Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

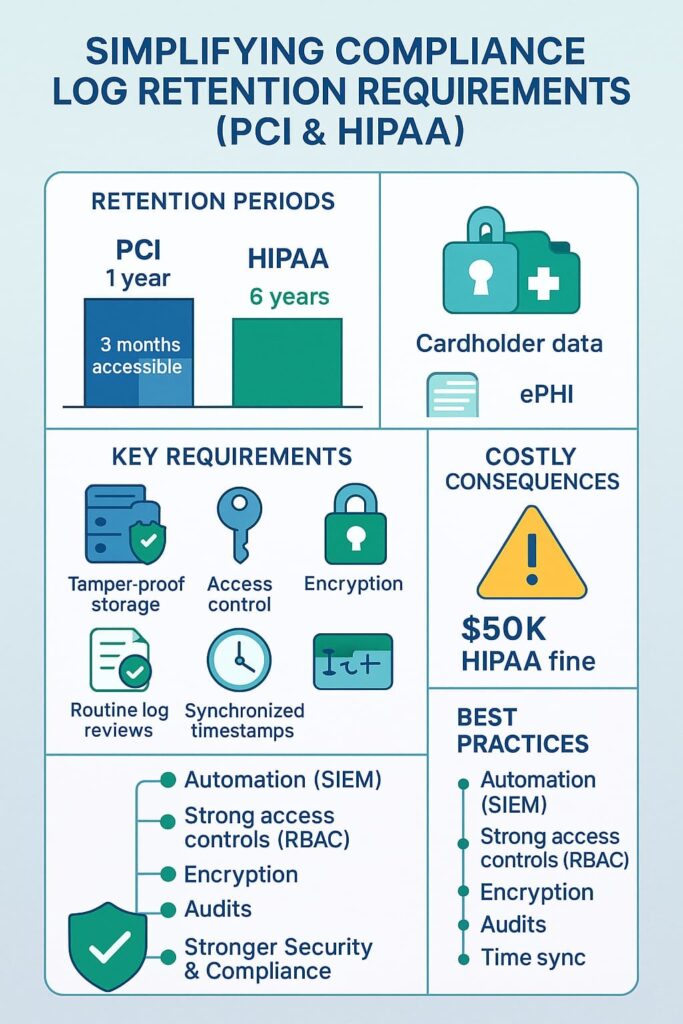
Data logs aren’t just dusty records taking up server space, they’re your safety net when things go wrong. Most businesses scramble with the basics: PCI DSS wants those logs kept for a year (3 months right at your fingertips), while HIPAA won’t let you off the hook for 6 whole years with patient records.
Look, these rules exist because someone, somewhere, lost critical data and couldn’t trace what went wrong. Pretty messy stuff. We’ve seen enough horror stories of companies caught without proper logs during audits.
Stick around, we’ll cut through the confusion and show you what to simplify compliance log retention requirements (PCI HIPAA)

Missing logs during an incident response can spell disaster. Just last month, our team had to tell a client they couldn’t track down who accessed sensitive patient records, their logging system only kept 30 days of history. Price tag for that oversight? A cool $50,000 in HIPAA fines.
We’ve watched MSPs struggle through audits without proper documentation, scraping together whatever traces they could find. It’s painful to watch, especially since most violations stem from basic logging mistakes. These aren’t just paper trails, they’re the backbone of incident investigations, showing exactly who touched what data and when.
Organizations can’t afford to treat logging as an afterthought. When regulators come knocking (and they will), those detailed records become your shield. Missing logs don’t just mean fines, they mean lost customers, damaged reputations, and countless hours spent doing damage control. Our audits consistently show that robust logging could’ve prevented most compliance nightmares.
Credit: CodeLucky
Working with dozens of MSSPs, we’ve seen firsthand how proper log management forms the backbone of cardholder data protection. After evaluating countless solutions, here’s what your MSSP needs to implement:
Every system touching card data must maintain logs for at least 12 months, no exceptions. The most recent 3 months of logs need instant availability for investigations.
Security teams should capture:
Our audits consistently show that raw logs need ironclad protection. Some proven approaches we’ve validated:
Through years of product evaluation, we’ve found that SIEMs dramatically improve visibility, but only with proper tuning. A mid-sized MSSP we worked with caught a potential breach within 15 minutes using centralized logging, compared to their previous 72-hour detection window.
When selecting monitoring solutions for clients, focusing on unified log management has consistently delivered the strongest results. The right setup means security teams spot patterns before they become problems.
We’ve worked alongside healthcare providers to automate log retention and review, reducing manual workloads while ensuring compliance readiness. Encrypting logs and enforcing strict access protocols is non-negotiable to prevent breaches and maintain patient privacy.
