Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Not all cybersecurity protection is the same. For years, traditional antivirus software has been the go-to defense, blocking known malware with signature-based detection. But cyber threats have grown far more advanced, and old antivirus tools can’t keep up.
That’s where Managed Detection and Response (MDR) comes in. MDR uses smarter detection methods, real experts watching around the clock, and active responses to stop attacks as they happen.
This article explains how MDR and traditional antivirus stack up in threat coverage, detection, response, and more, so organizations can make smarter choices about security.
The old guard of antivirus software still lurks in many computers, faithfully checking files against its database of known threats. Like a security guard with a most wanted list, it’s good at catching the usual suspects but pretty much useless when something new comes along.
MDR’s got a different trick up its sleeve. Instead of just matching fingerprints, it’s watching for weird behavior , like when someone’s moving through networks they shouldn’t be in, or when perfectly legit programs start acting sketchy.
Zero day attacks, fileless malware that doesn’t leave typical traces, even trusted employees gone rogue , MDR catches what traditional antivirus doesn’t even know to look for.
Beyond catching threats, MDR delivers active defense, 24×7 monitoring, human-led threat hunting, and rapid response like device isolation and token revocation. That’s a far cry from AV’s passive alerts that leave IT scrambling after the fact (1)
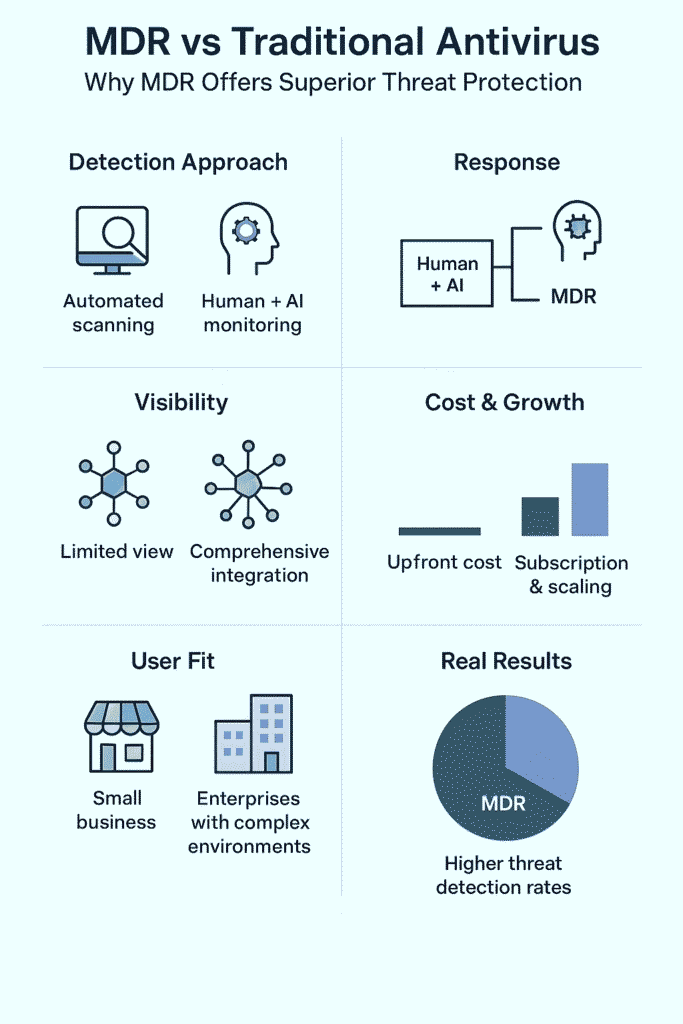
Core Differences in What They Catch:
Traditional antivirus is kind of like a bouncer checking IDs against a list. It’s scanning files, looking for matches to know bad stuff, maybe doing some basic behavior checks. But it’s always playing catchup, waiting for something bad to happen before it knows what to look for.
MDR’s more like having a whole security team watching everything , computers, networks, cloud stuff , all at once. There’s AI watching patterns (fancy machine learning stuff), plus real humans in security operations centers who’re actually hunting for threats.
They’re not just waiting around , they’re actively looking for trouble. Signature-based methods are inherently limited; some sources estimate about 33% of malware goes undetected by antivirus software because it’s unknown or altered in ways that evade signature matching (2).
Here’s where it gets interesting. Traditional antivirus just blocks the file and sends an alert , that’s it. Maybe send an email to IT. Really helpful, right?
MDR actually does something about it. When it spots trouble, there’s a whole team ready to jump in. They’ll check if it’s real (no more crying wolf), stop the attack from spreading, and actually fix the problem. Sometimes they lock down computers, shut off hacked accounts, or even undo the changes attackers made.
How They Handle Alerts:

Credit: pexels.com (Photo by Lukas)
Security teams can’t depend on it and forget it antivirus software anymore. Regular antivirus runs in the background, flooding IT staff with alerts while tricky threats slip by.
MDR works differently. It has real people, security analysts who watch networks around the clock. They look for strange activity and step in when something isn’t right. Automated tools can miss things, but a trained human eye often catches them right away.
a clear edge tied to the broader understanding of different MDR service levels that define how teams respond.
