Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Proactive security monitoring techniques is what teams use when alerts stop being useful.
Most attacks now slip through side doors, hiding in quiet logs and low-priority events that no one has time to study. Many readers know this already, too many notifications, almost no real direction.
Proactive security changes how you work. You don’t just wait for alarms, you look for early patterns, unusual behavior, and small signals that point to bigger risks. That’s the approach we use every day at MSSP Security, and it’s how teams get ahead instead of just reacting.
Keep reading to see how we do it.

Every strong proactive program we’ve reviewed has the same heartbeat: continuous, real-time monitoring.
Instead of staring at one tool, teams watch the whole environment at once, network traffic, system logs, user behavior, endpoint activity, firewall events, VPN usage, DNS requests. Every small signal gets a chance to speak up, even if it seems harmless on its own.
We see this line up with what other analysts report too. One source put it simply: constant analysis of live signals lets you catch trouble before it spreads.
That quote tracks with what we see when we audit MSSP stacks, teams that only rely on “after the fact” logs usually find out about attacks late, after lateral movement, cloud probing, or quiet data collection has already started.
In our consulting work, we’ve watched the opposite story play out. With the right continuous monitoring in place, odd process behavior, strange login paths, and suspicious outbound connections don’t blend into the noise; they stick out.
This mirrors findings in finding advanced persistent threats where timely insights can prevent more significant issues down the line.
When MSSPs plug SIEM platforms, EDR tools, cloud monitoring, and log aggregation into a single view, real-time alerts start showing patterns instead of random noise, and correlated events tell a clearer story.
There’s also the quieter side of this stage. Asset discovery, encryption monitoring, security posture checks, baseline deviation tracking, and continuous control monitoring don’t always create flashy alerts, but they decide how quickly a team can spot something “off.”
Our role is to help MSSPs pick and validate products that actually support this kind of always-on visibility, so their clients see less chaos, less blind faith in tools, and more grounded confidence in their defenses.
Credits: Operational Excellence Mastery
Normal is the most underrated signal in security. Once a team understands what “everyday” looks like, it becomes much easier to spot the one session, the one access, the one process that doesn’t fit. That’s where behavior analytics and baseline deviation really earn their place in a proactive program.
In many MSSPs we advise, UEBA and anomaly detection help flag changes such as odd login paths or spikes in activity. We’ve seen this become even more effective when paired with managed threat hunting, where analysts dig into long-term behavioral drift rather than waiting for rule-based alerts:
We’ve seen plenty of threats that never showed up as malware at all. Instead, they looked like slow drift: a user logging in three hours earlier than usual every day, a service account suddenly touching a finance database, or a sharp, unexplained spike in endpoint alerts from one quiet segment of the network.
On paper, each event looks minor. Together, they tell a different story. Vendors like to say their ML and UEBA “catch subtle anomalies that rules miss,” and SERP sources repeat that line, but we’ve actually watched that play out in live environments.
During product audits, we’ve seen one platform completely ignore a pattern of abnormal access while another flagged it within minutes, just because its baseline model was better tuned to that client’s behavior.
Behavior analytics also connects directly to more advanced use cases, including:
Our job, as a consulting partner to MSSPs, is to help them choose and verify tools that do this well in practice, not just on a feature sheet. When behavior baselines are solid and deviation detection actually works, teams stop chasing every alert and start focusing on the few behaviors that truly don’t belong. [1]
Threat intelligence integration gives monitoring the context it needs. Without context, alerts overwhelm teams. With context, risk prioritization becomes easier. Threat intelligence bridges internal and external signals: malicious IPs, known command-and-control domains, attack vector identification, phishing detection patterns, and attacker tactics.
In our day-to-day work at MSSP Security, we enrich logs with threat intelligence feeds to improve threat prediction and attack surface mapping. It turns raw data into real insights. As SERP information explains: “Threat intelligence offers early warning and contextual risk evaluation.”
That’s exactly why integrating threat intelligence with SIEM tools, endpoint detection, and cloud monitoring matters so much.
