Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

inding breaches early can mean life or death for company networks. When malware sneaks in, EDR tools record every suspicious file, connection, and process, kind of like a black box for computers. The system digs through event logs and network traffic, putting together a picture of what happened.
Tests show that good EDR cuts response time from days to hours, maybe even minutes. Most attacks get shut down before they mess up other machines. Want to know what makes EDR tick? Keep reading.
There’s something fascinating about watching digital threats unfold in real time across thousands of endpoints. It’s like being a detective who’s got eyes on every corner of a massive city, except this city is made up of computers and servers that need protecting 24/7.
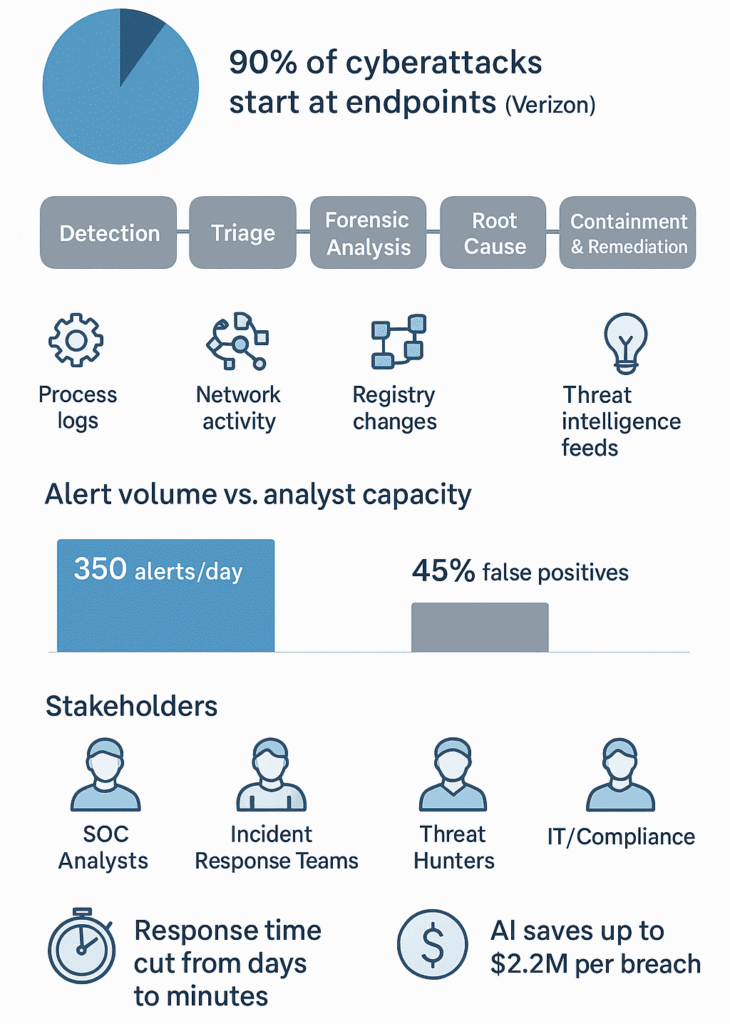
Endpoints fuel most breaches. According to Verizon, roughly 90% of successful cyberattacks and as many as 70% of data breaches begin at the endpoint (1).
The job’s pretty simple on paper , catch the bad stuff quickly, figure out what it’s doing, and stop it before it spreads. But anyone who’s spent time in a SOC knows it’s way messier than that.
The service combines behavioral analysis (the kind that spots when endpoints start acting weird), malware hunting, and non,stop monitoring of every device on the network.
Picture a constant stream of data flowing from every endpoint , processes starting up, files changing, weird behavior patterns. The system’s always watching, always collecting these digital breadcrumbs that might lead to something nasty.
Let’s be real , most alerts are just noise. A good analyst might see hundreds each day, and they’ve got to sort through them fast. It’s about picking out the real threats from the false alarms, kind of like finding needles in a digital haystack.
This is where things get interesting. The service digs deep into what happened on each endpoint, collecting everything from process logs to network connections. Think of it as digital archaeology, piecing together what happened from the traces left behind.
Nobody just wants to know what happened , they need to know how it happened. Was it a phishing email? A zero day exploit? Some employee who clicked the wrong link? This part’s about connecting all the dots.
Once you’ve found the problem, you’ve got to stop it from spreading (usually by isolating infected systems) and clean up the mess. Sometimes it’s automatic, sometimes it needs the human touch.

