Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Next-gen firewalls see everything, and they notice when an accountant tries to sneak around network rules. They scan packets, watch apps, and track who’s doing what on the network.
But there’s a catch: skipping SSL inspection or getting automation wrong leaves the door wide open for attackers. These aren’t your grandfather’s port blockers anymore.
Setting them up right takes more than clicking “next” in some wizard (plenty of admins learned this the hard way). Want to know how to lock things down properly? Keep reading.
A peek inside any modern network reveals how next-gen firewalls have become the new standard. Anyone who’s worked with traditional firewalls knows they just don’t cut it anymore. Let’s face it – today’s networks need more muscle.
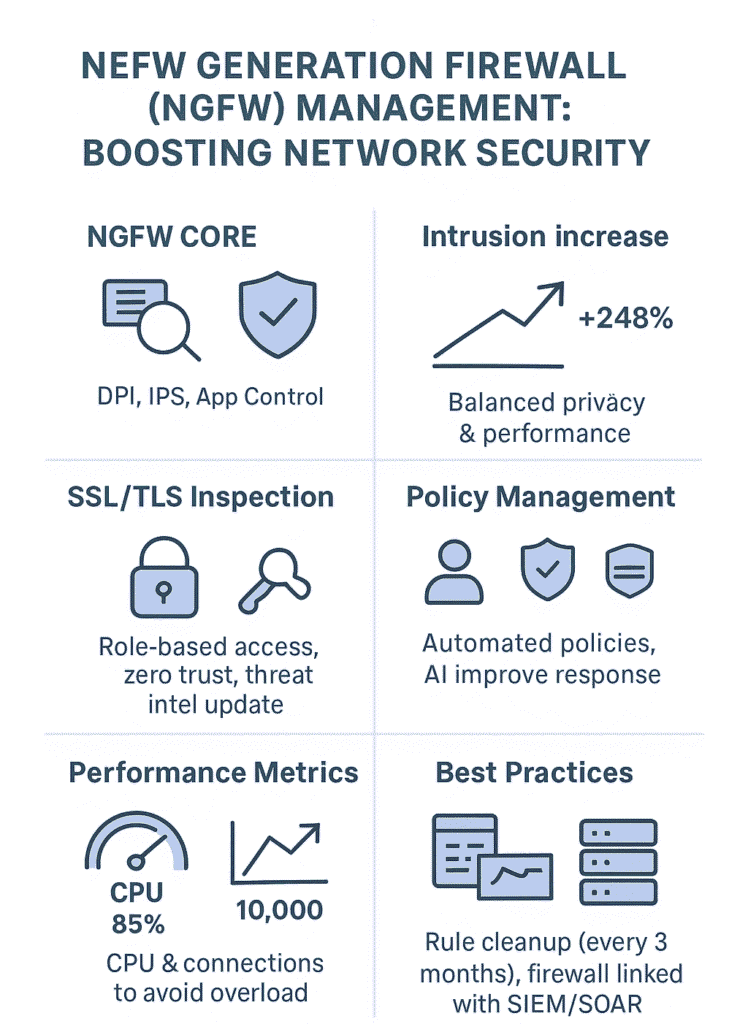
Deep packet inspection (DPI) sits at the core of what makes these systems work. Old school firewalls basically just checked port numbers and protocols, but DPI digs right into the data itself.
Security teams can see exactly what’s flowing through their pipes, down to individual application commands (which comes in pretty handy when things go sideways).
The built-in Intrusion Prevention Systems (IPS) are equally essential. They don’t just scan for known signatures, they analyze traffic behavior, spot anomalies, and can block attacks in real time.
Given that “interactive intrusion attempts” have increased by 248 % in recent years, the need for behavior-based detection has never been higher (1). Zero-day attacks that used to slip right through? Not so much anymore.
Application control gives these firewalls some serious smarts about what’s actually running on the network. Doesn’t matter if an app tries to hide on some weird port, the firewall knows what it is and can shut it down if needed.
