Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

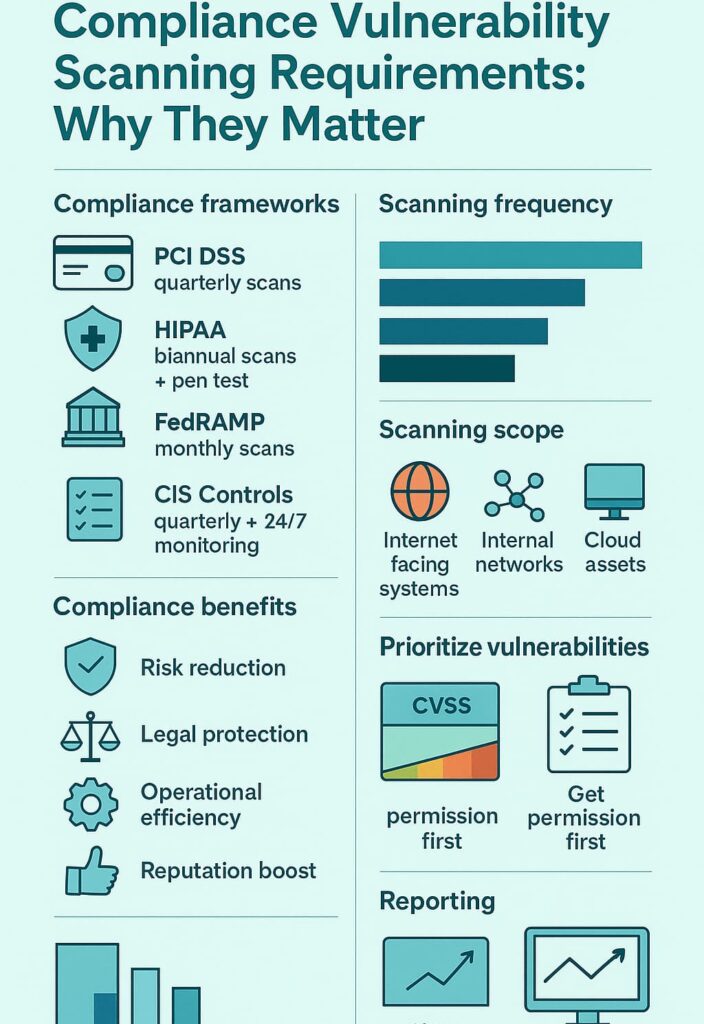
Let’s get real about vulnerability scanning, you can’t fix what you don’t look for. Most places treat these scans like a chore, something to check off their to-do list. But here’s the thing: PCI DSS doesn’t care about your excuses, they want those quarterly scans done, period. HIPAA’s more vague about it, but they’ll still come knocking if you slack off.
Think of these rules like having a night watchman, would you trust one who only checks the doors once a year? The numbers tell the story: companies that suck it up and do quarterly scans catch 60% more of the nasty stuff than the yearly scanners. That’s not just statistics, that’s the difference between catching a hacker at the door or finding them in your network.
Want the real story behind these requirements? Stick around.

Look, nobody really wants to deal with PCI DSS, but they’re not messing around, scans every quarter, inside and out, no wiggle room. Credit card companies got burned too many times, so now they want proof your systems aren’t leaking card numbers like a broken faucet. A solid vulnerability management services guide lays out how to track every system and scan every single place those numbers might be hiding.
HIPAA’s more relaxed about it (which is kind of weird when you think about it). Two scans a year, one pen test, that’s their magic number. Pen testing’s great and all, but regular scans are like having a doctor check your vitals. You want to catch that fever before you’re stuck in bed.
The big shots each want their own thing:
FedRAMP’s extra paranoid because, well, it’s government stuff. Can’t blame them when national security’s on the line.
Let’s get real, internal policies aren’t just CYA paperwork. Nobody (and we mean nobody) wants to be that guy who killed the payment system during Black Friday because they didn’t get approval first. SOC 2 doesn’t care when you scan, but they’ll crawl up your back if you’re not fixing problems quick. Smart companies turn this into a routine, like clockwork. [2]
Your tools better not suck, period. Old scanners miss new threats, it’s like trying to catch modern hackers with 1990s tech. Sure, CVSS helps sort out what matters (even though everyone fights about what counts as “critical”). But here’s the truth, if you’re not automating, you’re already behind. Because no admin’s gonna roll out of bed at 3 AM to run a manual scan, but hackers don’t sleep.

