Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

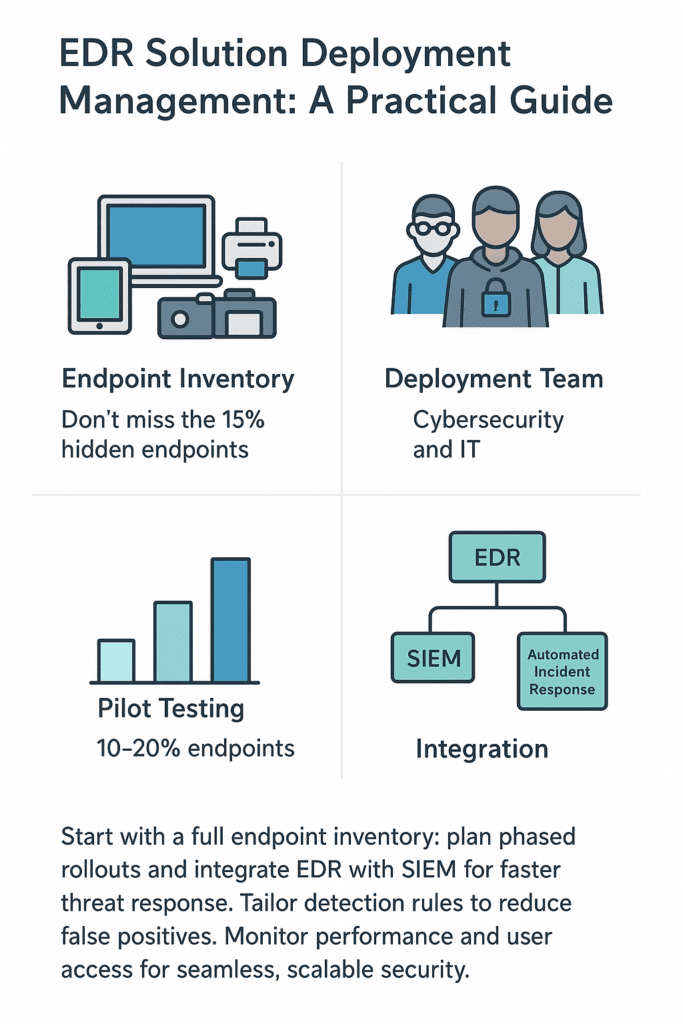
Security teams can’t just throw EDR tools onto their network and hope for the best. First things first: map out every single device, from the dusty old print server to the CEO’s laptop. Getting a real grip on which machines face the biggest threats makes all the difference.
Building the right team matters too, mixing security nerds with the IT folks who know the network inside and out. They’ll handle everything from getting agents installed to making sure alerts don’t get lost in the noise. Want to nail your EDR rollout? There’s more to cover , keep reading.
Nobody ever walks into a building knowing exactly what they’re protecting. That’s the problem with most organizations , a real mess of devices that just keep multiplying like rabbits. T
The first step’s always getting an honest count of every single endpoint out there, and we’re not just talking about the obvious stuff. It’s those random tablets in conference rooms, the security cameras nobody thinks about, and yeah, even that one printer from 2005 that’s somehow still chugging along.
After getting that list (and double checking it, because there’s always something missed), it’s time for the fun part , finding all the holes. Every device needs a good once over for ancient software versions,
patches that never got installed, and security rules that don’t quite match up to whatever compliance standard’s giving the security team headaches this week. Some devices are gonna need way more attention than others, that’s just how it goes.
Setting up these security systems isn’t exactly straightforward. There’s cloud options (perfect for companies that can’t sit still), on premises (for the control freaks), or something in between. It really depends on how big the place is and what kind of rules they’ve got to follow.
Gotta think ahead too. What works for a small office today might completely fall apart when they triple in size next year. Better to build it right the first time.
Integration’s key , these tools need to play nice together. When the EDR can actually talk to everything else, it’s way easier to spot the weird stuff happening. Some of these systems are smart enough to fight back on their own (when they’re set up right, anyway).
Rolling this stuff out takes patience. Start with a small group, maybe 10,20% of the endpoints, work out the kinks, then spread out from there. Beats having the whole place crash and burn at once (1).
Communication’s crucial through all of this. Nobody likes surprise software installs showing up on their computer, so keeping everyone in the loop helps keep the panic down.
For installing everything, automation’s your friend , most of the time. But there’s always those special cases that need someone to stand there and watch it happen. Good thing the main dashboard shows what’s working and what’s not, cause something always goes sideways somewhere.
The security team’s headaches often start with those endpoint detection and response management rules that never quite work right. Like a poorly fitted suit, these defaults need serious tailoring.
It’s a delicate dance between catching threats and not driving the analysts crazy with endless false alarms. Sitting down with the team and poring over incident logs, they tweak those settings until they’re just right.
Key areas for customization:
Dealing with endpoints isn’t exactly straightforward either. Most companies are running a zoo of different systems , old Windows machines that should’ve been retired years ago, the latest Macs, and everything in between.
Mobile devices add their own special brand of chaos to the mix, with employees carrying them everywhere and connecting to who knows what networks.

