Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Choosing DFIR provider in Fullerton starts with this: you need a team that can actually contain an active attack within hours.
Not in theory, not on a slide. In real cases. Every hour you lose means more data at risk, higher recovery costs, and longer downtime, so “24/7 support” only matters if the responders who pick up can take action right away, not just log a ticket. You’re looking for proven time-to-containment, real incident experience, and clear communication under pressure.
Keep reading so you can choose a DFIR partner who won’t waste your critical hours.

When a business in Fullerton gets hit with ransomware or a strange spike in logins, the room changes. People stop talking, screens get a little brighter, and everyone stares at the clock. Choosing a DFIR provider isn’t some checkbox on a project plan, it’s about whether that business comes out with a bruise or a broken leg.
Teams that already understand the pressure of digital forensics and incident response often react faster, similar to what you see in digital forensics work when every minute matters.
We work with MSSPs that feel that pressure every day. Their DFIR partners are the ones who dig into log trails, trace attacker movement, contain the damage, and piece together what actually happened so the client can face regulators, insurers, and their own board.
When the DFIR choice is wrong, containment drags, blame circles, and the losses quietly grow.
In Fullerton, a lot of owners still start with whoever handles their normal IT. On paper, that makes sense. Providers like ProLink Systems or NetWiz Computers show up in search, have solid Yelp ratings, and take care of backups, network issues, and daily user headaches.
But under the hood, we’ve watched those same “general IT first” calls turn into delays, shallow log collection, and missing forensic artifacts because those teams weren’t built for deep incident work.
From our side, supporting MSSPs, we see the aftermath. By the time an MSSP brings us in to help them evaluate or replace a DFIR product or partner, hours or even days have passed. Evidence is partially overwritten, attacker paths are fuzzy, and reporting turns into guesswork instead of a clean timeline.
Our job is to help those MSSPs pick DFIR tools and providers that don’t fold under live pressure, so the next time a Fullerton client calls at 2 a.m., the response is sharp, fast, and defensible.
When that choice is made early and made well, small incidents stay small. When it isn’t, one missed alert or slow handoff can turn a manageable intrusion into a full-blown breach. [1]
The choice between local and national DFIR support shows up fast once something goes wrong. Local providers in Fullerton, like Intelecis on N Harbor Blvd, can get to a site quickly when hardware has to be pulled, drives secured, or evidence sealed before someone accidentally wipes it.
Their teams know the regional quirks, how local businesses wire their networks, what compliance letters look like, who usually runs point on approvals. For a lot of small shops, there’s comfort in knowing someone can just get in a car and show up.
On the other side, big incidents don’t always stay polite or local. Ransomware, APT-style intrusions, and complex cloud breaches usually need more than a fast drive over, they need people who live in memory analysis, reverse engineering, and cross-tenant log correlation.
National DFIR firms bring dedicated labs, niche specialists, and real 24/7 coverage across time zones. They’re built to chase advanced malware, follow attacker movement across cloud and on-prem, and rebuild full incident timelines that hold up under legal and insurance review. Smaller shops rarely have that level of depth on the bench.
From what we see working with MSSPs, both models have a place, but the fit depends on risk, not comfort alone. Some teams in Fullerton want a local presence because their clients want to see someone in the room when drives are bagged and tagged.
Others quietly admit they’re out of their depth once the incident touches multiple cloud accounts, identity providers, or OT networks.
Our work comes in when MSSPs ask us to evaluate DFIR tools and providers before they commit, testing whether a local shop can hand off cleanly to a national team, or whether a national provider can support a local partner without stepping on the relationship.
The real trick is doing this homework before the attack, not while everyone is staring at an encrypted file server. When MSSPs map out their likely incident types and then match them to the right blend of local presence and national scale, Fullerton clients get faster, cleaner outcomes, and fewer surprises when the clock starts.
