Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

The screen glows blue in a dimly lit security operations center, where analysts scan through endless streams of data. Each alert might mean trouble , a laptop in accounting acting weird, or maybe someone’s phone trying to connect to a sketchy server in who knows where.
Every device connected to a network is like a door left slightly ajar. Sure, you could slam it shut, but people need to work. That’s where Endpoint Security MDR comes in, and it’s changing how we protect our digital doors.
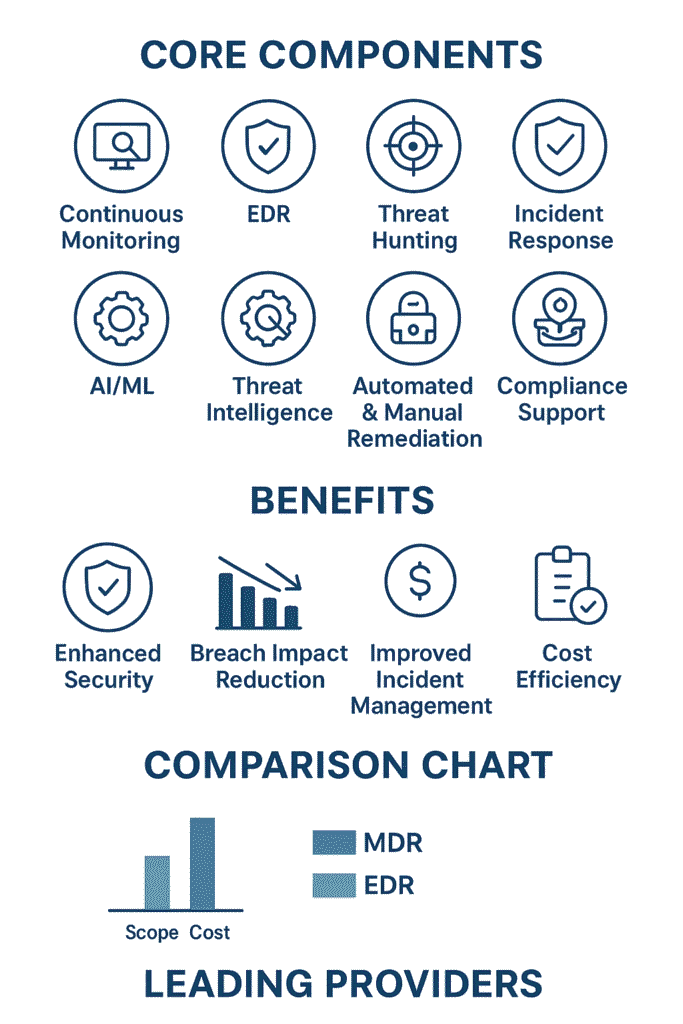
Anyone who thinks endpoint protection means just having antivirus software on their computer needs to wake up. Endpoint Security MDR (Managed Detection and Response) watches over every device connected to your network like a hawk , laptops, servers, phones, the works.
It’s not passive either, there’s always something happening under the hood. The real magic happens when tech meets human smarts. Unlike traditional antivirus software, MDR combines advanced technology with human expertise to detect, analyze, and respond to threats in real time (1)
Software agents sit quietly on devices, collecting mountains of data about what’s running, who’s doing what, and where data’s flowing (kind of like having thousands of security cameras, but for your network). Behind the scenes, analysts watch 24/7, ready to pounce on anything suspicious.
This tag team approach means bad actors can’t hide long. When something sketchy shows up , maybe ransomware trying to encrypt files or some sneaky malware playing it cool , the system catches it fast.
Picture someone watching every door and window of a house, all the time. That’s what endpoint monitoring does for your network. It tracks processes, connections, file changes , anything that moves.
The second something looks off, alerts start flying, giving your team the same proactive managed detection advantage top MSSPs provide.
EDR’s the heavy lifter here. It’s constantly gathering data, looking for signs of trouble. Let’s say a program starts acting weird or trying to access things it shouldn’t , EDR catches that. But EDR by itself isn’t enough, which is why MDR steps in with actual humans making the tough calls.
Endpoint Detection and Response (EDR) is a cybersecurity technology that continuously monitors and responds to threats on endpoint devices such as laptops, desktops, and mobile devices (2).
Sometimes the bad guys are too clever for automated systems. That’s where human threat hunters come in, digging through data like digital detectives. They’ll spot things machines might miss, like that one weird login at 3 AM from halfway around the world.
When things go sideways, MDR teams don’t mess around. They’ll isolate infected machines, kill bad processes, and clean up the mess, sometimes automatically, sometimes with an analyst double checking everything. Speed’s crucial here, every minute counts when malware’s trying to spread.
Modern MDR uses some pretty impressive AI to crunch through data (we’re talking terabytes here), delivering the full range of managed detection and response benefits without overwhelming analysts.
It helps cut through the noise, so analysts aren’t chasing false alarms all day, making ai assistant technology a key part of continuous protection.
