Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
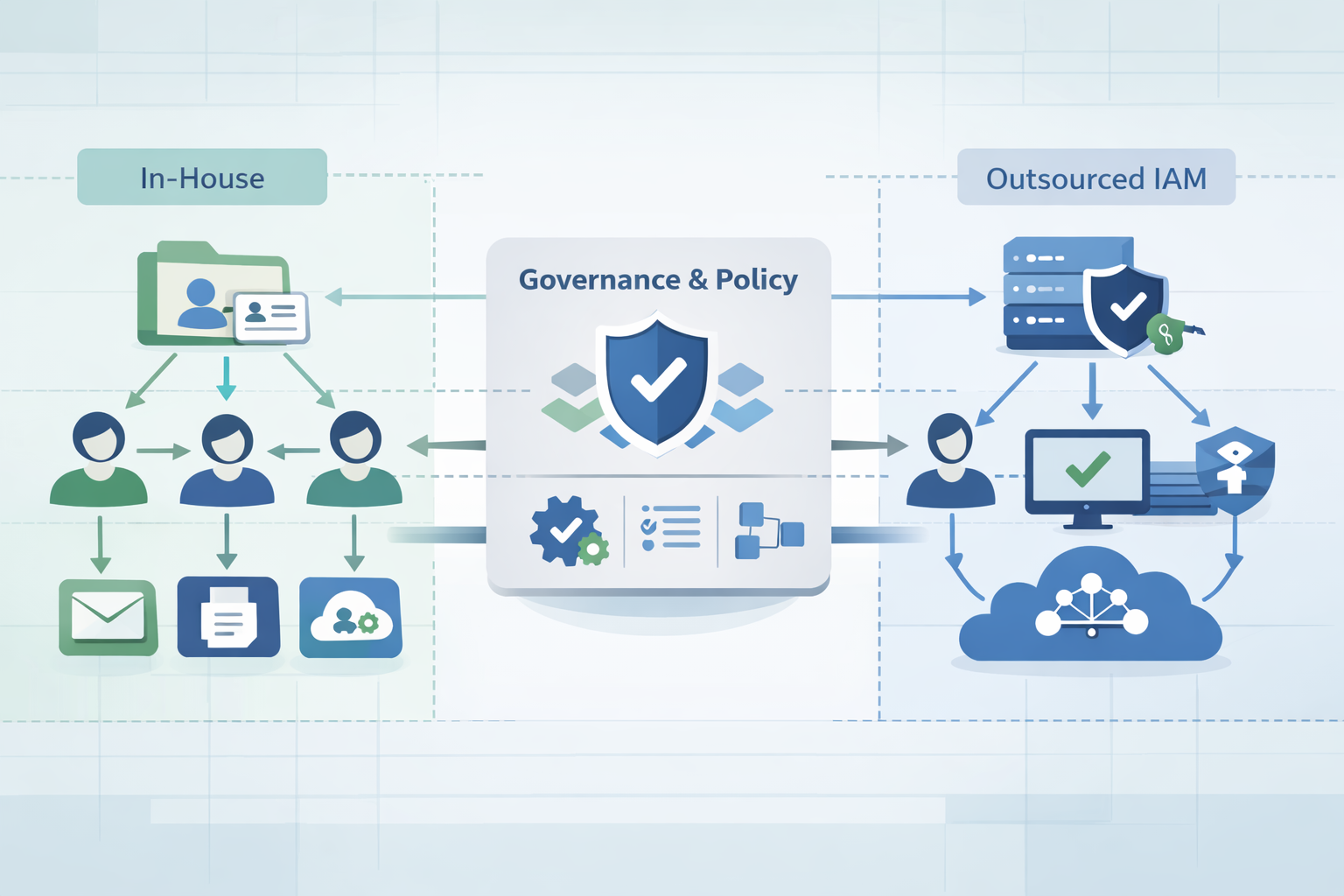
Outsourced identity access management now runs quietly behind most modern security operations. We have seen this firsthand across real environments. Teams no longer debate whether identity matters; they struggle with running it reliably at scale. When identity governs every login, API call, and privileged action, keeping it fully in-house often introduces risk instead of control.
Outsourcing IAM shifts lifecycle management, authentication, and access governance to specialists, while organizations retain ownership of strategy and policy. The outcome is tighter security, smoother operations, and fewer hidden gaps. Identity has become the control plane for everything else. Keep reading to see why this shift matters.
When organizations outsource IAM, they are not giving away control of “who can access what.” They are giving away the heavy lifting of running the systems that enforce these rules, keep them updated, and prove they are working.
Instead of:
They bring in a provider that runs IAM as an always-on service.
We see two big shifts when this happens:
For MSSPs, outsourced IAM also changes the consulting work. Our own role is to help MSSPs:
Outsourcing IAM does not remove responsibility. It changes where the work happens and who does what.
