Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Data protection compliance means making sure organizations handle personal data according to the laws that apply to them.
It’s not just about filling out forms or ticking boxes; it’s about building habits that guide everyday choices, from how products are designed to how teams respond when something goes wrong.
When everyone involved knows the rules and puts them into action early on, compliance stops being a last-minute scramble and becomes part of how work gets done.
There’s a lot to unpack here, including common challenges organizations face. Keep reading to see how these pieces fit together and where the real hurdles lie.
Data protection laws might wear different outfits depending on where you look, different words, deadlines, or penalties, but underneath, they share the same backbone. These seven principles form that backbone.
When we guide organizations through compliance, this is where we begin. Because these principles shape every choice that follows.
Ignoring even one principle can make the whole compliance structure shaky, like a house built on sand. But get them right, and audits lose their sting, becoming routine rather than a surprise.
Here’s a quick look at these core principles:
Starting with these principles means building compliance on solid ground. It’s not just about ticking boxes; it’s about creating a system that holds up when pressure comes.
Lawful processing basis is the gatekeeper. Every data activity must rest on consent, contract, legal obligation, or legitimate interest. Without that anchor, the rest collapses.
Transparency makes lawfulness visible. Clear privacy notices explain what data is collected, why it is needed, and how long it will be kept. According to the European Commission, transparency is central to enforcing GDPR rights.
Fairness is often overlooked. We have seen technically legal processing still fail regulatory scrutiny because it surprised users. Regulators notice intent.
Before moving deeper, it helps to recognize that transparency is not just a policy document. It is an ongoing communication practice.
Purpose limitation prevents silent expansion. Data collected for onboarding should not quietly fuel unrelated analytics later.
The data minimization principle reinforces discipline. Only collect what the business genuinely needs to operate. Extra fields become liabilities over time.
Teams that revisit forms regularly reduce breach impact. Less stored data means less exposed data.
In practice, this principle drives several operational habits:
These habits reduce risk without slowing growth.
Accuracy need sounds simple until legacy systems enter the picture. Outdated records create compliance exposure fast.
Storage limitation forces retention discipline. Data must be deleted once the purpose expires, not when storage fills up.
We have seen enforcement actions triggered by stale records alone. Retention schedules are not optional documentation.
Short retention windows also reduce discovery scope during investigations, which matters more than many teams expect.
Integrity and confidentiality focus on security controls. Encryption, access control policies, and monitoring protect data from loss or misuse, especially when supported by advanced security services that align controls across legal, technical, and operational teams.
According to IBM Security, “The global average cost of a data breach in 2023 was USD 4.45 million,” showing how weak accountability and fragmented controls quickly translate into measurable financial impact [1].
Accountability principle is where many organizations stumble. Regulators expect proof, not promises.
Documentation shows intent. Logs, policies, DPIAs, and training records show that compliance is embedded, not improvised.
This principle is where security teams and legal teams must collaborate closely, even when priorities differ.
