Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Identity governance administration (IGA) support manages user identities, access rights, and governance controls across systems to reduce risk, maintain compliance, and automate the access lifecycle. As organizations expand into cloud services and hybrid environments, identity misuse now drives a large share of security incidents.
Fragmented access models quietly raise exposure quarter after quarter, often without clear visibility. We have seen this firsthand while supporting teams under audit pressure, rapid hiring, and constant role changes. IGA support introduces structure where identity sprawl usually grows unchecked, aligning access with policy and business intent. Keep reading to see how it works, why it matters, and how to adopt it without disruption.
Identity governance administration (IGA) support is about control, not just access. It manages user identities, access rights, and governance rules across every system an MSSP and its clients rely on. Done right, it reduces risk, supports compliance, and makes access lifecycle management something you can trust, not just hope is working.
In practice, IGA combines two worlds:
We’ve sat with MSSP teams that onboard new users smoothly, only to realize months later that offboarding is broken. Former analysts still have console access. Old service accounts still sit open in client tenants. No one set out to be careless. The gaps were built over time.
That’s why identity misuse sits behind most breaches. Verizon’s analyzed 30,458 security incidents and 10,626 confirmed breaches, showing how easy identity-focused attack vectors still are for adversaries [1]. That shift is what moved IGA from a “nice-to-have” checkbox to a core part of security architecture, especially for MSSPs responsible for multiple client environments.
Some core capabilities that IGA support usually includes:
In short, IGA becomes the control plane for identity. Access starts matching business and security intent, not just a long trail of past decisions.
We see this pattern a lot: the MSSP has strong IAM, but weak IGA. Logins are secure, but entitlements are out of control. Many of the core advantages MSSP services deliver start to break down when identity decisions are enforced but never governed across environments.
Identity and access management (IAM) mainly answers:
“Can this user log in?”
Identity governance administration (IGA) answers:
“Should this user still have this access at all?”
We’ve watched MSSPs roll out SSO and MFA across multiple client environments and still fail audits, because no one can explain who approved which role, or why a junior tech has admin rights in a critical app. IAM enforces access. IGA governs it.
Research cited by Okta shows that organizations using governance automation can cut audit prep time by up to 50%. That reduction matters even more when you’re an MSSP handling audits across several clients at once.