Day to day, IAM providers sit in the path of every access decision. The work is more detailed than many MSSP leaders expect the first time we map it out.
Typical responsibilities include:
When we sit with an MSSP and map these flows, the pattern is always the same: the provider’s value comes from consistency. The rule is applied the same way at 3 a.m. Tuesday as it is at noon Friday, no matter who is shouting for an exception.
On paper, in-house and outsourced IAM can look similar. Same protocols. Same buzzwords. But day to day, the differences become clear very quickly.
Table In-House IAM vs Outsourced IAM (Operational View)
| Aspect | In-House IAM | Outsourced IAM |
| Primary focus | IAM shared with other IT and security tasks | Identity operations as a dedicated service |
| Operating model | Reactive, ticket-driven, manual fixes | 24/7 service with standard runbooks |
| Change management | Informal, often rushed | Controlled, documented, auditable |
| Cost structure | Projects, upgrades, specialist hires | Predictable service-based pricing |
| Accountability | Shared and often unclear | Defined SLAs and ownership |
Key contrasts we see:
We have seen MSSPs stuck in the middle: they are asked to “review IAM” or “help with MFA,” but the underlying platform is half-built by internal teams. Outsourced IAM, when selected and audited well, gives MSSPs a firmer base to secure everything else.

Outsourced IAM is not just one big platform logo. It is a framework made of pieces that need to work together cleanly. When those pieces clash, MSSPs feel it first during incidents and audits.
We usually break it down into four core parts.
Identity repositories are the source of truth. If they are wrong, every access decision built on top is wrong too.
In a solid outsourced IAM setup, we expect to see:
Any time we audit an MSSP’s environment and find multiple “sources of truth,” we know access risk is already baked in. Good outsourced IAM keeps those sources aligned and constantly checked.
Attackers love weak authentication. That is why we pay so much attention to how IAM providers handle it. Modern guidance aligns with this reality. The research makes it clear that access decisions should not rely on a fixed perimeter, but instead be continuously evaluated based on identity, context, and risk [1]. This is why outsourced IAM must enforce MFA, adaptive checks, and step-up authentication as default behavior, not optional controls.
Core elements we look for:
We have watched MFA projects fail because users hated them and leadership backed down. When authentication is managed well by an outsourced IAM provider, friction is low enough that users accept it, and strong enough that attackers do not.
Authentication answers “who are you.” Authorization answers “what are you allowed to do.” For breach impact, authorization usually matters more.
In outsourced IAM, we expect:
From our side, when we help an MSSP pick products, we test how easy or hard it is to enforce these controls in real life, not just on slides. The difference shows up fast when there is an incident.
Without identity logs, the SOC is half-blind. This is not just an operational inconvenience, it is a proven risk pattern. The study reports that credential misuse remains one of the most common paths attackers use to access environments [2]. When IAM events are missing, delayed, or incomplete, security teams lose the ability to trace how access was gained and what actions followed.
Outsourced IAM should bring:
We push hard on this when we audit products for MSSPs. Identity logs are where real Zero Trust monitoring starts.
Organizations rarely outsource IAM to save a few dollars. They usually do it because the current identity setup is fragile and the risk is too high.
For MSSPs and their clients, the main benefits tend to cluster around cost, expertise, scale, and compliance.
Running IAM well in-house means:
Outsourced IAM turns those into a service with predictable monthly or yearly costs, shared infrastructure managed by specialists, and fewer surprise upgrade projects. For many teams, this operational stability comes from relying on managed IAM support services that treat identity operations as a continuous security function rather than a series of one-off projects:
We see MSSPs benefit here too. Instead of babysitting a custom IAM build for each client, they can lean on standardized, audited services, and focus their time on detection, response, and consulting.
Identity is a deep niche. It touches SAML, OAuth, OpenID Connect, SCIM, device trust, and more. Most general IT or security teams only touch parts of it.
IAM providers bring:
Our own consulting work often starts here. We help MSSPs judge whether a given IAM vendor actually understands:
Theory is easy. Enforcement is what counts. We use real-world scenarios to tell those apart.
User counts rarely stay flat. Remote work, contractors, partner access, and customer portals all stretch identity systems.
Outsourced IAM helps by:
We have seen MSSPs struggle when each new client brings another custom IAM puzzle. When the core is outsourced and designed for multi-tenant use, adding new users and new clients becomes a predictable task instead of a fire drill.
Identity sits in the middle of most security frameworks. Regulations rarely say “use this specific IAM product,” but they do demand:
A mature outsourced IAM provider usually supports mapped controls for GDPR, SOC 2, ISO 27001, NIST frameworks, and NIS 2, along with pre-built reports to show access reviews, MFA coverage, and admin activity. This level of audit readiness is often reinforced through MSSP compliance reporting services that translate identity events into evidence auditors can actually use:
For MSSPs, this is useful twice: once for their own operations, and again when they help clients prove compliance. We routinely evaluate if a product’s IAM features can actually produce the evidence auditors ask for, not just tick a sales checkbox.