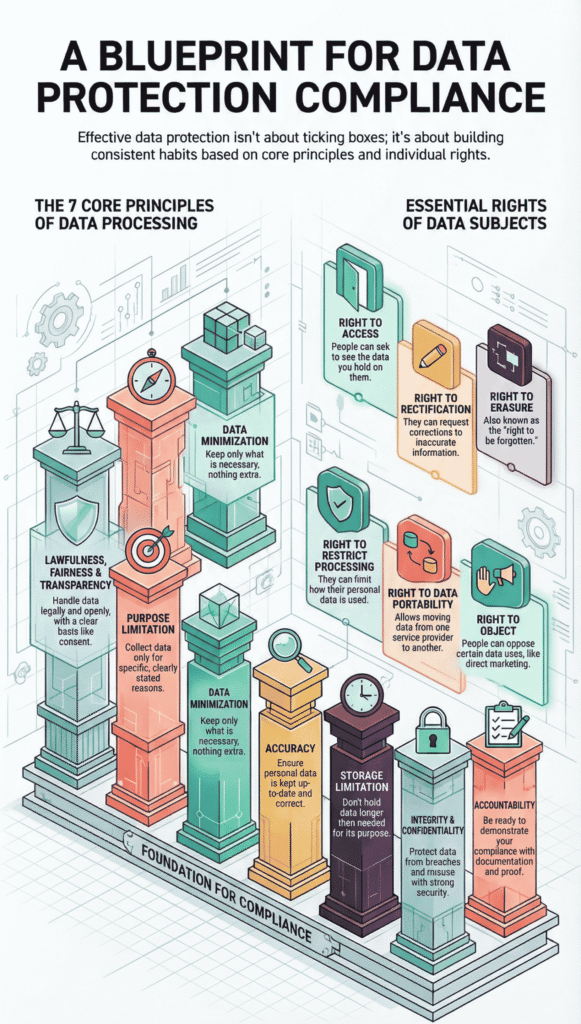
Rights of Data Subjects shift compliance from something that happens behind the scenes to a direct responsibility toward people. Every request that comes in, whether it’s to access, correct, or delete data, puts an organization’s readiness to the test.
This part of compliance reveals true maturity. Sure, having the right tools helps, but the real challenge lies in how disciplined and timely the response is. It’s about respect and precision, not just technology.
Here are the key rights data subjects hold:
Handling these rights well means building trust. It’s not just about rules, it’s about showing that the organization values the people behind the data.
Right to access data allows individuals to see what is held about them. Deadlines are strict and extensions are limited.
Right to rectification ensures inaccuracies are corrected quickly. Delayed updates undermine both trust and compliance.
Organizations that centralize identity verification handle these requests faster and with less friction.
Right to erasure applies when legal grounds no longer exist. It is conditional, but regulators expect clear justification when denied.
Data portability right enables individuals to move data between services. Machine readable formats are mandatory.
We have implemented portability workflows that double as internal data mapping tools. Compliance work often creates hidden efficiencies.
Objection to processing applies strongly to direct marketing. Opt out must be immediate and respected across systems.
Automated decisions rights address profiling and algorithmic outcomes. Humans must be able to intervene.
As noted by the UK Information Commissioner’s Office, automated decisions affecting individuals need transparency and safeguards.
These rights force organizations to understand their own data flows more deeply than they expect.
Global compliance feels complex because terminology changes. The underlying expectations remain surprisingly aligned.
We often build frameworks that map one core control set across many jurisdictions, reducing duplication and confusion.
GDPR compliance applies extraterritorially to EU residents’ data, regardless of company location.
CCPA requirements focus on California residents and businesses above defined thresholds.
PDP Law Indonesia applies to any entity processing Indonesian citizens’ data, with full enforcement beginning October 2024.
This global reach means location no longer limits regulatory exposure.
| Feature | GDPR | CCPA | Indonesia PDP Law |
| Consent | Opt-in (Explicit) | Opt-out (for sales) | Explicit for sensitive data |
| DPO | Mandatory for large scale | Not required | Mandatory for high-risk |
| Breach Notice | 72 Hours | Reasonable time | Prompt notification |
| Max Fines | 4% Global Revenue | $7,500 per violation | Administrative sanctions |
This comparison helps teams prioritize controls without rebuilding programs per region.

Security Measures are where theory meets pressure. Breaches do not wait for perfect compliance.
We have supported incident response under regulatory timelines. Preparation determines outcome more than intent.
Data encryption standards protect information at rest and in transit. Weak encryption attracts regulatory scrutiny quickly.
Multi-factor authentication limits credential abuse. Regulators increasingly expect MFA on privileged access.
Pseudonymization techniques and anonymization methods further reduce exposure when full deletion is not workable, particularly when paired with data loss prevention controls that limit how sensitive information is shared or moved internally.
Security controls should align with risk, not convenience.
Breach notification timeline varies by law but urgency is universal. Delays worsen penalties.