Here’s a simple breakdown:
| Aspect | IAM | IGA Support |
| Primary focus | Authentication | Governance and compliance |
| Core functions | SSO, MFA | Access reviews, SoD, lifecycle control |
| Automation scope | Login flows | Provisioning and deprovisioning |
| Compliance depth | Moderate | High, structured, and auditable |
We don’t position IGA as a replacement for IAM. It completes it, especially for MSSPs that live under constant compliance, client, and regulatory pressure.

When we evaluate IGA products for MSSPs, we usually look at four main pillars. These pillars are where we see the biggest impact across multiple client environments.
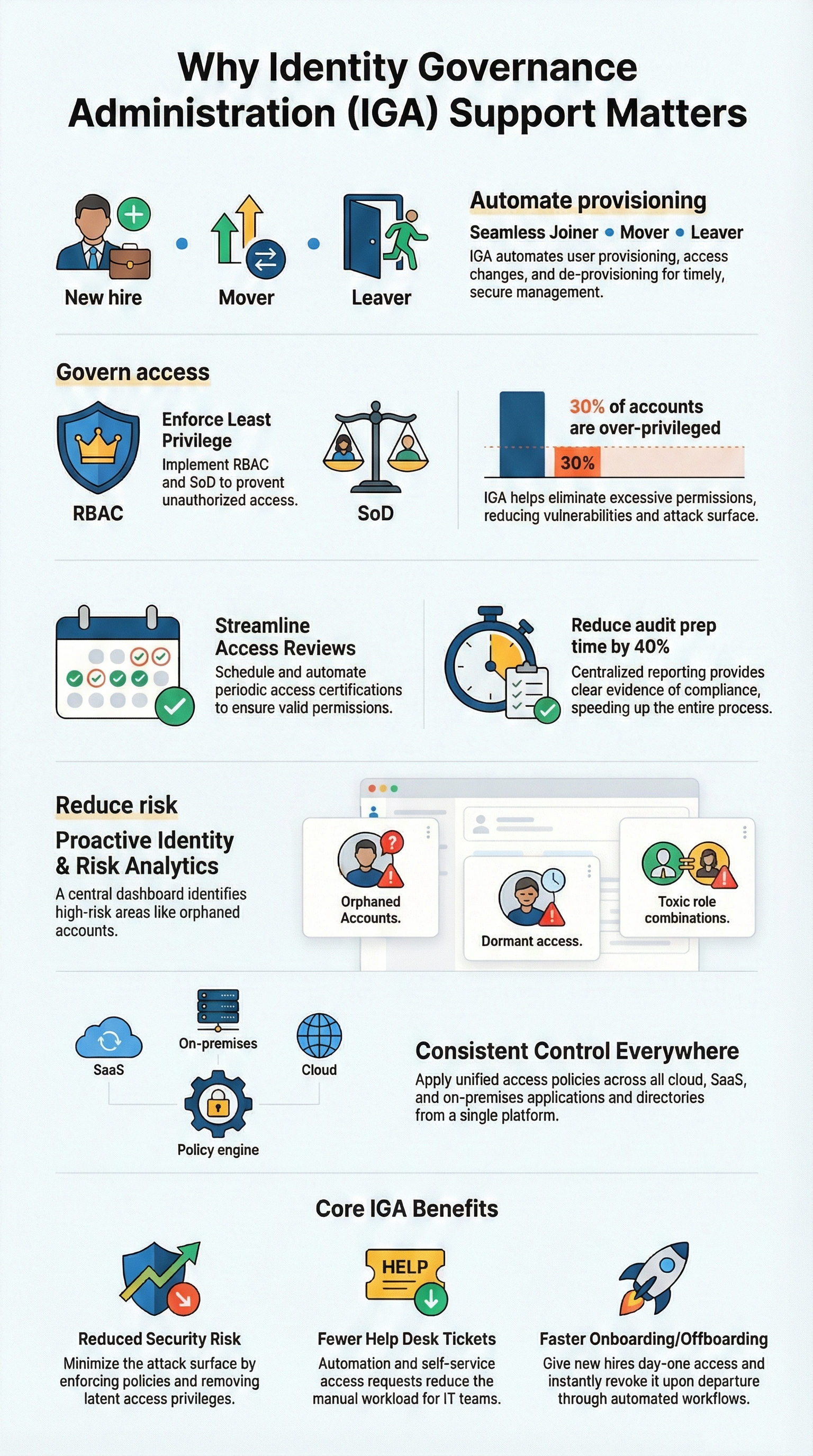
A lot of risk hides in the joiner-mover-leaver process. We’ve watched MSSPs struggle when a departing engineer still has admin access to a client’s cloud environment or when a contractor keeps permissions long after the project ends.
Good lifecycle management:
Access governance takes the guesswork out of “who gets what.” For MSSPs, this covers both internal staff and client-facing operations.
Key controls here:
In real environments, we routinely see that about 30% of accounts are over-privileged, a number echoed in many enterprise identity assessments from vendors like Oracle. MSSPs feel this problem amplified, because they operate across multiple clients and tools.
We’ve walked into audits where managers swear they review access, but everything lives in spreadsheets or old emails. That doesn’t usually survive real scrutiny.
With structured IGA:
Then there’s the quiet part: orphaned accounts, dormant access, risky combinations of roles. These are hard to spot manually, especially across many clients.
Analytics in IGA helps surface:
Identity management shifts from reactive cleanup to proactive control. And for MSSPs, that means fewer surprises during client incidents or audits.
Credits: Value Aligners
We see the same pressure points over and over with MSSPs: client audits, regulatory requirements, and constant fear of becoming the weak link in someone else’s security chain.
IGA support directly addresses those realities:
It is aligned with NIST research, that explicitly emphasizes least privilege, separation of duties, and continuous access review as foundational controls for modern systems [2].
Regulators now want proof, not promises. They ask who approved a specific admin role, when it was last reviewed, and what happened when a violation was found. With GDPR, SOX, HIPAA, PCI DSS, and client contracts tightening, that level of detail isn’t optional anymore.
GDPR fines alone reached over €2.1 billion in 2023, according to the European Data Protection Board. Even when MSSPs aren’t the regulated entity, they’re deeply involved in how identity controls are implemented.
Common outcomes we work toward with MSSPs include:
In many of the environments we support, adding yet another tool doesn’t help as much as tightening governance around the tools that already exist.

