Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

A managed DFIR retainer service is just an agreement that puts incident responders on deck before an attack ever happens. When a breach hits, there’s no waiting on contracts, no hunting for help while logs are disappearing and systems are failing. Reports keep showing the same pattern: the longer the delay, the higher the breach cost.
One industry study even calls out that pre-arranged DFIR support gives “immediate access to experts without contract delays.” At MSSP Security, we see prepared teams recover faster and argue less about next steps.
If you want that kind of calm in a crisis, keep reading.

Every serious cyber incident we’ve watched up close had the same look: money bleeding out, projects on hold, and leadership suddenly very, very interested in security. Breach counts keep rising each year, and the price tags follow.
Industry reports show average data breach costs pushing into seven figures, especially when response drags. While systems sit offline, operations stall, customers question everything, and executives scramble for answers.
We hear the same question from MSSPs all the time: are our clients actually ready to respond when it hits? When we dig in, the answer is usually uncomfortable. Internal teams are stretched between daily tickets, compliance demands, and project work.
They rarely have full 24/7 coverage, mature forensics capability, or a tested incident response plan. We’ve seen cases where ransomware is still spreading while people argue over contracts and approvals, those lost minutes turn into real money.
From our own consulting work with MSSPs, we’ve seen how a DFIR retainer changes the picture. Instead of chaos, there’s a playbook. Instead of haggling over terms mid-crisis, the experts are already on call, with access agreed in advance.
That’s why more MSSPs are pushing their clients toward DFIR retainers: they give structure when everything feels broken, letting external specialists handle the breach while the internal team keeps the business as steady as possible.
At its core, a managed DFIR (Digital Forensics and Incident Response) retainer is a standing agreement that says: when something bad happens, the responders move first, not the paperwork. The organization gets a pre-committed expert team on call, ready to step in the moment an incident starts, without waiting on new contracts or chasing signatures.
The purpose stays very direct:
In practice, we see managed DFIR retainers combining two worlds. On the proactive side, there’s threat hunting, vulnerability reviews, forensic readiness checks, and resilience planning.
On the reactive side, those same teams handle root cause analysis, malware forensics, digital evidence collection, and full breach response when things actually go wrong.
From the consulting work we do with MSSPs, this “pre-arranged access” is usually what makes or breaks an incident. One industry source calls out that the real value is avoiding “delays related to contract negotiations or resource availability,” and that matches what we see when MSSPs are trying to choose or audit DFIR providers.
When their client is in crisis and the DFIR partner has already been vetted, approved, and connected, our side of the work shifts from firefighting vendor issues to actually helping contain the breach, and that’s when the room finally settles down. [1]
Cyber incidents don’t wait for business hours. A DFIR retainer gives on-call cybersecurity support any time of day. Most services include a hotline answered by trained agents who begin incident triage within minutes. Early triage shapes everything: it sets priorities, confirms threat severity, and pulls in forensic capabilities fast.
Triage is where the chaos starts to settle. Analysts quickly assess what happened, what evidence matters, and which systems are at risk. With a DFIR retainer, these steps are smooth. No scrambling. Just clear evaluation and a plan. Teams get direction on containment, evidence preservation, and what must be isolated immediately.
Digital forensics uncovers the truth: how attackers got in, what they touched, what they stole, and whether they still lurk inside. Methods include:
For many clients we’ve helped at MSSP Security, this part brings relief. People always want answers. Forensics delivers them through documented evidence, forensic protocols, and forensic incident reporting.
Teams dealing with deeper questions often refer to core practices found in digital forensics work, which helps them map attacker movement and validate what evidence matters most.
When malware is involved, understanding its behavior is critical. Malware forensics reveal:
Analysts often rely on principles similar to malware analysis to break down hostile code and uncover unknown functions that would otherwise stay hidden.
After the investigation, organizations need specific guidance. Not vague advice. Not guesswork. Actual steps. That includes:
We help teams understand what to fix now and what changes keep them safer long term.
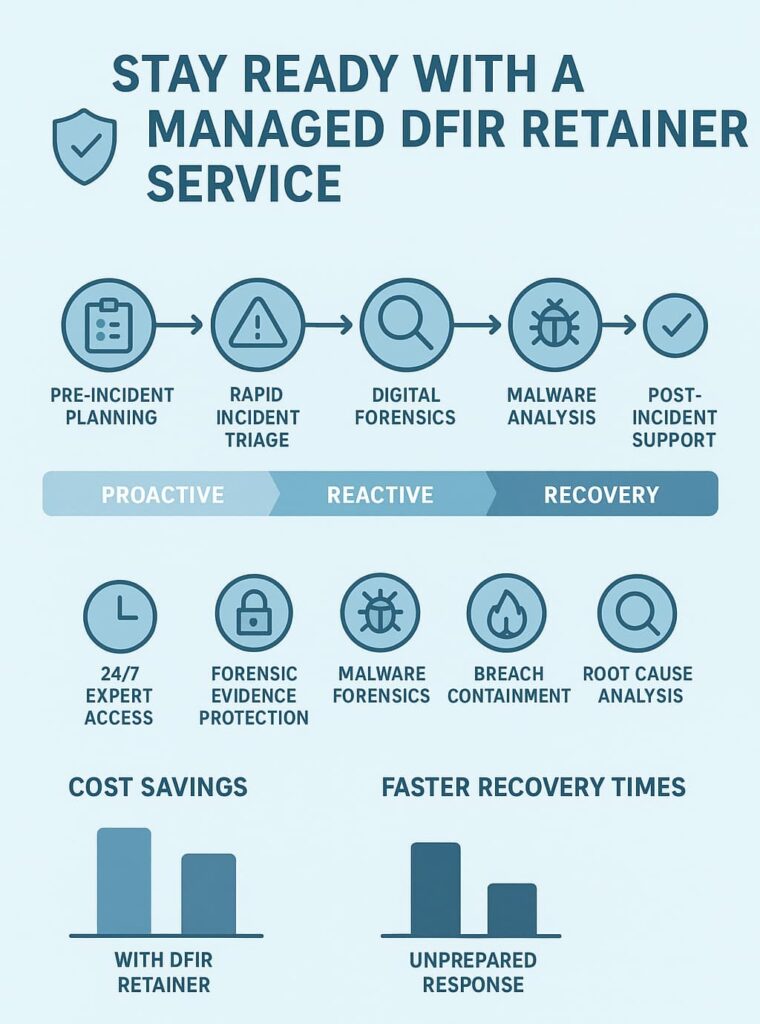
Strong security doesn’t end when the threat stops. Many DFIR retainers include:
These sessions build confidence. They help teams feel prepared, not overwhelmed, when the next alert fires. Some teams add review steps shaped by Incident response concepts to ensure gaps found during investigations don’t repeat in the next incident.
Speed is everything. Delays give attackers room to spread, steal, and damage. A DFIR retainer ensures rapid incident response, rapid incident containment, and faster recovery. With pre-negotiated terms, responders jump in immediately.
Compared to breach-related expenses, data recovery, legal fees, fines, downtime, reputation damage, a retainer is cost-efficient. Many organizations use retainers because they offer predictable pricing. The savings become clear after even one serious incident.
A DFIR retainer connects organizations with cybersecurity experts who handle digital investigation, attack analysis, ransomware investigation, and forensic audit work daily. At MSSP Security, our responders have lived through hundreds of incidents. That experience matters more than any tool.
Many retainers include proactive services such as:
These steps strengthen cyber resilience and prevent small incidents from turning into full-blown crises.
Organizations should start by asking:
The answers reveal whether a DFIR retainer is essential or urgent.
A strong provider should have:
At MSSP Security, our own approach focuses on clarity and evidence. We’ve shaped our services around lessons learned from clients in crisis.

