Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Evidence preservation handling forensics starts with one idea: protect what you see, don’t change it. People worry they’ll click the wrong thing, move a file, or power off a device and ruin a case, and honestly, that can happen if you rush.
Courts expect digital artifacts to stay in their original state from the moment you touch them. At MSSP Security, we’ve seen small habits, like browsing a drive out of curiosity, wipe out key traces. A simple, repeatable process matters more than advanced gear or big words.
Keep reading to walk through that process in clear steps.
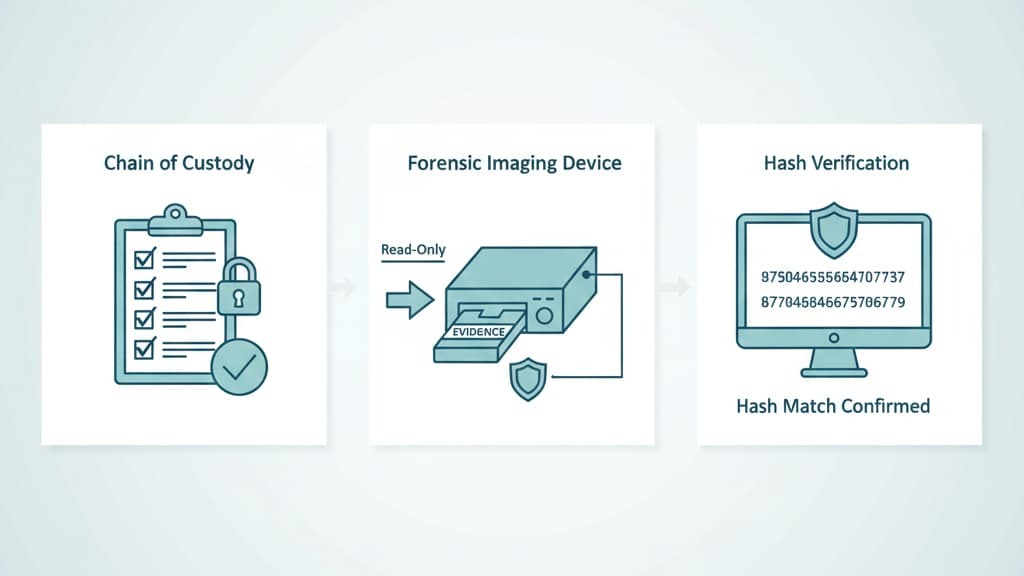
What usually surprises people first isn’t the tools, it’s the rules. In our work advising MSSPs at MSSP Security, we anchor evidence handling to ACPO and NIST standards, and we don’t treat them as “nice to have.”
One of the core principles says no action should change data held on a computer, and in our product audits, we’ve rejected tools that quietly modify files just by scanning them. For us, that rule is as automatic as putting on a seatbelt before driving.
From there, the second pillar is documentation. Every change, every command, every decision needs contemporaneous notes. That means we expect analysts, and the products we recommend, to record actions as they happen, not as a memory exercise at the end of a long shift.
We’ve sat in review calls where timelines didn’t line up because someone “filled in the gaps later,” and it nearly tore apart an otherwise strong case.
Then there’s hashing, which we treat as non‑negotiable. Evidence preservation handling forensics depends on cryptographic hash verification, MD5, SHA‑256, SHA‑512, acting like fingerprints for data.
In several product evaluations, we’ve insisted on automatic hash calculation the moment an image is taken, plus re-verification before any handoff. In one engagement, matching hash values exposed that a third‑party system had quietly altered log files, and that hash mismatch was what kept the investigation honest.
Finally, collection order isn’t just theory for us, it’s a checklist we grade tools against. Third‑party experts are clear: collect volatile data first, RAM, then disk images, then network captures, and only then go after longer‑lived physical media.
We’ve watched live memory disappear after an automatic reboot triggered by an overly aggressive security tool, and that single event changed how we evaluate MSSP product stacks.
