Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

A data breach investigation service shows you exactly how an attacker got in, what they did, and what risks you’re facing now. When a breach happens, the real problem isn’t just the attack, it’s not knowing what was exposed or how far it spread.
A careful investigation collects evidence, reviews logs, maps the attack path, and closes the gaps so it can’t be used again. At MSSP Security, we focus on speed, clarity, and containment, so you’re not guessing in the dark.
If you want to see how this process works step by step, keep reading.

A data breach investigation service always starts with one truth: a breach is more than stolen data, it’s a business emergency. Many breaches also require elements of digital forensics to understand how attackers moved and what systems they touched.
A data breach means someone gained unauthorized access to sensitive information like personal data, financial records, intellectual property, or operational files.
When attackers get in, they move quickly. They look for weak controls, misconfigurations, or human errors. They often take advantage of old vulnerabilities.
The financial toll is heavy. Industry reports show that data breaches lead to fines, legal fees, customer churn, and expensive downtime. One SERP source notes that organizations also deal with reputational fallout because “loss of customer trust can be more damaging than the breach itself.”
When systems go down, operations freeze. Employees panic. Customers worry. Leadership wants answers.
A strong data breach investigation gives those answers in hours, not weeks. It shows what happened, how far the attackers went, and what needs to be done to contain the damage. At MSSP Security, we’ve seen that businesses who respond in the first minutes, not days, save the most time and money. [1]
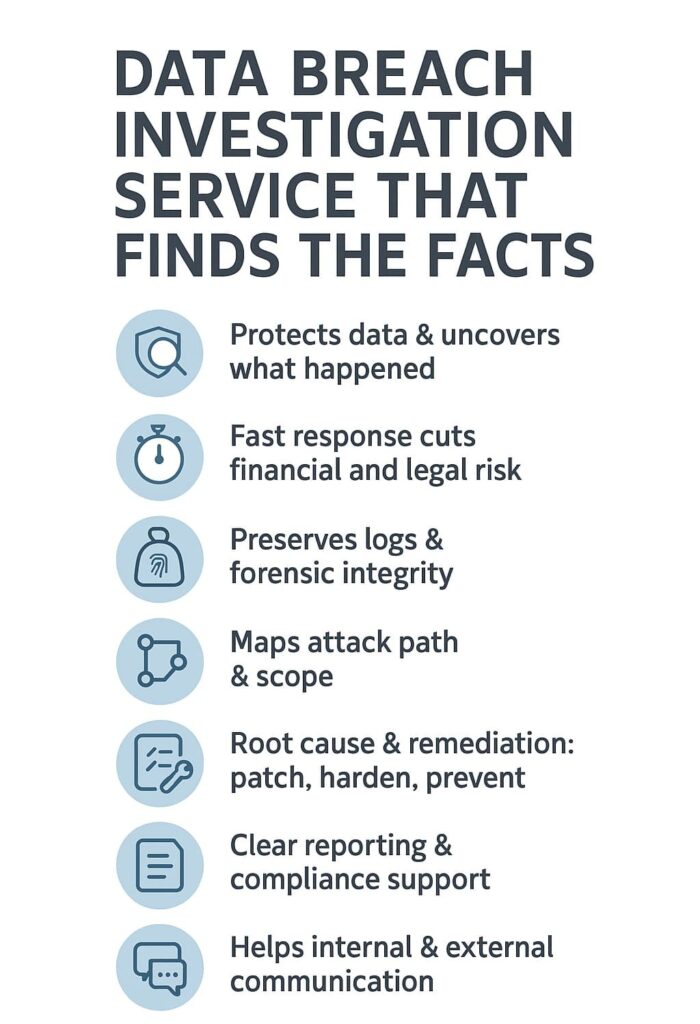
A data breach investigation service begins the moment an alert appears. Maybe it’s a spike in network traffic. Maybe it’s an employee who reports strange activity. Sometimes an outside party sends a warning. No matter the trigger, the first step is the same: contain the breach without destroying evidence.
Responders isolate affected systems, preserve logs, and prevent attackers from moving laterally. We always preserve forensic integrity because legal teams and regulators often need proof of what happened.
“Immediate containment prevents further data loss while maintaining evidence integrity,” as one SERP source states. In our experience, the first hours shape the entire outcome.
Once the breach is contained, investigators define what’s affected. Was only one server hit? Or was the entire network touched? A data breach investigation service needs this clarity before digging deeper. Teams also align with mandatory regulations, GDPR, HIPAA, CCPA, and more. Legal teams rely on investigators to ensure proper reporting and compliance.
This stage is where we center the mission: identify the incident’s depth, the attackers’ goals, and the business impact. Without clear scope, investigations take longer and cost more.
Digital forensics is all about precision. Investigators collect logs, analyze network traffic, capture system images, and document each step. A data breach investigation service uses structured, repeatable methods like forensic imaging, chain of custody tracking, and forensic artifact collection.
Every action must be defensible. If the case reaches court or regulatory review, investigators need to show exactly how evidence was preserved. That’s why at MSSP Security we maintain strict forensic readiness standards as part of our service.
This is where the story unfolds. A strong data breach investigation service rebuilds the attacker’s timeline. Investigators determine the initial point of entry, what tools were used, and how controls were bypassed. This stage often depends on forensic analysis to uncover hidden paths, artifacts, or signs of deeper compromise.
SERP descriptions mention “forensic timeline reconstruction” and “malware analysis” as core elements.
In our own cases, we’ve seen attackers hide inside logs, drop backdoors, or disguise exfiltration paths. Detailed analysis shows whether data was viewed, copied, or exfiltrated. It also reveals whether the threat actor is still inside the network.
Every breach has a reason. Sometimes it’s a missing patch. Sometimes it’s stolen credentials. Sometimes it’s an overlooked misconfiguration. A data breach investigation service identifies the weakness that allowed the breach to happen. According to SERP data, root cause analysis is a core function because it guides long-term prevention.
At MSSP Security, we share findings in plain language. No complex jargon, just clear answers teams can act on.
After the root cause is known, teams move to fix the damage. They patch systems, remove malware, harden endpoints, strengthen network segmentation, tighten access controls, and improve monitoring. A data breach investigation service helps guide these decisions, ensuring every gap is closed.
Prevention matters just as much. That includes employee training, phishing awareness, vulnerability management, and better alerting. We’ve seen organizations reduce repeat incidents dramatically by improving visibility and proactive detection.
Clear reporting brings closure. Investigators prepare a timeline, evidence summary, and recommendations. A data breach investigation service also helps businesses communicate internally and externally. Regulators often require formal notifications. Customers sometimes need reassurance.
A strong report explains what happened without fear-based language. Good communication restores trust.
Credits: Lean Security – Web and Mobile Applications Security Assurance
A data breach investigation service brings experience that most internal teams lack. These investigators understand attack patterns, forensic methods, and compliance requirements. They know where attackers hide. They know how to collect evidence properly.
They also use advanced tools, SIEM, XDR, log analysis platforms, and forensic toolkits, to gather and correlate data quickly. Threat intelligence helps identify attacker groups and their methods.
Compliance support is a major benefit. Businesses need guidance on GDPR, HIPAA, PCI, and other requirements. Investigators make sure reporting happens correctly to avoid penalties.
Many providers also offer proactive threat hunting. This means looking for hidden threats that haven’t activated yet. According to SERP info, proactive measures reduce the risk of repeat breaches.
At MSSP Security, we see data breach investigation as part of a bigger mission: making organizations resilient.