Let’s face it, nobody’s thrilled about fixed scanning schedules, but skipping them isn’t an option. These days, quarterly’s the minimum to keep auditors happy. Some places get antsy and scan monthly, while the really jumpy ones (usually finance guys) scan weekly.
Others move toward continuous vulnerability assessment to catch issues in real time. And when the dev team drops a big update? Yeah, that means extra scans. Just like double-checking the stove’s off before vacation, better safe than sorry.
If it’s got an IP address, it needs scanning:
Skip one, and you might as well email hackers your network diagram.
A report’s useless if it reads like a quantum physics textbook. Half the battle’s making sure both computers and humans get it, because sooner or later, someone’s gotta explain those red flags to people who think RAM is a sheep. Teams need solid metrics, like “we killed 15 critical bugs this month.” That’s how you show whether you’re winning or just running in circles.
Running surprise scans is about as smart as juggling chainsaws in the server room. Get the paperwork signed, period. Know which compliance rules matter and make your scans match. Trust me, it beats explaining to your boss why the payment system crashed during a “routine” scan. Plus, when auditors show up (and they always do), you won’t be scrambling for documentation like a student who forgot about finals.
Credits: SecurityMetrics, Inc.
Early detection of vulnerabilities is a big win. Compliance scanning helps identify exploitable flaws before attackers find them. Continuous monitoring keeps risk levels in check and aids in incident prevention. Together, these values create a robust defense posture.
Scanning reduces legal and financial penalties by minimizing non-compliance risks. It also safeguards sensitive data, meeting the strict demands of regulations like HIPAA and PCI DSS. We find that organizations taking these values seriously can avoid costly breaches and fines.
Automated scanning delivers consistent and scalable assessments. Remediation tracking documents fixes in an auditable way, simplifying compliance reporting. This efficiency frees teams to focus on strategic security improvements.
Trust builds when customers and partners see an organization committed to security. Compliance excellence differentiates businesses in competitive markets. Maintaining strong scanning practices reinforces this advantage.
Compliance scans verify adherence to policies and regulations. They ensure configurations, access controls, and encryption meet required standards. Vulnerability scans identify technical weaknesses regardless of policy. Organizations often rely on managed vulnerability management to bring these processes together. Both scans serve distinct but complementary purposes.
When combined, compliance and vulnerability scans form a comprehensive security program. Integrating findings into broader risk management strategies amplifies their impact. We’ve seen teams improve prioritization and resource use by merging these insights.
Compliance assurance avoids fines and legal trouble. Security enhancements from vulnerability scanning improve defense against attacks. Together, these values deliver measurable benefits that sustain business continuity.
Up-to-date scanning tools are non-negotiable. Vendors release new vulnerability signatures daily, so frequent updates are crucial. Prompt remediation and thorough documentation round out effective vulnerability management.
Internal vulnerability scans focus on devices, servers, and applications inside the corporate network, identifying risks like outdated software or poor configurations. External vulnerability scans test systems exposed to the internet, such as public-facing websites and cloud services.
Many compliance frameworks like PCI DSS and SOC 2 require both types. Combining internal vulnerability scans with external vulnerability scans ensures complete visibility for vulnerability management and accurate vulnerability reporting.
Scanning frequency requirements vary depending on the compliance framework. PCI DSS vulnerability scanning often requires quarterly vulnerability scans and monthly vulnerability scans after major changes. HIPAA vulnerability assessments and FedRAMP vulnerability scanning may require continuous vulnerability monitoring.
A defined vulnerability assessment cycle helps set timelines for vulnerability scan validation, vulnerability remediation, and secure configuration scanning to meet ongoing compliance vulnerability scanning standards.
Authorized vulnerability scanning prevents disruptions and ensures legal protection. Many organizations set up a vulnerability scan authorization process to get approval before running network vulnerability scanning, cloud vulnerability scans, or application vulnerability scanning.
This process helps define the vulnerability scanning scope, comply with regulatory vulnerability scanning rules, and create proper vulnerability scan documentation. It also ensures privileged credential scanning is handled securely during vulnerability detection and enumeration.
CVSS scoring helps classify threats found during network security scans and host vulnerability scanning. By linking scores to vulnerability database updates and vulnerability detection signatures, teams can prioritize vulnerability remediation.
This approach supports vulnerability risk assessment and vulnerability risk prioritization, guiding a clear vulnerability remediation timeline. CVSS scoring is also vital for vulnerability scan reporting, as many compliance scan tools require detailed reporting formats to meet vulnerability reporting requirements.
A compliance scan checks whether systems meet defined vulnerability scanning compliance standards, such as SOC 2 or FedRAMP vulnerability scanning frameworks. It focuses on regulatory vulnerability scanning controls and produces vulnerability scanning evidence for audits.
A vulnerability scan, however, is broader, aimed at discovering issues using vulnerability scanning tools and vulnerability discovery methods. Understanding compliance scan vs vulnerability scan helps organizations design a vulnerability monitoring program and align vulnerability assessment policies.
Compliance vulnerability scanning protects sensitive data and keeps you aligned with regulatory demands. It sets clear rules for scan frequency, scope, and remediation using trusted tools and CVSS scoring. Done right, it prevents breaches, cuts legal risks, and builds customer trust. Strengthen your scanning program with real-time threat modeling and automated risk analysis.
Join MSSP Security for expert consulting to streamline operations, cut tool sprawl, and improve service quality.