Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Your tool needs to run non-stop (cause attackers don’t take coffee breaks), work with whatever security stuff you’ve already got (without needing a PhD to set it up), and not flood your team with garbage alerts about problems that don’t exist. Half the companies out there probably don’t even realize their scanner’s missing critical bugs, until something breaks or gets hacked.
After seeing too many teams struggle with the wrong tools, it’s pretty obvious what counts: can it scan everything daily without breaking things? Does it spot actual threats instead of crying wolf? Will it play nice with your current setup? That’s what you gotta figure out before signing any checks.
Think of vulnerability scanning like checking doors and windows, except there’s thousands of them, and new ones keep popping up. Most networks need constant watching, not just weekly checkups.
The best tools scan networks round-the-clock, and a continuous vulnerability assessment service can help ensure problems are caught before they blow up into full-scale disasters. Sure, scheduled scans still work for some places, but they’re kind of like locking the barn door after the horse got out. [1]
Active scanning’s pretty straightforward, it pokes and prods systems to find weak spots (sometimes causing network hiccups, but that’s life). Passive scanning’s more subtle, just watching traffic flow for weird stuff. Smart teams use both, cause why not cover all bases?
Here’s what actually matters for scanning:
Running both types of scans might seem like overkill, but networks are messy and threats are sneaky. You’d be surprised what slips through with just one method.

Let’s be real, not every hole in the wall needs fixing right now. Good tools help figure out what matters most, using something called CVSS scores (basically a 1-10 scale of how bad things could get). They also look at how likely someone’s gonna actually try to break in through that particular hole.
Context matters too. A vulnerability on your company’s website is way worse than one on Bob’s test machine in the basement. Smart tools factor in stuff like where the problem is, what it might cost the business, and how hard it’d be to fix.
Look for tools that can:
This way, your team’s not running around like chickens with their heads cut off, they’re fixing what matters.
Nobody wants to spend their days clicking “update” a thousand times. But letting machines run wild with patches isn’t smart either. Most teams need both, automated patches for the simple stuff, and careful human touches for the tricky parts. The right managed vulnerability management solution handles both without making a mess, ensuring updates roll out smoothly and safely. [2]
If your patch tool can’t talk to your ticket system, you’re in for a world of hurt. The best setups connect everything, when a vulnerability pops up, it automatically creates a ticket, assigns it to the right person, and tracks it till it’s fixed. ServiceNow and JIRA users especially need this kind of harmony.
These features actually matter:
Credits: CISO Tradecraft
Security tools that don’t talk to each other are about as useful as a screen door on a submarine. Your vulnerability management services guide can help you choose scanners that integrate seamlessly with your SIEM (that’s where all your security alerts live) and your EDR (the thing watching your endpoints). When they work together, you see the whole picture, not just pieces.
These days, code moves fast. Really fast. Your vulnerability tool better keep up and fit right into those pipelines. It needs to spot problems while developers are still coding, not after everything’s built and deployed.
Nothing’s worse than scrambling before an audit. Good tools keep compliance records updated automatically. They track what vulnerabilities showed up, what got fixed, and when, all the stuff auditors love to see.
Integration must-haves:
Remember, a tool that plays well with others saves more headaches than one with fancy features that lives in its own world.
Even the most powerful vulnerability management platform fails if it’s too complex for users. We’ve learned that an intuitive user interface and role-specific dashboards encourage adoption across security, IT, and development teams. Easy navigation and clear visualization reduce errors and speed decision-making.
Deployment ease and training requirements matter too. A tool that installs with minimal hassle and has a gentle learning curve helps your team get up to speed fast. This is especially critical in diverse environments where users have varying expertise.
Usability aspects to consider:
Choosing a tool that fits your team’s workflow boosts consistent vulnerability management practices.
