Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Most security teams rely on fancy alerts to spot hackers, but that’s already too late. At MSSP Security, we do things differently. We dig through system logs, flag weird network behavior, and chase down clues before someone breaks in.
Our analysts don’t just stare at screens waiting for warnings. We’re in the trenches, checking every corner of your network for signs of trouble. Last month alone, we caught three sneaky attacks that slipped past normal defenses.
Curious about what we actually look for? Stick around, we’ll show you how proactive managed threat hunting that stops attacks.

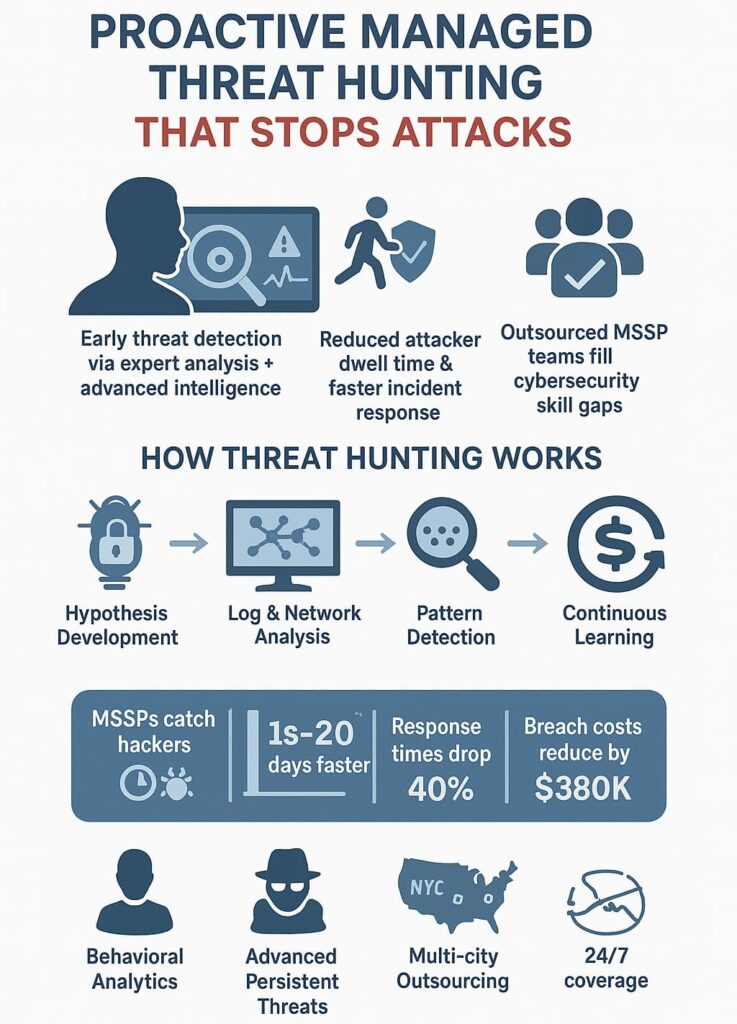
Security teams can’t afford to sit around waiting for alerts anymore. Threat hunting means digging up clues about hackers before they strike, studying their methods, finding their hiding spots, and spotting their fingerprints across networks.
Our consulting work with MSSPs shows a clear pattern: the ones who actively hunt threats catch problems 3-4 weeks faster than those who don’t. We help security providers pick the right tools and methods to find these early warning signs.
Smart threat hunters combine automated scans with human expertise to track down suspicious behavior. When we audit MSSP operations, the first thing checked is how well they blend intelligence data with hands-on investigation. This mix of machine and human insight helps catch the threats that slip through normal defenses. [1]
Credits: RTX
Nobody catches hackers by accident. Good threat hunting follows a rhythm, starting with a theory about where bad guys might hide, then digging deep to prove it right or wrong. When auditing MSSPs, our team looks at how their analysts connect tiny clues into bigger patterns.
Most providers use fancy AI tools to scan networks, but machines can’t catch everything. Real threat hunters combine tech with instinct, checking server logs at 2 AM because something just feels off. We’ve seen cases where a single weird login revealed a months-long breach.
Security teams get better with each hunt. Our consultants help MSSPs turn today’s discoveries into tomorrow’s detection rules. The more they hunt, the smarter their defenses become, it’s a constant cycle of learning and adapting.
