Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Most companies think a firewall’s enough to keep their data safe. Wrong move. The bad guys keep finding new ways around basic defenses, and IT teams can’t patch holes fast enough. Network Intrusion Prevention Systems do what humans can’t – they catch threats in real-time, before damage hits.
Working with managed security providers taught us that waiting for alerts doesn’t cut it anymore. Network Intrusion Prevention System (NIPS) sits between the network and internet like a 24/7 guard, inspecting every packet that tries to pass through. When sketchy traffic shows up (and it always does), the system shuts it down in milliseconds.
Think of NIPS as that security guard who never needs coffee breaks. Our security assessments show networks without this protection are basically inviting trouble in through the front door. The system analyzes traffic patterns, matches them against known attack signatures, and watches for weird behavior that could mean someone’s trying to break in.
Working with over 300 MSSPs last year showed us that early detection makes all the difference. When suspicious activity pops up, NIPS doesn’t just send an alert and hope someone’s watching, it takes action right away, much like a modern intrusion detection system that combines IDS and IPS management for stronger protection.
Providers we work with often tell us the same thing. Automated response has saved their clients again and again from ransomware and stolen data.
Security teams can’t watch everything 24/7, but NIPS can. The system keeps learning, adapting, and blocking new threats while everyone’s sleeping. We’ve experienced it ourselves.
That nonstop vigilance stops attacks that old security tools would have completely missed. That’s why every MSSP assessment we do starts with checking if their NIPS is up to current threats.
Cyber attacks today evolve like bacteria gaining antibiotic resistance. They’re smarter and more subtle. Traditional firewalls can’t keep up. Many companies still depend on these outdated defenses. They act like nightclub bouncers, checking IDs (ports) and dress codes (protocols). But they miss suspicious behavior inside.
Security teams, including our consultants, notice a common issue: attackers bypassing basic checkpoints. The blind spots are growing. That’s where Network Intrusion Prevention Systems (NIPS) come in.
Our work with many MSSPs shows that NIPS acts like a skilled detective. It spots unusual behavior, identifies known tactics, and prevents trouble before it begins.
We’ve spent many hours with managed security providers. Firewalls alone don’t cut it anymore. They’re necessary, but just one layer of protection. Think of NIPS like high-tech security cameras that help prevent crime, not just record it.