None of this is free of risk. When you hand over identity operations, you are trusting someone else with your most sensitive control surface.
We spend a lot of time helping MSSPs understand these trade-offs clearly.
If an IAM provider is breached or misconfigured, many customers can be exposed at once. That is classic supply chain risk.
Mitigation steps we watch for:
Our stance is simple: treat IAM providers as critical infrastructure. If they fail, the blast radius is large, so the due diligence needs to match that.
Most IAM platforms are multi-tenant. That is normal. The question is how tenants are separated.
We look for:
During product audits for MSSPs, we ask hard questions here. How is tenant context enforced in code? How is it tested? Weak answers are a red flag.
When IAM is outsourced, some teams feel they are “losing control.” In practice, what usually changes is the type of control:
Healthy outsourced IAM setups give:
We encourage MSSPs to push clients toward this mindset: operational control can move outside, but governance must stay in-house.
Choosing to outsource IAM should be treated like a design decision, not a quick purchase. We have seen projects go sideways when this step is rushed.
A few areas always deserve careful review.
If IAM cannot reach your apps, it cannot protect them.
Integration checks should cover:
For MSSPs, we also test how IAM integrates with existing SIEM, SOAR, and MDR tooling, ticketing systems for approvals and reviews, and endpoint tools that may supply device trust signals. This is where strong Identity Access Management (IAM) support matters, because integration failures often surface first during incidents, not during design reviews:
Integration is where “nice architecture” meets reality.
Most of the MSSPs we work with are heading toward some form of Zero Trust model, even if they do not use the label. IAM must support that path.
Requirements usually include:
We also pay attention to customer and partner-facing IAM (CIAM and B2B). If those are bolted on as an afterthought, scale and privacy problems show up later.
SLAs are where expectations become enforceable. Weak SLAs lead to finger-pointing.
Good IAM SLAs tend to cover:
We advise MSSPs to push for clear shared responsibility models. Who patches what? Who handles misconfigurations? Who talks to regulators if something goes wrong? Writing this down early saves a lot of pain later.

Not every organization wants, or needs, to outsource everything. Hybrid IAM models are common, and sometimes the best choice.
We see this most often in regulated sectors and in MSSPs with very sensitive internal environments.
A balanced hybrid approach might look like this:
In this setup, outsourced IAM becomes a force multiplier. Internal staff set rules and review outcomes, while providers handle the constant operational churn.
Our consulting work often sits right here: helping MSSPs define where the line should be, and which IAM products support that split cleanly.
We see outsourced IAM patterns repeat across sectors:
From our side, we approach IAM not as a shiny product category but as a living security system. It breaks, it evolves, it gets tested by real attackers every day. Our job is to help MSSPs pick, question, and audit IAM products so their clients get stronger controls, not just more dashboards.
Outsourced identity access management helps teams avoid daily access issues and security mistakes. IAM outsourcing takes over user provisioning services, access control outsourcing, and identity lifecycle management. This reduces errors with privileged access management and role-based access control. Internal teams spend less time fixing access problems and more time setting rules, reviewing risk, and supporting the business safely.
IAM outsourcing supports zero trust IAM by checking access every time, not just once. It enforces least privilege enforcement, just-in-time access, and multi-factor authentication outsourcing in the background. Users log in securely without extra steps. This also replaces VPN access with zero trust network access, endpoint access control, and safer remote access IAM.
Third-party IAM providers handle outsourced user management and identity lifecycle management. This includes Active Directory outsourcing, LDAP management, SCIM provisioning, and federated identity outsourcing using SAML outsourcing, OAuth services, and OpenID Connect providers. They also manage session management services, privileged account management, and IAM monitoring to spot risky behavior early.
IAM managed services make audits easier by keeping access records in one place. Providers run access governance, audit logging outsourcing, and compliance reporting IAM. They support GDPR IAM outsourcing, SOC 2 IAM services, ISO 27001 IAM, and the NIST IAM framework. This gives clear proof of who accessed what, when, and why.
Outsourced IAM often costs less when systems grow across cloud IAM providers and hybrid IAM models. External IAM solutions reduce tool overlap, failed setups, and manual fixes. IAM cost optimization improves with scalable IAM solutions, clear service level agreements IAM, and fewer emergency issues. Teams avoid hiring more staff just to manage access problems.
Outsourced identity access management is no longer about convenience. It is about survival in an access-driven threat landscape. Identity now governs users, workloads, APIs, and customers, and when those controls fail, everything downstream fails with them.
Teams that outsource IAM well gain consistency, visibility, and resilience. Those that delay usually uncover identity risk the hard way. Treat IAM as a managed security discipline from day one, backed by governance and real operational expertise.
Work with MSSP Security to build and audit IAM the right way