Credit: unsplash.com (Photo by Headway)
Data’s the key to everything in endpoint security. Without good data, you’re just guessing. That’s why strong endpoint threat detection response capabilities ensure investigations can trace attacks with precision instead of relying on assumptions.
The best EDR tools out there can:
This tech’s what keeps the incident response team moving fast when every second counts.
The digital security landscape needs multiple teams working together, each bringing their own expertise to the table. Some might call it complex, but it’s really just about having the right people in the right places. AI powered solutions can save as much as USD 2.2 million per breach (2).
SOC Analysts work through endless streams of alerts all day, sifting wheat from chaff, moving from simple checks into full-blown searches when something doesn’t look right. Like air traffic controllers, they’re watching dozens of screens at once, (it’s usually more than eight displays per person).
Incident Response Teams might as well carry digital fire hoses. They rush in when alarms go off, armed with pre-made scripts and tools that can quarantine infected systems in seconds – beats doing it by hand, which used to take hours. There’s no time for coffee breaks when ransomware’s spreading.
Threat Hunters don’t wait for trouble to find them. They poke around in dark corners of networks looking for signs that something’s off, even slightly.
A login at 3 AM from an IP in Russia? That’s worth checking out. Three failed password attempts from the CEO’s account while they’re supposed to be on vacation? Even more suspicious.
IT and Compliance Teams get stuck with the paperwork nobody wants to touch. They’re writing up incident reports, checking boxes for auditors, making sure every single thing that happened gets documented properly.
Not the most thrilling job, but somebody’s got to keep the regulators happy and the lawyers off everyone’s backs.
Speaking of results, organizations that get EDR investigation right tend to see some pretty clear benefits:
Security analysts stare at screens filled with endless streams of alerts thousands per day flooding their dashboards like water from a broken dam. Most teams run with half the people they need, leaving analysts scrambling to keep up with an average of 350 alerts each day (based on recent industry reports).
The reality? About 45% of these notifications are complete duds. False positives. Dead ends that lead nowhere. Yet each one needs checking, documenting, closing out. Time ticks away while real threats might slip through unnoticed.
Take a typical day at a mid,sized company: the morning starts with 127 new alerts, another 89 from overnight, and they just keep coming. Every beep could mean trouble or nothing at all. One analyst’s been working on the same potential incident for three hours, turns out it’s just a misconfigured server setting off alarms. Again.
The math doesn’t add up. There’s just not enough hands on deck, and the tools keep crying wolf. Something’s gotta give, and right now it’s the security teams caught in the middle of this mess.
Looking at the bigger picture, there’s different ways to tackle this:
The trick isn’t picking the fanciest option , it’s picking what actually works for your situation.

Credit: unsplash.com (Photo by Shahadat Rahman)
A forensic investigator’s workflow doesn’t look that different from a detective’s case board, just with more screens and fewer pushpins. Here’s how the process actually works:
Everything starts with data (lots of it). This digital evidence hunt runs through these main phases:
These tools aren’t perfect, but they’re getting better. Here’s what they bring to the table:
A computer screen flickers at 3 AM while security teams pore over data streams. That’s what EDR incident investigation services look like in real life , not the glossy vendor photos of analysts in clean rooms.
Watching endpoints 24/7, gathering evidence, and fighting back against threats automatically , that’s what makes these systems work. But there’s more to it than fancy software. Success depends on getting your people and processes lined up right, along with the tech tools.
And yeah, breaches will happen. That’s just reality in 2024. But having solid EDR investigation capabilities means the difference between catching problems early or explaining to the board why customer data is showing up on the dark web.
For companies that actually care about protecting their stuff (and they all should), it’s pretty simple—you’re gonna get hit someday. The only question is whether you’ll see it coming and stop it fast, or find out about it on the news. EDR investigation tools give you a fighting chance.
Endpoint detection and response is central to an EDR incident investigation because it gathers endpoint telemetry, tracks behavioral indicators, and strengthens threat detection. By combining process monitoring, activity logging, and file integrity monitoring, investigators can uncover malicious activity analysis patterns early.
Threat hunting works closely with behavioral analysis to stop threats before they spread. With endpoint monitoring, teams watch for behavioral indicators linked to ransomware detection, phishing detection, or APT detection.
Incident response automation helps a security operations center handle threats at scale. Automated incident response and response automation cut down manual work during SOC incident response, reducing the time needed for breach remediation or system recovery.
A forensic investigation often begins with collecting endpoint audit trails and examining them with forensics tools. Malware analysis, network traffic analysis, and malicious activity analysis play major roles. Endpoint breach investigation may involve IOC detection.