Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

SQL injection and XSS attacks persist because developers still let untrusted input reach executable code. The core defense is separating data from logic through parameterized queries, strict validation, and proper output encoding. OWASP and modern frameworks repeat this because it works, yet real breaches keep happening in finance, healthcare, and SaaS due to small implementation gaps.
One missed encoding step or unsafe form field can open the door. This guide focuses on practical lessons from what succeeds and what fails in production, so teams can apply defenses without slowing development. Keep reading to see how to stop them.
Think of them as two sides of the same dirty coin. SQL injection messes with our database queries. XSS (Cross-Site Scripting) injects malicious scripts into our web pages. Different targets, same root cause: trusting input we shouldn’t.
The OWASP Top 10 for 2023 still lists them both near the top. That tells us everything. They’re not rare or complicated. They’re common.
In practice, SQLi hits our server and database. XSS targets our users’ browsers. We’ve reviewed incidents where an app had both. A team would fix the SQL injection on a login page but forget about the XSS in a comment field. Attackers notice that gap faster than we think.
Why do they persist? The defenses are well-known. The problem is consistency. Applying them to every endpoint, every API, every legacy feature, that’s the hard part.

It starts with a simple, dangerous idea: letting user input become part of a SQL command. Imagine a login form. The code takes a username and password, slaps them into a query string, and sends it to the database. If that input contains actual SQL code, the database will run it. That’s SQL injection.
OWASP testing data suggests about 65% of web apps still have some injection flaw. It’s that common. We’ve seen it ourselves. A mature codebase, solid security posture, then a single dynamic query built with string concatenation in a forgotten admin tool. Boom. Authentication bypass.
The danger grows with dynamic SQL and detailed error messages. Those errors are a goldmine for attackers, revealing table names and structures so they can refine their next payload. Attackers use tricks to bypass logins. The database just sees it as more SQL to run. It doesn’t know the difference between data and code.
These techniques have fancy names, blind SQLi, union-based, error-based, but they all stem from the same basic mistake. MITRE tracks it as CWE-89.