These basics may feel strict on paper, but in practice they protect everyone involved, the analysts doing the work, the MSSPs making promises to clients, and the truth that has to stand up in court. [1]
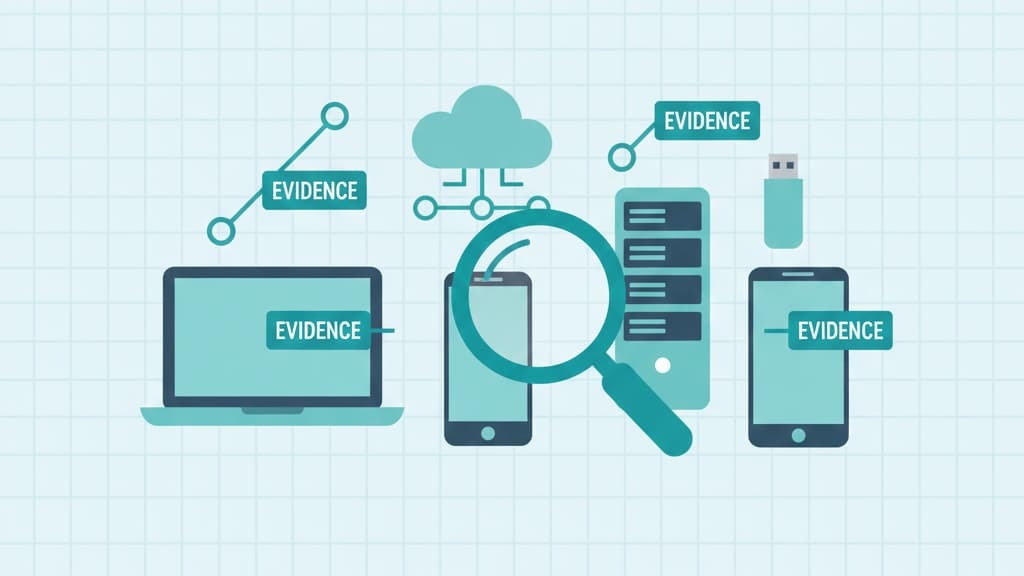
The very first moments in a case can decide how much truth you ever get to see. Our team has walked into live incidents where an attacker was still connected, pushing commands and trying to wipe traces in real time.
In those situations, step one is always the same: secure the environment. That means cutting remote access, stopping risky automations, and freezing activity before any product or platform even starts collecting data.
This is also where experience in incident response becomes essential, ensuring every move stabilizes the environment. If a tool can’t support that kind of controlled pause, we flag it during our MSSP product audits.
Photographs come next, and they’re not optional. SERP guidance tells readers to capture everything in place, devices, cables, indicator lights, error messages, timestamps on screens, and we follow that ourselves, down to the angle of the power strip.
More than once, a photo of a small status LED or a USB dongle in the background has answered a question hours later that nobody thought to write down. This is where we look at how well tools help MSSPs preserve visual context, not just logs.
From an outside view, the main evidence sources look predictable, and they’re the same categories we move through methodically:
In our evaluations, we pay close attention to how products discover and correlate these sources, instead of assuming analysts will remember everything under pressure.
Legal authority is the quiet line that can’t be crossed. If warrants or formal approvals are required, they must be in place before anyone touches a device or starts a collection workflow. Courts can and do reject evidence that was gathered without proper authorization.
We’ve stood in conference rooms with legal counsel explaining that grabbing a laptop too early, or letting an automated agent pull data without clear scope, would undo weeks of careful work. Identification, when done well, looks calm from the outside. It depends more on patience, legal awareness, and tool discipline than on rushing to “get the data” at any cost.
Once sources are identified, the delicate part begins. Evidence preservation handling forensics requires tools that won’t change original data. We use write-blockers because they prevent a computer from writing even a single byte to a drive. A small write can ruin an entire investigation.
SERP sources explain that bit-for-bit forensic imaging is the gold standard. It captures everything: slack space, deleted files, hidden partitions, and metadata. File copying does not. Years ago, we saw a case fall apart because someone copied folders instead of creating a forensic image. They lost unallocated space that held deleted messages.
During acquisition, we document each step with timestamps and signatures. Some analysts underestimate documentation, but we treat it as seriously as the imaging itself.
Notes become part of the evidence’s story, and if that story is incomplete, a court may doubt the whole process, something we’ve also seen during forensic investigation disputes where procedures were challenged.
Third-person sources emphasize the same pattern: clear notes, write-blockers, and full forensic duplication keep evidence trustworthy.
A chain of custody is the evidence’s diary. It must show everyone who touched it, when, where, and why. In court, this can matter more than the evidence itself. We’ve testified in cases where lawyers focused entirely on whether handling steps were clean.
