Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Attackers get in. They move through your network quietly, copying files, mapping where things are. Standard security tools don’t catch them because these intruders work in the spaces where alarms don’t go off.
Threat hunters search differently. They read logs others skip over, notice traffic that looks normal but feels off, push back on what automated systems accept. Real people combined with actual data, that’s the mix.
Hackers change their methods faster than defenses can keep up, so organizations need hunters digging through networks instead of just sitting back waiting for something to trigger.
Keep reading to learn how this actually stops threats while they’re still inside and how proactive threat hunting intelligence works.

Proactive Threat hunting intelligence works differently than most security approaches. Instead of waiting for alerts to trigger, a human team assumes attackers are already moving through the network and searches for evidence of their presence.
We’ve seen this distinction matter countless times, reactive detection catches incidents after they’ve caused damage, but hunting finds them while they’re still operating.
The actual work combines knowledge of how attackers move (their tactics, techniques, procedures) with threat intelligence and behavioral analysis. Our teams look for indicators of compromise or attack that automated systems let slip by.
These aren’t always obvious patterns. Sometimes it’s a connection that shouldn’t exist, a file accessed at an odd hour, or data moving in a direction it shouldn’t.
From what we observe in MSSP environments, this matters because threats hide. Many attacks remain undetected for weeks or months before anyone notices. We’ve audited products where the dwell time, the period between initial breach and detection, stretched dangerously long.
Proactive hunting cuts that window down. When our clients implement this approach, they catch threats faster, respond better prepared, and reduce the actual damage these intruders cause.
Credits: SynerComm
Threat intelligence shapes how hunting actually works. Without it, hunters search blind. With it, they know where to look and what patterns matter most, especially when aligning hunts with proactive managed threat hunting strategies that help analysts concentrate on the behaviors that matter most.
Strategic intelligence shows the bigger picture. When we see ransomware targeting healthcare organizations, for instance, our clients know to focus resources there first. That’s not guessing, it’s informed prioritization based on what’s actually happening in their industry right now.
Then there’s tactical intelligence, which gets into the mechanics. Attackers tend to exploit specific vulnerabilities, use particular tools, follow patterns. Intelligence tells us what those patterns look like. If a newly discovered software flaw starts appearing in active attacks, we hunt for signs of it in our clients’ networks before widespread exploitation happens.
Operational intelligence is more immediate. It tracks active campaigns, the domains being used for phishing, the IP addresses launching attacks this week. We feed this into hunts so detection happens while the threat is still fresh.
Technical intelligence provides the specifics. File hashes, command-and-control server addresses, malware signatures. These let us confirm what we’ve found and block it before spread occurs.
