Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
APTs move in ways that feel almost quiet, like someone brushing past a doorway you didn’t notice at first. You see their trail in tiny marks, logins that drift past midnight, a file growing by only a few kilobytes, a process that hangs on longer than it should, and we think that’s where the truth starts to show.
We watch those marks because these groups don’t rush, they settle in, they study us, and we try to press back with steady intel and hands‑on hunting. It’s slow work, but it matters.
If you want to finding advanced persistent threats, keep reading.
We keep noticing how people talk about APTs like they’re just bigger versions of everyday attacks, though anyone who’s watched one unfold knows they move with a slower, heavier kind of intent.
An advanced persistent threat isn’t loud; it settles into a network and tries to stay there, almost like it’s learning the rhythm of the place. Some groups push these operations for political gain, others for economic pull, and the funding behind them shows in the patience they bring.
There’s a point in our work with MSSP teams where we see the difference more clearly, usually when the first clues surface in places most folks overlook. A crafted spear-phishing email, for instance, opens a tiny door, something that often becomes clearer when you understand how threat hunting works and why early clues matter.
Then comes the privilege escalation (the part that makes admins uneasy), followed by lateral movement that spreads inch by inch across internal systems. It’s slow, careful, and never random.
We’ve watched MSSP analysts try to treat these threats like routine intrusions, and that’s where trouble grows, because APT groups focus on specific, high‑value targets, not broad chaos.
Their campaigns feel planned out, almost mapped by hand. So we remind ourselves, and the teams we guide, that catching them takes a strategic view, not just another set of alerts. Detecting that kind of persistence requires steady observation and tools chosen with intention, which is why product audits matter so much in this space. [1]
Credits: Huntress
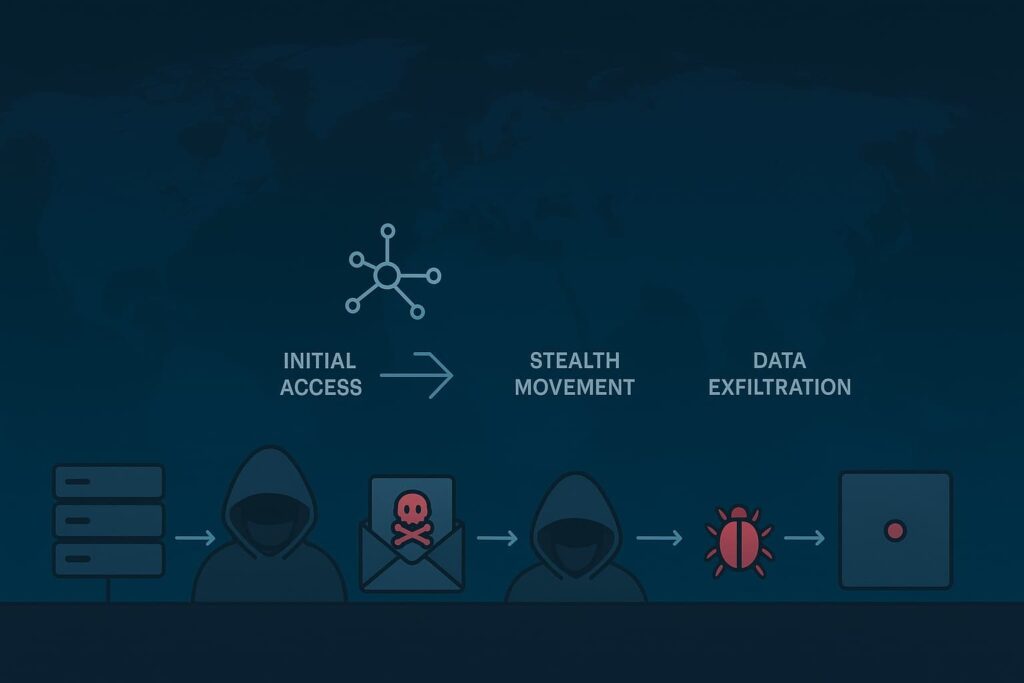
we watched enough APT cases to see how they move in stages, almost like someone tracing a careful path through a house they don’t own. Each step has its own rhythm, and defenders get a clearer shot at spotting them when they understand that rhythm.
Reconnaissance tends to show up first. Attackers linger at the edges, pulling details from public records, probing weak points, even nudging employees with light social tricks. They study a network’s shape long before touching it.
Then comes infiltration. A single spear-phishing lure or an old, unpatched service is usually enough. We’ve seen MSSP teams miss this moment because it feels small, though it sets the whole operation in motion, and why strong visibility from MSSP threat hunting helps catch the earliest traces.
Privilege escalation and lateral movement slide in right after. The intruder lifts their access level, often with borrowed credentials, and then moves sideways across systems. It’s slow, almost cautious, as if they’re testing the floorboards.
When data exfiltration begins, the activity hides inside normal traffic, files shaved down, timed transfers, nothing flashy. Third‑person observers might think it’s regular traffic unless they’re looking with the right tools.
Persistence is the part that unsettles people. Backdoors tucked into odd corners, scheduled tasks that look harmless, little footholds that stay quiet for months. We remind ourselves during product audits that only continuous monitoring picks up these faint marks.
From our own time supporting MSSPs, the pattern stays the same: APT actors lean on “low and slow” methods, and catching them means choosing tools and practices built for patience, not noise.