This step strengthens cyber defense, enhances SOC metrics, and supports compliance monitoring and security governance, because alerts become clearer and less noisy. Incorporating solid threat-hunting platform management creates a more robust defense strategy that mitigates potential attacks before they escalate.
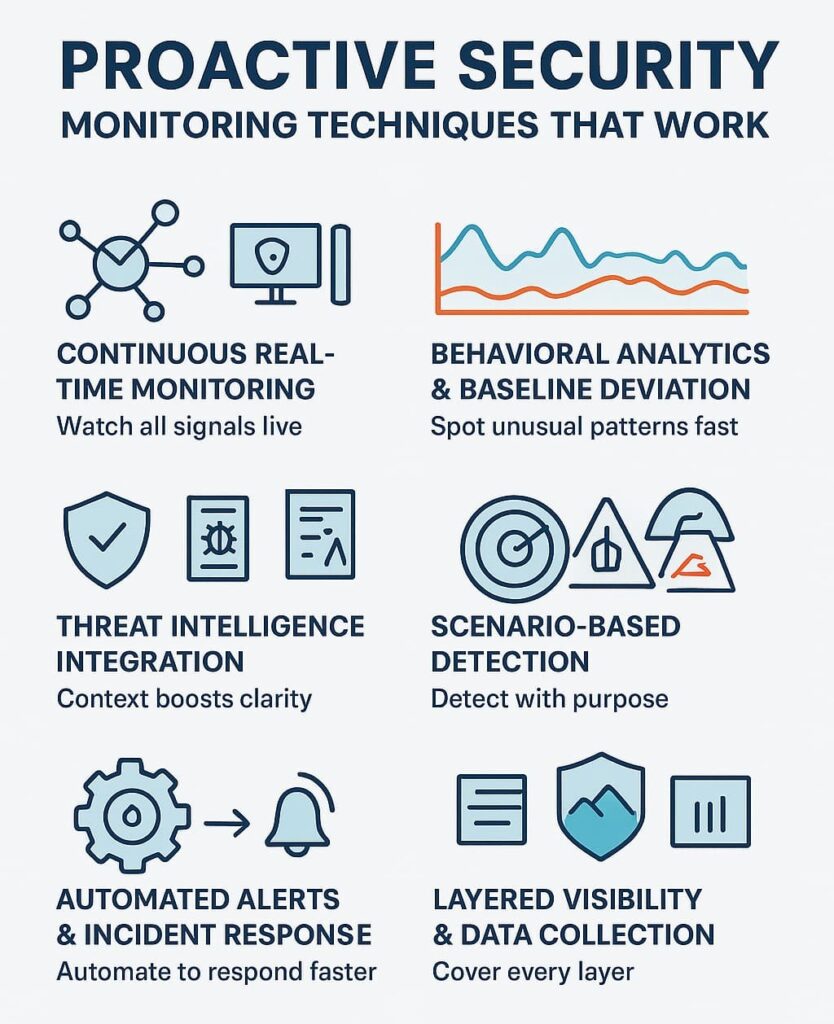
Scenario-based detection is where proactive security monitoring becomes smarter, not louder. Teams map detections directly to adversary behaviors: command-and-control beaconing, credential misuse, sandboxing bypass attempts, data exfiltration via SaaS apps, attack simulation triggers, or unusual cloud workload patterns.
At MSSP Security, we rely on scenario mapping heavily. When teams monitor without scenarios, they drown in alerts.
When they monitor with scenarios, like detecting DDoS detection, malware analysis patterns, configuration management issues, or identity and access management anomalies, the results are consistent and meaningful. A SERP source explains that scenario-based detection “improves relevance and accuracy.” We see this daily.
Scenario mapping also helps detect zero trust monitoring gaps, IoT security issues, and potential insider threat analytics patterns. It’s proactive security with purpose.
Automated remediation and incident response speed up containment. When something looks wrong, teams cannot wait. Proactive security monitoring relies on automation to reduce alert fatigue and shorten mean time to respond.