SSL/TLS decryption capabilities add another whole layer to this. With most web stuff encrypted these days, being able to peek inside that traffic is huge. Network teams constantly find malware trying to sneak through encrypted channels.
Getting encrypted traffic inspection right isn’t easy. Sure, you want to catch the bad stuff hiding in encrypted sessions, but you’ve got to balance that against performance hits and privacy concerns.
Most places end up using different inspection rules for different groups, maybe looking closer at guest traffic while letting trusted admin sessions flow faster.
It’s all about tuning those policies just right. And don’t forget, those decryption rules need constant updates or they’ll miss new tricks attackers come up with.
Finally, there’s a financial angle that often tips the balance toward inspection: the average cost of a data breach was reported at about $4.45 million in 2023 (IBM), so when encrypted channels are used to hide.
Intrusions the potential impact can be very large, which is why major vendors (Microsoft, IBM and others) now publish tooling and guidance for TLS inspection and secure decryption workflows (2)

Credits: pexels.com (Photo by Mikhail Nilov)
Managing these firewalls means getting serious about policy control. Zero trust is the name of the game now, everyone gets checked, no exceptions. Role-based stuff helps figure out who should access what (and more importantly, who shouldn’t).
Teams often combine these rules with broader managed firewall services to streamline oversight and keep policies consistent across complex environments.
The threat landscape changes fast, so detection has to combine both known signatures and behavior watching. Feed in some threat intelligence, and the firewall learns about new attacks automatically. No waiting around for someone to manually update rules.
Too many places let their rule sets get messy over time. Rules pile up, overlap, sometimes even fight with each other. Regular cleanup isn’t fun but it’s necessary, messy rules mean slower firewalls and security gaps.
Nobody’s got time to manually handle everything anymore. AI helps spot patterns in security events way faster than human eyes could. This frees up the security folks to hunt down serious threats instead of doing routine stuff.
Alongside automation, organizations highlight the benefits of pairing NGFW policies with a managed firewall service, where proactive monitoring and policy updates reduce the burden on in-house teams.
Basic tasks like patches and updates run on autopilot through management platforms. Makes sense, fewer human touches means fewer chances to mess something up.
When something sketchy does pop up, these systems can react right away, blocking traffic, quarantining network segments, or getting help on the scene.
Anyone who’s spent time handling modern firewalls knows it’s nothing like the simple point and click setups from 2013. Think about managing security across offices in Singapore, London, and Chicago. You’d go crazy trying to watch separate screens, hoping nothing crashes while you’re focused elsewhere.
For many, outsourced firewall management becomes a practical way to balance pricing concerns with enterprise-grade protection, especially when scaling across global branches.
The big players now run these slick command centers that pull everything into one view (even if getting there means wrestling with legacy systems and cranky APIs).
No security team’s got time to dig through yesterday’s noise when something’s crushing the network right now. And when a firewall hits 85% CPU, that’s not just a number on a dashboard, that’s a four-alarm fire waiting to happen.
These next gen systems are doing heavy lifting most folks don’t see, breaking down packets and encrypted stuff bit by bit. Takes some serious processing power, especially when everyone’s streaming their lunch break Netflix.
Updates well, that’s always interesting, like performing surgery while the patient’s running a marathon. Nobody wants to push changes during business hours, so there’s usually some bleary eyed admin running tests at 2 AM on a Saturday, living on energy drinks and pure hope.
Smart teams build these interconnected systems, where firewalls feed into threat analysis tools, and sandboxes catch the weird stuff before it hits production. It’s like those classic crime movies where every guy’s covering someone else’s blind spots.
As traffic keeps climbing, these systems need room to grow. Users couldn’t care less about your fancy IPS signatures when their connections move like frozen honey.
Sometimes it’s just about housekeeping, clearing out rules from three years ago, or finally getting approval for that hardware refresh that accounting kept dodging.
