Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Outsourced digital forensics investigation is for teams that have more alerts than hours in the day, but still need every case handled right. When a breach hits, most organizations aren’t shopping for new dashboards, they’re trying to understand the damage and stop the bleeding.
At MSSP Security, the same three questions always come first: “What happened, what broke, and how do we keep this from spreading?” If you need sharper answers, leaner costs, and someone who can carry the hard parts with you during an incident, keep reading.

We see the need for real DFIR expertise grow every quarter, especially when we sit with MSSP teams staring at queues full of unresolved incidents. Cyber events don’t wait, ransomware, insider abuse, targeted intrusions, and quiet data leaks all move faster than most teams can staff up.
Leadership still expects immediate answers, full root cause analysis, clean forensic triage, disk and image handling, memory forensics, log analysis, and defensible evidence preservation, but they rarely have the headcount to sustain a proper DFIR arm.
On the MSSP side, we hear the same thing in product review calls and service audits: the SOC is strong on detection, but thin on digital forensics investigation and response.
Some providers spend months hiring “the right analyst” only to realize they still don’t have DFIR playbooks, forensic readiness planning, or strong habits around chain of custody, timeline analysis, and malware reverse engineering.
Our work often starts when they ask us to assess a new toolset or stack, and we find that DFIR capabilities are either missing or bolted on without much thought.
Then there’s the tooling itself. Forensic platforms are expensive, noisy, and easy to misconfigure, and anti-forensics countermeasures (wiping, tampering, obfuscation) keep raising the bar.
We’ve watched teams invest in three different DFIR tools and still fail to get reliable forensic imaging, memory dump analysis, file carving, or artifact extraction during a live incident. That’s usually when they call us in to evaluate what they bought, what they actually use, and what should be replaced.
What most leaders tell us, once we’re past the product sheets and demos, is that they just want the stress taken off their analysts. Outsourced digital forensics investigations, and the consulting that comes with choosing and auditing the right products, give MSSPs breathing room.
They get access to mature DFIR workflows and tools without carrying all the risk themselves, and they get faster, clearer answers when every minute feels a little too loud. [1]
Credits: EC-Council
Outsourced digital forensics investigation, at its core, is when an organization hands the heavy DFIR work to a team that already lives in that world every day. Instead of trying to build everything themselves, they rely on specialists with mature tools, repeatable workflows, and the training to run incident response and forensic work on demand.
Some partners call this DFIR-as-a-Service (DFIRaaS) or Digital Forensics as a Service (DFaaS). Others fold it into a broader DFIR retainer so they can guarantee rapid triage when something breaks at 2 a.m.
From our side, when we’re helping MSSPs review or select products, we’re often checking whether a platform can really support that model, or if “DFIRaaS” is just a label in the sales deck.
On the investigative side, these providers step in after a breach to answer the hard questions. That can be deep ransomware forensics, phishing incident response on compromised inboxes, or targeted data exfiltration analysis that spans cloud accounts and on-prem systems.
They take on cloud forensics outsourcing, mobile device forensics, network forensics services, and classic dead box analysis that still matters in a lot of cases.
Under the hood, they’re acquiring and preserving data the right way. That means capturing disk images, running memory forensics with tools like Volatility, and doing remote forensic triage when physical access isn’t an option.
We often evaluate whether tools actually support proper log collection, IOC extraction, threat actor TTP mapping with MITRE ATT&CK, and clean, court-admissible reporting, or if those claims fall apart during a real review.
When we help MSSPs assess or improve these services at MSSP Security, we treat every case and every product stack like a puzzle. Our work is to see whether the technology and process can actually reconstruct events, step by step, while keeping chain of custody intact.
Because if the evidence won’t hold up when challenged, then the “forensics” label is just marketing, and we call that out directly.
