Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
A Managed Email Security Gateway works because it removes guesswork from email defense. Instead of relying on tools alone, it pairs advanced filtering with people who watch email threats every hour of the day. We have seen how a single missed phishing email can unravel weeks of work.
Most organizations already know email is their biggest risk. What they want is fewer alerts, fewer breaches, and a system that quietly does its job. That is where a managed secure email gateway earns its place. Keep reading, because the way email attacks work has changed, and the way protection works has too.
Email remains the front door for attackers because it is trusted, familiar, and constant. Every invoice, calendar invite, and shared document looks routine until it is not.
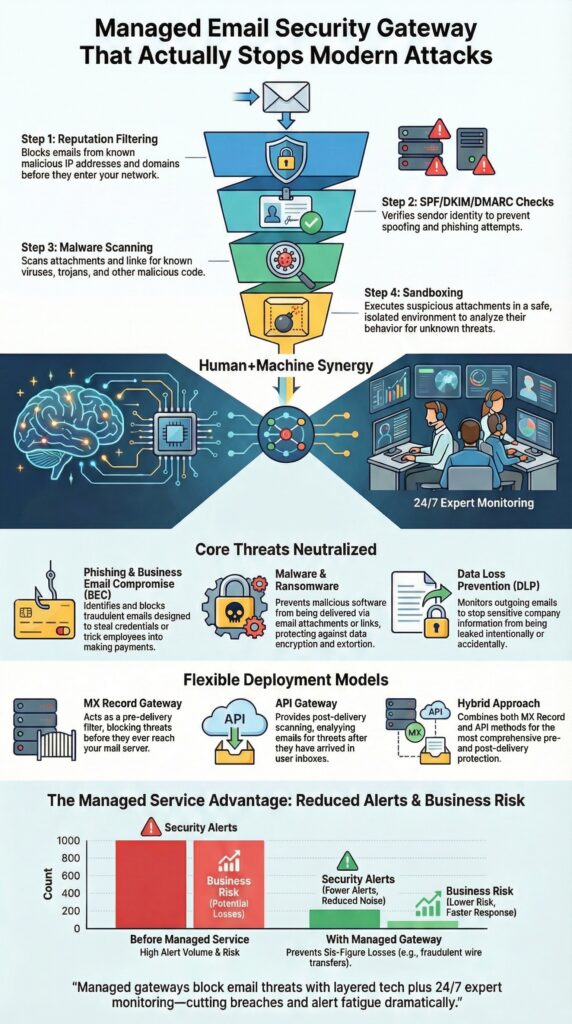
Threat actors no longer rely only on noisy malware. They use subtle social engineering, compromised vendors, and patient reconnaissance. A secure email gateway acts as a perimeter email defense that inspects every message with context, not just signatures.
We have watched organizations struggle with alert fatigue. Tools flag hundreds of emails, but no one has time to tune policies or investigate every quarantine item. A managed SEG changes that dynamic by making email security a service, not a side task.
Early in most environments, protection starts with a few core layers.
Those layers matter, but on their own they are no longer enough.
Most people think email security is just spam blocking, but a managed secure email gateway works more like a checkpoint between the internet and your mailboxes.
It usually connects in two ways:
At MSSP Security, real deployments are usually hybrid: inline for obvious threats, API for subtle or behavioral attacks.
For inbound mail, the flow looks like this:
Outbound filtering matters too:
Done well, users just notice fewer bad emails, while security teams gain control and visibility without drowning in noise.
Phishing has shifted from cliché scams to careful impersonation of:
A managed SEG looks for:
BEC protection is context-heavy, and that context gets sharper when humans review borderline messages. We have seen cases where a single blocked wire transfer prevented six-figure losses. That is not theory. That is lived incident response.

Signature-based AV still helps, but it misses new or customized payloads. A managed gateway adds:
AI models assist, while managed analysts confirm high-risk decisions. CISA continues to list phishing—especially attachments and links—as a leading initial access vector for ransomware. A layered gateway cuts that path down sharply.
Outbound controls handle:
TLS and S/MIME help keep sensitive email private in transit.
A lot of organizations begin with a self-managed secure email gateway. On paper, it looks cheaper:
But the hidden costs come later:
A managed email security service shifts that weight off the internal team and turns it into an ongoing, specialist function.
Managed services don’t just “host” the tool, they actively run it. That usually includes:
From a resource angle, this is the core benefit: most IT teams do not want to become email forensics experts. They want fewer successful attacks, faster answers, and less noise. Managed email security is built around that outcome.
Before you sign with a provider, it helps to line up the main models side by side.
