Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
DDoS Protection Mitigation WAF solutions work together by spotting abnormal traffic, blocking malicious requests, and keeping applications online during distributed denial of service attacks. In 2023, many global reports showed average attack volumes pushing beyond 1 Tbps, proving how quickly the threat has grown.
We have seen this change firsthand while securing production systems where even minutes of downtime were unacceptable. This article breaks down how DDoS protection, mitigation, and WAF security operate as connected layers, what each one actually handles, and why integration matters more than relying on a single control. Keep reading to learn how it works.
It starts with knowing what “normal” even looks like. We have to measure the usual hum and chatter of our network, the baseline. When live traffic veers off that map, we’ve got a problem. CISA’s guidance is blunt: speed is everything. The faster we spot the anomaly, the shorter the outage.
Then comes the filtering. This is mitigation in action. Suspicious traffic gets diverted, rate-limited, or blocked based on its reputation or behavior. We’ve seen early filtering like this cut an attack’s impact by more than half before the heavier defenses even kick in. It’s like stopping a flood at the neighborhood gate instead of waiting for it to reach our front door.
But attackers adapt. They change tactics. So the final, crucial step is adaptation. Modern systems can’t rely on static rules. They have to adjust thresholds in real-time, a point hammered home in NIST studies on multi-vector attacks.
The cycle never really stops:
It’s an always-on discipline, not a fire alarm we pull only in an emergency.
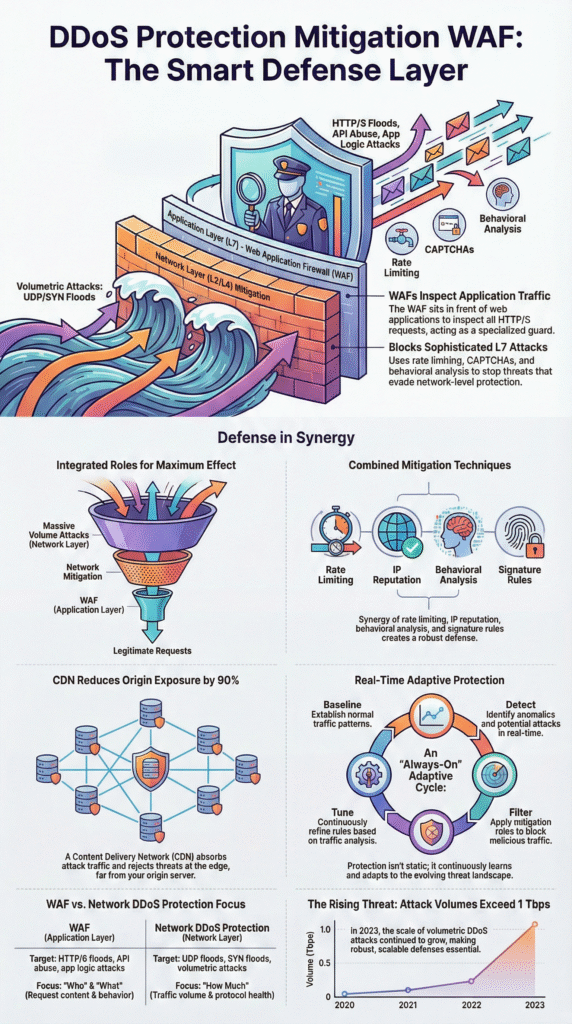
Attacks come from different altitudes, and we need different defenses for each.
Down at the network and transport layers (L3/L4), it’s often a brute-force assault. UDP floods, SYN floods, they just try to smash our bandwidth or fill up every connection slot our servers have. Research from groups like ENISA suggests over 60% of the big, headline-grabbing attacks still use these methods.
Up at the application layer (L7), it gets sneaky. Here, attackers look like legitimate users. They send HTTP requests, slowly tie up API connections, or hammer a login page. The packets are valid, so they slip right past basic volume filters. We’ve watched these low-and-slow attacks choke a service without setting off a single traditional DDoS alarm.