It ties directly into SOAR (security orchestration, automation and response), log analysis, attack surface mapping, and remote monitoring workflows.
At MSSP Security, automation saves hours every week. Automated triage sorts out false positives. Automated remediation handles routine tasks like isolating endpoints, blocking IPs, or resetting compromised credentials. SERP results call this “immediate notification and fast containment,” and that is exactly why it matters.
This also includes creating incident response playbooks, incident investigation steps, and incident forensics workflows, ensuring teams stay calm when real threats appear.
Not all systems are equal. Asset and risk prioritization helps teams protect what matters most: critical databases, admin accounts, financial records, customer data, and core applications. Without prioritization, teams spread their attention too thin.
MSSP Security often starts projects here. We map critical assets, understand business processes, measure risk tolerance, and identify gaps where data loss prevention or network segmentation is weak. SERP analysis says this step “aligns detection with organizational risk,” and we’ve seen it transform chaotic SOC operations into focused ones.
This stage ties to vulnerability management, vulnerability prioritization, penetration testing results, patch management cycles, and security baseline enforcement. It turns security into strategy.
Layered visibility keeps no corner of the system dark. Proactive security depends on gathering data across networks, endpoints, cloud platforms, IAM tools, and business apps. When data stays in silos, threats hide between them.
At MSSP Security, we merge data from cloud security monitoring, network traffic analysis, endpoint detection, identity systems, and threat intelligence. SERP info states this creates “comprehensive coverage for detecting sophisticated threats.” It also improves threat correlation, attack prediction, and anomaly response automation.
This stage often includes honeypots, sandboxing, dark web monitoring, and cyber threat intelligence inputs. With the right data layers, patterns become clear. [2]
Feedback loops keep security alive. As threats evolve, detection must evolve too. Proactive security monitoring includes reviewing incident reports, updating detection rules, improving threat intelligence, refining alerts, and adjusting risk assessment results.
At MSSP Security, we keep this loop constant. Every incident, big or small, teaches something. SERP sources note that continuous improvement “boosts long-term effectiveness.” This is true. Teams that adapt grow stronger; teams that don’t fall behind.
Continuous improvement strengthens compliance reporting, security policy enforcement, SOC automation, suspicious activity detection, and entire cyber defense programs. It’s the part of proactive security that keeps everything sharp.
Proactive security helps teams see risks sooner by using continuous monitoring, threat detection, and behavior analytics. It also uses threat intelligence, network traffic analysis, and log analysis to show early warning signs. With risk assessment and risk prioritization, teams get a clearer view of what matters most and can respond before small issues grow.
Users can watch for unusual activity through anomaly detection, insider threat detection, and user behavior monitoring. Real-time alerts, endpoint detection, and suspicious activity detection help catch problems fast.
Baseline deviation and UEBA tools make it easier to notice odd logins, strange network traffic, or data exfiltration attempts that might signal danger.
If alerts feel noisy, or incidents keep slipping by, it may be time to add stronger tools like cloud security monitoring, vulnerability scanning, and attack surface mapping. SIEM integration, SOC automation, and security analytics add clarity. A security operations center can also support incident response and ongoing cyber defense when things get complex.
Threat hunting gets easier with AI threat detection, machine learning security, and threat correlation. Automated remediation and automation and response (SOAR) help filter false alarms. Honeypots, sandboxing, and malware analysis give teams safer places to test attacks. These tools support better incident investigation without slowing anyone down.
Proactive security monitoring techniques give teams a clear, steady way to stay ahead of threats. With continuous monitoring, behavior analytics, threat intelligence, automation, and layered visibility, organizations gain more control, reduce risk, and respond faster.
By applying these techniques, and keeping a strong feedback loop alive, security becomes calmer, clearer, and far more resilient.
If you want expert support to strengthen your approach, our team at MSSP Security is ready to help with strategy, stack optimization, and hands-on guidance built on 15+ years and 48K+ completed projects.