Not all retainers are alike. Organizations should understand:
A good agreement removes confusion, not creates it. [2]
SLAs are the heart of a DFIR retainer. They define:
Clear SLAs turn panic into predictability.
A basic package offering a set number of hours for incident response, malware forensics, forensic documentation, and cyber incident management. Ideal for smaller teams that need expert backup.
Adds proactive features like forensic readiness assessment, vulnerability assessment, and incident response playbook creation. Good for mid-sized organizations with growing security needs.
A comprehensive model combining 24/7 incident handling, cyber insurance coordination, crisis management, security monitoring advice, incident response automation guidance, and full forensic services. This model suits regulated industries or high-risk enterprises.
A DFIR retainer focuses on digital forensics and incident response. It helps with incident management, forensic investigation, and cyber incident response. It gives you rapid incident response, incident triage, and breach containment when something goes wrong.
Many people choose it because it supports digital evidence collection, forensic readiness, and clear incident handling that a basic cybersecurity retainer may not cover.
A DFIR retainer supports ransomware response with malware forensics, attack analysis, and cyberattack mitigation. The incident response team can guide breach response, cyber incident management, and incident containment.
They also protect forensic evidence so you can understand what happened. This helps with data breach investigation, incident recovery, and longer-term cyber resilience after the attack.
Most retainers follow a simple incident response lifecycle. You get 24/7 incident response, security monitoring, and help with incident escalation. Teams use threat detection, incident forensic reporting, and root cause analysis.
You may also see forensic analysis, cyber forensics, and digital investigation. All of this supports strong evidence preservation and smooth cyber incident coordination.
A solid retainer helps with cybersecurity preparedness through proactive threat hunting, vulnerability assessment, and forensic readiness assessment. Many plans include tabletop exercises, an incident response plan, and a forensic toolkit.
These steps build cyber defense strategy, improve security operations, and support forensic capabilities. Over time, this boosts cyber resilience and helps reduce chaos when something happens.
A managed DFIR retainer service gives organizations what they rarely have during a crisis: speed, clarity, and expert guidance. It shortens response time, protects forensic evidence, and helps teams move from chaos to control.
Over time, it becomes the backbone of real cyber readiness. We’ve seen organizations feel calmer and more prepared once a retainer is in place. If you want the same confidence, you can join us here.