The metrics tell the real story, memory usage, CPU load, connections per second. Good teams spot the trends, add capacity before users start flooding the help desk.
We watched one setup hit the wall at 10,000 connections per second before things got ugly. But that’s just one network, every environment’s different. When it’s all working right, people shouldn’t even notice the firewall’s there. That’s what you’re aiming for.

Credits: pexels.com (Photo by Tima Miroshnichenko)
Getting policy rules right makes all the difference between true security and just having expensive gear sitting in a rack. When policies match what the business actually needs (not what some vendor says it needs), that’s when NGFWs really shine.
Most teams forget that exceptions aren’t always bad, sometimes you’ve got to loosen things up a bit, as long as you know the risks.
Security rules don’t have to be complicated. They just need to be crystal clear so admins don’t mess things up at 3 AM during an emergency change window. Plus, everyone’s got to be on the same page about what’s allowed and what’s not.
Look, firewalls get messy fast. Rules pile up like old newspapers, and before you know it, you’re running hundreds of policies that nobody remembers creating. Smart teams check their rules every 3 months (or right after big network changes).
It’s kind of like cleaning out your garage, nobody wants to do it, but you’ve got to trash the junk you don’t need anymore. Traffic inspection’s a must these days, especially with encrypted stuff (which is pretty much everything now).
Sure, it’s a pain trying to figure out how much inspection you can do before everything slows to a crawl. What seems to work best is turning up the inspection heat on sketchy traffic while going easier on trusted flows.
When you hook your NGFW into your other security tools, your SIEM, your SOAR platform (if you’ve got one), that’s when things start clicking. The security team can actually hunt down threats instead of just staring at firewall logs all day hoping to spot something weird.
Network admins deserve more recognition, honestly. Between juggling user complaints and keeping those finicky firewalls humming along, they’re doing a lot more than just pushing buttons and praying nothing breaks.
Been watching these security teams do their thing, and there’s a clear pattern, the ones who really know their stuff are neck deep in their next gen firewall features. They’re the ones getting their hands dirty with application tracking and SSL inspection (which, yeah, can be a real pain to set up right).
It’s this weird balancing act. You’ve got people who need to get their work done, but you can’t just open the floodgates and hope nothing bad happens. Zero trust sounds great on paper, but implementing it? That’s where things get messy.
Automation’s been a game changer though. Most teams were drowning in alerts before they got their scripts and automated responses working right. Now they’re catching weird network stuff in minutes instead of hours (or never).
Look, if you’re running network security, you might as well get comfortable with your NGFW. The threats aren’t slowing down, last count showed something like 1,200 new attack variations per month. Plus, those compliance folks won’t get off your back until everything’s locked down tight.
Some advice? Keep it simple at first. Don’t go nuts with 500 different rules, and let the automated stuff handle the grunt work.
These firewalls are smart, but they’re only as good as the person setting them up. Take the time to learn the weird little quirks of your system, it’ll pay off when things go sideways. Want help streamlining your security stack and building a strategy that actually works in practice? Join us here.
NGFW policy management relies on firewall rule optimization, firewall rule cleanup, firewall rule auditing, firewall rule least privilege, and firewall rule conflict resolution. These steps streamline how rules are applied, reduce clutter, and close gaps attackers might exploit.
Threat intelligence integration lets firewalls learn from global data to spot new attacks faster. Paired with firewall incident response, firewall anomaly detection, firewall incident alerts, and firewall real-time alerts, teams can act quickly.
Automated firewall monitoring runs nonstop, catching issues before they spread. With AI-driven firewall management, firewall traffic baselining, firewall anomaly detection, and firewall traffic analysis, it gets even smarter.
Firewalls are only as strong as their maintenance. Firewall patch management, firewall firmware updates, firewall security updates, and firewall signature updates keep defenses current. These steps block known flaws before attackers exploit them.