce attack vectors while improving incident response speed across industrial systems.
Zero trust assumes no device or user should be trusted automatically, even inside industrial networks. When combined with the Purdue Model, zero trust architecture enforces strict verification between every level.
This approach strengthens access control, limits lateral movement, and helps defend operational technology from modern cyber threats tied to IT/OT convergence.
The connection between Level 3 operational systems and Level 4 business platforms like enterprise resource planning is a major risk point. Strong monitoring here tracks data flows, remote access, and unusual requests. This visibility helps catch early warning signs of breaches that could impact production, safety, and overall operational resilience.
Purdue Model security monitoring is about building clarity, not chasing checklists. We’ve seen the biggest wins start with one critical zone, mapped carefully, segmented properly, and monitored with intent. That small success creates momentum across the environment.
Threats will keep evolving, but structured visibility keeps you ahead. If you’re an MSSP looking to simplify tooling, improve detection, and strengthen OT security outcomes, work with our consulting team to select, audit, and optimize the right security stack for real-world operations.