Credit: pexels.com (Photo by cottonbro studio)
The whole “who can touch what” question gets pretty intense when you’re talking about EDR systems. Think of it like a newsroom , editors get different access than reporters, and freelancers get even less.
When you’re managing security for multiple clients (which happens a lot in the managed services world), keeping everyone’s data separate becomes super critical.
Response workflow essentials:
The real magic happens when all these pieces work together. When that ransomware alert pops up at 3 AM, the system’s already working to contain it before the on-call analyst even reaches for their phone.
Every alert gets logged, tracked, and handled according to preset playbooks , because nobody’s making their best decisions at 3 AM, and sometimes the computer really does know best.

Credit: pexels.com (Photo by Christina Morillo)
A quiet endpoint is a protected endpoint. Nobody wants security software that drags down their laptop , that’s just asking for users to try and disable it.
The tech team tracks things like CPU usage and disk I/O to catch any hiccups before users start complaining. Patches and updates roll out seamlessly in the background (most of the time anyway).
Getting the alerts right is a constant battle. The security team’s already drowning in notifications, and they don’t need more noise clouding their view. A mix of fine,tuning and plugging in threat feeds helps separate the real threats from the background noise.
The human side matters just as much as the tech. The security team runs through attack simulations and follows detailed playbooks, so they don’t freeze up when something nasty hits.
Teaching regular employees about security doesn’t hurt either, they’re usually the ones who click on something they shouldn’t.
Everything needs a paper trail these days. With GDPR and NIST breathing down everyone’s neck, proper logging and data handling isn’t optional anymore. The vendor’s support team pitches in with updates and scaling advice to keep the system running smoothly.
Numbers tell the story at the end of the day. How fast can the team spot a threat? How quickly do they shut it down? These metrics shape where the program goes next (2).
Key metrics to watch:
Rolling out EDR doesn’t mean just clicking “install” and hoping for the best. You’ve got to know what you’re protecting first , every laptop, server, and mobile device on the network needs counting. (Most organizations miss about 15% of their endpoints in initial counts).
Building the Right Foundation :
The day-to-day stuff matters too. Real time watching of what’s happening, letting the system block obvious bad stuff, and making sure your team knows what they’re doing , it all adds up. And don’t forget to check if those agents are still running right and catch those false alarms before they drive everyone crazy.
Continuous endpoint security monitoring helps keep visibility sharp and reduces blind spots that attackers love to exploit.
Make a list. A real one, not just what you think you have. Get people involved who know both the tech side and how the business actually runs. Don’t try to do everything at once , that’s asking for trouble. Test it, see what people say, and keep tweaking those rules.
Hook it up to your other security tools (like SIEM) and set up some automatic responses. When something sketchy shows up, you’ll want to move fast.
In some cases, having a plan for EDR incident investigation can be the difference between a quick fix and a lingering breach.
Sure, managing EDR is kind of like having a puppy, it needs constant attention. But stick to these steps, and you’ll end up with security that actually works and grows with you. No magic required, just solid planning and follow through.
Deploying and managing an Endpoint Detection and Response (EDR) solution isn’t about flipping a switch, it’s about building a resilient framework that protects every corner of your organization’s digital environment.
Success begins with knowing exactly what you’re defending: a full inventory of endpoints, risk assessments, and a clear understanding of where vulnerabilities lie.
From there, a thoughtful strategy,balancing phased rollouts, fine-tuned policies, and seamless integration with existing security infrastructure, ensures the technology actually strengthens defenses instead of overwhelming teams with noise.
Equally important is the human element. EDR thrives when cybersecurity specialists, IT operations staff, and business leaders collaborate, keeping both the technology and the workflows aligned. With automation handling routine responses and analysts empowered by streamlined dashboards.
Continuous monitoring, alert refinement, and user education transform EDR from a reactive tool into a proactive shield.
With over 15 years of experience and 48K+ projects completed, we help MSSPs and enterprises streamline operations, reduce tool sprawl, and optimize their security stack, from vendor-neutral selection and PoC support to actionable recommendations that align technology with business goals. Ready to strengthen your EDR strategy? Let’s build it together.
EDR deployment sets the stage for endpoint detection and response by ensuring every device is protected from the start. When done well, endpoint security deployment reduces blind spots and makes it easier to keep track of systems.
EDR agent installation is at the heart of any rollout strategy. These small software pieces sit on each device and allow endpoint monitoring to happen in real time. Without them, teams would struggle to collect data or react to threats.
SIEM integration connects EDR management to broader security tools, so information flows across systems. Together, automation and integration remove silos and speed up the reaction process. The end result is fewer delays, stronger defenses, and a clearer view of what’s happening across the network.
EDR policy configuration guides how the system reacts when threats show up. Well-made policies help with endpoint threat hunting by pointing teams toward the right signals. At the same time, they protect EDR agent health.