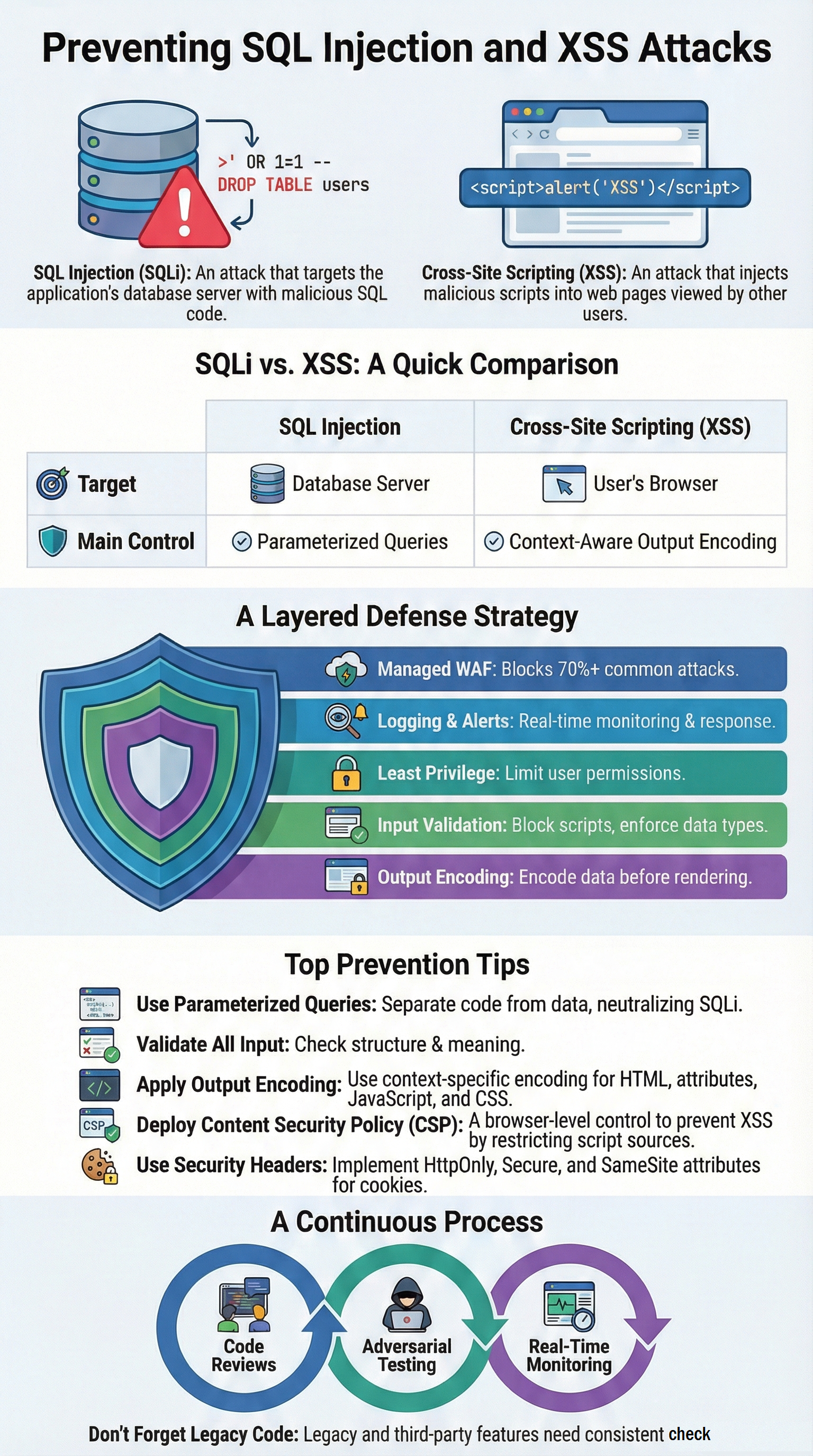
The answer isn’t a secret. It’s a practice: parameterized queries. Also called prepared statements. They force a separation between the SQL command and the data filling it. The database knows, “This part is instruction, this part is just value.” Input can’t change the logic.
Studies cited by groups like SANS show this simple step can cut SQLi risk by 90% or more. It works on MySQL, PostgreSQL, SQL Server, we name it.
In the environments we help manage, we push for framework-level enforcement. Make parameterization the default path, so a developer has to work hard to do the unsafe thing.
Pair this with least-privilege access. Our app’s database user should only have the permissions it absolutely needs. If a query does get injected, the damage is contained. No dropping tables from a login function.
A quick note on stored procedures: they only help if they also use parameters internally. A stored proc that builds dynamic SQL inside is just moving the problem around. We see this misunderstanding in audits all the time.
Credits: Web Dev Simplified
If SQL injection attacks our database, XSS attacks our users. It lets an attacker run their own malicious scripts inside a victim’s browser. Think session hijacking, stolen cookies, logged keystrokes.Data from the Mozilla Developer Network suggests about a third of web vulnerabilities involve XSS. It’s a persistent plague.
“Because [the browser] thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site.” – OWASP Foundation [1].
The danger is in the ripple effect. We’ve seen a single stored XSS flaw in a messaging system lead to mass session hijacking. Why? Because the session cookies weren’t locked down with HttpOnly and Secure flags. One flaw, multiplied.
When teams discover gaps late in the process, a structured data breach investigation service often becomes critical for tracing exploitation paths and confirming whether SQLi or XSS payloads reached sensitive systems.
The script runs with the victim’s permissions. It can do anything that user can do. Send messages, transfer funds, change settings. And it often spreads silently, user to user. MITRE classifies this under CWE-79, and OWASP has volumes of guidance on it.
There are three main flavors, and we need to know them all.
The prevention principles are similar, but we have to know where the injection happens to choose the right defense.