We rely heavily on real-time monitoring of network traffic, endpoints, and user behavior. Suspicious patterns, like unusual data flows or unexpected login activity, can be early signs of APT presence.
Behavioral analytics powered by machine learning and UEBA (User and Entity Behavior Analytics) tools enhance this detection capability by baselining normal activity and flagging deviations.
Threat intelligence feeds are invaluable in our work. They provide indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) linked to known APT groups.
By correlating observed behavior with this intelligence, we can identify potential intrusions and update defenses accordingly. Staying current with evolving adversary tactics is essential since APT actors constantly innovate.
Deep analysis of logs from firewalls, servers, endpoints, and applications helps us piece together fragments of malicious activity. Correlation engines and provenance tracking allow us to link events across systems, revealing the subtle attack chains typical of APTs.
One of the most effective controls we implement is network segmentation, which isolates critical assets to restrict lateral movement. Coupled with strict access controls, including multi-factor authentication and least privilege principles, this strategy hampers attackers’ ability to escalate privileges and maintain persistence.
Automated tools like SIEM, EDR, and XDR provide broad visibility, but experienced threat hunters bring a critical edge by formulating hypotheses and investigating anomalies manually. It’s this hands-on style that shapes proactive managed threat hunting, where teams look beyond alerts and search for signs attackers try to hide.
When an APT is detected, rapid containment is crucial. We isolate compromised systems, eradicate malicious code and backdoors, and restore systems to a secure state. Post-incident analysis ensures lessons are learned and defenses are strengthened.
From our vantage point in MSSP Security, combining these tools in a layered defense framework offers the best chance to detect and disrupt APT activities early.
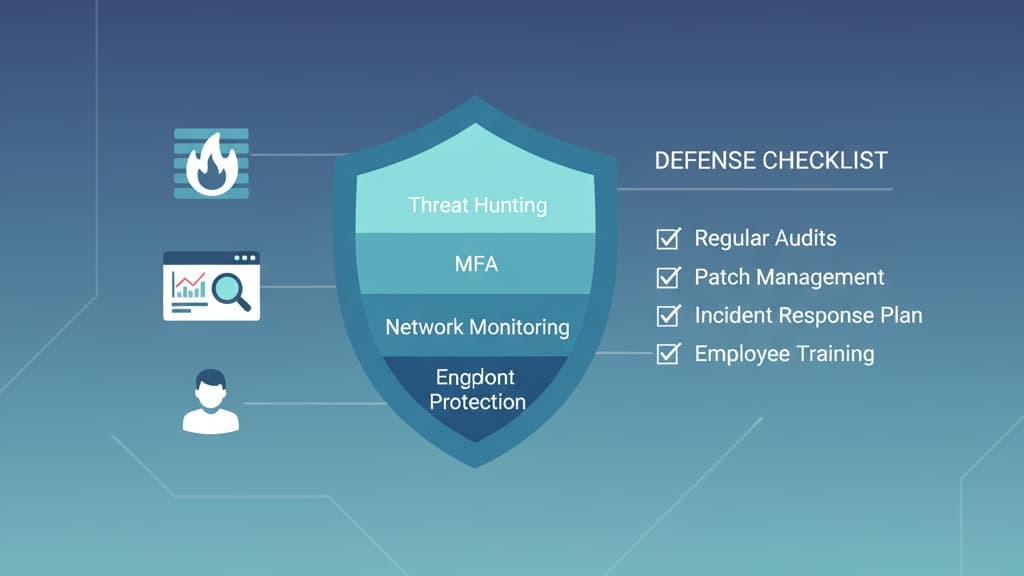
To defend effectively, organizations should:
Our approach at MSSP Security emphasizes continuous improvement and collaboration, recognizing that APT defense is a dynamic challenge requiring vigilance and adaptability. [2]
Noticing an advanced persistent threat early often comes from watching for small shifts in behavior. Slow lateral movement, strange login times, or quiet privilege escalation can point to an initial compromise.
Using anomaly detection, log correlation, and endpoint telemetry can help you see patterns that don’t fit normal habits, even when a stealthy attack tries to stay hidden.
Many threat actors use persistence techniques to stay inside a system. They may hide command and control activity, use malware persistence, or blend into normal network traffic.
They avoid alerts by using stealth tactics, zero-day exploits, or changes in the cyber attack lifecycle. Good network segmentation and user behavior analytics can limit how long they stay.
Large networks need a mix of tools to uncover silent threats. Many teams rely on SIEM, intrusion detection systems, behavior analytics, and network traffic analysis to track unusual moves.
Combining threat indicators, threat intelligence feeds, and incident response playbooks gives a clearer picture of cyber intrusion attempts and the attack surface where APT detection matters most.
Strange system behavior may be harmless, but a pattern can show something deeper. Repeated anomaly detection alerts, unexpected lateral pivoting, or odd C2 communication may point to a stealthy attack.
Checking activity against MITRE ATT&CK, doing forensic analysis, or reviewing malware signatures can help you understand if the behavior matches known attack tactics.
Finding advanced persistent threats is never easy, it requires a dynamic strategy that blends technology, human expertise, and intelligence-driven insight. After countless threat hunts and incident response engagements, one truth is clear: APTs thrive in silence, but a coordinated, proactive defense exposes their path.
If you’re ready to strengthen your resilience against these stealthy attackers, consider partnering with a trusted managed security provider. Our expert consulting helps streamline your stack, enhance visibility, and elevate threat hunting maturity.