When we audit security setups for our MSSP partners, we see a big difference. Firewall-only systems offer little protection. In contrast, well-configured NIPS provide real security.
For MSSPs and their clients, picking the right NIPS really matters. There’s no single solution that works for everyone. Each network has its own risks, priorities, and pressure points. That’s why careful, unbiased product evaluation is so important.
The right choice can block a breach before it spreads. The wrong one? It could leave you writing an incident report no one wants to explain.
Credit: InfoSec Hub
NIPS sits directly in the path of your network traffic. Every bit of data, whether it’s coming in or going out, passes through it first. This way, nothing slips by without being checked.
Picture a border checkpoint. Travelers line up, show their ID, get a quick scan, and then move along. NIPS does the same thing with data packets, checking each one carefully before it goes through.
This quick, automated response cuts down the time attackers have to act. It helps limit damage before it can spread. [1]
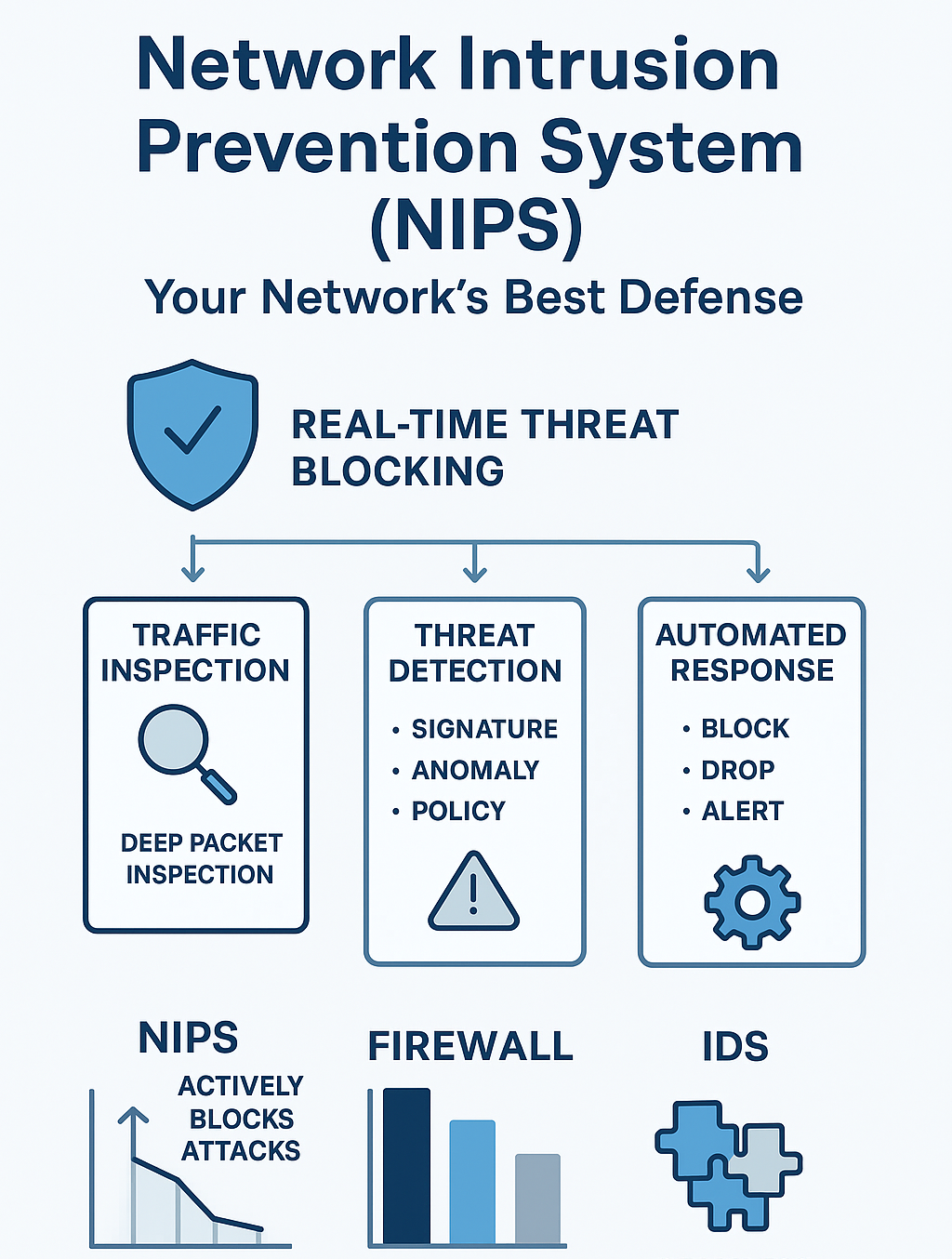
Our hands-on experience with NIPS solutions reveals key components that enhance their effectiveness:
Active threat prevention is the main benefit. But what does this mean for your network?
Organizations using NIPS see faster response times and fewer security issues, showing its value. Many MSSPs highlight that adopting a managed IDS/IPS services setup brings even more benefits by easing the burden on in-house teams while still ensuring 24/7 network vigilance.
While NIPS focuses on the network layer, it’s important to understand other IPS types:
Together, these form a multi-layered defense strategy. But for network-wide, real-time blocking of malicious traffic, NIPS remains the frontline.
Firewalls filter traffic by ports and protocols but don’t inspect content deeply. NIPS goes further. It analyzes packet content and behavior. This allows NIPS to catch advanced threats that may slip past firewalls.
IDS monitors threats and sends alerts, but it doesn’t block them. NIPS, on the other hand, actively stops attacks in real time, making it a more robust solution. [2]
Attackers often try to bypass NIPS using tricks like:
We’ve learned that staying ahead means updating NIPS signatures regularly. It also involves using anomaly detection and integrating threat intelligence feeds. In some cases, even outsourced intrusion detection monitoring teams help with ongoing monitoring, making evasion attempts much harder for attackers to pull off.