That’s why we need the right tool for the right job. Network controls stop the tidal wave. A WAF analyzes the intent of each individual boat in the harbor.
| Attack Layer | Common Methods | What They Exhaust |
| L3/L4 (Network/Transport) | UDP floods, SYN floods, DNS amplification | Bandwidth, server connection tables |
| L7 (Application) | HTTP floods, Slowloris, API abuse | Application CPU, database threads, memory |
Think of a WAF as a smart bouncer for our web apps and APIs. It sits out front as a reverse proxy, inspecting every HTTP/S request, the headers, the URLs, and the data inside. It checks them against a set of security rules and behavioral patterns.
“A web application firewall inspects the HTTP traffic between clients and web servers. It monitors and filters this traffic in order to protect a web application from certain attacks” – Cloud Security Alliance [1]
This makes it our best defense against those sneaky application-layer attacks. Many teams rely on a managed Web Application Firewall (WAF) to reduce operational burden while keeping strong inspection and enforcement in place.
A good WAF uses rate limiting, challenge questions (like CAPTCHAs), and behavior analysis to tell real users from malicious bots.
Here’s the catch, though. A WAF isn’t a shield against a tsunami. If a massive volumetric flood hits it directly, it’ll get overwhelmed. That’s why it must work with upstream DDoS mitigation.
The mitigation service soaks up the raw flood; the WAF handles the sophisticated infiltration attempts. SANS Institute papers often stress this combo: inspection paired with sheer scale.
A WAF brings three key things to the fight:
In a layered defense, the WAF is the brain making nuanced decisions.
A WAF’s power is multiplied when we combine its brains with a few key techniques. Rate limiting is fundamental. It simply caps how many requests a single client can send. During attacks we’ve managed, setting adaptive limits cut backend server load by nearly two-thirds, all while real users kept browsing smoothly.
For many organizations, the real value comes from the broader managed WAF service benefits, especially when tuning rules and responding under pressure requires consistent expertise.
Then there’s behavioral analysis. Instead of just counting requests, it learns what normal user behavior looks like, how they move through a site, how fast they click. This catches the slow-burn attacks that try to fly under the radar. While machine learning helps here, it still needs a human to fine-tune it and prevent false positives.
Never underestimate the basics, either. IP reputation filtering, blocking traffic from known bad networks or temporary greylisting of suspicious ranges, stops repeat offenders cold. Groups like FIRST emphasize that sharing threat intelligence makes these lists much more accurate.
The strongest approach uses them all together:
No single technique is a silver bullet. The strength is in the coordination.
Credits: Cyber&Tech
A Content Delivery Network (CDN) changes the battlefield. It spreads our content across hundreds of edge locations worldwide, close to our users. This does two critical things for DDoS defense.
First, it absorbs and distributes traffic. A huge chunk of requests is served from the edge cache, never touching our origin servers. Some analyses show this can reduce origin exposure by 90% during a traffic flood. It’s a distributed shock absorber, a concept backed by research on network resilience from institutions like Harvard.
Second, it lets we act faster. We can apply security rules, rate limiting, bot challenges, at the edge, right where the traffic first arrives. Bad requests are stopped thousands of miles away from our data center. In our work, this “early rejection” is one of the most effective ways to keep an application responsive under pressure.
Typical CDN and WAF synergies include:
When we combine a CDN with mitigation and WAF layers, our defense isn’t a single castle wall. It’s a whole fortified landscape.
It’s not a versus. It’s a partnership. Network-layer protection is our heavy artillery. It deals in raw volume, packets, and protocols. Its job is to scrub the massive floods and protocol attacks before they reach our infrastructure. It sees all traffic but doesn’t understand the context of a web session.
A WAF is our forensic detective. It understands HTTP, sessions, and user behavior. It can spot a malicious login attempt or a subtle API attack. But, faced with a 100 Gbps UDP flood, it would be useless.
