Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Let’s face it, nearly everyone’s cloud security is a mess right now. Last year, 95% of businesses got hit with cloud breaches, and fixing those holes wasn’t cheap. Whether you’re running stuff on AWS, keeping it in-house, or mixing both, each setup’s got its own security headaches.
Most IT teams are stuck using security tools from 2010, hoping nothing breaks. But there’s a better way, Cloud Workload Protection Platform (CWPP) management catches problems before they blow up.
Stick around to see how real CWPP works in the trenches, minus the fancy sales pitch.

The problem hits close to home, cloud workloads keep multiplying across VMs, containers, and serverless setups. We’ve watched clients juggle apps between AWS, Azure, and their own data centers, making security a real headache. Our audits show most monitoring tools can’t keep up when workloads spin up and vanish in minutes.
Security teams often miss the gaps in cloud provider coverage. Sure, AWS handles infrastructure security, but everything running on top? That’s on you. We’ve pulled all-nighters helping MSPs patch holes after attackers snuck through outdated configs. Some breaches could’ve been caught early if someone had looked in the right places.
Getting ahead means picking tools built for cloud-native ops. CWPP management works because it watches 24/7, catches vulnerabilities automatically, and fits right into existing workflows, much like effective cloud security monitoring that keeps an eye on fast-moving workloads in real time.
Over years of product testing, we’ve seen it transform struggling security teams into proactive defenders. No more hoping nothing breaks, now they catch issues before users notice.
Credit: Value Aligners
No security team wants to play whack-a-mole with system holes. After testing dozens of platforms, automated scanning stands out as the backbone of solid protection. MSPs need tools that check everything, from basic VMs to fancy serverless setups. Building these scans into development pipelines catches problems before they hit production servers.
Raw scan data doesn’t help much though. We learned this lesson helping clients drown in vulnerability alerts. Smart teams rank issues by how much damage they could do to critical systems.
Our tests show automated patch management cuts down fix times from weeks to hours. Last month, one client caught three zero-days because their CWPP flagged unusual patterns during routine scans. [1]
Real-time monitoring is key. Behavioral analytics help detect anomalies, like unusual process launches, privilege escalations, or lateral movement attempts, that might signal attacks in progress. Coupled with automated response capabilities, such as isolating affected workloads or triggering alerts, threat detection becomes proactive rather than reactive.
We integrate threat intelligence feeds to enrich detection accuracy. This helps correlate suspicious activity with known attack patterns, enabling faster incident response. Automation here is a lifesaver; it reduces alert fatigue and ensures critical threats are addressed promptly.
Misconfigurations pose a significant risk in cloud environments. CWPP management includes enforcing secure configurations and maintaining compliance with industry standards like CIS Benchmarks, PCI DSS, HIPAA, and GDPR. Automating compliance audits and generating detailed reports help security teams demonstrate adherence to regulators.
Regularly reviewing and updating security policies is essential. Cloud environments evolve quickly, and static policies quickly become outdated. Our approach is to combine continuous compliance monitoring with policy enforcement to minimize drift and maintain a strong security posture.
Access management is a frontline defense. Implementing least privilege and zero trust models ensures users and systems have only the permissions they absolutely need. Role-based access control (RBAC), multi-factor authentication (MFA), and microsegmentation techniques isolate workloads, limiting the blast radius of any compromise.
We’ve found microsegmentation especially effective in containing lateral movement within hybrid environments. By segmenting networks into smaller, manageable zones, it’s easier to enforce security controls and detect suspicious activity.
CWPP management cannot operate in isolation. Integrating with SIEM solutions provides a unified view of security events, enhancing threat detection and investigation.
Connecting with managed cloud security monitoring and Cloud Security Posture Management (CSPM) tools helps close security gaps at the infrastructure level, ensuring all environments are tracked and protected.
APIs enable automation and seamless workflow integration, reducing manual overhead and improving response times. As part of our MSSP Security offerings, we emphasize these integrations to provide clients with consolidated dashboards and actionable insights.
