Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Threat hunting improves security by catching threats that hide quietly instead of waiting for alerts that may never fire. Many teams are finally shifting to this approach because attackers often sit in networks for months, staying just below the noise. That gap creates risk nobody sees, and that’s where the real damage builds.
At MSSP Security, we’ve seen how proactive hunting exposes silent movement, strange access, and weak points that tools alone miss. This guide breaks down why it works, how to do it well, and what to expect.
Keep reading if you want improve security with threat hunting today.

We kept seeing the same quiet pattern repeat itself. Threats weren’t noisy malware popping up on screens, they were patient intruders sitting inside networks for months, moving sideways, touching sensitive systems, and staying just under the radar.
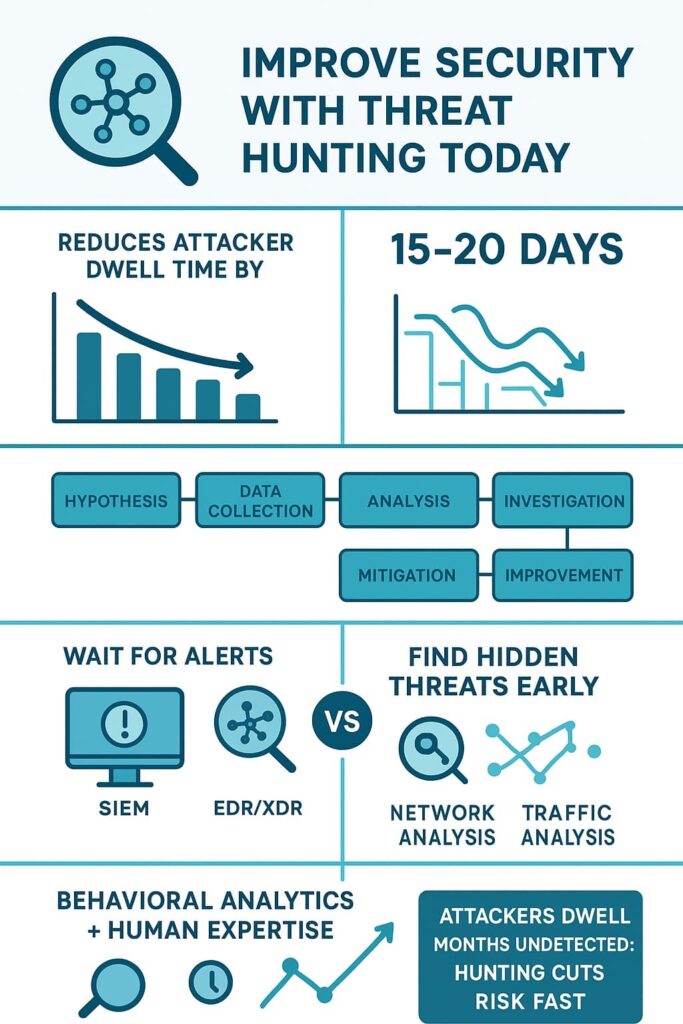
Most detection timelines still hover around 200 days, which is a long time for an attacker to learn a network better than the people who run it.
Most tools still try to guard the front door. Firewalls, email filters, endpoint agents, they all do solid perimeter work, but determined actors don’t always come charging in, they slip through the cracks and blend into normal traffic.
That’s where traditional setups break down, and why sharpening visibility with proactive security monitoring becomes essential for catching subtle movements early.
In our incident response and product audit work with MSSPs, we’ve watched well-funded environments, with impressive-looking stacks, miss attacks that had been active for weeks. The tech wasn’t useless, it just wasn’t the whole answer. The shared problem was mindset: teams were waiting for alerts to light up instead of assuming compromise and going hunting.
So the strongest programs we see now pair automated detection with human-led hunting. Tools flag known patterns and obvious abuse, while analysts test hypotheses, follow odd behaviors, and challenge what the dashboards “say” is fine.
When we help MSSPs select and review products, this blend, machine speed plus human curiosity, is one of the first criteria we check for.
Money-wise, the case is blunt. Breaches cost millions in direct losses, clean-up, and lost business, and that’s before regulators get involved. When hunting finds intruders early, they’re boxed in before they spread, encrypt, or leak at scale.
It’s less like watching a door camera, and more like having trained staff walking the halls, checking every wing, every shift, every day. [1]
Credits: InfraSOS
We use the term “threat hunting” a lot in reviews and workshops, but it’s easy to confuse it with incident response or classic forensics.
At its core, hunting means systematically combing through an environment, looking for signs of malicious activity that hasn’t triggered an alarm yet. Incident response waits for a known problem. Hunting assumes the problem is already there and just hasn’t been noticed.
From what we’ve seen across MSSPs and their clients, the mindset shift is the real separator.
Hunters don’t start by asking, “Are we breached?” They start with, “If someone was in here, where would they hide, and what would that look like in the data?” That assumption changes how tools are chosen, how logs are kept, and how analysts spend their time.
Most serious hunting programs, and most products we recommend to MSSPs, follow some version of a structured cycle, especially when paired with expert hunter support that strengthens the accuracy of each pass through data:
When this becomes a habit, not a one-off exercise, the organization starts to change. We’ve watched teams that document hunts carefully grow very sharp about what “normal” really looks like in their networks.
