Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Threat hunting works by using a person’s steady eye alongside tools that pull out quiet signals from wide logs and short bursts of network traffic, and we keep noticing how a small shift in timing can change the whole search.
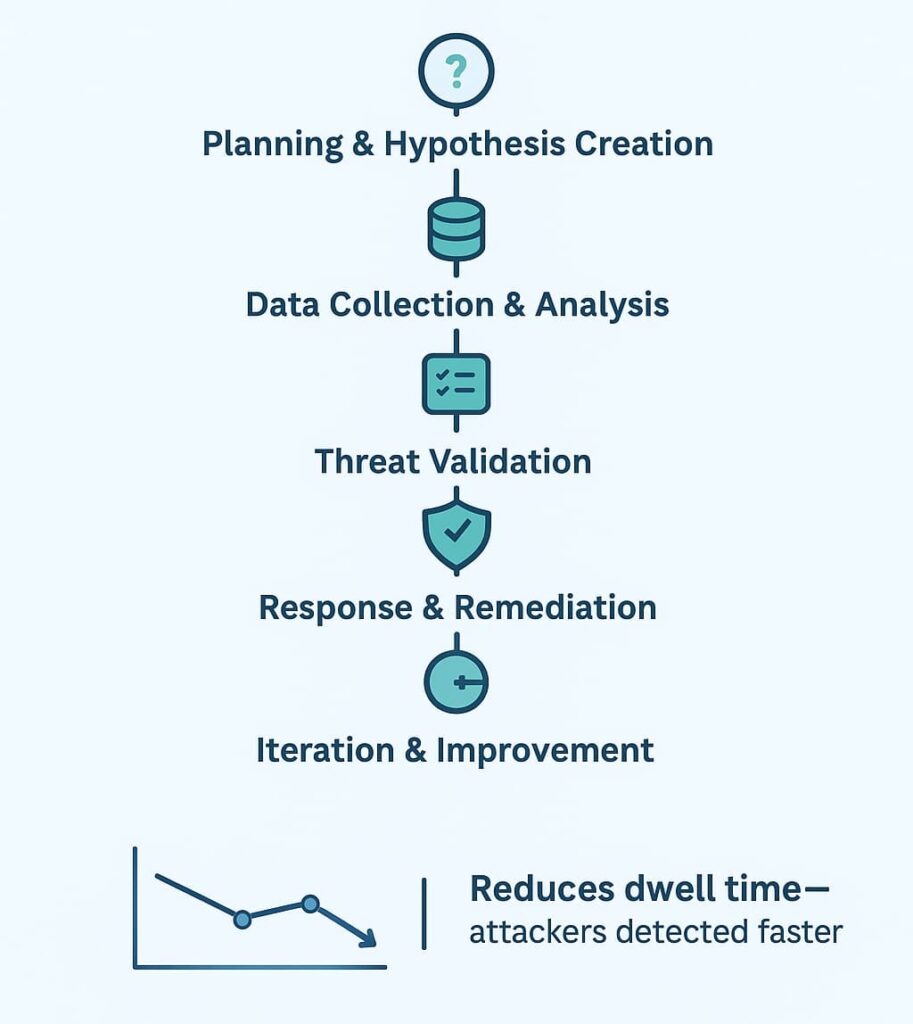
A team builds a plain hypothesis, then moves through each data trail, sometimes circling back when patterns kink or blur, sometimes pushing ahead when a clue feels warm. The cycle keeps running, trimming how long threats sit hidden, and you can see the system grow tougher even on slow days, when evidence comes in crooked.
Keep reading to see how does threat hunting work.

We keep seeing how threat hunting starts with a simple idea: someone chooses not to wait. While automated tools scan for signatures, a hunter walks through logs, odd network shifts, and quiet alerts that never fired, looking for hints that something slipped in sideways.
Some threats hide in short bursts of movement, some in malware that barely changes shape, and a few sit still for weeks, hoping no one looks their way.
There’s a reason hunters stay busy, and it’s not just curiosity. Attackers keep changing their methods faster than filters can tag them, so relying only on automated alarms leaves wide gaps.
When hunters work through those gaps, they cut down dwell time, the stretch attackers spend inside a network without anyone noticing, and that window can be the difference between a small fix and a long recovery. You also see the byproducts: blind spots get mapped, rules get sharpened, and incident responders walk in better prepared.
In our consulting work with MSSPs, we’ve watched how threat hunting becomes an early warning line, even when the findings don’t feel dramatic at first. A strange login at 02:14, an unusual jump between two servers 12 meters apart, or a script that runs only once can tell more than a long alert report.
We help MSSPs select and audit products that make this cycle tighter, and we’ve seen how a good hunting process steadies the whole operation. It gives teams a chance to act before a breach grows teeth, much like what strong proactive managed threat hunting efforts aim to support, and the sense of control that brings matters more than most tools admit.
Credits: Heimdal®
A hunt usually starts with someone asking a simple, pointed question, even if the answer feels far off. A hypothesis forms from new TTP reports, quiet oddities in the environment, or patterns that don’t sit right in a week’s telemetry.
We might find ourselves wondering if compromised credentials are drifting laterally between hosts, and that single question shapes which logs we pull first and which systems we watch closer. [1]
Then the work leans into data, wide logs, short bursts of endpoint traces, network movement that stretches across a few seconds, sometimes less. We’ve seen MSSP teams lean on tools that scan DNS trails, firewall events, and user behavior markers, all overlapping in ways that take some patience to read.