To keep the chain intact, we seal devices in tamper-evident bags. Anti-static bags protect drives, and Faraday bags stop wireless signals from reaching mobile devices. Third-person guidelines agree: any break in custody can invalidate evidence.
We track serial numbers, hash values, conditions, signatures, transfer reasons, and timestamps. In our own casework, we often use dual verification, two analysts verify the same hash before sealing the item. It reduces mistakes and strengthens credibility.
Digital evidence management systems help automate the trail, but we still double-check manually. Automation helps; human oversight protects. A clean chain of custody gives courts confidence that nothing was altered, intentionally or by accident.
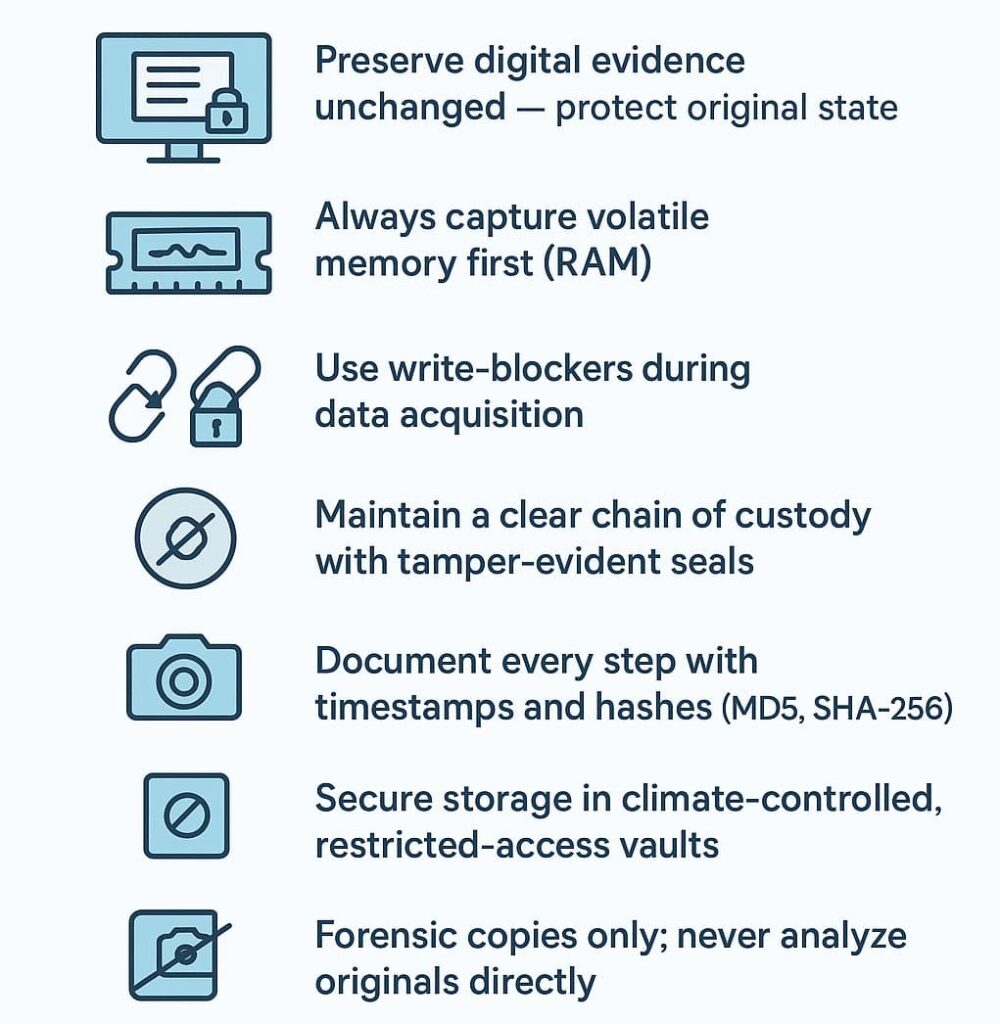
After collection, the focus shifts to preservation. Originals are stored like fragile antiques. SERP sources describe climate-controlled vaults with restricted access, and we use the same approach at MSSP Security. Only a few people are allowed inside.