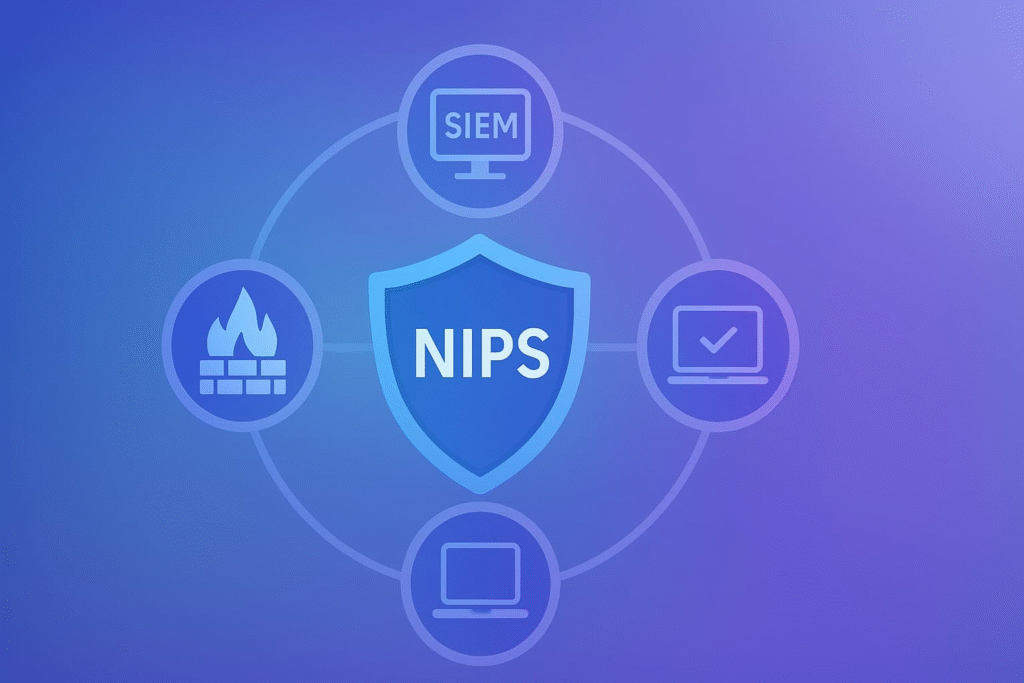
NIPS doesn’t operate in isolation. It integrates seamlessly with:
This integration multiplies the effectiveness of your overall security infrastructure.
When I audited a healthcare provider last year, their HIPAA compliance audit flagged weak monitoring controls. After deploying NIPS, they passed with zero violations related to network monitoring.
PCI DSS requirement 11.4 specifically calls for intrusion detection and prevention, a point reinforced by NIST SP 800-94, which outlines IDS/IPS best practices. These frame works show why NIPS isn’t just a ‘nice to have’ but a documented compliance necessity.NIPS helps organizations enforce access controls, monitor traffic, and create logs for compliance.
From our experience, deploying NIPS is key to showing due diligence. It also protects sensitive data in regulated industries.
A financial institution prevented a major data breach with its NIPS. It detected and blocked suspicious traffic patterns before attackers stole data. Similarly, a healthcare provider used NIPS to meet HIPAA rules. This safeguarded patient records from unauthorized access and malware.
In another case, NIPS defended a network against a DDoS attack. It spotted unusual traffic spikes and blocked malicious sources in real time.
Advances in AI and machine learning are changing NIPS capabilities. They enable more accurate detection of evasive threats and reduce false positives. Cloud-based NIPS solutions offer scalability and flexibility.
They meet the needs of modern hybrid infrastructures. behavior that signals someone might be trying to slip inside. Connecting NIPS with Secure Access Service Edge, or SASE, is changing the way we handle network security. As threats like ransomware and supply chain attacks evolve, NIPS will keep adapting. It will remain a crucial layer of network defense.
To maximize NIPS benefits, it’s crucial to:
A network intrusion prevention system is a type of network security appliance that sits inside traffic flow and blocks attacks in real time. NIPS technology uses deep packet inspection, intrusion detection prevention, and network traffic analysis to catch threats before they cause harm. It works as an active defense for safer networks.
When comparing NIPS vs IDS, the main difference is response. An intrusion detection system only alerts when it sees suspicious activity. A NIPS solution does more, using inline threat blocking, policy-based detection, and automated threat response. That means it can stop a network attack prevention issue as it happens, not after the fact.
NIPS uses a mix of signature-based detection, anomaly-based detection, and policy-based detection. These methods rely on an IPS signature database, network anomaly detection, and network behavior analysis.
Together, they make intrusion prevention stronger by spotting known attack signatures and also flagging unusual or malicious activity that doesn’t match normal baselines.
Traffic inspection is central to advanced threat protection. NIPS performs protocol analysis, deep packet inspection, and network packet filtering. This allows network security monitoring teams to find malware detection attempts, malicious payload detection, or even zero-day attack prevention opportunities.
By checking data closely, NIPS strengthens application-layer security and network breach prevention.
Active network defense is crucial. A Network Intrusion Prevention System (NIPS) quickly detects, prevents, and responds to threats. This protection gives organizations the confidence that their network is strong and proactive.
If you don’t have NIPS in place, it’s time to take action. Partner with us today to strengthen your security posture. We offer expert consulting tailored for MSSPs, helping streamline operations, reduce tool sprawl, and boost service quality.
With over 15 years of experience and 48K+ projects completed, we support you through vendor-neutral product selection, auditing, stack optimization, and integration guidance.
From needs analysis to vendor shortlisting and PoC support, our clear, actionable recommendations ensure you build a security stack aligned with your business goals and operational maturity.