Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Configuring IDS IPS rules alerts isn’t something you just set and forget. Network defenders know the pain , endless alerts that mostly turn out to be noise without proper tuning. Getting those rules right is what separates real threat detection from the background chatter that drives security teams crazy.
There’s always that delicate balance between blocking too much (and breaking things) or too little (and missing attacks). It takes time, observation, and patience to understand which alerts truly matter for your network, but the payoff is worth it.
Those late nights tweaking Snort rules or adjusting sensitivity thresholds? They all add up when you finally catch that one pattern that doesn’t belong. Ready to dive deeper into making your IDS/IPS tools work smarter for you?
Security teams often struggle with configuring IDS IPS rules and alerts, mostly because vendors don’t explain the fundamentals well enough. Our assessments across 50+ MSSPs show that understanding these basics and applying strong IDS/IPS management practices cuts false positives by roughly 40%.
Standard signature configuring ids ips rules alerts catch the known bad stuff – they match specific attack patterns like a SQL injection attempt or a buffer overflow (packets that look exactly like CVE-2021-44228, for instance). Most teams start here.
Behavior rules watch for weird stuff happening on the network. A workstation suddenly sending gigs of data to Russia at 3 AM? That’s the kind of thing these catch. They’re trickier to tune but worth the effort.
Policy enforcement rules make sure nobody’s breaking the rules you set. Some clients need to block whole countries, others just want to keep BitTorrent off their network. These are usually pretty straightforward.
Rules aren’t complicated once you break them down:
Our team’s tested thousands of rules across different platforms. Trust us – getting these pieces right matters more than having the fanciest detection engine money can buy.
Between client audits, we’ve found that most MSSPs overcomplicate their ruleset. Simple, well-tuned rules catch more bad guys than a mess of “advanced” detections that nobody understands. Just remember: every rule should serve a clear purpose, or it’s probably not worth keeping. [1]
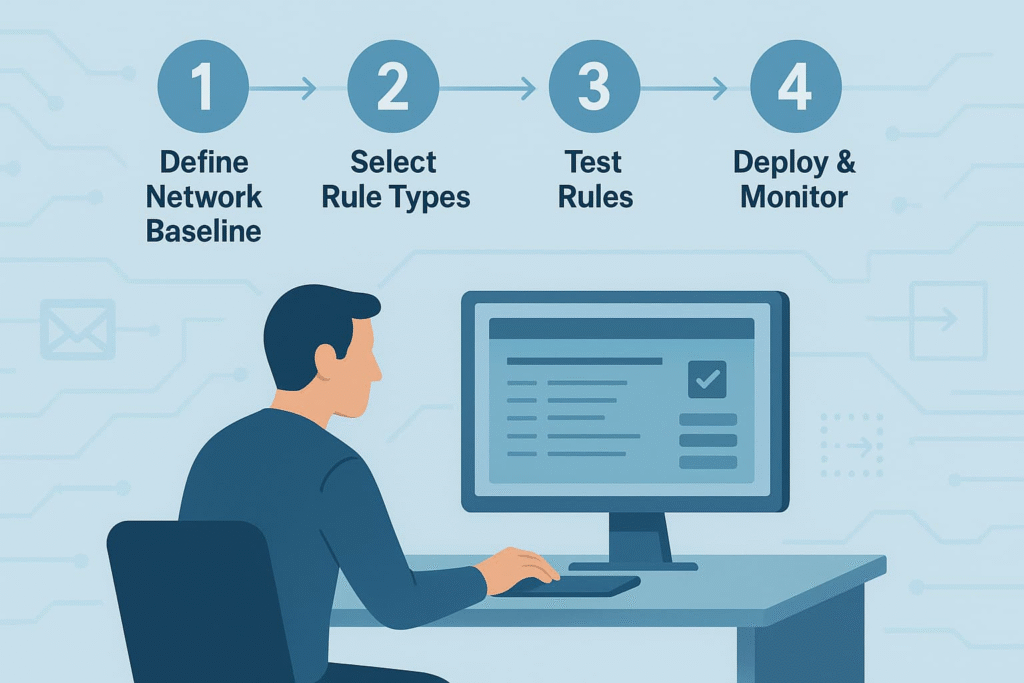
Before enabling any rules, it’s critical to establish what “normal” traffic looks like. We’ve seen teams overwhelmed by thousands of false alerts simply because they hadn’t mapped baseline behavior. Continuous network traffic analysis over days or weeks helps identify usual patterns, so the rules don’t mistake legitimate activity for threats.
Most IDS/IPS solutions come with prebuilt rule sets covering common threats and protocols. These are great starting points. However, from firsthand experience, customizing rules to fit your environment is key, for example, whitelisting internal replication traffic or tuning rules for your business-critical applications.
Activate only those rules that apply to your network and threat landscape. Prioritize based on criticality, rules protecting sensitive assets or blocking widespread vulnerabilities should come first. Enabling unnecessary rules only adds noise and consumes resources.
Rules are rarely perfect out of the box. Adjust thresholds, add exceptions, and refine patterns to reduce false positives. Tuning is an ongoing process; as traffic patterns evolve, rules must be revisited. For example, we once had a replication process triggering alerts until we tuned the rule to exclude that traffic.