Incident response plans define roles, escalation paths, and notification templates, supported by monitoring data movement across channels so anomalies are detected early instead of after regulatory deadlines are missed.
This preparation matters, as Cisco’s Cybersecurity Readiness Index reports that 86% of organizations experienced at least one operational outage caused by a cybersecurity incident, reinforcing how delayed detection directly affects business continuity [2].
When we assist clients through MSSP Security, we emphasize rehearsal. Tabletop exercises reveal gaps documentation never shows.
Prepared teams respond calmly. Unprepared teams improvise under pressure.
You can’t avoid the mess that comes with unclear responsibilities. When no one knows exactly who’s in charge, mistakes creep in, and liability follows close behind.
Clear compliance roles act like a map, everyone knows their path, and the chances of stepping on each other’s toes drop. This clarity smooths out the bumps between departments, making cooperation less of a headache.
Here’s what defining compliance roles does for an organization:
When combined with the right organizational tools, these roles become even more effective. Tools like compliance software, checklists, and reporting systems keep everyone on the same page, ensuring that responsibilities don’t just exist on paper but translate into real action.
Data controller duties define purpose and means of processing. Controllers bear primary accountability.
Data processor obligations focus on executing instructions securely and lawfully.
Joint controllership arises when decisions are shared. Written agreements become critical evidence.
The table below highlights how these roles differ operationally.
| Role | Primary Responsibility | Key Risk |
| Controller | Defines purpose and legal basis | Regulatory liability |
| Processor | Executes processing securely | Contractual breach |
| Joint Controller | Shared decision making | Shared enforcement |
Privacy by design embeds safeguards early. Retrofits cost more and meet fewer regulators.
Privacy by default limits exposure without user action.
Impact assessment DPIA evaluates high risk processing before deployment. Regulators expect documented reasoning.
When teams adopt DPIAs as planning tools rather than compliance chores, decision quality improves noticeably.

Best practices turn principles into everyday habits. Audits don’t reward perfection, they reward consistency.
Here’s what really matters:
At MSSP Security, we’ve seen that organizations treating compliance as an ongoing operation, not just a legal checkbox, face fewer surprises and save money over time.
Compliance requirements data protection guide how organizations collect, use, and store personal data.
They rely on principles like data minimization, purpose limitation, and a lawful processing basis. Teams must also follow accuracy requirements, storage limitation, and integrity and confidentiality rules, while proving accountability through clear records and documented processes.
Compliance requirements data protection give clear rights of data subjects. These include the right to access data, rectification, erasure, restriction, and data portability.
People can also object to processing and challenge automated decisions. Organizations must respond on time and explain actions clearly to stay compliant.
Compliance requirements data protection define clear compliance roles. Data controller duties focus on decision-making, while data processor obligations cover secure handling.
Some organizations appoint a Data Protection Officer, share responsibility through joint controllership, and apply privacy by design and privacy by default. DPIA impact assessments help manage high-risk processing.
Compliance requirements data protection vary across regions. GDPR compliance, CCPA requirements, PDP Law Indonesia, LGPD Brazil, PIPEDA Canada, and APPI Japan set different standards.
Many also enforce data localization rules. Organizations handling cross-border data must understand overlaps to avoid gaps and reduce regulatory risk.
Compliance requirements data protection rely on strong security measures. These include data encryption standards, access control policies, and multi-factor authentication.
Teams prepare incident response plans, meet breach notification timelines, and use pseudonymization or anonymization methods. Regular monitoring and updates help prevent violations and penalties.
Compliance in data protection works best when principles, rights, security, and accountability come together. Laws will shift, and enforcement will tighten, but what endures is disciplined governance and practical security planning.
Organizations that start early avoid the scramble later, while those who delay often face pressure under scrutiny.
The right approach is steady, well-documented, and focused on people. When done right, compliance signals trust instead of burden.
Simplify your compliance workflow, generate precise, legally-aligned data protection policies in minutes without the stress. Join MSSP Security.