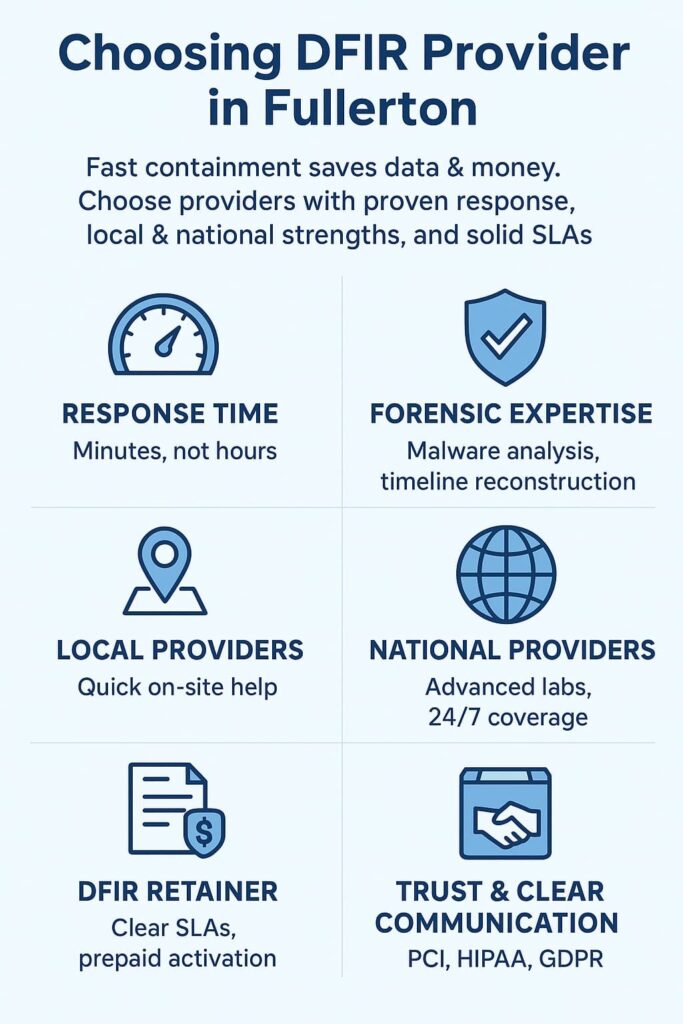
There are five things that make or break an IR team: response time, expertise, service scope, compliance support, and SLAs. First, response speed. The strongest providers guarantee activation within minutes, not hours. Some even promise triage under 15 minutes. When attackers move fast, delays cost real money.
Next is expertise. A provider should be able to handle root-cause analysis, malware reverse engineering, timeline reconstruction, and cloud forensics. The SERP notes that many Fullerton IT shops do not offer these deep forensic services.
Compliance is another make-or-break factor. PCI, HIPAA, and even GDPR matter more than people expect. You need a partner who knows the rules.
Finally, always ask for:
We follow these standards ourselves because clean documentation and fast forensic decisions protect clients legally and financially.
The safest path starts with a simple self-assessment. What systems matter most? What data must never leak? What downtime can the business tolerate? These answers shape what kind of DFIR provider fits.
Next, research 2–3 providers. Look for those offering DFIR retainers with prepaid activation. Retainers prevent slow onboarding and eliminate contract delays during emergencies, similar to what managed DFIR retainer setups aim to support.
Then, request RFPs. You’ll want clarity on pricing, response speed, forensic capabilities, and real case studies.
The SERP recommends tabletop exercises, and we agree. Running a mock incident shows how a team communicates under pressure. In our own tabletop practice, we often see gaps clients never noticed: missing logs, unclear escalation paths, tools no one knows how to use.
Finally, pick the provider that feels steady, calm, and professional under stress. Choose the one that answers questions clearly. Incident response requires trust more than flashy marketing.
Intelecis stands out as one of the few Fullerton-based cybersecurity providers with genuine incident response capabilities. Located at 1440 N Harbor Blvd, they offer 24/7 support, threat intelligence, and penetration testing. For businesses that want a familiar local team, they provide reliable on-site help and understand the Fullerton business environment well.