Over time, odd patterns jump out faster, tools get tuned better, and MSSPs can judge products not just on features, but on how well they support that ongoing hunt-and-learn cycle.
Hunting catches what automated tools miss. We’ve identified threats that had been present for months but never triggered alerts. By finding these early, you contain damage before attackers achieve their objectives.
The time between intrusion and detection drops dramatically, sometimes from 200 days to just 48 hours. This reduction in dwell time directly limits data loss and system compromise.
Regular hunting uncovers vulnerabilities you didn’t know existed. It might be misconfigured servers, weak access controls, or unpatched software. Each finding represents an opportunity to strengthen your defenses.
Over time, this continuous improvement hardens your entire environment. We’ve seen hunting programs evolve into comprehensive security optimization initiatives.
Hunting provides real-world feedback for your security tools. When you find attacks that evaded detection, you can tune your systems to catch similar attempts in the future. This refinement reduces false positives and makes your automated alerts more accurate.
The result is a security operations center that focuses on genuine threats instead of chasing noise.
Structured hunting uses known indicators and patterns. You might search for specific malware signatures or attacker techniques documented in threat intelligence feeds. This method is great for catching common threats but requires current intelligence to be effective.
Hypothesis-driven hunting starts with educated guesses. Based on your organization’s profile, you might hypothesize that attackers would target financial data or customer records. Then you hunt for evidence supporting that theory. This approach works well for targeted threats specific to your industry.
Intel-driven hunting combines both approaches. You use external intelligence about active threat groups, then formulate hypotheses about how they might attack your environment. This method requires good threat feeds but catches sophisticated attacks early.
We typically recommend starting with structured hunting to build confidence, then progressing to more advanced techniques. The key is consistency, regular hunting sessions yield better results than occasional efforts.
Building an effective hunting program requires planning. You need the right tools, data sources, and skilled personnel. Many organizations struggle with the last component, and this is where proactive managed hunting can help close the gap by adding seasoned eyes that actively look for hidden intrusions.
That’s where specialized security providers add value. An MSSP with hunting capabilities brings expertise you might not have in-house. They’ve seen attacks across multiple environments and know what to look for. This external perspective often spots threats internal teams miss.
The implementation process typically involves:
We’ve helped organizations stand up hunting programs in weeks rather than months. The acceleration comes from proven methodologies and existing tool integrations. The goal is sustainable hunting that becomes part of your security culture.

You need visibility across your environment to hunt effectively. This means collecting data from endpoints, networks, cloud services, and applications. The specific tools matter less than their integration and the quality of data they provide.
Security information and event management systems aggregate logs from multiple sources. They provide the centralized data repository hunters need. Look for systems with strong search capabilities and flexible data retention.
Endpoint detection and response tools provide deep visibility into workstation and server activity. They record process creation, network connections, and file modifications. This granular data is essential for investigating suspicious behavior.
Network traffic analysis tools monitor communication patterns. They help identify command-and-control channels and data exfiltration attempts. When combined with endpoint data, they provide complete attack visibility.
The best toolset depends on your environment and budget. We’ve seen effective hunting with various technology combinations. The common factor is always comprehensive data collection and skilled analysis. [2]
Threat hunting transforms security from reactive to proactive. It’s the difference between waiting for alarms and actively patrolling your digital premises. The benefits extend beyond threat detection to overall security improvement.
Starting doesn’t require massive investment. Begin with what you have, your existing security tools likely provide enough data for initial hunts. Focus on your most critical assets first, then expand coverage as you gain experience.
Consider partnering with experts if internal resources are limited. The important thing is starting somewhere. Even basic hunting provides insights that improve your security posture. The goal is continuous improvement, not perfection from day one.
Your security deserves more than automated alerts. It deserves human intuition backed by data and experience. That’s what threat hunting delivers, the ability to find threats others miss. The question isn’t whether you can afford to hunt, but whether you can afford not to.
Threat hunting can help even a small team. It uses proactive threat detection, behavioral analytics, and anomaly detection to spot problems early. You can work with managed threat hunting or follow simple hunting methodologies. By using clear hunting workflows and basic hunting tools, you can find issues before they spread and reduce risk.
You may need SOC threat hunting when alerts pile up, you worry about insider threat detection, or you face advanced persistent threats. If you struggle with threat detection in your daily work, using EDR, XDR, and simple hunting processes can help you see hidden behavior and respond faster.
It depends on your needs. Hunting analytics helps when you want clear patterns from hunting telemetry, hunting rules, or IOC hunting. Hunting automation helps when you get too many hunting alerts or must speed up the hunting lifecycle. Many teams start small, then mix both tools as they grow.
Look at hunting network traffic, endpoint detection and response logs, and simple hunting data sources. Watch for hunting command and control activity, odd login times, or unknown files. These clues help you detect APT detection issues early. This approach gives you better hunting investigation results and stronger incident response.
Threat hunting strengthens security by cutting dwell time, improving visibility, and boosting incident response.
It combines human expertise, behavioral analytics, and proactive techniques to uncover threats before they escalate. At MSSP Security, we’ve seen how early detection and smarter insights help organizations stay ahead of attackers and build stronger resilience.
If you want to enhance your operations, streamline tools, and elevate service quality, we’re here to help. Join us to improve your security with expert guidance. With 15+ years of experience, we deliver clear, actionable, vendor-neutral recommendations.