Analysts never work on the original. We create verified forensic copies and run every analysis on those. This isolation protects evidence integrity.
Volatile memory is always captured first, tools like memory acquisition utilities allow us to get RAM before shutdown. Once a device shuts off, RAM disappears forever. We’ve learned this lesson more than once in early years of field work.
Backups add another layer of safety. We store multiple copies, each hashed and labeled. During long investigations, we re-hash images to ensure nothing drifted or corrupted over time. Third-person sources confirm that periodic re-hashing maintains trust during examination, analysis, and reporting.
These steps might feel slow, but slow is sometimes the safest speed.
Every case has obstacles. Encryption is a big one. It protects people’s privacy, but it also slows forensic work. Some drives use full disk encryption that locks up when power is removed. In the past, we had to image laptops while they were still powered on because shutting them down would lock everything permanently.
Anti-forensic tools create more trouble. SERP sources list timestomping, changing file timestamps to confuse investigators. We’ve seen attackers wipe logs, overwrite memory, or hide malware deep in registry hives.
Cloud data brings another challenge: volatility. Some logs live only a few hours before they rotate. Third-person experts warn that delays can destroy key artifacts.
Massive volumes complicate everything, terabytes of logs, captures, and images. Sorting through them takes time and discipline.
Still, none of these are impossible challenges. They just require the right mindset and process.
The best teams follow a mix of smart tools and strong habits. SERP sources list specialized kits like Velociraptor or Autopsy for triage and analysis. We’ve used similar tools ourselves, but the tool is never more important than the method.
Legal holds are crucial for cloud investigations. They freeze logs so they don’t get erased. Without them, vital clues vanish.
Training matters too. Analysts must learn memory forensics, live forensics, disk imaging, and forensic scripting. At MSSP Security, we train ourselves constantly because standards and attacks evolve fast.
One of the biggest skills is balancing speed with preservation. During rapid incident containment, we often use EDR telemetry for remote triage. This helps reduce impact fast while still preparing for full forensic acquisition later.
Third-person experts note that courts expect well-documented methods. A strong forensic report follows Daubert or Frye standards and explains every step clearly.
These practices keep investigations smooth, accurate, and defensible. [2]
Evidence only matters if it stands up in court. That’s why documentation becomes the backbone. A proper forensic report includes:
We’ve had cases where the report alone convinced a judge of evidence integrity. Courts want reproducibility. If another trained person can follow the same steps and reach the same results, the evidence becomes strong, especially when the findings align with well-structured forensic analysis that clearly explains how the conclusions were reached.
SERP sources emphasize Daubert and Frye rules for expert testimony and methodology standards. These rules ensure scientific reliability.
Evidence preservation handling forensics is not only about collecting artifacts. It’s about telling a clear, trustworthy truth supported by logs, hashes, timelines, and notes. That’s how evidence moves from “interesting data” to “admissible proof.”
You keep evidence integrity by slowing down and following simple evidence handling steps. Use a write blocker during data acquisition so you don’t change anything. Capture volatile memory first, then move to disk imaging or full forensic imaging. When you finish, use hash verification to confirm nothing shifted. These habits help keep every artifact trustworthy.
Live forensics works best when you collect fast but still protect the device. Capture volatile memory, gather process lists, and record network activity. Keep a clear chain of custody and add forensic documentation as you go.
These small steps help a cybercrime investigation stay clean while you still move quickly during incident response or early incident containment.
Pick tools that support forensic duplication, metadata analysis, and simple forensic timeline views. Some tools help with file carving, log analysis, or endpoint forensics, while others focus on network forensics. Choose what fits the artifact you have. Clear forensic methodology matters more than the brand. Good tools only help you follow it.
A strong forensic report shows how you collected each item and how you protected it. Courts want clean forensic procedures, consistent forensic protocols, and a solid forensic chain. Add hash values, timestamps, and steps you took for forensic validation. Clear writing helps judges follow your work and trust your forensic examination.
Effective evidence preservation relies on simple habits: keeping originals untouched, documenting every step, and verifying integrity with hashes. This article showed how identification, collection, chain of custody, preservation, and reporting protect digital evidence and strengthen court readiness.
At MSSP Security, we’ve seen these methods prevent mistakes and simplify complex cases. For tailored support that streamlines operations and improves your security stack, get expert MSSP consulting today.