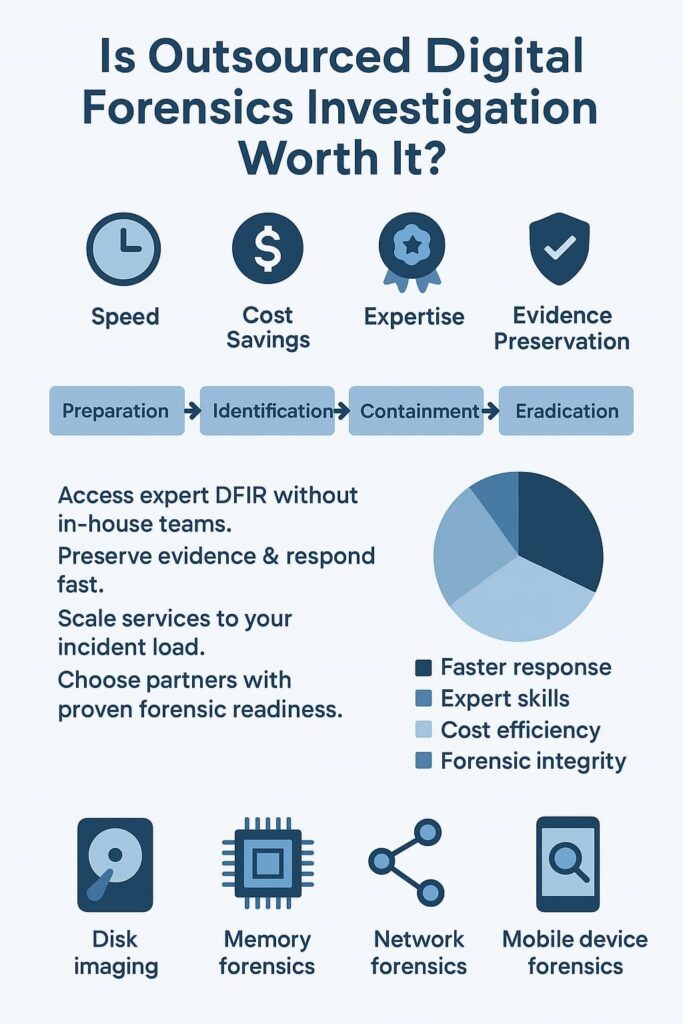
Outsourced digital forensics investigation gives organizations something they rarely have: calm during chaos. First, it offers access to specialized expertise, analysts trained in anti-forensics detection, steganography detection, password cracking forensics, or encrypted data forensics. This avoids hiring delays and training costs.
Second, cost efficiency matters. A full forensic lab, forensic storage, and tools like FTK imager outsourcing, EnCase forensic services, or magnet AXIOM analysis can be expensive to maintain. Outsourcing removes those overheads. Services scale up during major breaches and scale down during quiet periods.
Third, speed improves dramatically. With on-demand forensics experts and secure evidence transfer, teams get faster results, reducing downtime. Rapid incident response outsourcing often prevents attackers from spreading further.
Last, evidence stays forensically sound. Providers preserve legal admissibility evidence and perform forensic report generation that holds up under scrutiny. For many leaders, this alone makes the investment worthwhile.
The IR lifecycle stays the same, even when outsourced. What changes is the speed and depth. It usually includes:
Here, teams often lean on digital forensics incident response practices that blend smoothly with ongoing work when every minute counts.
With outsourced support, forensic tasks become clearer. Investigators handle:
The goal stays simple: reveal what happened and document it in a detailed, court admissible report.
Not all outsourced DFIR teams are equal. Organizations should evaluate experience first. Look for teams with proven cases involving insider threat forensics, APT forensics hunting, zero day exploit forensics, supply chain compromise DFIR, or persistent threat investigation. Certifications like CCFE or CDFE show formal training.
Next, check forensic capabilities: forensic labs, secure storage, remote forensics access, and specialized tools for forensic imaging and artifact extraction. Testimonials reveal reliability, professionalism, and how well the provider communicates.
Scope of services matters too. Some offer proactive support like threat hunting and vulnerability testing. Others focus mostly on reactive breach investigation outsourcing. Pricing and contract terms should be clear. Hidden fees lead to frustration.
Finally, industry expertise is crucial. A provider familiar with GDPR breach investigation, HIPAA forensics services, PCI DSS forensics, or compliance forensics audit can save teams from legal headaches. Clear reporting protocols and rapid escalation help the service integrate smoothly with existing SOCs and MSSPs.
Outsourced DFIR teams use a wide range of techniques. Computer forensics involves disk imaging, deleted file analysis, hash matching forensics, and artifact extraction. Analysts recover lost data or identify suspicious executables.
Mobile device forensics uses tools like Cellebrite mobile forensics or Oxygen forensics cloud to extract call logs, messages, app data, and GPS traces.
Network forensics services track suspicious traffic, proxy server forensics, VPN forensics analysis, and reconstruct attack paths. Teams often use log analysis forensics, packet inspection, and cross-drive correlation.
Social media forensics examines accounts, profiles, fake identities, and message trails. Email forensics investigation checks headers, attachments, encryption, and file tampering.
Some cases require steganography detection, keylogger detection, indexed keyword search using regular expressions forensics, or foreign language forensics when attackers use multilingual content. Each technique plays a part in building a complete picture.
These steps often intersect with focused malware analysis efforts or quick when threats hide deeper layers. [2]
Outsourcing DFIR comes with challenges that teams must prepare for. Data volume is one, huge logs, memory dumps, and cloud data sets take time. Providers use cloud-based tools to handle scalability.
Anti-forensics evasion techniques like encryption, log wiping, or timestomping require advanced expertise. Skilled analysts detect hidden data and reconstruct tampered timelines. In fast-moving cases, this blends with malware incident response work, helping teams follow an that keeps attackers from slipping through unnoticed.
