Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Any device connected to a network might be the next target. The mere thought probably keeps security teams awake at night, staring at screens full of alerts. But there’s a solution that’s making their lives easier, Endpoint Threat Detection Response, or ETDR.
When hackers strike computers, phones, or servers (basically anything with an internet connection), every second counts. That’s where ETDR steps in, working like a digital security guard that never sleeps. It doesn’t just watch for trouble, it actually does something about it.
Think of ETDR as the friend who spots trouble at a party before it starts and knows exactly what to do about it. It’s watching everything happening on devices across a network, picking up on weird behavior that might spell trouble.
There’s something almost old,fashioned about picturing antivirus software as our main defense these days. Endpoint Threat Detection & Response takes things way further , it’s built to catch bad actors early, figure out what they’re up to, and shut them down fast before they can wreak havoc.
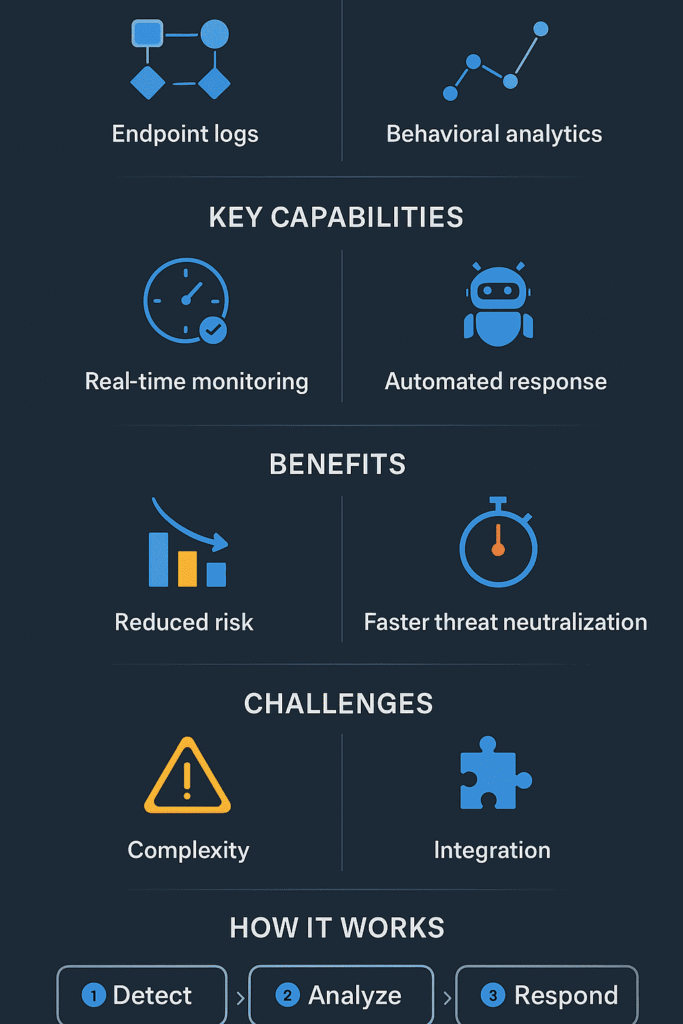
The whole thing runs on three basic jobs that work together: detect, investigate, respond. Detection watches everything happening on devices (computers, laptops, phones) for anything that doesn’t look right , weird programs starting up, unusual network stuff, files changing when they shouldn’t.
According to IBM, as many as 90% of successful cyberattacks and 70% of successful data breaches originate at endpoint devices, underlining why detection at the endpoint is absolutely mission-critical (1)
Investigation’s about digging into those red flags to figure out what’s really going on. Response, that’s the muscle , it jumps in to stop threats cold, often without needing a human to give the go ahead.
Unlike old,school antivirus that sits around waiting for known threats, ETDR actively hunts for behavior that just seems off. It’s got smart ways of spotting new attacks that nobody’s seen before.
The real power of ETDR comes from what it sees and how it makes sense of it all. It’s collecting data from everywhere, what processes are running, how much memory’s being used, changes to settings, what files are doing, network connections, even tracking what users are up to on their devices.
All this info feeds into different ways of catching threats. There’s behavior watching that spots weird patterns, matching against known threat signatures, AI that catches stuff humans might miss, and intel from global threat feeds that adds extra context.
Meanwhile, demand for these systems is surging, the global EDR market is expected to hit USD 7.27 billion by 2026, growing at 26% annually (2)
For ETDR to really work, it needs certain abilities running all the time. It has to watch endpoints 24/7 (because threats don’t sleep), and it needs to respond automatically when it spots trouble , and can’t always wait for someone to push a button.
Threat hunting’s a big deal too. Security teams can actively look for threats hiding in all that collected data instead of just waiting for alarms to go off. And it all needs to work with other security tools (SIEM and SOAR platforms) to see the bigger picture.
The big names in ETDR tools include:
Each one’s got its own mix of features , and that’s where solid EDR management plays a role in keeping the setup effective. Picking the right one depends on what you need to protect and how you want to do it.

Credit: pexels.com (Photo by Christina Morillo)
Anyone who’s spent a sleepless night handling a cyber breach knows the brutal truth about dwell time. ETDR cuts through that mess, shrinking the window attackers have to wreak havoc.