Their strengths include quick deployment and regional compliance support. For small to medium businesses that want someone nearby, this local presence matters. However, like many regional providers, scalability can be a limitation during large-scale incidents involving advanced threats or cloud-native attacks.
Many companies pair a local provider like Intelecis with a national forensic team or an MSSP partnership. In situations where local triage is needed but deeper investigation requires broader resources, this hybrid model works well.
Intelecis is a solid choice for teams wanting regional familiarity backed by practical security services.
National DFIR providers bring serious firepower. They offer global threat intelligence, around-the-clock forensic teams, and specialized labs that handle complex incidents like ransomware, data extortion, or APT infiltrations. These teams manage chain-of-custody evidence, reverse engineered malware strains, and reconstruct full attacker timelines.
Businesses in Fullerton often choose national teams when operating across multiple states, relying heavily on cloud platforms, or storing sensitive data that requires airtight compliance. National providers also integrate well with SIEM, EDR, and MDR systems, something local shops rarely match.
In our experience supporting incident response efforts, national DFIR teams work best when a business needs scale. They’re fast, structured, and battle-tested in thousands of cases. Many provide proactive tabletop exercises and forensic readiness planning, which lowers breach costs and helps teams act confidently during chaotic moments.
For complex threats, national teams are often the safer option. [2]

While some providers offer only forensics and others only monitoring, the strongest option for many Fullerton teams is a blend of both.
At MSSP Security, we see firsthand how combining 24/7 monitoring with DFIR readiness shortens response time and cuts damage, aligning with the practical value seen in MSSP DFIR support for teams that need constant protection.
Because we already know the client’s systems, logs, and behavior patterns, containment happens faster.
We don’t hard-sell ourselves as the only option. Instead, we emphasize preparedness. Many businesses call us after trying to assemble a response team mid-crisis. By then, logs have rotated, systems have rebooted, and crucial evidence has vanished.
With a strong MSSP-DFIR hybrid approach, teams stay ready long before anything goes wrong. A retainer with pre-agreed processes, priority activation, and a clear communication plan makes even the worst-case scenario manageable.
For many Fullerton businesses, this balanced model offers the right mix of speed, scale, and calm expertise.
When you start DFIR provider selection in Fullerton, focus on clear needs. Look at Fullerton DFIR services, provider reputation DFIR, and vendor breach history. Ask about chain-of-custody handling and evidence preservation IR.
Check if they offer rapid response SLA or a 2-hour triage guarantee. This helps you choose a team that actually fits your risk level.
When choosing DFIR vendor support, match the provider to your setup. Ask about managed DFIR providers, scalable DFIR retainers, and business size DFIR match. Check if they offer cloud forensics providers, hybrid MSSP DFIR support, and access scope risk DFIR review. Clear SLA response time and simple pricing help you understand what you’re really getting.
When checking DFIR supplier criteria, look for DFIR expertise assessment, technical DFIR experts, and forensic lab certification. Ask about root cause analysis DFIR, timeline reconstruction IR, and malware reverse engineering.
If they provide DFIRaaS providers or outsourced DFIR companies, make sure you ask about log retention DFIR and threat hunting DFIR to see how deep they go.
During incident response provider evaluation, ask how they handle compliance support DFIR, GDPR PCI DFIR, and regulatory alignment IR. Many firms also support HIPAA PCI DSS DORA or newer rules like CIRCIA CMMC OCPA.
Look for ISO27001 incident response experience and strong credential hygiene DFIR. A good provider should explain these clearly in plain language.
Choosing a DFIR provider in Fullerton comes down to preparation, speed, and trust. Local teams bring comfort. National teams bring power. A hybrid MSSP-DFIR approach often delivers both.
The goal stays simple: contain threats fast, protect evidence, and return operations to normal without panic. When businesses follow the right criteria, SLAs, expertise, reporting quality, they avoid costly mistakes and stay resilient, no matter what hits their network.
If you want tailored guidance on building the right security stack, strengthening visibility, or improving MSSP operations, Get Expert MSSP Guidance.