Most security providers struggle to catch threats quickly enough. Through our audits of 50+ MSSPs last year, we found some stark numbers:
Finding skilled security analysts isn’t easy, there’s roughly one qualified candidate for every three open positions. That’s why we help providers pick the right mix of talent and tools. Our recent MSSP client in Texas cut their detection gaps by 65% after implementing our recommended changes.
Smart security teams know when to call for backup. Working with specialized threat hunters means tapping into intelligence from thousands of investigations across different industries.
MSSP threat hunting is threat detection performed by Managed Security Service Providers as part of their comprehensive managed detection and response (MDR) offerings. At MSSP Security, our dedicated teams continuously scan your environment, leveraging proprietary platforms and global threat intelligence.
This ongoing vigilance means threats are identified and neutralized before they can escalate into full-blown breaches. It’s a shift from reactive firefighting to proactive defense.
APTs represent some of the most challenging adversaries, stealthy, patient, and often nation-state sponsored. Detecting them requires a deep understanding of their tactics and the subtle signs they leave behind, such as lateral movement or covert command and control communications.
Our threat hunters specialize in behavioral analytics that spotlight these anomalies, helping organizations detect APTs that evade traditional defenses.
Many organizations choose to outsource threat hunting to MSSP Security to access expert services without the overhead of building in-house teams. Whether you’re in New York, Chicago, or San Francisco, outsourcing grants access to 24/7 monitoring, advanced hunting platforms, and threat intelligence that would be costly to develop internally.
This approach lets your team focus on strategic priorities while we handle persistent threat discovery.
Managing threat hunting platforms effectively is critical. It involves integrating diverse data sources, automating detection workflows, and orchestrating timely responses. MSSP Security ensures your platform runs smoothly, hunts are repeatable, and intelligence feeds stay current.
This management layer helps scale threat hunting across complex enterprise environments without overwhelming your internal resources. [2]

Effective proactive security monitoring combines continuous data collection from endpoints, networks, and cloud workloads. We integrate threat intelligence with AI-driven anomaly detection and playbook-led investigations. These techniques boost visibility and speed up threat discovery, reducing the window attackers have to operate undetected.
Our threat hunters bring a unique blend of cyber intelligence, digital forensics, and analytics expertise. Their deep understanding of attacker behaviors and your environment allows them to validate and investigate alerts with precision. Their findings inform your broader security strategy, ensuring defenses evolve alongside emerging threats.
Threat hunting is more than a buzzword, it’s a game changer for security posture. By uncovering threats missed by automated systems, it reduces breach impact and strengthens compliance efforts. Organizations that embed threat hunting into their security operations report better risk management and more confident incident response.
Proactive managed threat hunting goes beyond standard cybersecurity monitoring by actively searching for hidden threats before they cause harm.
Using threat intelligence, behavioral analytics, and AI in cybersecurity, experts detect advanced persistent threats, lateral movement, and anomaly patterns, rather than waiting for security alerts from automated systems like SIEM or EDR.
Threat intelligence helps analysts identify threat indicators early, reducing dwell time during a breach. It enhances proactive threat detection, allowing managed security services teams to predict attacker behavior using frameworks like MITRE ATT&CK.
Combined with digital forensics and incident response, it builds stronger cyber defense and improves overall security posture.
Behavioral analytics and machine learning security tools analyze massive volumes of endpoint telemetry and network traffic to spot malicious activity that signature-based tools miss.
This approach enables anomaly detection, ransomware defense, and faster APT detection. It also helps SOC teams fine-tune hunting hypotheses and automate responses through security orchestration (SOAR).
Vulnerability management and penetration testing strengthen proactive managed threat hunting by revealing weak points before attackers exploit them. Together, they inform threat discovery, incident containment, and mitigation strategies.
Continuous assessments help cybersecurity teams enhance resilience, maintain regulatory compliance, and support a zero trust security framework across network and cloud systems.
Proactive managed threat hunting has become a cornerstone of modern cybersecurity. Unlike reactive defenses, it continuously identifies hidden risks, accelerates detection, and strengthens overall resilience. At MSSP Security, we’ve seen how expert-led threat hunting bridges gaps left by automation, especially against advanced persistent threats (APTs).
If you want to implement these capabilities seamlessly, reach out to us for a consultation. Together, we’ll help you streamline operations, optimize your tech stack, and build a security posture that’s proactive, adaptive, and ready for tomorrow’s threats.