Many teams now rely on outsourced log collection and retention solutions to simplify HIPAA compliance and guarantee long-term audit readiness.
We’ve worked alongside healthcare providers to automate log retention and review, reducing manual workloads while ensuring compliance readiness. Encrypting logs and enforcing strict access protocols is non-negotiable to prevent breaches and maintain patient privacy. [1]
| Feature | PCI DSS | HIPAA |
| Retention Period | 1 year (90 days accessible) | 6 years |
| Data Focus | Cardholder data | Electronic Protected Health Information (ePHI) |
| Key Requirements | Tamper-proof logs, daily reviews | Regular log reviews, access controls, encryption |
To meet these rigorous requirements while managing the volume and complexity of logs, here are some best practices we’ve found invaluable:
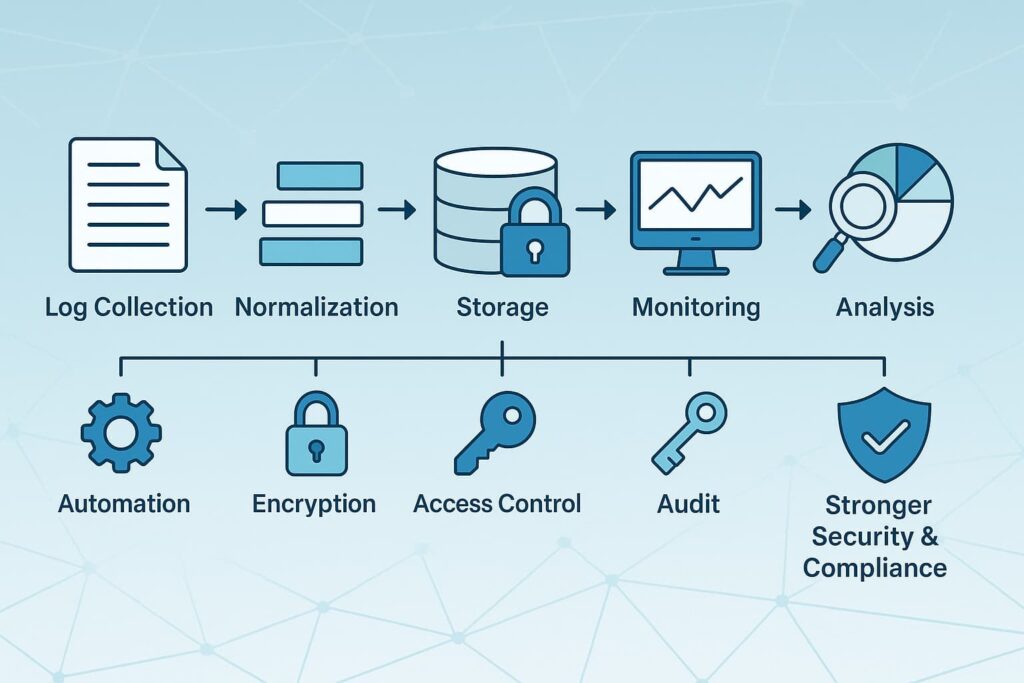
Manual log review is time-consuming and error-prone. We recommend leveraging SIEM systems or MSSP Security’s managed services to automate collection, analysis, and alerting. Automation ensures timely detection and consistent compliance through centralized log management practices that strengthen visibility across systems.
Logs are sensitive, they often contain personal or financial data. Restricting access to only authorized personnel prevents insider threats and tampering. Role-based access control (RBAC) is a practical way to enforce this.
To protect log integrity and confidentiality, encrypt logs both at rest and during transmission. This guards against unauthorized access and meets compliance log encryption requirements.
Regularly audit your log retention policies and procedures. This helps identify gaps, ensures logs are complete, and verifies retention timelines are followed. [2]
Accurate timestamps across your environment are essential for event correlation during forensic analysis. Use NTP or similar protocols to keep clocks in sync.
Implement and test incident response plans that incorporate log review and monitoring. This ensures your team is prepared when incidents occur.
Educate your teams about the importance of log retention and security. Awareness reduces human error and promotes a culture of compliance.
Clear policies around who can access, modify, or delete logs reduce risk and increase accountability.
Complying with PCI DSS and HIPAA log retention requirements is challenging but vital. A solid retention strategy goes beyond ticking compliance boxes, it strengthens resilience, speeds incident response, and protects sensitive customer data.
Partnering with a trusted MSSP Security provider simplifies the process through centralized logging, real-time monitoring, and automated reviews that keep you compliant and secure. Don’t wait for an audit or breach to act.
Start building your robust log retention and monitoring framework today, with MSSP Security and ensure long-term protection, efficiency, and peace of mind for your organization and customers.