Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

OT security monitoring helps keep power plants, factories, and water systems safe by finding problems early. It also helps companies follow safety and legal requirements. Ransomware attacks on important systems went up 34% in 2025, with factories seeing a 61%…
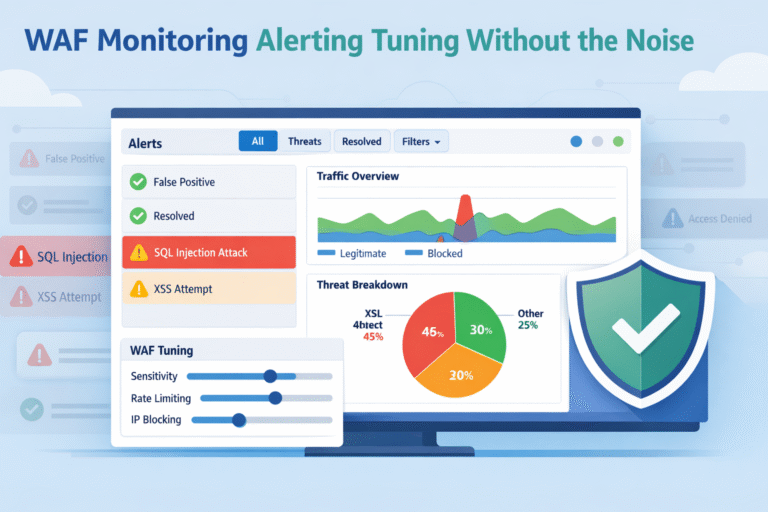
WAF monitoring, alerting, tuning are what make a firewall useful in real life. We can deploy a strong WAF, but without operating it well, it becomes an expensive traffic viewer. We’ve seen this firsthand. The real defense comes from watching…

Securing web applications compliance should feel like steady engineering, not last-minute chaos. We’ve all seen the panic when an audit notice lands and teams scramble for proof their app is secure. In our work with managed security providers, we’ve learned…

Configuring WAF policies rules means defining how a web application firewall inspects requests and enforces allow or block actions to stop real attacks like SQL injection and XSS. In practice, most breaches exploit misconfigured rules, not missing tools. According to…

The OWASP Top 10 isn’t a checklist. It’s a blueprint for building a website that doesn’t break. Since 2003, it’s listed the flaws attackers actually use. Teams that just tick the boxes still get hacked. The ones who bake these…

Outsourced web application security is when you bring in outside experts to handle the testing and monitoring, but the big decisions and final responsibility stay with your company. It’s not a magic fix. A lot of mid-sized firms use it…
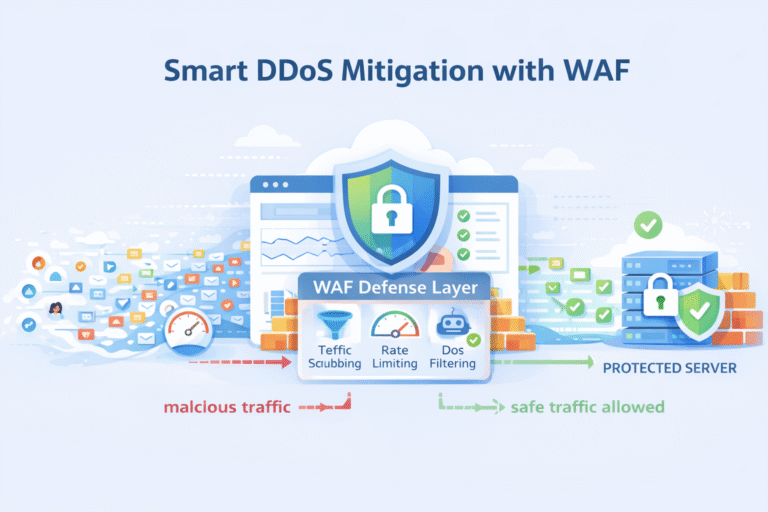
DDoS Protection Mitigation WAF solutions work together by spotting abnormal traffic, blocking malicious requests, and keeping applications online during distributed denial of service attacks. In 2023, many global reports showed average attack volumes pushing beyond 1 Tbps, proving how quickly…
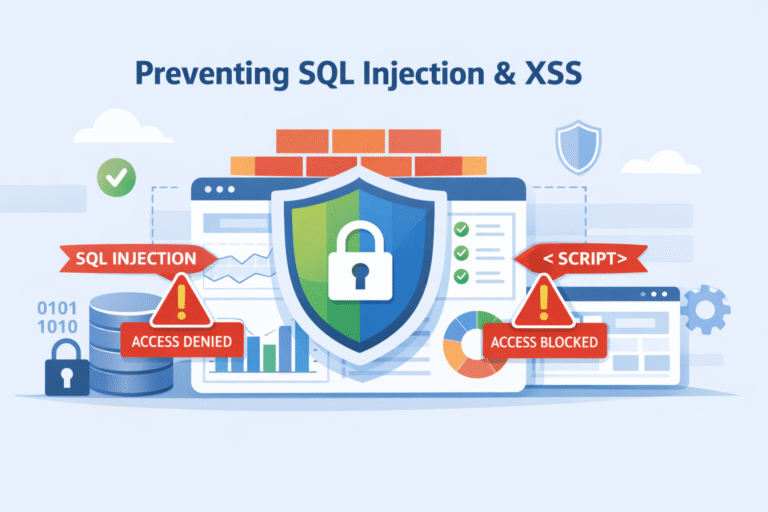
SQL injection and XSS attacks persist because developers still let untrusted input reach executable code. The core defense is separating data from logic through parameterized queries, strict validation, and proper output encoding. OWASP and modern frameworks repeat this because it…

A managed WAF service strengthens application security, cuts operational load, and speeds up protection against new attack patterns. By handing monitoring, tuning, and incident response to specialists, your team can secure web apps and APIs without becoming WAF experts. OWASP…

A Managed Web Application Firewall (WAF) is a cloud-based shield that filters harmful HTTP and HTTPS requests at the application layer before they ever touch your code. It blocks common attacks covered in the OWASP Top 10, helps with security…