ENISA reports show that using both layers together can cut successful DDoS incidents by nearly half compared to using just one. We need the network layer to stop the bulldozer, and the WAF to catch the pickpocket.
| Aspect | Web Application Firewall (WAF) | Network DDoS Protection |
| Primary Focus | Layer 7 (Application) | Layers 3 & 4 (Network/Transport) |
| Traffic it Sees | HTTP/HTTPS, Web APIs | All protocols (TCP, UDP, ICMP, etc.) |
| Good at Volumetric Floods? | Not really, can be overwhelmed. | Yes, designed to absorb and scrub them. |
Knowing this stops ours from asking a WAF to do a job it was never built for.
In practice, an integrated strategy means our traffic always flows through the defenses. Detection systems monitor, mitigation scrubs, and the WAF enforces application logic continuously. This aligns with government guidance.
“When deployed with a web application firewall (WAF), DDoS Protection solution protects both at the network layer and at the application layer. The solution must offer a service level agreement with a guaranteed time to mitigation (TTM) [and] provide reports and dashboards of prevented attacks and actions.” – National Cybersecurity Authority [2].
But strong availability defense also depends on visibility beyond the perimeter. Many security teams pair DDoS response planning with a dark web monitoring service to detect early indicators of targeting, leaked credentials, or coordinated threat activity before attacks escalate.
An integrated strategy has three legs:
The goal is straightforward but tough: keep malicious traffic to a tiny fraction of what hits our app, even during a complex, multi-vector attack. Getting there takes the right tools, layered deliberately, and the experience to make them sing together.
DDoS protection stops volumetric attacks. By using strong network layer protection and traffic scrubbing. These attacks try to overwhelm bandwidth with massive traffic floods. Mitigation systems detect abnormal spikes quickly and reroute traffic through a DDoS scrubbing center. There, malicious packets are filtered out before they reach the server.
Techniques such as anycast network routing, UDP flood defense, and SYN flood protection help maintain service uptime. Always-on protection ensures defenses stay active. without waiting for manual action during an emergency.
WAF security protects against application layer DDoS attacks that mimic real users. A web application firewall inspects incoming HTTP requests and blocks harmful patterns. Before they disrupt services. It applies rate limiting to prevent excessive requests from one source.
It also stops threats like HTTP flood blocking and Slowloris attack prevention. WAF tools use behavioral analysis, anomaly detection, and challenge response methods. Such as CAPTCHA verification or JavaScript challenges to reduce bot-driven traffic.
Organizations should use both DDoS mitigation and a cloud WAF. When attackers target multiple layers at once. Multi vector DDoS attacks often combine L3 L4 floods with L7 application abuse. Network defenses stop amplification attacks like DNS amplification.
While WAF protection handles HTTP-based disruption attempts. Together, they provide real time mitigation, origin shielding, and better resilience for critical online systems. This layered approach reduces downtime during complex distributed denial of service events.
Traffic baseline monitoring helps teams understand what normal traffic looks like before an attack happens. This makes anomaly detection faster and more accurate during a distributed denial of service event. Adaptive thresholding adjusts security limits automatically as traffic conditions change.
This reduces false alarms while still blocking real threats. When combined with machine learning DDoS detection and signature based filtering, mitigation systems can respond immediately. These methods improve traffic scrubbing accuracy during high-pressure attacks.
Organizations can reduce bot mitigation failures. By combining multiple controls instead of relying on one method. IP reputation checks help identify suspicious sources early. Teams should also apply IP blacklisting, ASN filtering, CIDR blocking, and geo blocking for stronger filtering.
Challenge response tools, rate limiting, and origin shielding add more protection against automated abuse. Regular DDoS simulation testing and well-defined mitigation playbooks help teams stay prepared. Continuous tuning strengthens defenses against evolving WAF bypass techniques.
DDoS protection, mitigation, and WAF security are no longer optional add-ons. They are core availability controls for modern services. When layered correctly, they help teams turn disruptive traffic floods into manageable security events.
If an organization is reassessing its DDoS Protection Mitigation WAF strategy, the next step is aligning tools, processes, and expertise around always-on defense. At MSSP Security, we provide vendor-neutral consulting to reduce tool sprawl, optimize integration, and strengthen visibility. Join us here.