MDR platforms tap into global threat feeds, staying current on what the bad guys are up to. It’s like having spies in enemy territory, feeding back intel about new attack methods.
Some problems can be fixed by automation , quarantining suspicious files or blocking sketchy IP addresses. Others need a human touch. Good MDR solutions know when to use which approach.
Everything gets logged, tracked, and stored. Need to figure out how an attack happened three months ago? The data’s there. Auditors asking questions? You’ve got answers.
Between the chatter of cybersecurity conferences and vendor pitches, there’s a constant buzz about MDR and EDR. They’re cousins in the security family, but they’re not twins.
EDR works like a security camera system for computers , it watches, records, and sends alerts when something looks off. Pretty straightforward stuff, but someone’s got to watch those cameras.
MDR takes that same system and adds real people behind the screens (think of those intense security monitoring rooms you see in movies). These folks don’t just stare at alerts , they dig in, investigate, and jump into action when needed. Expertise Integration
With MDR, there’s always someone keeping watch. Teams of analysts work in shifts, digging through the data 24/7, looking for the needles in the digital haystack. EDR’s more like having the cameras but expecting your already busy staff to monitor them between their regular duties.
MDR doesn’t just sit back and wait for trouble. The teams actively hunt for threats, kind of like security guards doing their rounds instead of just watching monitors. They’ll spot things EDR might miss on its own.
Sure, MDR costs more than just buying EDR software. But it’s like choosing between buying a car and hiring a driver. Sometimes it’s worth paying extra to let someone else handle the wheel, especially if you don’t have time to learn every traffic rule.

Credit: unsplash.com (Photo by Cristiano Firmani)
When you’ve got both smart software and skilled analysts working together, threats don’t stand much chance.
These teams spot problems faster than software alone, and they know exactly what to do when they find something, giving organizations a measurable MDR service level that reduces risk.
Quick reactions matter. When MDR teams spot an attack, they shut it down fast , before it spreads through networks like wildfire. Keeps the business running smooth.
IT teams already have enough on their plates. MDR takes the security load off their shoulders, letting them focus on keeping everything else running.
MDR brings big company security to smaller operations without breaking the bank. It grows with you , adding more protection as you need it.
Most MDR services track everything and generate the reports regulators want to see (particularly helpful for those dealing with HIPAA, PCI, or GDPR requirements).
The security market’s crowded with endpoint protection vendors, each claiming they’re the best. Here’s a real look at who’s who and what they actually bring to the table.
A cloud based service that watches your endpoints round the clock. They’ve made it pretty straightforward to get up and running, and you won’t find any surprise costs in the fine print. While their forensics work well enough, they might not dig as deep as some others in the field.
Running on their Singularity platform, this one’s got some serious AI muscle behind it. They hang onto your data longer than most (which comes in handy), and their machine learning really works. But it’s not cheap, and setting it up isn’t exactly a walk in the park.
They’ve taken a regular Defender and added some actual experts to watch over things. Works like a charm if you’re all,in on Windows, and it’ll keep the compliance folks happy. Just don’t expect much if you’re running other systems , it’s not their strong suit.
Part of Sophos’ bigger security package, covering pretty much everything from endpoints to cloud stuff. They let you pick different service levels, which is nice. Makes sense if you’re already using their other products, though they’re playing catch up with some of the AI features.
Their MDR ties right into their XDR platform and works great with their firewalls. If you’ve got Palo Alto gear already, it’s worth a look , they know their stuff when it comes to spotting trouble across networks and endpoints.
Arctic Wolf, Rapid7, Red Canary, Expel, and eSentire are all doing good work in the MDR space, each with their own twist on endpoint security.
There’s no one,size,fits,all here. Your pick should match what you need.
MDR’s different because it mixes smart tech with actual human brains, giving you protection that regular endpoint security just can’t match. For companies serious about stopping the bad guys, MDR’s worth every penny. It’ll strengthen your security, handle problems faster, and let your team sleep better at night.
Your endpoints need protecting, that’s just facts. MDR might be your next smart move. Take a hard look at what you’ve got now and find a provider that fits. Your whole system will run better for it.
Endpoint security combined with MDR strengthens threat detection, continuous endpoint monitoring, and incident response. While an endpoint protection platform or EDR blocks known threats, MDR adds human expertise for breach detection, ransomware defense, and cyber threat hunting.
Traditional endpoint protection platforms or EDR tools handle malware detection, endpoint threat prevention, and ransomware defense. MDR adds 24/7 SOC integration, automated threat response, behavioral analytics, and cyber threat hunting.
MDR uses continuous endpoint monitoring, endpoint anomaly detection, and real-time threat analysis to spot risks quickly. It improves breach detection, phishing protection, insider threat detection, and endpoint risk assessment.
Combining MDR with vulnerability management, endpoint security policies, and best practices strengthens endpoint access control, configuration management, and endpoint security lifecycle.
Zero trust architecture, endpoint compliance, data loss prevention, endpoint encryption, and sandboxing enhance phishing protection and intrusion detection.