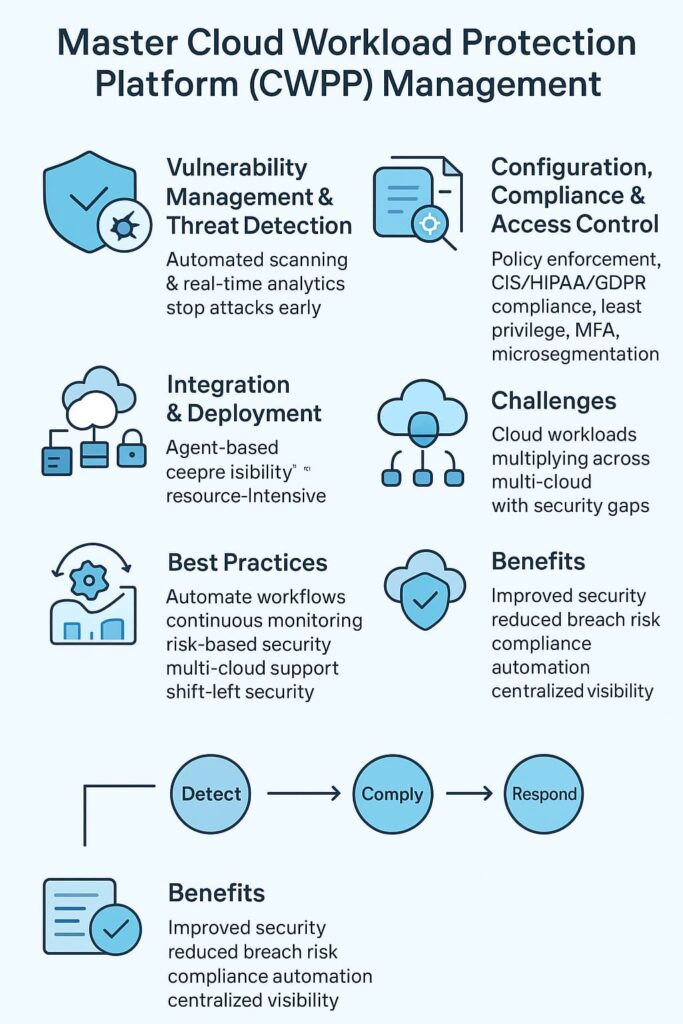
Agent-based solutions install lightweight software agents on each workload. They provide deep visibility into workload behavior, network traffic, and configurations in real time. This granular insight improves detection accuracy and allows customized security policies tailored to specific workloads.
However, agents consume resources and require ongoing management. In some environments, this can impact performance or introduce complexity. From our experience, agent-based CWPPs work best when deep control and customization are required, especially in sensitive or high-compliance workloads.
Agentless CWPPs rely on cloud provider APIs and hypervisor integrations for monitoring without installing agents. This approach simplifies deployment, reduces resource consumption, and scales well across large, dynamic cloud estates.
The tradeoff is sometimes reduced visibility or delayed detection, as agentless models might miss certain runtime behaviors. We often recommend agentless solutions for early-stage cloud adoption or when operational simplicity is paramount.
Embedding CWPP management into your organizational culture is critical. Security teams need to stay adaptive, continuously updating policies and tools to counter evolving threats. We advocate for a security-first mindset that treats CWPP management as a core business function rather than an afterthought. [2]

Managing a CWPP isn’t just about tools, it’s about people, processes, and culture. We’ve helped organizations transform their cloud security posture by integrating CWPP capabilities into DevOps pipelines, automating workflows, and providing centralized visibility.
Our MSSP Security expertise shows that continuous improvement and collaboration across teams yield the best results. Leveraging outsourced cloud security posture services can also help organizations stay compliant and adaptable without stretching internal resources. When security is woven into daily operations, workloads remain resilient, compliant, and secure.
Cloud workload protection platform management strengthens workload security by combining threat detection, vulnerability management, and continuous compliance.
It helps spot risky configurations, automate patching, and monitor runtime behavior across cloud environments. This approach keeps workloads safe from intrusion, data loss, and configuration errors, especially in hybrid or multi-cloud setups.
Automation simplifies CWPP management by handling routine security tasks like vulnerability scanning, policy enforcement, and incident detection. It reduces manual errors, speeds up breach prevention, and ensures consistent compliance across workloads.
With security automation and orchestration, teams can focus on threat hunting and cloud security strategy instead of repetitive work.
CWPP tools track configuration compliance and create real-time reports for audits. They align with cloud security standards, detect policy violations, and generate alerts when workloads drift from security baselines.
This continuous compliance approach helps organizations meet regulations, improve visibility, and strengthen cloud security posture without heavy manual oversight.
Workload visibility helps security teams understand what runs inside their cloud infrastructure. CWPP management tools offer workload discovery, runtime protection, and cloud asset management.
With clear visibility, organizations can identify unprotected workloads, enforce zero trust architecture, and manage cloud operations security more effectively across containers, VMs, and serverless apps.
Effective Cloud Workload Protection Platform (CWPP) management requires a balanced approach that integrates automation, compliance, and continuous monitoring.
By prioritizing vulnerability management, threat detection, and access control, you can safeguard workloads from today’s and tomorrow’s threats. Managed security services simplify this process, offering expertise and advanced tools without added complexity.
Partner with our experts to streamline operations, reduce tool sprawl, and enhance service quality. With 15+ years of experience and 48K+ successful projects, we help MSSPs optimize stacks, select vendors, and build security strategies aligned with business goals.