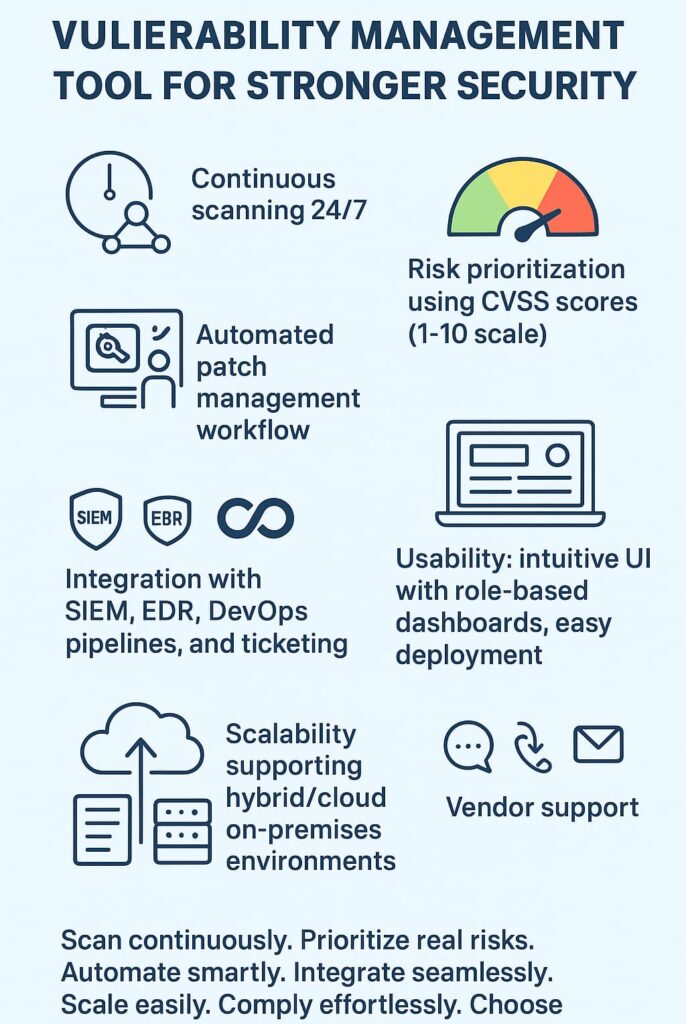
Our networks aren’t static; they grow and evolve. A vulnerability management tool must handle increasing asset volumes without slowing down or missing scans. Support for hybrid environments, including on-premises and cloud infrastructures, is essential.
Performance features to check:
Future-proofing your tool means your security program stays robust as your organization expands or shifts technology stacks.
Compliance can’t be overlooked. The right tool supports frameworks like PCI DSS, HIPAA, and ISO 27001, generating reports auditors expect. Customizable report formats and stakeholder-specific summaries keep everyone informed, from technical teams to executives.
Important reporting features include:
These capabilities reduce audit preparation headaches and improve transparency across your security program.
We’ve noticed how timely vendor support can prevent small issues from snowballing. Responsive customer service across multiple channels, phone, chat, and email, helps resolve problems quickly. Frequent software updates and vulnerability database refreshes ensure your tool stays effective against new threats.
Support factors to weigh:
Strong vendor engagement means fewer surprises and a more stable security posture.
Cost always factors into decision-making. Licensing models vary, subscription, perpetual, or usage-based, and should align with your budget and deployment scale. Don’t forget the total cost of ownership, which includes training, integration, and ongoing support expenses.
Assess whether the tool’s feature set matches your organization’s needs and if the vendor has a reliable track record. The right investment yields better vulnerability risk reduction and operational efficiency.
Consider these financial aspects:
We recommend weighing cost carefully but not sacrificing necessary capabilities for short-term savings.
Many businesses now run hybrid environment security setups with both cloud assets and local servers. A strong vulnerability management platform should offer cloud vulnerability management, network vulnerability scanning, and endpoint vulnerability scanning in one place.
Look for vulnerability management cloud integration and agent-based scanning features. This lets you track container security scanning and cloud-native resources while using vulnerability reporting tools to see all data in a single dashboard.
Vulnerability management false positives can waste hours of work and slow down patch management automation. The best vulnerability assessment tools use vulnerability intelligence feed updates and a solid vulnerability prioritization algorithm to filter out noise.
Features like continuous vulnerability scanning, web application scanning, and vulnerability risk scoring help you focus on actual threats. A clear vulnerability management dashboard analytics setup makes it easier to spot trends and verify results.
Vulnerability management ROI depends on more than just the vulnerability management cost. Track metrics like reduced vulnerability lifecycle management time, automated patch deployment success rates, and faster vulnerability remediation workflow completions. Use vulnerability management reporting tools to show risk-based vulnerability prioritization improvements.
SIEM integration vulnerability tracking and vulnerability management alerting can also help justify investment by proving better vulnerability management risk reduction over time.
Without proper vulnerability management integration, teams waste time moving data manually. The right vulnerability management solution should connect with IT security tools, vulnerability ticketing systems, and even developer tools for DevSecOps workflows.
Features like vulnerability management network integration and automated patch deployment speed up the vulnerability remediation workflow. Look for role-based access controls and multi-user setups to keep vulnerability management policy enforcement simple and consistent.
As businesses grow, the vulnerability assessment process must adapt. Continuous vulnerability scanning is ideal for real-time threat detection, but sometimes network vulnerability scanning or endpoint vulnerability scanning needs to run on a set schedule.
Automated patch deployment and vulnerability management patch scheduling help balance speed with stability. Consider vulnerability management scalability, usability, and user adoption rates to decide how scanning frequency changes as your asset inventory expands.
Choosing the right vulnerability management tool takes balance, coverage, ease of use, integration, and cost. Focus on continuous scanning, risk-based prioritization, and workflow integration to improve remediation speed and accuracy. Test tools in real-world environments to ensure they fit your team’s needs and compliance requirements.
Need help optimizing your MSSP tech stack? Work with our experts to streamline operations, reduce tool sprawl, and select solutions that align with your business goals and operational maturity.