There’s another side to all this: operations. Manual access management doesn’t just create risk, it burns time. This is where managed IAM support services often become essential for MSSPs balancing client demands with limited internal capacity.
We see this play out in very familiar ways:
With solid IGA in place:
Microsoft’s research suggests that mature automation can cut manual access reviews by up to 80%. For an MSSP, that kind of reduction means teams can focus more on monitoring, incident response, and client strategy rather than chasing permissions.
Typical efficiency gains include:
Those aren’t side benefits. They’re part of why we recommend certain products and reject others when we help MSSPs evaluate IGA platforms.
Most MSSPs now live in hybrid identity by default. They support:
Forecasts cited by Amazon Web Services show that over 90% of enterprises operate in hybrid IT environments. When you multiply that by the number of clients an MSSP manages. Access sprawl becomes almost guaranteed without centralized governance.
We’ve worked with MSSPs that had strong control in one layer, like Active Directory, but almost no consistent view across SaaS or cloud resources. IGA helps fix that by:
For MSSPs building or supporting zero trust approaches, IGA isn’t a side feature. It’s what keeps identity-based control grounded, traceable, and consistent.
When an MSSP goes into an audit, whether it’s for its own operations or alongside a client. Two problems cause the most pain: scattered evidence and manual processes.
We’ve been in rooms where teams scramble to pull:
IGA platforms simplify that by:
Organizations working with ISO frameworks often report cutting audit cycles by around 40% once governance is automated. MSSPs feel this doubly, because they repeat audits across several clients and standards.
Key audit-support features we look for when evaluating products:
With that in place, “audit-ready” stops being a major project. It becomes normal operating mode.
The IGA market is growing quickly. Forecasts cited by Gartner put it on track to reach around $9 billion by 2027. New platforms, features, and promises appear constantly, and MSSPs get pulled into all of it, often with limited time to evaluate what actually works.
Our role is pretty direct:
Our role is pretty direct. We help MSSPs assess IGA platforms against real operational needs, audit existing deployments, and design governance models that survive audits and incidents. This work builds on broader Identity Access Management (IAM) support efforts, ensuring governance and enforcement stay aligned as environments scale.
From our side, the technology matters, but the operating model matters more. We’ve seen brilliant tools fail because no one defined ownership, review frequency, or clear policies. We’ve also seen “simple” tools perform well when paired with strong governance and consistent use.
We position ourselves beside the MSSP, not the vendor. That means:
When MSSPs ask how to “start” with IGA, we usually steer them away from big-bang projects. The strongest programs grow in stages.
A phased approach usually looks like this:
From our experience, MSSPs that treat IGA as an ongoing discipline, not a single project, end up with smoother audits, calmer incident response, and fewer late-night surprises.
IGA support brings identity governance and identity administration together in one system. It controls access using clear roles, access rules, and the principle of least privilege, so users only get what they need. By syncing with directory services, it removes unused accounts and keeps access accurate as systems and users change.
IGA support manages the full user lifecycle, often called joiner-mover-leaver (JML) processes. It automates user provisioning, role updates, and user deprovisioning during onboarding and offboarding. Automated provisioning helps by removing unused accounts, reducing access errors, and making sure people only have the permissions they need for their current job.
IGA support helps audits by automating access reviews, access certification, and audit trails. It supports compliance reporting for frameworks like GDPR, SOX, HIPAA, and PCI DSS. Clear records show who has access, why it was granted, and when it was reviewed, reducing manual work during audit cycles.
Yes. IGA support uses identity analytics and risk analytics to spot risky access patterns. It helps find toxic combinations, excessive privileges, and inactive accounts. By watching privileged accounts closely and managing access risks. Organizations can stop insider threats early and reduce harm when identities are misused.
IGA support works with privilege access management (PAM) by controlling who can request and keep elevated access. It supports zero trust by making sure users get only the access they need. Only when they need it, with approvals and regular reviews to prevent misuse. This approach reduces standing privileges and improves visibility into sensitive systems.
Identity governance administration support is no longer optional. It underpins security, compliance, and operational resilience. When identity becomes the control plane, teams reduce breach risk, simplify audits, and move faster without losing control.
We’ve seen structured IGA support turn fragmented access into defensible governance without disrupting daily operations. The next step is not adding more tools, but governing identity with intent. Work with MSSP Security to strengthen your IGA strategy