Picking the right provider matters. Businesses should consider expertise, certifications, response times, communication style, and industry experience. Some organizations prefer a DFIR retainer because it guarantees fast access to specialists when every second counts. A good provider answers questions directly:
Third-party reviews and case histories matter too. But the most important factor is trust. Organizations must feel confident that the provider can handle sensitive data.
MSSP Security often becomes the first call because we combine incident response, digital forensics, threat intelligence, compliance support, and long-term monitoring. We don’t just investigate, we help businesses get better. [2]
Stronger controls prevent many breaches. Access policies, encryption, MFA, and patch management form a solid baseline. Continuous vulnerability assessments help catch risks early.
Human error is still a major cause of breaches. That’s why cybersecurity awareness training is essential. Simple habits, like spotting phishing emails, reduce risk dramatically.
A tested incident response plan is the final piece. It prepares teams for real-world pressure. Tabletop exercises help employees practice their roles. A data breach investigation service relies heavily on good preparation, and organizations with a plan always recover faster.
A team will look at digital forensics and incident response steps right away. They check digital evidence preservation, breach containment, and basic cyber incident analysis. They may run forensic triage to see what happened and use log analysis to spot early clues. Their goal is to keep your data safe and stop more damage fast.
Investigators use root cause analysis, forensic artifact collection, and network forensics to track how the attack began. They study the incident timeline creation, attack vector identification, and threat intelligence.
They may use forensic imaging and endpoint forensics to see what the attacker touched. This helps them explain how the breach started in clear terms.
Teams gather forensic evidence collection and digital evidence analysis from devices, servers, and cloud forensics sources. They follow chain of custody rules so nothing gets changed. They also check data integrity verification, data exfiltration analysis, and behavioral analytics. All of this helps them show what was taken and how the attackers moved.
They use forensic timeline reconstruction, breach impact assessment, and threat hunting to see the full path. They check SIEM integration alerts, XDR correlation, and SOAR orchestration to track movement. They also study insider threat detection and breach severity grading. This helps you understand the size of the event in simple terms.
A strong data breach investigation service isn’t just about fixing what went wrong. It’s about building a system that helps businesses stay calm, act fast, and protect what matters, every single time.
That’s why our team at MSSP Security focuses on giving organizations clear guidance, evidence-driven insights, and practical steps that keep operations steady even under pressure.
If you want support that cuts noise, reduces tool sprawl, and brings real clarity to your security stack, you can join us here.