Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Network scans might seem boring, but they catch the holes in your system before hackers do. Think of it as a digital watchdog that sniffs out weak spots 24/7, from ancient Windows updates to ports left wide open.
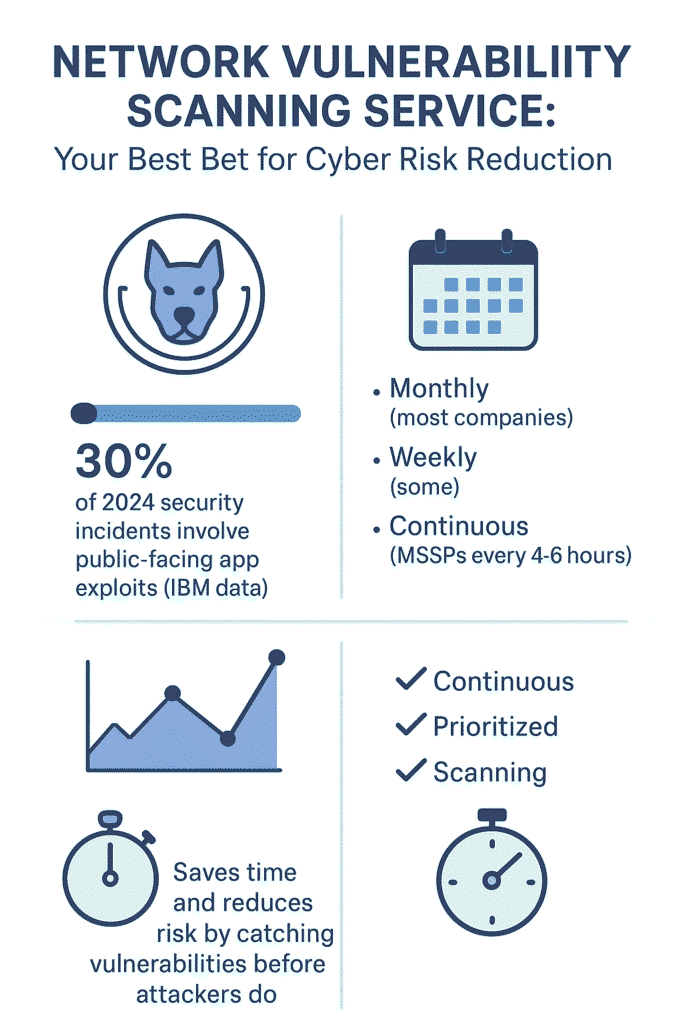
Most companies we’ve talked to run these scans monthly (some do it weekly), and it’s saved their IT folks countless hours of manual checks. Instead of playing whack a mole with security issues, these automated scans point straight to what needs fixing.
Want to know how to set this up without breaking the bank? Keep reading.
Network security isn’t just about having strong locks on the doors , it’s about knowing where those doors are in the first place. Think of vulnerability scanning as sending digital scouts through your network, checking every nook and cranny for places where bad guys might sneak in.
These tools don’t sleep, they don’t get bored, and they definitely don’t miss the small stuff that humans might overlook.
Most organizations run antivirus software and call it a day, but that’s like having a security guard who only watches the front entrance.
Network vulnerability scanning digs deeper, poking at every device on the network (from the CEO’s laptop to that ancient printer in accounting that nobody remembers ordering) to find weak spots before someone else does.
According to IBM’s “Threat Intelligence Index”, 30% of the security incidents responded to in 2024 were due to exploitation of public-facing applications (1).
Some stuff these scanners look for:
These scans aren’t just one-and-done deals , they’re constant watchdogs for your digital space.
The whole process runs like a well-oiled machine, starting with what’s basically a digital census. The scanner creates a list of everything that’s alive and kicking on your network, which often turns up surprises.
It’s not uncommon to find old servers still running in closets that everyone forgot about years ago. After taking attendance, the scanner starts mapping connections. It’s kind of like watching traffic patterns in a city, seeing which devices talk to what, when, and how often.
This builds a picture of your network’s daily life, making it easier to spot when something’s not right. Then comes the actual vulnerability check.
The scanner compares what it found against known security problems (there’s a massive database called the National Vulnerability Database that tracks these things). It’s looking for stuff like outdated software, weak passwords, or misconfigured settings that could let attackers in.
At the end, you get a report that breaks everything down. The best part? It tells you what to fix, first kind of like having a home inspector who not only finds problems but tells you which ones might burn your house down and which ones are just cosmetic.
Sure, these scanners aren’t perfect , sometimes they cry wolf, and sometimes they miss things that only a human would catch. That’s why lots of places combine scanning with actual people testing their security (penetration testing, if you want to get fancy about it).
Nobody wants to get caught with their digital pants down. That’s why vulnerability scanning, particularly when handled by a Managed Security Service Provider (MSSP), makes so much sense.
Many teams now rely on structured approaches like managed vulnerability management to keep track of issues systematically and close gaps before attackers can exploit them.
These security pros bring the kind of 24/7 watchdog mentality that’s practically impossible to maintain in-house, keeping an eye on networks that seem to change faster than the weather in New England.
MSSPs run scans non-stop (typically every 4,6 hours), catching problems before they turn into disasters. Security teams get real time alerts about threats, instead of discovering them during the next quarterly review, when it might be too late.