We pull internal logs and alerts, then cross-reference them against external intelligence feeds. That combination validates what we discover and helps us adjust our approach. The layers stack together, transforming messy data into directions hunters can actually follow. [1]
The hunt follows a structured, iterative cycle:
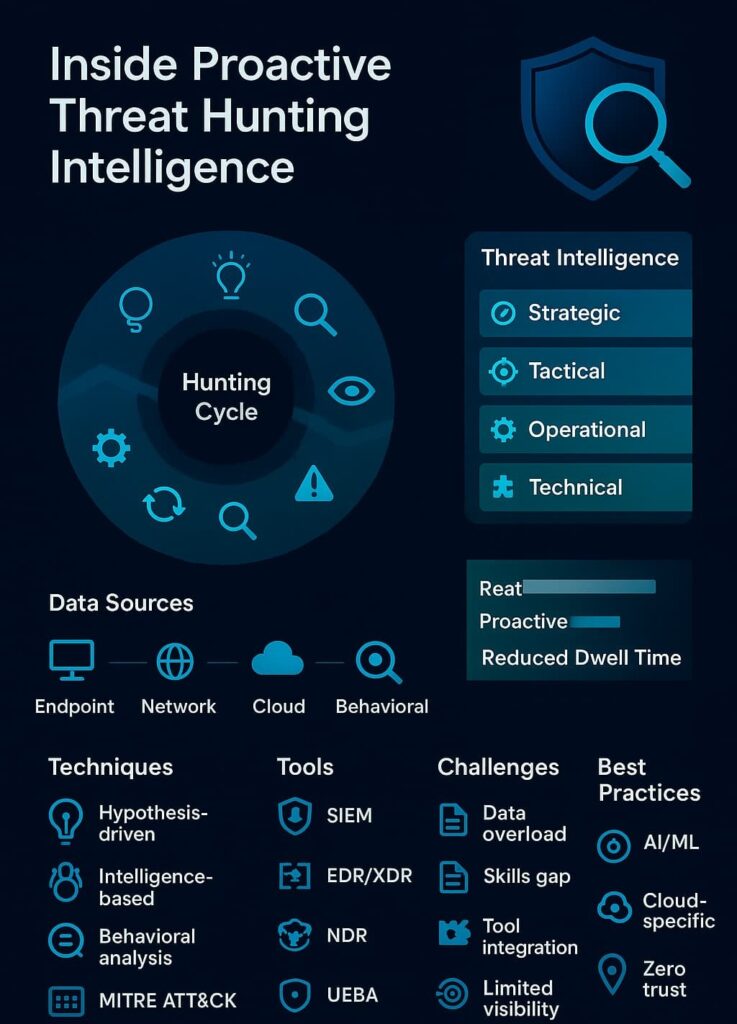
We employ several complementary approaches during hunts:
Effective hunting requires rich, diverse data:
By fusing these data sources, we build a comprehensive picture of activity, enabling detection of subtle threat behaviors.
The right technology stack amplifies our hunting capabilities:
In our MSSP Security practice, we integrate these tools seamlessly, orchestrating data flows and automating routine tasks so analysts can focus on high-impact investigations.
Proactive threat hunting is not without hurdles:
We address these by emphasizing training, collaboration, and leveraging MSSP Security’s expertise to augment internal teams.
Based on our hands-on experience, we recommend:
The landscape is evolving rapidly:
At MSSP Security, we embrace these trends to keep our threat hunting program adaptive and forward-looking.
Proactive threat hunting goes beyond alerts. It uses threat intelligence, behavioral analysis, and hunting hypotheses to find hidden risks before damage happens.
Unlike reactive monitoring, it studies attack TTPs, indicators of compromise, and network traffic analysis to uncover malicious behavior early, improving overall security posture and reducing attacker dwell time.
Analysts start with threat actor profiles, threat intelligence feeds, and MITRE ATT&CK data to form hunting hypotheses. They combine endpoint telemetry, log correlation, and behavioral analysis to validate assumptions.
This proactive cybersecurity process reveals attack patterns and supports continuous learning through threat hunting frameworks, helping teams adapt to evolving adversary techniques and improve detection accuracy.
Behavioral analysis helps identify anomalies that traditional detection tools might miss. It looks for unusual activity in endpoint detection and network data using security analytics and anomaly detection.
This approach uncovers advanced persistent threats and malicious behavior linked to threat actor infrastructure, strengthening defense through real-time threat hunting and continuous incident response improvement.
A typical threat hunting workflow includes hunting environment preparation, hunting hypothesis development, data fusion, and validation. Analysts collect hunting endpoint data, analyze network traffic, and refine detection logic using hunting automation tools.
This lifecycle approach ensures hunting insights translate into better SOC efficiency, improved detection engineering, and overall cybersecurity resilience.
Proactive threat hunting intelligence is no longer optional in today’s cyber battlefield. It’s a necessity, a strategic approach to outsmart attackers who slip past automated defenses. By combining human expertise, advanced data integration, and continuous learning, organizations can build stronger, more adaptive defenses.
Partnering with experienced MSSP Security teams gives your organization access to proven expertise, streamlined operations, and smarter tool integration. With over 15 years of experience and 48K+ successful projects, MSSP Security helps you reduce complexity, enhance visibility, and build a resilient security ecosystem aligned with your business goals.