During one hunt, a run of logins from places no one in the org had ever visited forced us into a deeper review, and the pattern finally showed its edges after a long scroll through authentication records.
Of course, not every crooked line means trouble. Suspicious signals get weighed against normal baselines, and a team might simulate an attacker’s path (within safe limits) just to see if the behavior fits.
We’ve watched analysts sift through clusters of alerts only to find a harmless script running at the wrong hour, while another time a tiny mismatch turned into a real foothold. Sorting false positives from genuine threats saves hours, sometimes days.
When something is confirmed, the mood in the room shifts. Systems get isolated, malware pulled apart, and controls tightened. Our role, especially when advising MSSPs, often sits at that junction where hunters hand findings to response teams, making sure nothing slips between the cracks.
The documentation that follows might look dry on the surface, but it becomes the backbone for later response playbooks.
The cycle doesn’t end there; it turns back on itself. Each hunt leaves behind traces, new rules, discarded tools, sharper hypotheses, that make the next pass smoother.
We’ve watched MSSP operations grow sturdier as these small adjustments accumulate, almost like tightening bolts on a long walkway. Over time, the system doesn’t just react better, it sees further ahead.
Threat hunting isn’t one-size-fits-all. Different approaches fit different organizational needs:
We find that combining these approaches, tailored to the client environment, yields the best results.
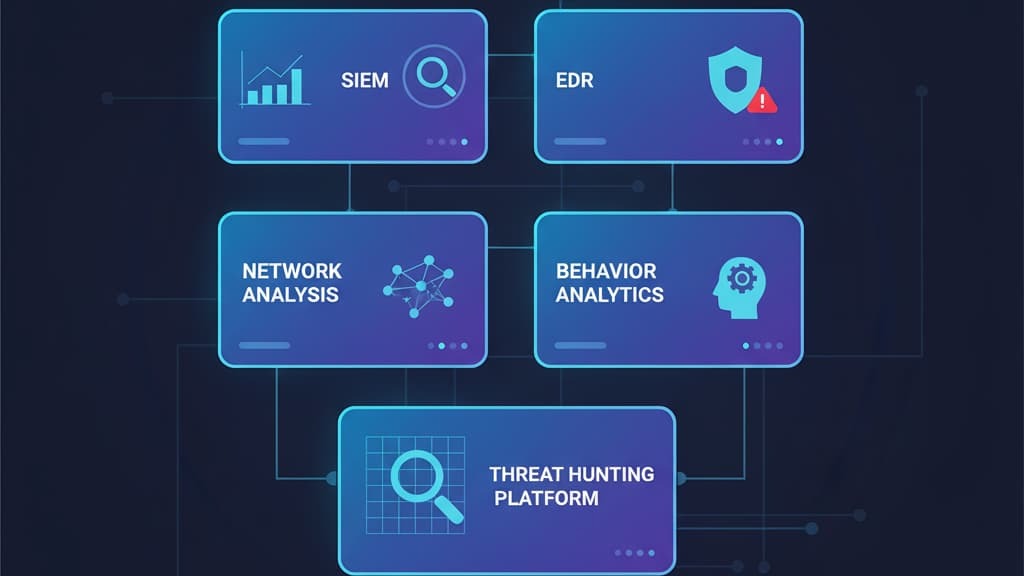
Effective threat hunting relies on a suite of technologies that augment human analysis:
These tools work best integrated, with automation and orchestration to streamline workflows. [2]
From our operations, these practices help maintain an effective threat hunting program:
Threat hunting thrives in an environment where skilled analysts work alongside advanced tools and threat intelligence. As a managed security service provider, we embed threat hunting deeply within our security operations center (SOC) workflows.
This integration allows us to detect stealthy threats early, reduce false positives, and respond swiftly, helping clients maintain robust cyber defense.
Through continuous improvement and collaboration, our threat hunting efforts not only stop attacks faster but also build stronger, more resilient security postures, something that effective MSSP threat hunting practices consistently reinforce across varied environments.
If you’re new, start by learning how threat detection, cyber threat hunting, and proactive security work together. Read simple guides on anomaly detection, threat indicators, and the threat hunting process. These ideas help you see how hunters look for strange patterns, use threat intelligence, and build a clear path toward stronger cyber defense.
Look for odd actions in network traffic analysis, behavioral analytics, or endpoint detection. Sudden changes may point to malicious behavior or an IOC (Indicator of Compromise).
Pairing these signs with MITRE ATT&CK, log analysis, and threat actor profiling helps you understand why something looks wrong and how threat hunting techniques uncover hidden risks.
You can check their value by looking at real-time monitoring, security analytics, and false positive reduction. Tools that support SIEM, data correlation, and security event correlation make it easier to see what matters. When they improve incident investigation and threat mitigation, the tools are likely helping your security posture.
Hypothesis-driven hunting starts with simple ideas about how an attack might work. You test those ideas using endpoint telemetry, threat detection rules, and data visualization. This helps you follow adversary tactics, attack vector clues, and cyberattack patterns while keeping the hunting workflow clear enough for anyone to understand.
Threat hunting is more than a security task, it’s a proactive mindset that helps defenders stay ahead of attackers. By understanding how threat hunting works, organizations can shift from reacting to alerts to actively uncovering hidden risks. This approach strengthens resilience, shortens response time, and reduces the chance of attackers moving unnoticed.
If you want to enhance your cybersecurity foundation, integrating threat hunting, especially with support from expert MSSP Security partners, can make a real difference. With vendor-neutral guidance, tool optimization, and proven experience, you gain clearer visibility and a stronger, more mature security posture.