The scanning reports these providers generate aren’t just data dumps either, they’re practical roadmaps for fixing what’s broken.
The thing about MSSPs that really stands out is how they make sense of all the noise. In networks with thousands of endpoints, they’ll spot the three or four vulnerabilities that actually matter.
Their prioritization systems (which usually factor in CVSS scores and real world exploit likelihood) help cut through the clutter that might paralyze an in-house team.
And yeah, there’s the whole compliance thing too. Most regulations these days want proof of regular security checks, and MSSPs tie scanning right into their broader security monitoring. It’s like having a security camera that also checks the locks and tests the alarm system.

Credit : unsplash.com (Photo by Fabian Irsara)
Here’s what actually works in the real world:
The organizations that stick to this playbook? They’re the ones sleeping better at night, knowing their attack surface shrinks month after month.
The difference between scanning for vulnerabilities and running a penetration test might seem murky at first glance. Each plays its own part in the cybersecurity toolkit, and they’re definitely not interchangeable.
Think of vulnerability scanning as throwing a wide net, it’s mostly machine driven and looks for known weak spots across the network (usually running daily or weekly). Pretty straightforward stuff. Though it won’t catch everything, since it can’t think like a hacker or actually try to break in.
Pen testing gets way more hands on. Real security experts spend days or weeks trying to crack their way into the system, finding sneaky problems that automated tools miss. Most companies run these tests every 3-4 months, or once a year if they’re on a tight budget.
The smart money’s on using both, they complement each other like peanut butter and jelly. Regular scans catch the obvious stuff, while pen testers dig deep into the system’s dark corners.
The scanning tool market’s gotten pretty crowded, and picking the right one can make your head spin.
Some companies turn to external vulnerability management services when their in-house teams struggle with prioritization or interpreting results. Here’s what matters when shopping around:
Some security teams we’ve seen practically drowned in scan data until they found tools that didn’t require a decoder ring to understand. When a scanning tool clearly shows what’s broken and how to fix it, that’s when the magic happens.

Credit : unsplash.com (Photo by Tianyi Ma)
Network security teams can’t seem to shake off some basic problems, despite having fancy tools at their fingertips. These issues keep popping up in assessments, kind of like that one person who’s always late to meetings, you know it’s coming, but it still happens.
Many compromises still come from short, simple attack paths: Microsoft’s analysis found 90% of organizations are exposed to at least one attack path, and 10% of attack paths contain three steps or fewer, which means attackers often don’t need advanced techniques to reach valuable accounts or systems (2)
Even with scanning tools, certain vulnerabilities remain stubborn foes:
Security teams find these issues over and over during assessments. It’s like checking your doors are locked every night, you’ve got to keep doing it, and fix problems right away when you find them.
Network scanning isn’t just another box to check off for the compliance folks. Think of it as having a security guard who never sleeps, always watching for trouble spots.
When organizations pair up automated scanning with expert support (and actually follow through with fixes), their security gets way better.
Not scanning your network? That’s like leaving your car unlocked in a sketchy neighborhood. Regular scanning with risk-based fixes cuts down the odds of getting hit. These tools basically give you a map of where the problems are and how to fix them.
Want better network defense? Start with a full scan. Then keep track of what you find, fix it fast, and scan again. That’s how networks stay safe these days, nothing fancy just consistent work.
Network vulnerability scanning isn’t just another IT checklist item, it’s your extra set of eyes on the digital perimeter, running 24/7. These scans catch weak spots before attackers exploit them.
When companies combine automated scanning with expert support and follow a consistent security plan, their defenses become significantly stronger.
On the flip side, skipping scans (or running them sporadically) is like leaving your front door unlocked in a risky neighborhood, you’re inviting trouble.
Regular scans, paired with prioritizing and fixing the riskiest issues first, drastically reduce the chance of becoming the next breach headline. These tools essentially hand you a map of your vulnerabilities and tell you exactly where to reinforce your defenses.
But the right tools alone aren’t enough. That’s where expert consulting comes in. We help MSSPs streamline operations, reduce tool sprawl, and strengthen service quality.
With 15+ years of experience and 48K+ projects delivered, we provide vendor-neutral guidance, stack optimization, and clear recommendations, so your tech stack aligns with business goals, integrates smoothly, and delivers stronger security outcomes.
If you’re serious about protecting your network, set up a proper scanning service, backed by the right expertise. Find the holes, patch them, and keep scanning, again and again. Get started with expert vulnerability scanning and consulting support here.
Network vulnerability scanning looks for weak spots in devices, apps, and systems, while network security scanning takes a broader look at overall defenses. Both rely on vulnerability detection, but vulnerability scanning tools often dig deeper into technical flaws.
A vulnerability scanner is the engine behind most vulnerability scanning tools. These tools check systems for known flaws using a vulnerability database. A vulnerability scanning service automates the process and produces a network vulnerability report.
Automated vulnerability scanning allows organizations to run checks regularly without extra manual effort. Continuous vulnerability scanning improves security by spotting new risks quickly. Paired with vulnerability reporting automation, results become easier to digest and share.
Penetration testing is a simulated attack that shows how real hackers might exploit weaknesses. Network penetration testing zooms in on specific network assets, while a broader network penetration assessment often includes network infrastructure scanning and network security monitoring.