Old school antivirus is pretty simple, you install it on computers and servers, and it scans for viruses. That’s about it. Can’t see what’s happening on networks or in the cloud, which is kind of a problem these days.
MDR’s more flexible, working from the cloud or mixing cloud and local setups. It watches everything , computers, servers, networks, cloud stuff, all at once. When something suspicious happens across different systems, MDR connects the dots.
Look, antivirus is cheaper, that’s just facts. Small companies and regular folks like that. MDR costs more (usually between $15,25 per endpoint monthly), but you’re paying for actual experts and better protection. When you think about how much a breach costs (averaging $4.35 million in 2022), MDR starts looking pretty reasonable.
MDR grows with companies pretty well, especially ones using lots of cloud stuff. That’s why the long-term benefits are often greater than just saving money upfront.
Regular antivirus? Not so much. It’s stuck in the endpoint world, which isn’t great for bigger operations.
Most mom, pop shops and regular folks do just fine with traditional antivirus, they’re not exactly cyber attack magnets. Quick installation, basic protection, done. But bigger companies, especially those dealing with sensitive data or strict regulations?
That’s where MDR comes in. They can’t afford to mess around with security, and they’ve probably got cybercriminals actually targeting them (not just random malware).
Target Audience Breakdown:
There’s a lot of confusion between MDR and EDR, and it’s easy to see why. EDR’s like having a really smart security camera system for your computers , it watches for weird behavior but doesn’t do much else.
MDR takes that tech and adds actual humans who watch everything 24/7 and jump in when something’s wrong. Old school antivirus just sits there checking for known bad stuff, kind of like a guard dog that only knows a few tricks.
What Each One Does:
Companies using MDR don’t just get warnings about problems , they get solutions. When something sketchy happens, the MDR team figures out exactly what went wrong, how it happened, and makes sure it gets fixed right away.
This active managed detection & response approach ensures organizations aren’t left on their own after an alert.
Traditional antivirus only sends a warning and then leaves you to deal with it. That often means the problem sticks around much longer than it should.
What You Actually Get:
From above, MDR platforms can watch almost everything, your computers, networks, cloud systems, and even long system logs. It’s like having eyes all over your IT setup, which really helps when sneaky attacks try to jump between different systems.
Old school antivirus? That’s just watching one computer at a time. Kind of like trying to guard a house by only watching the front door.
MDR covers:
Traditional Antivirus only covers:
Look, picking between MDR and regular antivirus isn’t rocket science , it’s about what you need. If you’re dealing with sensitive data, worried about compliance, or just can’t afford to get hacked, MDR’s probably your best bet.
But if you’re running a small operation without much IT stuff to worry about, regular antivirus might do just fine. The thing about staying ahead of cyber threats is that they don’t sit still. MDR keeps learning and adapting (thanks to some pretty clever AI and security experts working behind the scenes).
Regular antivirus? It’s still playing catch up, waiting for the next update to tell it what’s dangerous.
First off, take a good hard look at what you’re trying to protect. Talk to some security providers (the ones offering MDR), and see how they’d fit with what you’ve already got. Don’t throw out your antivirus just yet , layering security still makes sense.
The whole cybersecurity thing isn’t getting any simpler, that’s for sure. But whether you go with MDR or stick with antivirus, at least now you know what you’re getting into. Just remember: the fanciest security in the world won’t help if nobody’s watching it.
The old standby antivirus software works fine for your average home user or mom-and-pop shop,it’s like having a basic burglar alarm. But against today’s craftier cybercriminals, it’s showing its age. Traditional programs rely on scanning for known threats, which means new and more sophisticated attacks often slip right through.
MDR brings more muscle to the fight. With real security experts monitoring networks around the clock, spotting unusual behavior before it escalates, and stepping in to contain and fix issues in real time, MDR is like having an entire security team on call,not just a motion detector.
For companies handling sensitive customer information, working under strict compliance rules, or being directly targeted by skilled attackers, MDR may come at a higher cost, but the protection it delivers is well worth it. The threats aren’t getting any simpler, and basic protection just doesn’t cut it anymore.
Explore our expert consulting services for MSSPs and take your cybersecurity strategy to the next level. With over 15 years of experience and 48K+ projects completed, we help streamline operations, optimize tool stacks, and ensure your defenses keep pace with modern threats.
Cybersecurity operations bring together continuous monitoring, cybersecurity monitoring tools, and security analytics to spot threats faster. Unlike antivirus software features that focus on malware scanning, cybersecurity operations combine security automation, threat containment strategies, and real-time monitoring.
Cybersecurity frameworks and IT security policies shape cybersecurity management and guide IT security tools. They support cyber risk management, cybersecurity services, and cyber hygiene practices that go beyond malware prevention.
Security incident management covers the full process of dealing with malware variants, threat identification, and cyber incident management. Data breach response is one part, focused only on containing damage once sensitive data is exposed.
A skilled cybersecurity workforce boosts cybersecurity awareness, improves use of malware analysis, and supports intrusion detection system tools. By following cybersecurity best practices and learning from malware trends, staff strengthen malware defense systems and cyber hygiene.