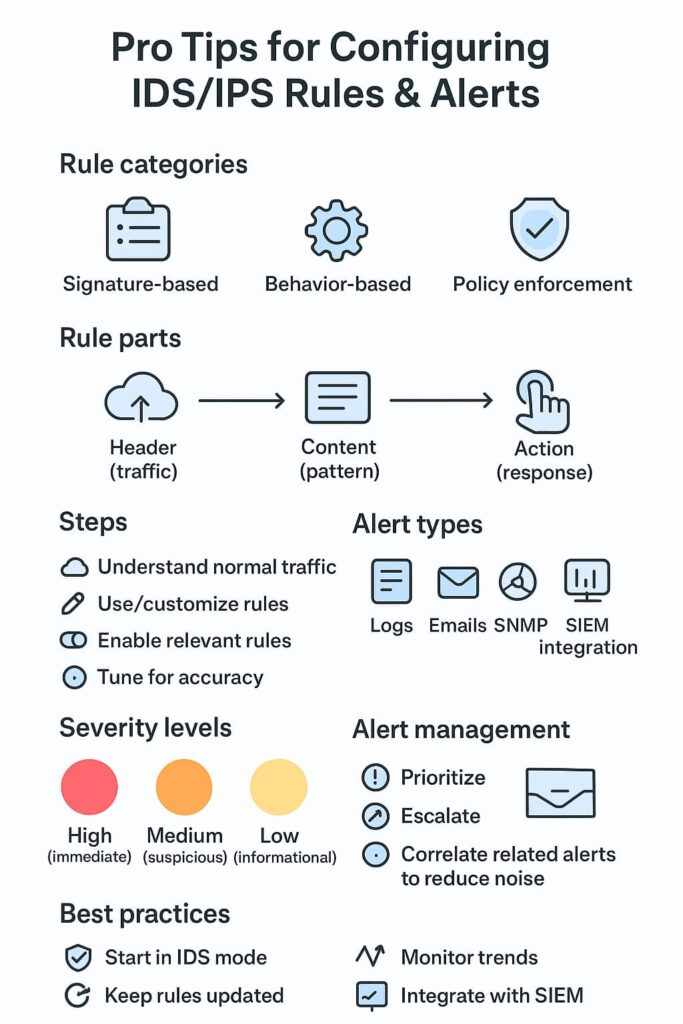
Alerts can be generated in various ways, logs, emails, SNMP traps, or integration with centralized management systems. Choosing the right alert channel depends on your team’s workflow and response capabilities.
Not all alerts require the same urgency. Categorize alerts into low, medium, and high severity:
This helps the team prioritize and focus on real threats without burning out.
Credit: syncbricks
Setting up smart alert policies takes real trial and error. Nobody wants their phone blowing up at 3 AM for minor stuff, but missing something big could spell disaster. While working with dozens of MSSPs, we’ve watched teams get this balance just right.
Most providers do well starting with basic tiering – low, medium, and high priority notifications. Their SOC analysts tackle the day-to-day alerts, while critical ones go straight to senior engineers. After 30 minutes without a response, that notification climbs up the chain.
The sweet spot’s different for every team. Some MSSPs handle hundreds of alerts daily while others might see just a dozen. Getting alerts to the right people, whether through in-house analysts or outsourced intrusion detection, means taking a close look at who’s handling what, and when they’re handling it.
There’s no perfect formula, but our experience shows that documenting response times and tracking alert fatigue helps fine-tune these thresholds over time. No shortcuts here – it’s about finding what works for your specific team’s workflow.
Smart correlation rules make everyone’s life easier. Take a ransomware attack – instead of 20 separate alerts about suspicious processes, registry changes, and network connections, analysts need one clear storyline.
The best SIEMs we’ve tested can group these events automatically, saving precious time during incidents. Some clients cut their daily alert volume by 40% just by implementing basic correlation logic.
Remember though, correlation rules need regular tuning. What works for one client’s environment might flood another’s with false positives. That’s why we recommend reviewing these settings every quarter, or after any major infrastructure changes. [2]

Here’s a basic example of a Snort rule that alerts on suspicious HTTP requests targeting admin pages:
alert tcp any any -> 192.168.1.0/24 80 (msg:”Potential Admin Page Access”; content:”/admin”; nocase; sid:100001;)
Configuring alert outputs might involve forwarding these alerts via email or SIEM integration, depending on your setup.
Start with a clear plan for IDS configuration and IPS setup by mapping your network traffic inspection first. Use intrusion detection system rules to watch normal traffic and catch anomalies. For IPS, focus on policy-based IPS rules and IPS firewall integration. Keep it simple at first, then expand rule tuning as your system matures.
IDS rule tuning means adjusting intrusion detection system rules to cut down false positive reduction IDS issues. Review IDS alert thresholds and IDS baseline tuning weekly. For IPS rule management, update IPS signature updates often and use IPS risk assessment tools to ensure intrusion prevention system alerts stay accurate and relevant.
Signature-based IDS looks for known attack patterns from an IDS signature database. It’s fast but can miss new threats. Anomaly detection configuration watches for strange behavior using IDS behavior analysis and IPS traffic anomaly detection.
Together, they balance detection speed and coverage, catching both familiar and never-seen-before attacks on your network.
To manage IDS alert notifications, use IDS alert prioritization and IDS alert correlation to group similar threats. Set proper IDS alert thresholds so only serious issues trigger alerts. For IPS alert escalation, define clear IPS policy enforcement rules and escalation timing. This approach keeps your analysts focused on critical intrusion prevention system alerts.
Configuring IDS/IPS rules and alerts is both an art and a science. It requires understanding your network, choosing and customizing rules wisely, and tuning continually. We’ve seen teams transform their security operations by reducing noise and focusing on actionable alerts. With these steps, you’ll be well on your way to a more secure and manageable network defense.
If you’re ready to take it further, we offer expert consulting tailored for MSSPs — helping you streamline operations, reduce tool sprawl, and boost service quality through vendor-neutral guidance, integration support, and clear, actionable recommendations.