Jurisdictional issues matter too. Legal and regulatory requirements differ across regions. Providers must clarify how evidence is stored, transferred, and preserved. Clear agreements ensure privacy and compliance with frameworks like NIST DFIR framework or SANS incident handler poster.
For many organizations, these challenges become manageable with the right partner. At MSSP Security, we’ve seen that clear communication and strong forensic readiness planning help teams handle investigations smoothly.
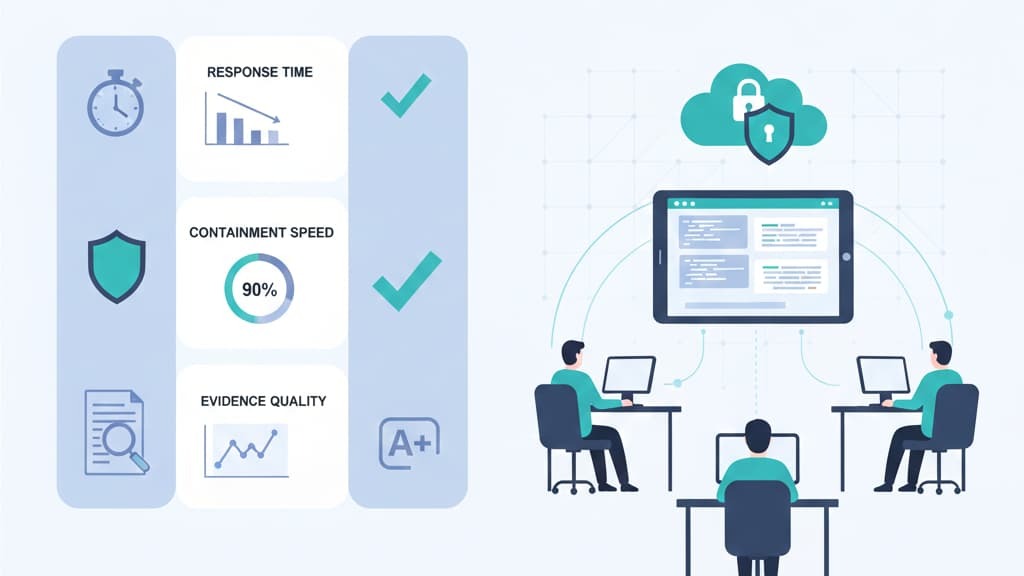
Teams measure outsourced DFIR using KPIs. Mean Time to Detect (MTTD) shows how quickly analysts identify incidents. Mean Time to Respond (MTTR) reflects containment and neutralization speed. Mean Time to Recover (MTTREC) shows how long operations take to return to normal. Evidence Collection Rate measures how effectively data is captured.
Regular reporting tracks improvements over time. Teams adjust strategies, tighten logging, improve playbooks, and strengthen forensic readiness planning. When organizations review results consistently, their security posture improves, and incidents become easier to control.
Case Study 1:
A company suspects a disgruntled employee of stealing intellectual property. The internal team lacks deep DFIR skills, so they contact an outsourced digital forensics provider. The analysts perform disk imaging, live forensics, and email forensics. Timeline analysis DFIR reveals file transfers to a personal drive. The report becomes court-admissible evidence.
Case Study 2:
An online retailer faces complaints about compromised credit card data. A DFIR provider performs network forensics services, firewall log forensics, and proxy server forensics. They uncover a hidden script capturing payment info. Rapid containment and eradication prevents further loss.
When you use outsourced digital forensics, you get help with digital forensics investigation tasks like evidence preservation, chain of custody, and forensic triage.
Teams often use DFIR services, digital forensics as a service, or DFIRaaS to handle memory forensics, disk imaging, and log analysis forensics. This support helps you respond faster when something goes wrong.
Incident response outsourcing gives you quick help with live forensics, dead box analysis, and forensic triage when an attack starts. Providers can run malware reverse engineering, timeline analysis DFIR, and IOC extraction to find what happened. They also check for data exfiltration analysis and phishing incident response issues so you can stop more damage.
Outsourced teams can handle cloud forensics outsourcing and mobile device forensics when you can’t do it alone. They check apps, files, and logs using artifact extraction, file carving, hash matching forensics, and steganography detection. They also run network forensics services and VPN forensics analysis to see how an attacker moved through your systems.
Many groups help you keep legal admissibility evidence safe by following chain of custody rules. They support court admissible reports through forensic report generation and secure evidence transfer. They also use tools like FTK imager outsourcing, EnCase forensic services, and magnet AXIOM analysis to collect clear data that holds up in court.
Outsourced digital forensics investigation gives organizations the speed, expertise, and clarity needed to handle incidents without the cost of building an internal DFIR team. It preserves evidence, reveals root causes, and helps prevent repeat attacks. With the right partner, teams stay calm and decisive when moments turn critical.
Join us to strengthen your incident response and streamline your security operations