This idea of reducing attacker dwell time is one of its biggest strengths, like having a security guard who doesn’t just spot trouble but actually does something about it right away.
The tech gives security teams a real-time view of what’s happening on every device (laptops, desktops, servers , the whole nine yards). Perfect for those minds,numbing compliance reports that nobody wants to compile but everyone needs.
But let’s be real , it’s not perfect. The biggest pain? Alerts. So many alerts. Security teams get bombarded with notifications, and sorting through them feels like finding needles in digital haystacks. Even with good tuning, it’s still a challenge.
Then there’s the whole performance thing. These monitoring agents need computing power, and they’ll take it from somewhere. Users might notice their machines running slower if the setup isn’t just right. Plus, you need people who actually know what they’re doing to run these systems. Not exactly something you can throw at the new intern.
Despite the headaches, most organizations find it’s worth the investment, especially when facing down sophisticated threats.
The whole system runs on data , tons of it. Each endpoint runs agent software that’s constantly watching everything: new processes spinning up, files changing hands, registry tweaks, network connections, user activity. All of it.
This flood of information feeds into detection engines that never sleep, using fancy behavioral analytics and machine learning to separate the normal from the nasty. They’re looking for known bad guys and weird behavior that might signal something new.
When something sketchy pops up, the system jumps into action automatically. It might quarantine the infected machine, kill suspicious processes, or lock down sensitive files. These automated responses buy precious time for the human experts to figure out what’s really going on.
The security team gets alerts with enough forensic details to piece together what happened. Without automation handling the heavy lifting, they’d never keep up with the constant stream of data.
Think of it like layers of defense, each with its own job. Traditional antivirus is the old guard , it checks files against known bad stuff. Simple but limited. Can’t catch what it doesn’t know about. EDR takes that basic idea and supercharges it with real,time monitoring and automated responses.
XDR goes bigger, pulling in data from everywhere , networks, cloud services, user accounts. It’s more comprehensive but needs everything to play nice together. Usually builds on what EDR already does.
SIEM’s the big picture tool, collecting logs from across the organization. It’ll take alerts from EDR and other tools, but doesn’t get into the nitty,gritty endpoint stuff or handle responses like EDR does.
ETDR fills that sweet spot between basic antivirus and broader security platforms, focusing hard on endpoint protection with enough automation to make it practical.
Across the security operations floor, the constant ping of alerts has become white noise , a problem that’s pushing teams to their limits. Smart organizations are fighting back against this digital cacophony, finding ways to make their ETDR actually work for them instead of drowning in data.
Teams are getting smarter about alerts, cutting through the noise by setting up better filters and priority levels. The good ones let machines handle the boring stuff (like known,safe program installations) while human analysts tackle the weird and dangerous threats that need real brain power.
Nobody wants security that brings their computer to a crawl. The best ETDR tools run light , we’re talking less than 2% CPU usage on average. Most vendors push the heavy lifting to cloud servers (processing about 100GB of endpoint data per day for a mid,sized company).
Security tools need to play nice together. Modern ETDR systems feed data straight into security dashboards and automation platforms. The math is simple: one screen equals faster response times, period.
A fancy tool’s useless without smart people running it. Security teams need real training , not just clicking through slides but hands-on practice with live scenarios.
Some companies run three hour shifts for round the clock coverage, while others partner with security firms under clear MDR service level agreements who do the watching for them.
This isn’t just another tech trend that’ll fade away. ETDR’s become as essential as locks on doors, just a lot more complicated. Here’s what needs attention:
Bad guys don’t sleep, and they’re getting faster every day. Good ETDR makes their job harder, your response quicker, and keeps endpoints locked down tight.
Look around any company these days and you’ll see endpoints everywhere , laptops, phones, servers, they’re all over the place. That’s why ETDR isn’t optional anymore, it’s just part of doing business.
The system works 24/7, watching those endpoints like a hawk, jumping on anything fishy, and dealing with threats right away. ETDR cuts down the time attackers hang around in networks from months to days or hours.
Yeah, there’s some headaches , too many alerts driving analysts crazy, computers running slower sometimes, and needing people who actually know what they’re doing (which doesn’t come cheap). But here’s the thing: when it talks nicely with other security tools and catches bad guys in realtime, that’s what matters.
The simple truth is attackers don’t wait around anymore, and neither can defense teams. EDR gives security professionals a fighting chance, spots threats early, and keeps organizations from becoming tomorrow’s breach headlines.
Endpoint security protects individual devices, while traditional threat detection and threat response focus more on networks. With real-time threat detection, endpoint monitoring, and malware detection, teams can spot ransomware detection signals and contain attacks quickly. Network isolation and continuous monitoring add another layer of cybersecurity defense.
Endpoint monitoring and continuous monitoring provide endpoint telemetry and endpoint logging that reveal suspicious activity. Anomaly detection and endpoint anomaly detection make responses faster, while forensic analysis and endpoint investigation give context.
Endpoint threat hunting digs deeper than automated threat detection to catch hidden risks. It supports ransomware detection and advanced persistent threat detection by analyzing endpoint telemetry, endpoint activity logging, and endpoint sensor data.
Endpoint investigation confirms if malware detection alerts are real threats. Using endpoint forensics, endpoint malware analysis, and endpoint threat investigation, teams decide when malware containment or endpoint isolation is needed.