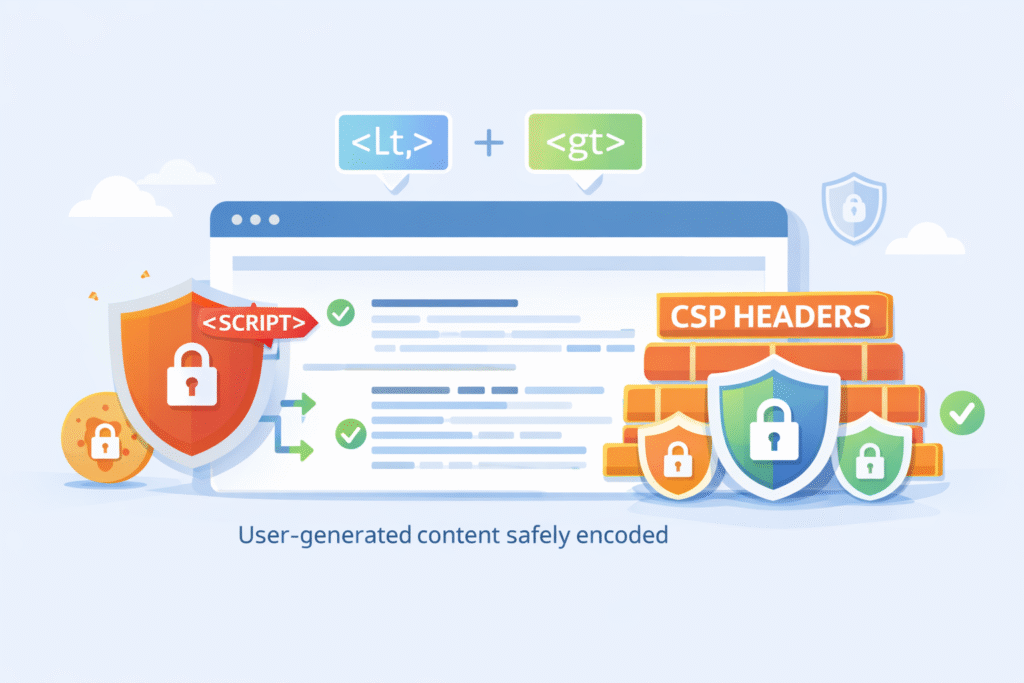
We stop XSS by making sure any user input is safe before it gets to the browser. This isn’t one trick; it’s a combination.
“Cross-site scripting vulnerabilities are dangerous because they don’t attack the application itself but exploit user trust in a legitimate website. Allowing attackers to hijack user sessions, steal sensitive information, or even alter website content to trick users.” – CISA [2].
First, context-aware output encoding. This is the cornerstone. We don’t just “encode” data. We encode it for where it’s going.
They’re not interchangeable. Using HTML encoding in a JavaScript context does nothing.
Modern frameworks like React, Angular, and Vue do this auto-escaping for us, which is fantastic. But we constantly see XSS creep in when developers use dangerously Set Inner HTML in React or bypass the sanitizer in Angular for “performance.” It’s almost never worth the risk.
Second, strict input validation. Validate for type, length, format, and business rules on the server-side. Client-side validation is for user experience, not security. It can be bypassed.
Third, deploy a strong Content Security Policy (CSP). This is a browser-side safety net. A CSP header tells the browser which sources of scripts, styles, and other resources are allowed.
Research from the Google Chrome security team suggests a well-configured CSP can cut XSS exploitation success by about half. It stops the attack even if a malicious script somehow slips through our other defenses.
Also, use security headers: X-XSS-Protection, SameSite cookies, and always mark session cookies as HttpOnly. This shrinks the blast radius.
No single silver bullet exists. Real security comes from layers. We assume one layer might fail, so we have another behind it.
A Web Application Firewall (WAF) is a great outer layer. Many teams rely on a managed Web Application Firewall (WAF) approach to apply consistent filtering rules across high-traffic applications, especially when patching every legacy endpoint is not realistic.
Threat reports from companies like Cloudflare show WAFs can block up to 70% of automated attacks before they even touch our application logic. They filter out the common SQLi and XSS payloads. But we can’t rely on a WAF alone. The core layers are in our code.