1. MX record gateway
2. API email gateway
3. Hybrid email security
Email continuity is part of the fit, not an extra. If the gateway goes down, users still need:
Managed providers usually design for:
The best fit often ends up hybrid: strong front-line blocking, rich post-delivery control, and continuity plans baked in.
| Deployment Type | How It Works | Strength |
| MX record gateway | Routes email through the gateway before delivery | Strong pre delivery blocking |
| API email gateway | Scans mailboxes after delivery via API | Deep visibility and remediation |
| Hybrid email security | Combines both models | Layered defense and resilience |
A modern managed email security gateway is built for more than just filtering junk. Here are the capabilities that usually make the real difference:
Email doesn’t live alone, so its signals should not either. Key integrations include:
The National Institute of Standards and Technology (NIST) stresses layered controls and ongoing monitoring for email, especially in cloud environments. These advanced capabilities are exactly what turn that guidance into working practice.

Technology features are baseline. Most serious providers can check the boxes on spam, phishing, sandboxing, and APIs. The real separation is in how they run the service day to day.
A few practical questions help cut through the noise:
At MSSP Security, we treat email as part of the larger threat surface, not a separate island. Seeing patterns across many clients and industries helps us spot emerging attacks faster, then tune defenses across the board.
That mindset is what you want to test for. You’re not just buying a filter. You’re choosing a partner that treats email as a living system that needs constant attention, context, and adjustment.
Even the best managed email security gateway can’t fully shield against human decisions. Users still:
A strong managed service leans into this reality instead of ignoring it.
Key support areas:
Over time, that mix of technology and training changes outcomes, not just theory. We’ve seen phishing click rates drop when:
The most effective email defenses pair a managed gateway with informed users. The gateway catches what it can, and people help catch the rest, turning every reported email into training data for the whole system.
A good managed email security setup should feel controlled but not heavy. The goal is to keep users safe without turning every harmless message into a helpdesk ticket.
Managed email security providers typically handle:
Inline scanning and policy enforcement run quietly in the background. Most emails just flow. When something serious shows up, response is:
That structure lets internal teams stay focused on projects that actually move the business forward, instead of babysitting quarantine queues all day.
A managed email security gateway is built for those real, shifting conditions, not just neat diagrams.
Smaller teams often assume “enterprise-grade” email protection is too complex or too expensive. Managed services break that barrier by providing:
A scalable model means you can:
The underlying principles—phishing defense, malware control, DLP, monitoring—stay the same, even if you triple headcount.
Enterprises face a different kind of complexity:
A managed secure email gateway helps by:
In both small and large settings, managed email security serves as a stabilizing layer, keeping protection steady while everything around it keeps changing.
Credits : Professor Messer
Email is not disappearing, and attackers know that very well. So the real question isn’t whether to “fix email this year,” but how to keep it under control every year.
A managed email security gateway works less like a one-time product and more like an operating model. At its best, it combines:
Over time, we’ve seen organizations move from constant reactive cleanup to a quieter, more stable state:
That’s what a managed email security gateway looks like when it’s treated as a long-term strategy instead of a short-term plug.
A Managed Email Security Gateway protects email systems from spam, phishing attacks, malware, ransomware, and business email compromise. It applies email threat filtering, URL scanning, attachment detonation, and reputation filtering. Using machine learning email analysis and zero-day threat detection, it blocks malicious messages, impersonation attempts, and reconnaissance emails before they reach user inboxes.
A secure email gateway is deployed using an MX record proxy or an API email gateway. This setup enables inline email scanning without changing how users send or receive messages. It supports inbound email security, outbound email filtering, hybrid email security, and cloud email protection while maintaining email continuity and failover protection during outages.
Managed SEG prevents phishing and business email compromise through behavioral analysis, heuristic analysis, and email anomaly detection. It verifies sender identity using DMARC enforcement, SPF DKIM, and email authentication. Real-time blocking, spear phishing filters, and user impersonation blocks ensure suspicious emails are quarantined before users can engage with them.
An email security service prevents data loss by applying DLP email controls and outbound email filtering. Data loss prevention rules inspect message content, attachments, and sensitive data patterns. Email encryption, TLS encryption, and S/MIME support secure confidential information and help organizations meet GDPR email and HIPAA email security compliance requirements.
Enterprise email protection provides a centralized admin console for quarantine management and email policy enforcement. It includes threat intelligence feeds, SIEM email logs, and SOAR integration for faster response. With 24/7 email monitoring, MDR email support, post-delivery remediation, and clear incident workflows, security teams maintain strong, scalable email defense.
A Managed Email Security Gateway is not a one-time fix; it’s a long-term defense layer that shifts as attackers change their tactics. The control itself stays in place, but the rules, intelligence, and response patterns keep moving with the threat landscape.
If you’re weighing options, starting with a managed approach usually cuts risk faster and with less operational drag. At MSSP Security, we treat email protection as foundational, not optional, and we extend that mindset to your broader MSSP stack. See how our consulting services can help you choose the right tools, reduce tool sprawl, and optimize your stack.