We design systems with this layered mindset. The table below shows how shared controls apply to each threat.
| Defense Layer | SQL Injection Protection | XSS Protection |
| Input Validation | Enforces data types (e.g., this field is an integer). | Blocks scripts at the door by rejecting invalid patterns. |
| Output Encoding | Not really applicable here. | Critical. Neutralizes scripts by encoding them for the output context. |
| Least Privilege | Limits what the database user can do, containing damage. | Limits user account permissions, reducing what a hijacked session can do. |
| WAF Rules | Filters out common SQLi payloads in requests. | Filters out common XSS payloads in requests and responses. |
| Logging & Alerts | Detects unusual database query patterns. | Detects attempted script injection or anomalous client-side behavior. |
These controls aren’t new. They align perfectly with guidance from NIST and standards like PCI DSS. It’s about making them work together, consistently.
They tackle different parts of the problem, but the mindset is the same: distrust user input.
These controls aren’t new. They align perfectly with guidance from NIST and standards like PCI DSS. Teams often see the biggest improvement when they understand the long-term managed WAF service benefits of pairing traffic filtering with continuous rule tuning and monitoring, rather than treating it as a static control.
SQLi defense is a server and database game. Our main weapon is the parameterized query. Our strategy is to lock down database permissions and validate input types. The goal is to protect our data store.
XSS defense is about the boundary between our server and the user’s browser. Our main weapon is contextual output encoding. Our strategy involves security headers like CSP and cookie flags. The goal is to protect our users’ sessions and our page integrity.
We advise teams to tackle them together. The secure coding standards we build for one will strengthen the other.
| Aspect | SQL Injection | XSS (Cross-Site Scripting) |
| Primary Control | Parameterized Queries / Prepared Statements | Context-Aware Output Encoding |
| Execution Location | Database Server | User’s Web Browser |
| Common Impact | Data Breach, Data Loss | Session Hijacking, Defacement, Client-Side Data Theft |
| Key Standard | CWE-89 | CWE-79 |
Treating them as a unified front makes our training, code reviews, and long-term maintenance much simpler.
Parameterized queries separate user input from SQL commands, so attackers cannot change the query structure. This prevents common attacks like authentication bypass and union-based SQL injection. Prepared statements also reduce the risks of dynamic SQL and improve safer error handling. Teams should combine query parameterization with the least privilege principle to limit database permissions and reduce potential damage.
Output encoding protects users by converting untrusted input into safe text before it appears in a page. HTML escaping, JavaScript encoding, and URL encoding each apply in different contexts. These methods block reflected XSS, stored XSS, and DOM-based XSS payloads. Proper encoding is more reliable than blacklist filtering because attackers can bypass weak pattern checks.
Framework security features help, but input validation still prevents harmful data from entering the system. Server-side validation using whitelist validation and input length limits reduces script injection and SQL escaping errors. Client-side validation improves usability, but it cannot stop attackers. Strong validation also helps protect APIs from threats like GraphQL injection and NoSQL injection.
Content Security Policy (CSP headers) adds an extra browser-side defense against malicious scripts. Even if unsafe code reaches the page, CSP can block unauthorized script sources. When combined with HTTPOnly cookies, Secure flag cookies, and the SameSite attribute, CSP reduces the risk of session hijacking. This approach strengthens protection against event handler XSS and script injection attempts.
Penetration testing, vulnerability scanning, and DAST scanning help teams find SQL injection and XSS flaws before attackers exploit them. Logging attacks and maintaining audit trails also reveal repeated intrusion attempts. Secure error messages and generic errors prevent attackers from learning system details. Regular code reviews and SAST tools support consistent secure coding practices over time.
Preventing SQL injection and XSS attacks depends on discipline, consistency, and layered defenses across every input and output. Teams that reduce risk treat secure coding as ongoing operational hygiene, not a one-time patch.
In our work at MSSP Security, we see the best outcomes when engineering, security, and operations share ownership of these controls over time. If you want expert guidance to strengthen your security stack, join our MSSP Security consulting here.